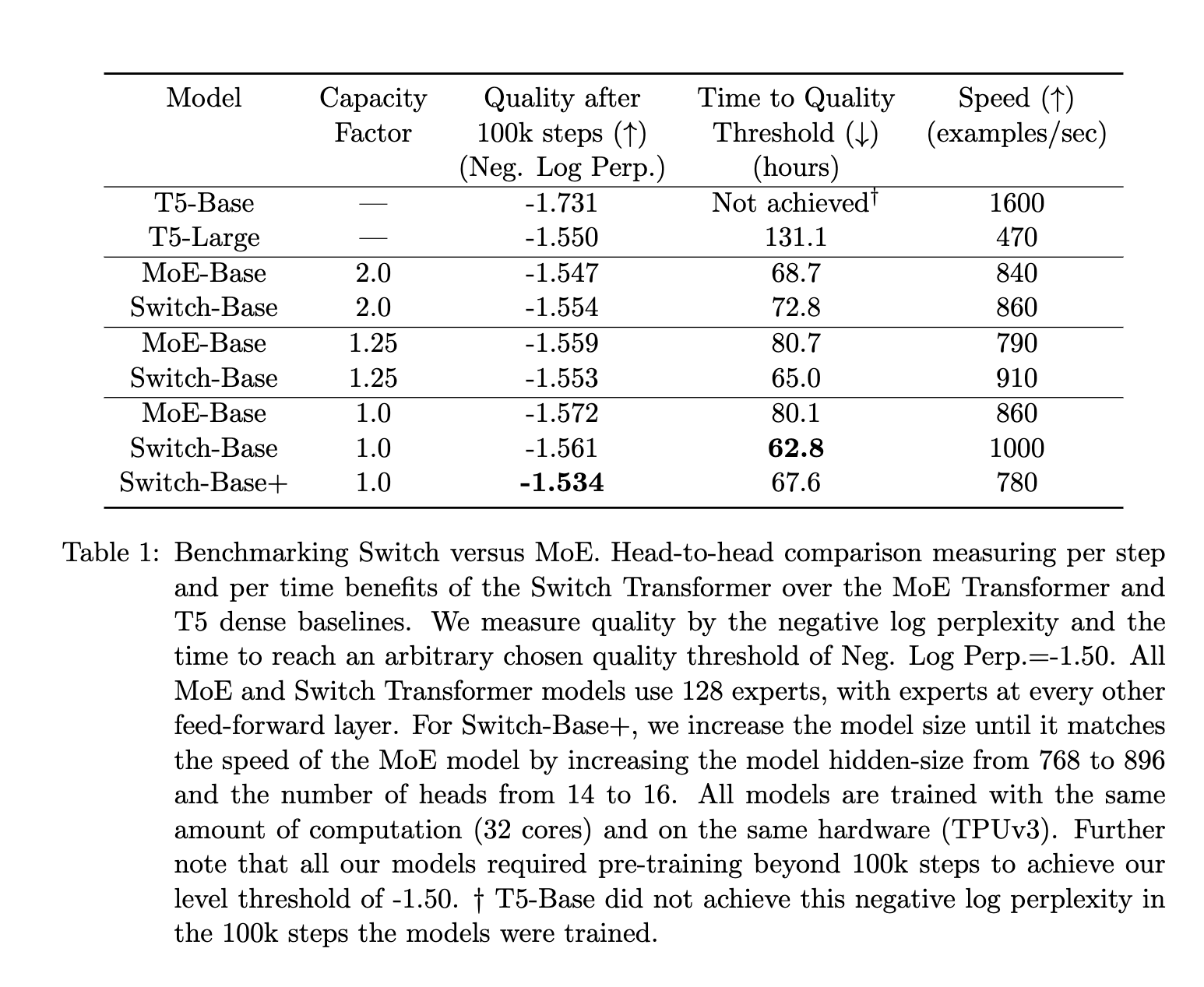
每次手动登录特别麻烦,而且时不时断一下,因此搞个脚本让它定时监测、断开重连比较方便。这里不讲这个脚本怎么写,只记录一下登录时的抓包内容。
蒜了,直接上解析吧,也不复杂,相信大家一目了然。
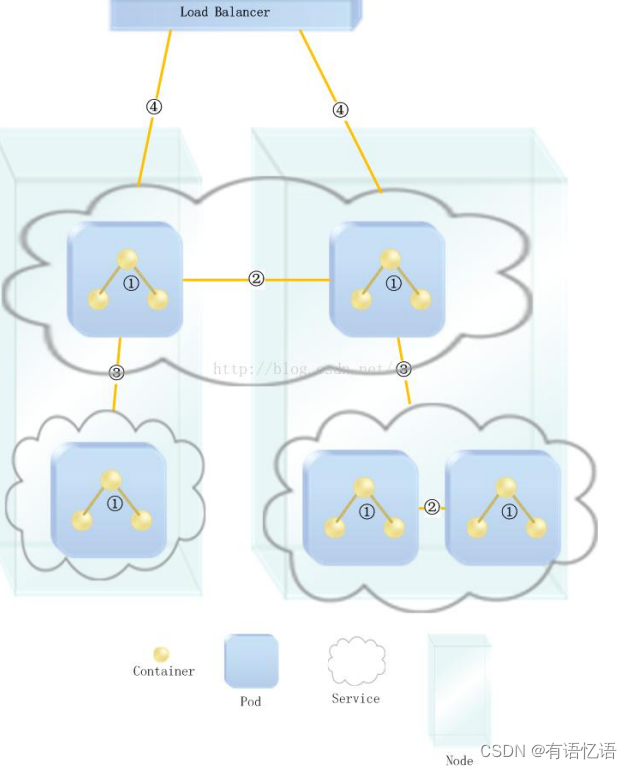
目录
抓包分析
postman测试请求
python模拟
抓包分析
办公区域网络的登录地址:https://172.25.31.129:9444/
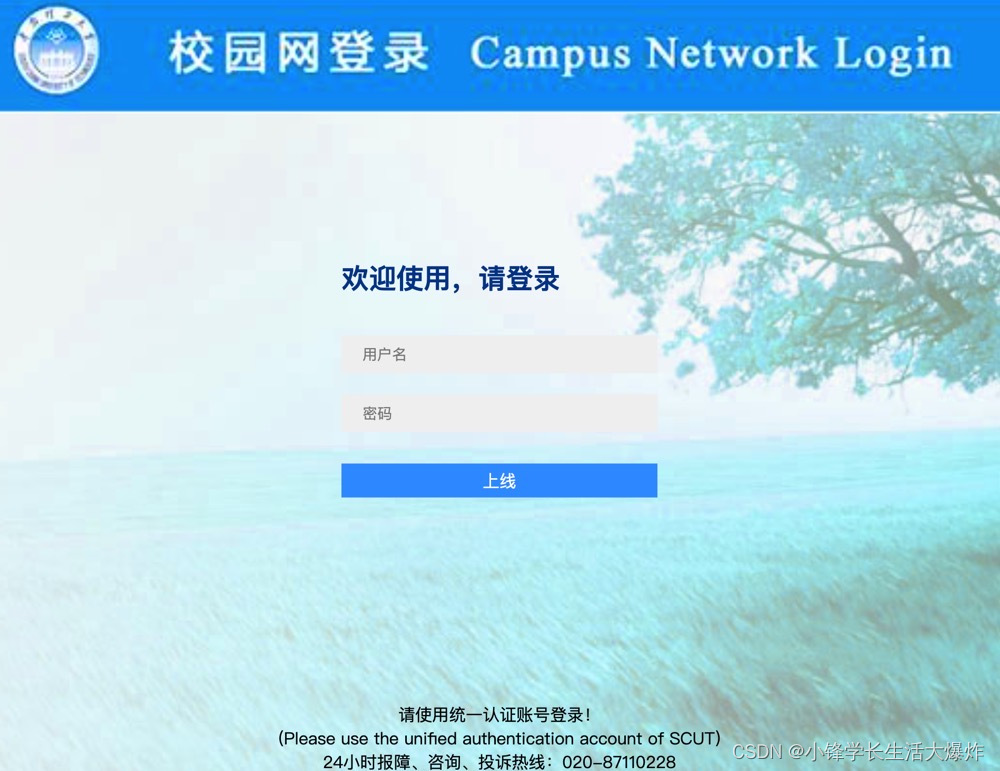
对于Base64的编码,可以看这里:Base64 在线编码解码 | Base64 加密解密 - Base64.us
提取主要信息:
请求 URL:
https://172.25.31.129:9444/byod/byodrs/login/defaultLogin请求方法:
POST请求头:
cookie=testcookie=yes; userip=分给你的IP,连上WiFi就会给你请求负载:(为方便展示,实际请求时候不要有空格或者换行)
{"username":"你的学号","userPassword":"登录密码并使用base64编码","serviceSuffixId":"-1","dynamicPwdAuth":false,"code":"","codeTime":"","validateCode":"","licenseCode":"","userGroupId":0,"validationType":0,"guestManagerId":0,"shopIdE":null,"wlannasid":null
}Postman测试请求
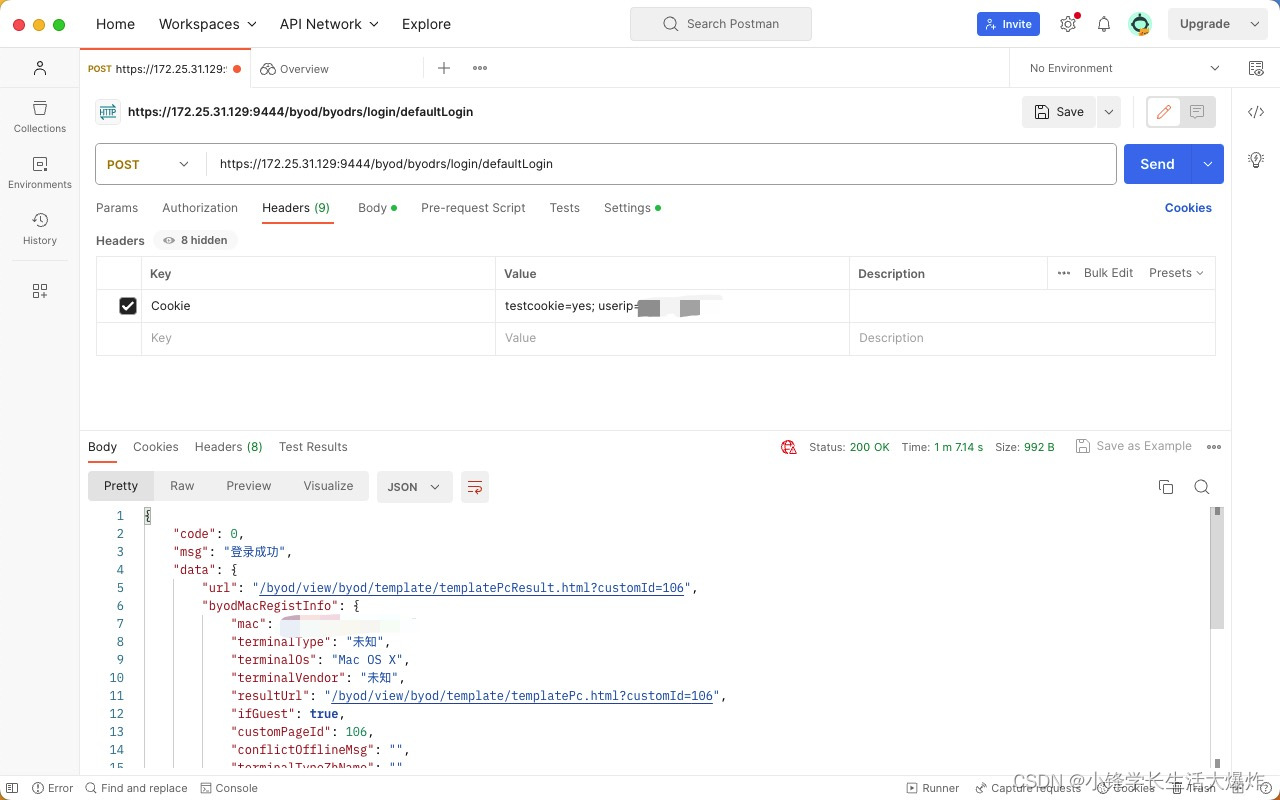
Python模拟
import requests
import socketdef get_local_ip():ip_address = ''try:hostname = socket.gethostname()ip_address = socket.gethostbyname(hostname)except:passreturn ip_addressurl = r'https://172.25.31.129:9444/byod/byodrs/login/defaultLogin'
data = {"userName":"学号","userPassword":"密码的base64编码","serviceSuffixId":"-1","dynamicPwdAuth":False,"code":"","codeTime":"","validateCode":"","licenseCode":"","userGroupId":0,"validationType":0,"guestManagerId":0,"shopIdE":None,"wlannasid":None}
headers = {"cookie":"testcookie=yes; userip="+get_local_ip()}res = requests.post(url, json=data, headers=headers, verify=False).text
print(res)