在之前的博客Python爆破shadow文件密码脚本(简化版)中我们做了简化版的爆破shadow文件密码的python脚本,接下来在之前代码的基础上改进:
import crypt
shadow_line="root:$y$j9T$uEgezfJhn7Ov5naU8bzZt.$9qIqkWYObaXajS5iLDA43uFhdrtt4ZfbmiZjkZFYve2:18711:0:99999:7:::"
print(f"[+] The shadow line is {shadow_line}")crypt_text=shadow_line.split(":")[1]
print(f"[+] The crypt text is {crypt_text}")salt=crypt_text[0:crypt_text.rindex("$")]
print(f"[+] The salt is {salt}")password="root"
new_crypt_text=crypt.crypt(password,salt)if new_crypt_text == crypt_text:print(f"[+] password is {password}"")
else:print(f"[+] password not found!")
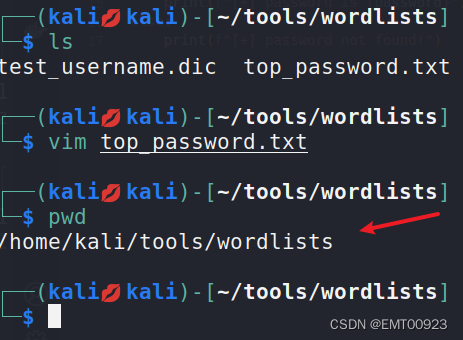
在kali中找到一个密码字典,查看它的绝对路径复制:
将代码中的password="123456"替换成下面代码
line.strip()函数首尾去空格
print(f"Trying password:")显示爆破的密码和过程
flie_path="/home/kali/tools/wordlists/top_password.txt"
wirh open(file=file_path,mode="r") as f:for line in f:password = line.strip()print(f"Trying password:{password}")
由于添加了一个for循环,再稍作修改,让password not found!在for循环结束后输出,并给密码加上绿色醒目:
from termcolor import colored
import cryptshadow_line="root:$y$j9T$uEgezfJhn7Ov5naU8bzZt.$9qIqkWYObaXajS5iLDA43uFhdrtt4ZfbmiZjkZFYve2:18711:0:99999:7:::"
print(f"[+] The shadow line is {shadow_line}")crypt_text=shadow_line.split(":")[1]
print(f"[+] The crypt text is {crypt_text}")salt=crypt_text[0:crypt_text.rindex("$")]
print(f"[+] The salt is {salt}")flie_path="/home/kali/tools/wordlists/top_password.txt"
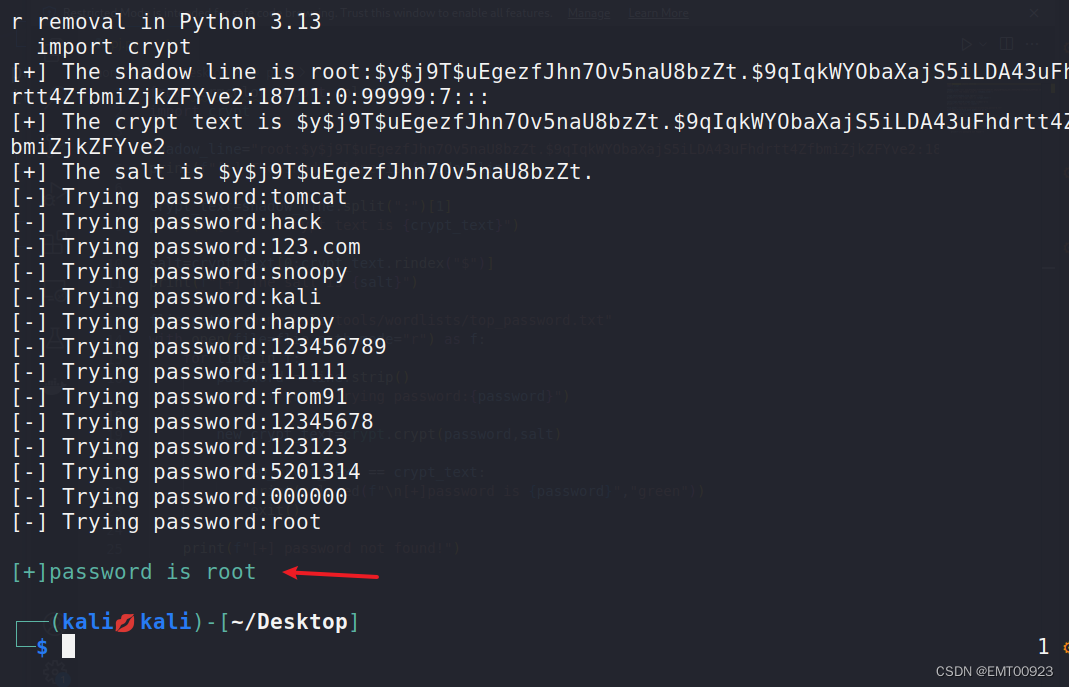
with open(file=flie_path,mode="r") as f:for line in f:password = line.strip()print(f"\r[-] Trying password:{password}")new_crypt_text=crypt.crypt(password,salt)if new_crypt_text == crypt_text:print(colored(f"\n[+]password is {password}","green"))exit()print(f"[+] password not found!")
如图,爆破出密码为root: