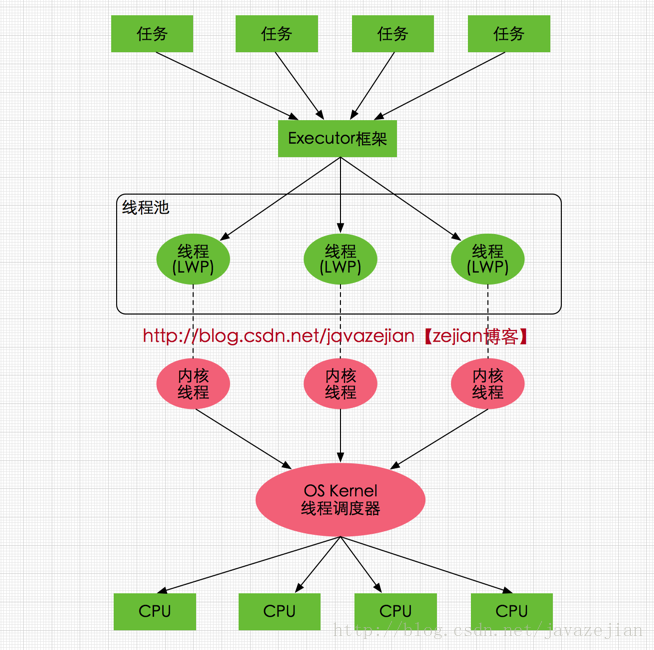
说明:
ldap信息配置到es配置文件上,然后kibana读取es的配置信息
用户与角色的关系通过role_mapping.yml文件配置获取
角色与权限的关系通过elastic stack提供的DevTools或API进行维护
一、前置条件:
1.1 es已开启xpack(已开启的可忽略)
es01:environment: - xpack.security.enabled=true1.2 新建ldap 映射文件:role_mapping.yml
superuser:- "cn=Manager,dc=houpu,dc=com"
kibana_user:- "uid=langpf,ou=people,dc=houpu,dc=com"
test:- "uid=chasy,ou=people,dc=houpu,dc=com"1.3 将映射文件挂载到es容器
es01:volumes:- ./role_mapping.yml:/usr/share/elasticsearch/config/role_mapping.yml二、在es配置中开启ldap
es01:environment:- xpack.security.authc.realms.ldap.ldap1.type=ldap #此项已弃用- xpack.security.authc.realms.ldap.ldap1.order=0- xpack.security.authc.realms.ldap.ldap1.url=ldap://192.168.31.240:389- xpack.security.authc.realms.ldap.ldap1.bind_dn=cn=Manager,dc=houpu,dc=com- xpack.security.authc.realms.ldap.ldap1.bind_password=changeme- xpack.security.authc.realms.ldap.ldap1.user_search.base_dn=dc=houpu,dc=com- xpack.security.authc.realms.ldap.ldap1.user_search.filter=(cn={0})- xpack.security.authc.realms.ldap.ldap1.group_search.base_dn=dc=houpu,dc=com- xpack.security.authc.realms.ldap.ldap1.files.role_mapping=/usr/share/elasticsearch/config/role_mapping.yml- xpack.security.authc.realms.ldap.ldap1.unmapped_groups_as_roles=false三、重启elk
docker-compose down
docker-compose up -d四、查看效果
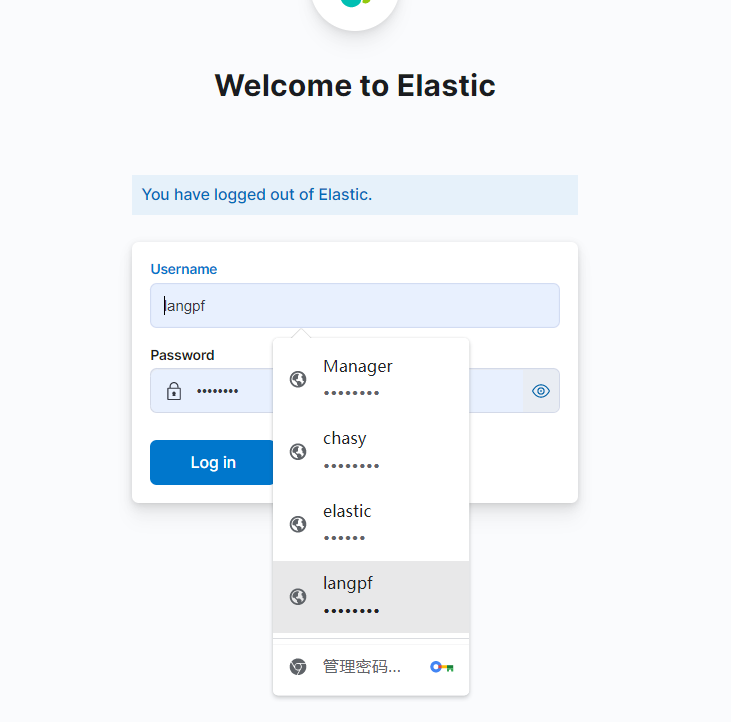
管理员用户:拥有所有权限
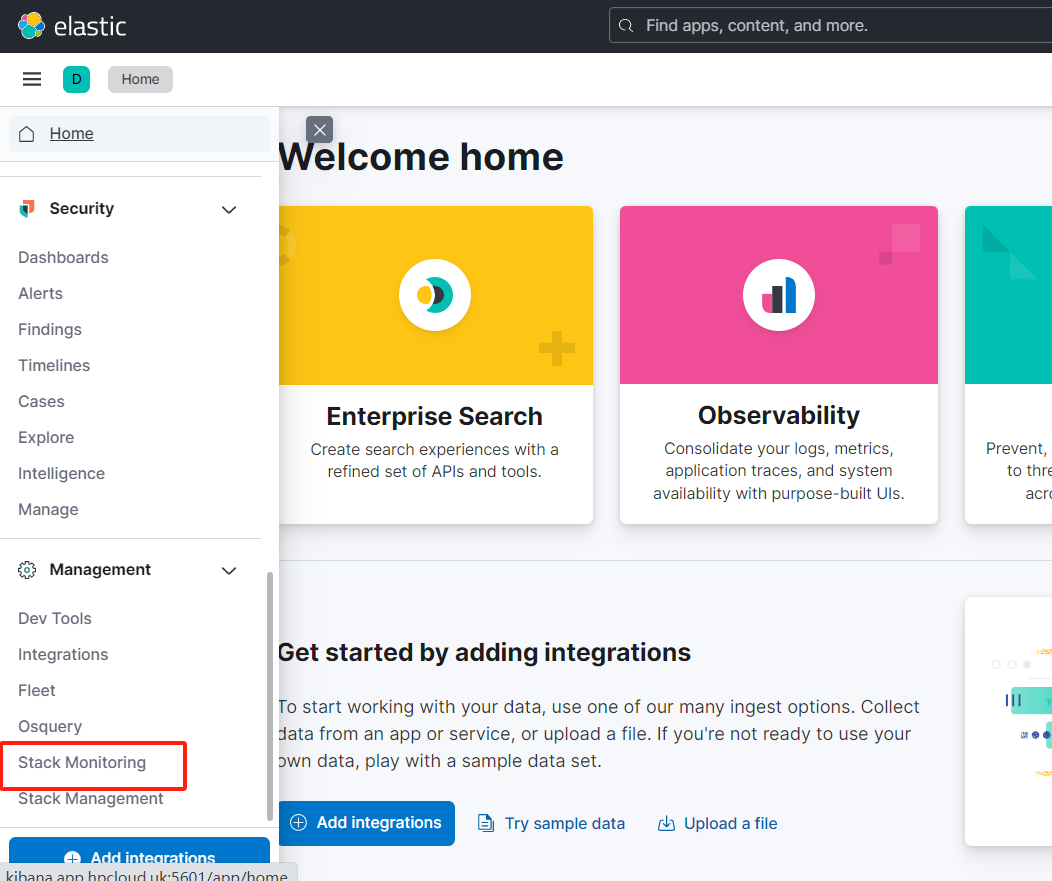
kibana_user用户:无discover权限,无stack monitor权限,也无dev-tools api权限
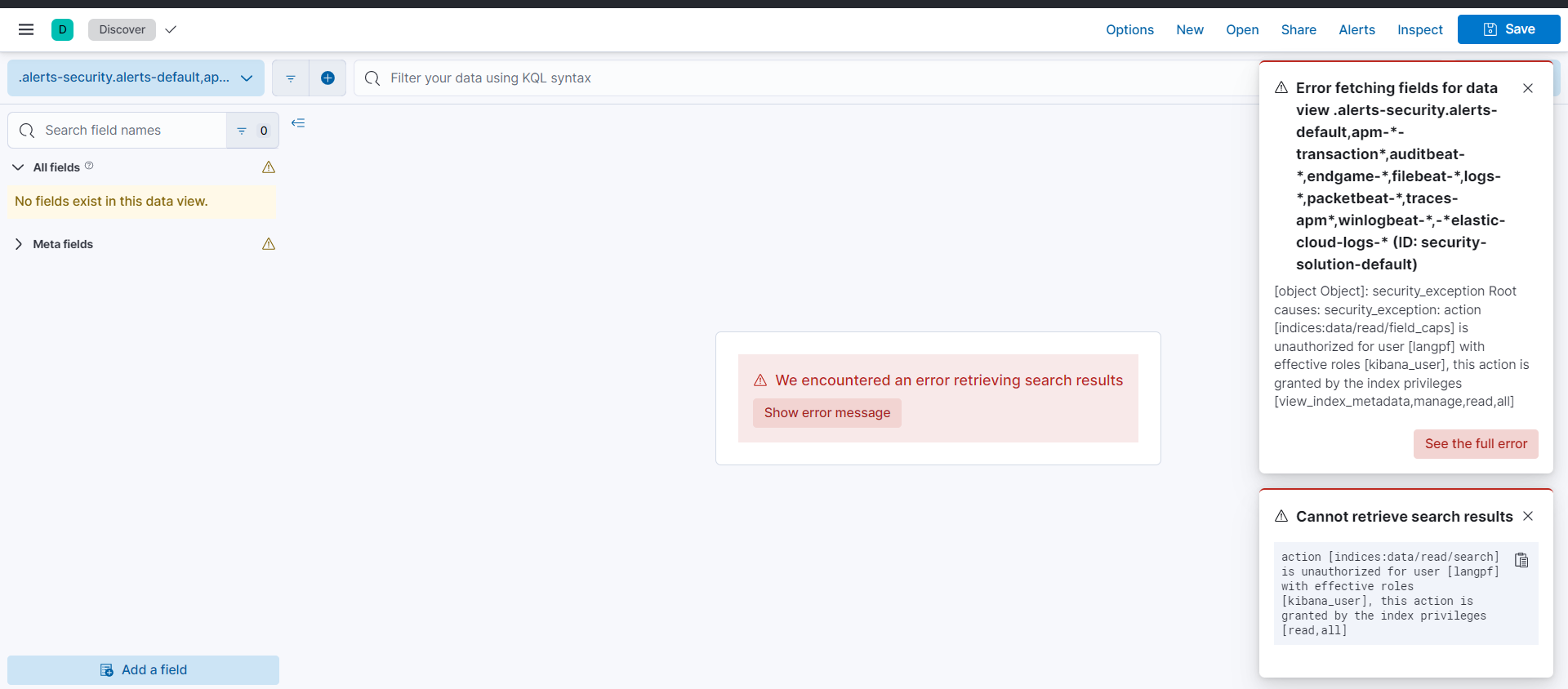
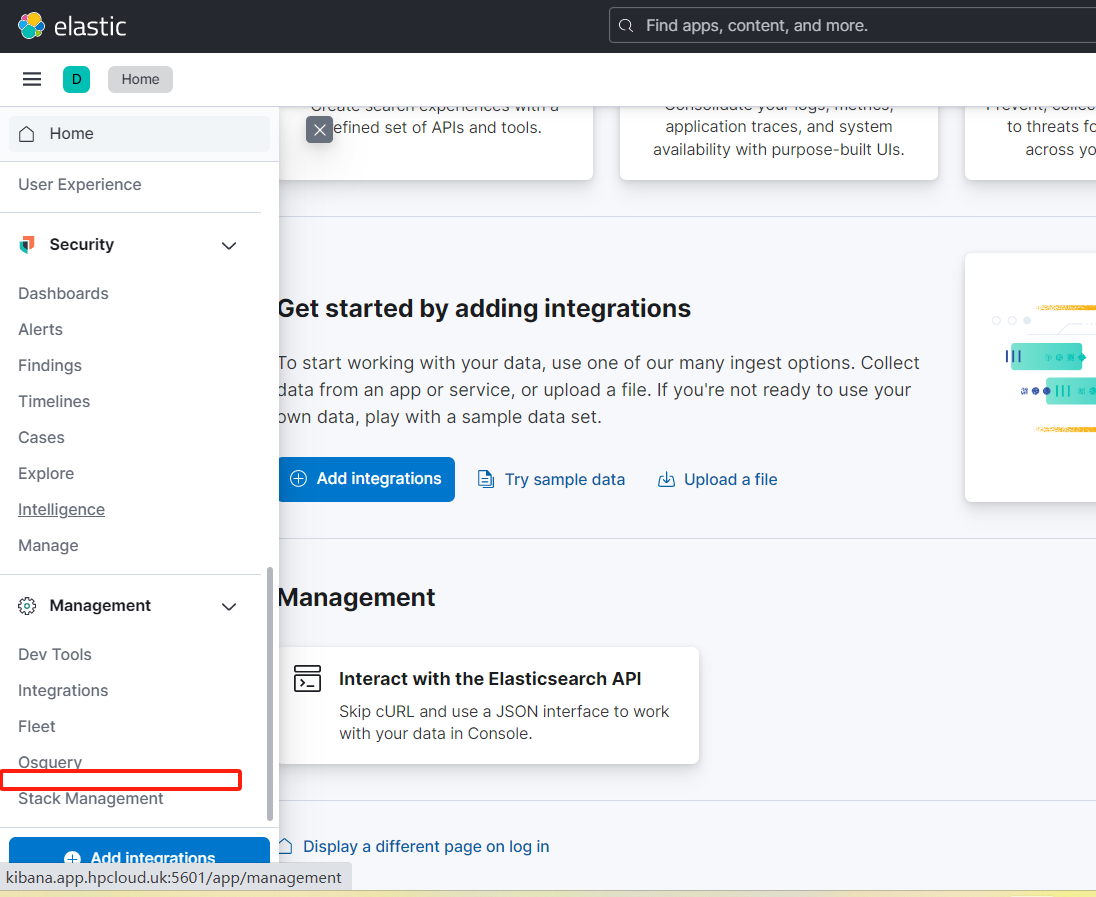

test用户:不在角色列表中,无任何权限
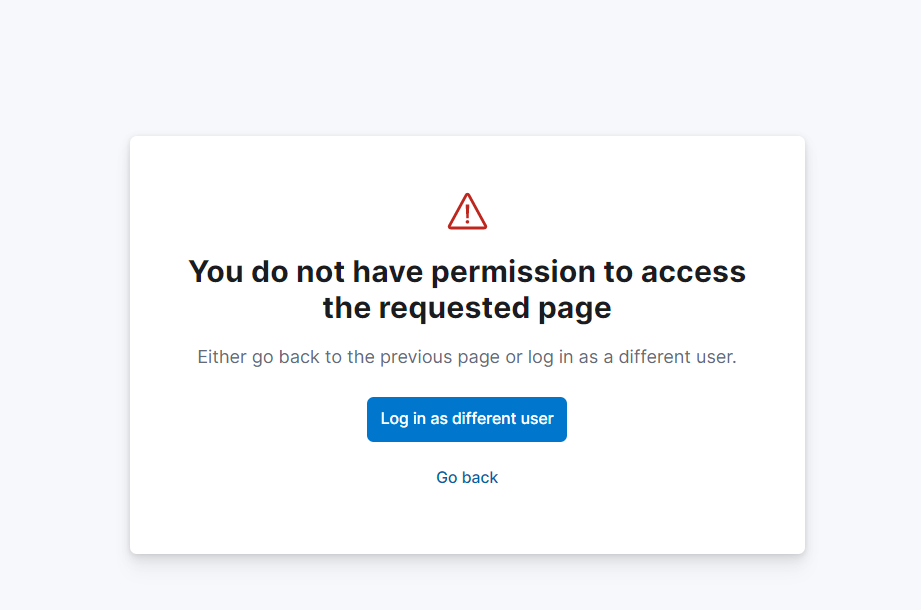
附:角色管理API常用请求:
# Click the Variables button, above, to create your own variables.
GET ${exampleVariable1} // _search
{"query": {"${exampleVariable2}": {} // match_all}
}GET /_security/roleGET /_security/role_mappingGET /_security/role/kibana_userGET /_security/role/testPUT /_security/role/test
{"indices": [{"names": ["index1", "index2", "log-test-*"],"privileges": ["read"]}],"applications": [{"application": "kibana-.kibana","privileges": ["all"],"resources": ["*"]}]
}POST /_security/realm_cache/_clear