DNS服务一些理论
域名系统(Domain Name System,DNS)是互联网的核心应用服务,可以通过IP地址查询到域名,也可以通过域名查询到IP地址。
FQDN(Full Qualified Domain Name)是完全限定域名,可以从逻辑上准确的指出主机在什么地方,FQDN总是以主机名开始并且以顶级域名结束,从全域名中可以看出主机在域名树中的位置
域名的分类:
根域名(
.)
顶级域名(.com、.cn、.edu等)
DNS的解析类型:
正向解析:把主机名解析为IP地址。
反向解析:把IP地址解析为主机名。
DNS服务器分类:
主DNS服务器
从DNS服务器
缓存DNS服务器
bind安装及其配置文件
yum install -y bind bind-utils安装软件包。
安装完成如下图:
/etc/named.conf是bind的主配置文件,我这里/etc/named.conf的内容如下:
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// See the BIND Administrator's Reference Manual (ARM) for details about the
// configuration located in /usr/share/doc/bind-{version}/Bv9ARM.htmloptions {listen-on port 53 { 127.0.0.1; };listen-on-v6 port 53 { ::1; };directory "/var/named";dump-file "/var/named/data/cache_dump.db";statistics-file "/var/named/data/named_stats.txt";memstatistics-file "/var/named/data/named_mem_stats.txt";recursing-file "/var/named/data/named.recursing";secroots-file "/var/named/data/named.secroots";allow-query { localhost; };/*- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.- If you are building a RECURSIVE (caching) DNS server, you need to enablerecursion.- If your recursive DNS server has a public IP address, you MUST enable accesscontrol to limit queries to your legitimate users. Failing to do so willcause your server to become part of large scale DNS amplificationattacks. Implementing BCP38 within your network would greatlyreduce such attack surface*/recursion yes;dnssec-enable yes;dnssec-validation yes;/* Path to ISC DLV key */bindkeys-file "/etc/named.root.key";managed-keys-directory "/var/named/dynamic";pid-file "/run/named/named.pid";session-keyfile "/run/named/session.key";
};logging {channel default_debug {file "data/named.run";severity dynamic;};
};zone "." IN {type hint;file "named.ca";
};include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
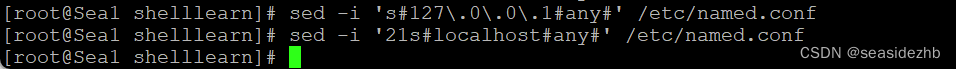
listen-on port 53 { 127.0.0.1; };表示监听ip是127.0.0.1的53端口,allow-query { localhost; };表示只能本地能够查询。sed -i 's#127\.0\.0\.1#any#' /etc/named.conf把127.0.0.1改成any,这样就表示监听这个计算机中所有的网卡ip,sed -i '21s#localhost#any#' /etc/named.conf把第21行中的localhost改成any,这样就表示所有的ip都可以访问这台计算机。
named-checkconf可以看一下/etc/named.conf文件,是否有问题,要是格式没有问题的话,没有任何输出。
sed -n '/^zone/,/};/{p}' /etc/named.conf可以看到zone区域的配置信息,发现.根域名的配置在named.ca文件里边,而named.ca是在/var/named目录下。
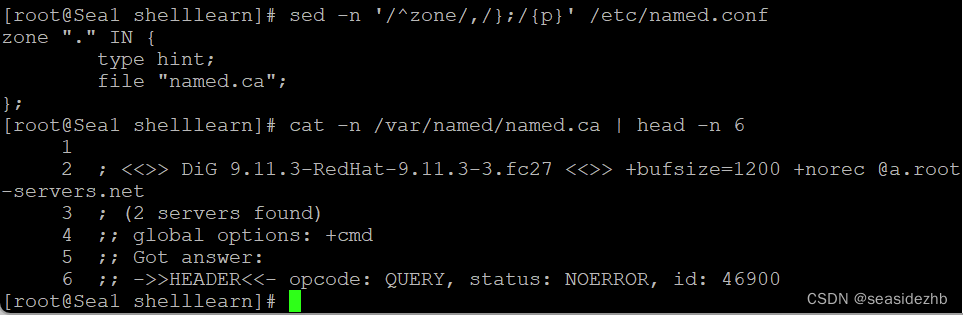
/var/named/named.ca里边内容如下所示:
; <<>> DiG 9.11.3-RedHat-9.11.3-3.fc27 <<>> +bufsize=1200 +norec @a.root-servers.net
; (2 servers found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 46900
;; flags: qr aa; QUERY: 1, ANSWER: 13, AUTHORITY: 0, ADDITIONAL: 27;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1472
;; QUESTION SECTION:
;. IN NS;; ANSWER SECTION:
. 518400 IN NS a.root-servers.net.
. 518400 IN NS b.root-servers.net.
. 518400 IN NS c.root-servers.net.
. 518400 IN NS d.root-servers.net.
. 518400 IN NS e.root-servers.net.
. 518400 IN NS f.root-servers.net.
. 518400 IN NS g.root-servers.net.
. 518400 IN NS h.root-servers.net.
. 518400 IN NS i.root-servers.net.
. 518400 IN NS j.root-servers.net.
. 518400 IN NS k.root-servers.net.
. 518400 IN NS l.root-servers.net.
. 518400 IN NS m.root-servers.net.;; ADDITIONAL SECTION:
a.root-servers.net. 518400 IN A 198.41.0.4
b.root-servers.net. 518400 IN A 199.9.14.201
c.root-servers.net. 518400 IN A 192.33.4.12
d.root-servers.net. 518400 IN A 199.7.91.13
e.root-servers.net. 518400 IN A 192.203.230.10
f.root-servers.net. 518400 IN A 192.5.5.241
g.root-servers.net. 518400 IN A 192.112.36.4
h.root-servers.net. 518400 IN A 198.97.190.53
i.root-servers.net. 518400 IN A 192.36.148.17
j.root-servers.net. 518400 IN A 192.58.128.30
k.root-servers.net. 518400 IN A 193.0.14.129
l.root-servers.net. 518400 IN A 199.7.83.42
m.root-servers.net. 518400 IN A 202.12.27.33
a.root-servers.net. 518400 IN AAAA 2001:503:ba3e::2:30
b.root-servers.net. 518400 IN AAAA 2001:500:200::b
c.root-servers.net. 518400 IN AAAA 2001:500:2::c
d.root-servers.net. 518400 IN AAAA 2001:500:2d::d
e.root-servers.net. 518400 IN AAAA 2001:500:a8::e
f.root-servers.net. 518400 IN AAAA 2001:500:2f::f
g.root-servers.net. 518400 IN AAAA 2001:500:12::d0d
h.root-servers.net. 518400 IN AAAA 2001:500:1::53
i.root-servers.net. 518400 IN AAAA 2001:7fe::53
j.root-servers.net. 518400 IN AAAA 2001:503:c27::2:30
k.root-servers.net. 518400 IN AAAA 2001:7fd::1
l.root-servers.net. 518400 IN AAAA 2001:500:9f::42
m.root-servers.net. 518400 IN AAAA 2001:dc3::35;; Query time: 24 msec
;; SERVER: 198.41.0.4#53(198.41.0.4)
;; WHEN: Thu Apr 05 15:57:34 CEST 2018
;; MSG SIZE rcvd: 811
接下来用www.baidu.com来解释一下解析过程:首先先查询根域名(.),这里有13个根域名服务器,哪个快可以选那个服务器,比如选中了ANSWER SECTION下d.root-servers.net.,那么就需要到ADDITIONAL SECTION找到对应的ip为199.7.91.13,然后199.7.91.13到.com服务器里边查找,之后.com服务器到.baidu服务器查找,找到之后就返回结果。
设置主域名解析
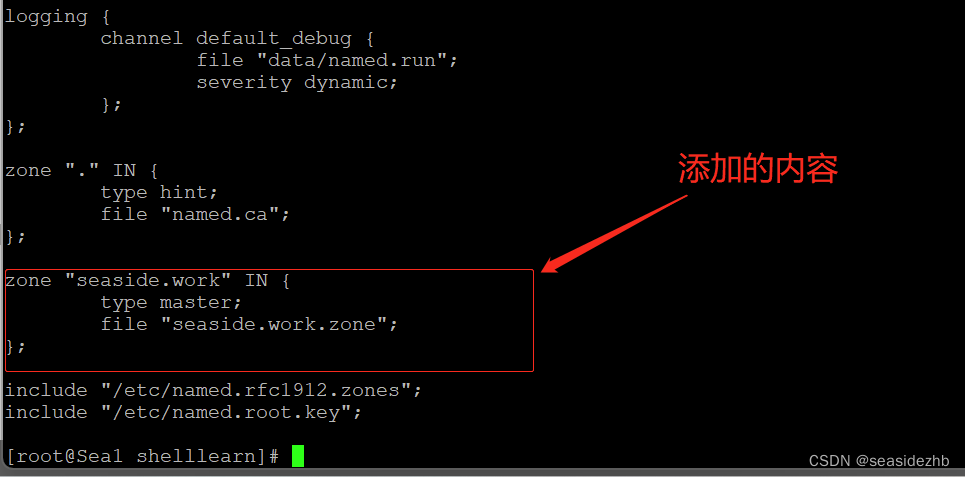
把下边的内容添加到/etc/named.conf 对应的位置。
zone "seaside.work" IN {type master;file "seaside.work.zone";
};
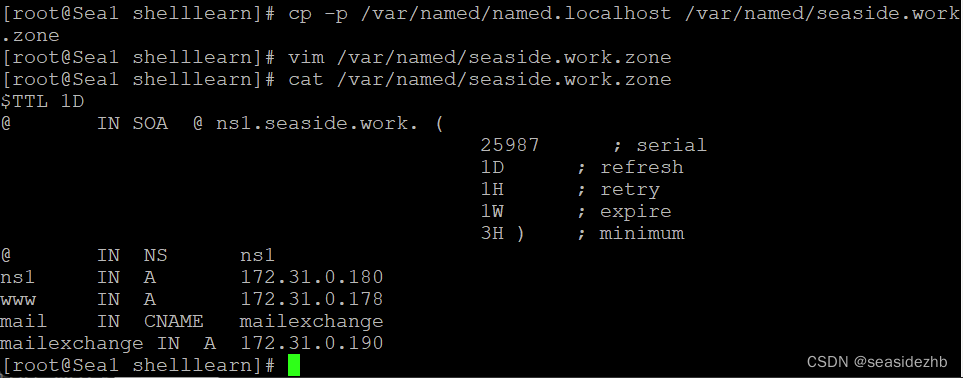
cp -p /var/named/named.localhost /var/named/seaside.work.zone把/var/named/named.localhost按照原来的权限复制成/var/named/seaside.work.zone,之后把/var/named/seaside.work.zone里边的内容修改如下:
$TTL 1D
@ IN SOA @ ns1.seaside.work. (25987 ; serial1D ; refresh1H ; retry1W ; expire3H ) ; minimum
@ IN NS ns1
ns1 IN A 172.31.0.180
www IN A 172.31.0.178
mail IN CNAME mailexchange
mailexchange IN A 172.31.0.190
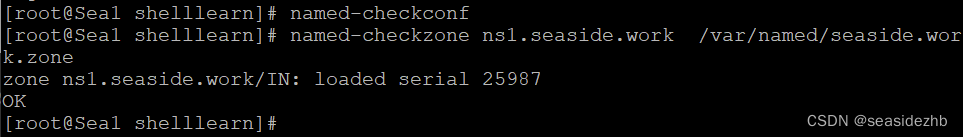
named-checkconf检查主配置文件语法或者参数错误,没有输出就是正确的。
named-checkzone ns1.seaside.work /var/named/seaside.work.zone检查数据配置文件/var/named/seaside.work.zone中ns1.seaside.work这个zone中语法或参数的错误,最后输出OK,就是没有错误。
systemctl start named打开named服务。
进行测试
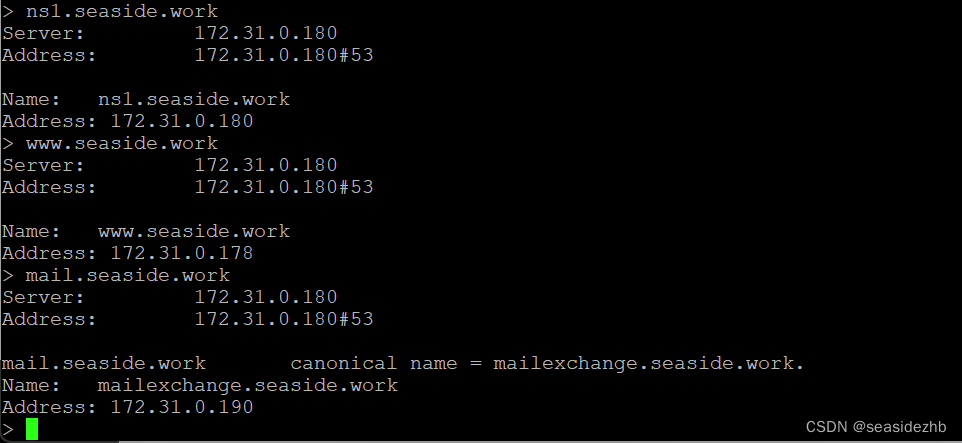
nslookup进行测试,server 172.31.0.180,注意server后边输入真实服务器ip。

ns1.seaside.work、www.seaside.work和mail.seaside.work都正常解析出来了。
此文章为8月Day 28学习笔记,内容来源于极客时间《Linux 实战技能 100 讲》。







![java八股文面试[数据结构]——HashMap和HashTable区别](https://img-blog.csdnimg.cn/70db7c62a72d4052850f0adf745622f5.png)