最近在审计Exchange邮件系统的时候,发现大量用户半夜登录的日志。而且都是成功的,几乎没有失败的情况。其中Logon Type 8表示用户从网络登录。
Logon type 8: NetworkCleartext. A user logged on to this computer from the network. The user’s password was passed to the authentication package in its unhashed form. The built-in authentication packages all hash credentials before sending them across the network. The credentials do not traverse the network in plaintext (also called cleartext).
Logon Process:Advapi说明这个一个基于网页的登录,IIS的登录请求过程就是通过advapi进程的。后面的w3wp.exe也说明了是通过IIS登录。如果是Windows验证的这里会显示Kerberos。
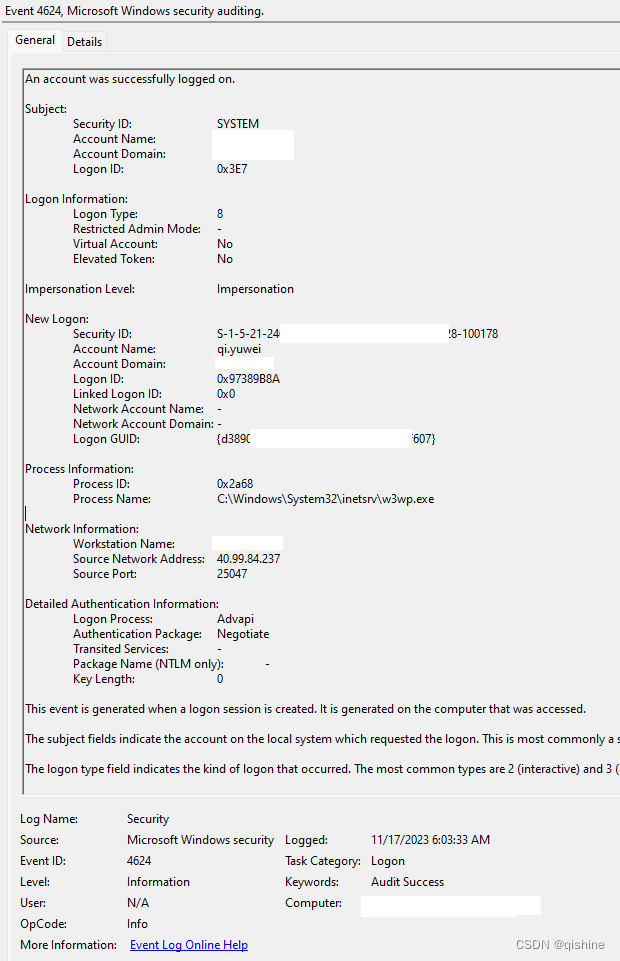
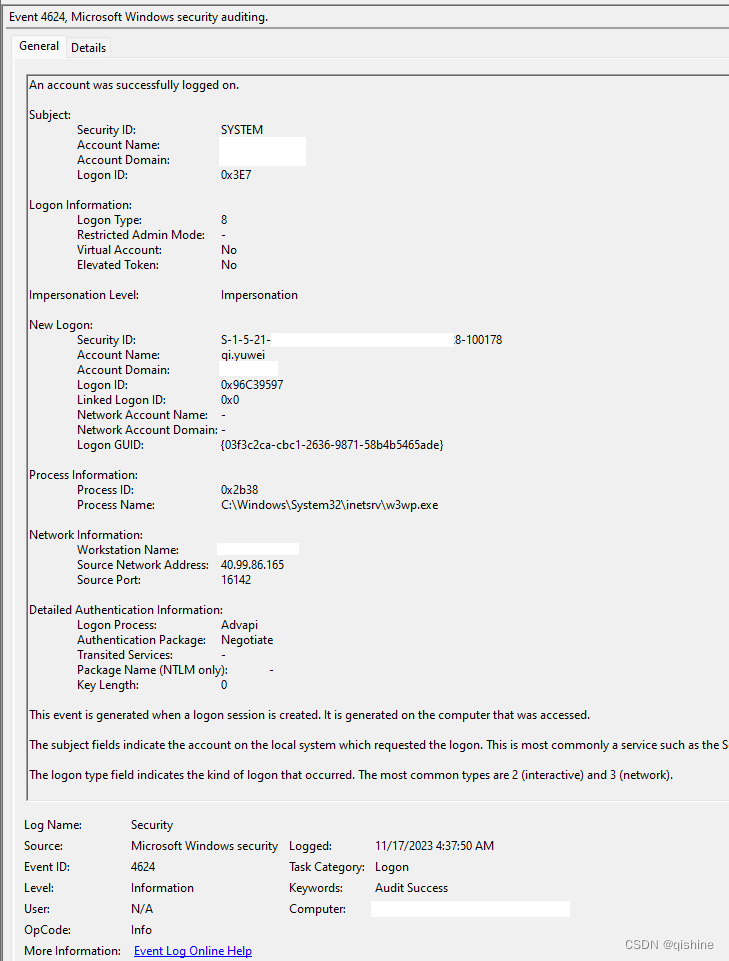
这时候我很担心是不是账户泄露或者系统有漏洞,造成别人能直接访问了。
查了一下这两个地址都是国外Azure的地址。这就需要检查一下手机上的Outlook是不是有什么问题了。因为半夜我的电脑关掉了,只有手机上配置过邮箱了。

经过查找,有一篇文章说了这种情况,移动客户端会通过Microsoft 365的地址连接到用户本地部署的Exchange上。
- Supports and has SOCKS proxy capability enabled. The Outlook for iOS and Android client utilizes TCP connections to our Microsoft 365- or Office 365-based architecture. The IP ranges for the SOCKS connections are not restricted to a subset of Azure IP ranges, which means that customers cannot define an allowlist range. The PAC must be configured to use hostnames instead of protocol and return the SOCKS proxy information given the host URL; no extra custom settings are supported.
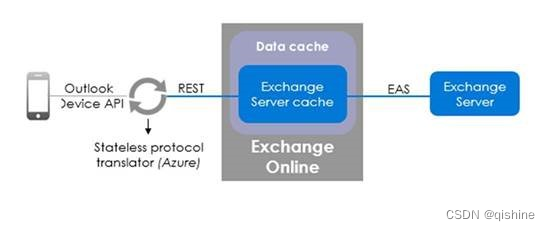
这样至少说明了服务器和账户没有问题,但是这样通过Exchange Online绕一圈真的好吗?我的数据还安全吗?