#因为是最小化安装,先安装vim编辑器,net-tools查看端口,psmisc可以使用killall命令bash-completion tab补全命令(需要重启生效)
[root@localhost ~]# yum -y install net-tools psmisc vim bash-completion
[root@localhost ~]# tar zxvf nginx-1.17.6.tar.gz #因为等下要源码安装nginx,所以先安装gcc make编译软件,pcre-devel是为了使nginx支持正则表达式,openssl-devel是为了nginx加密
[root@localhost ~]# cd nginx-1.17.6/ && ls
auto CHANGES.ru configure html Makefile objs src
CHANGES conf contrib LICENSE man README
[root@localhost ~]# yum -y install gcc make pcre-devel openssl-devel
[root@localhost nginx-1.17.6]# ./configure --prefix=/usr/local/nginx --user=nginx --with-http_ssl_module && make && make install
--prefix 指定安装位置
--user 指定以哪位用户身份启动nginx
--with-http-ssl_module 使用安全网站模块
[root@localhost nginx-1.17.6]# cd /usr/local/nginx/
[root@localhost nginx]# ls
conf html logs sbin
[root@localhost nginx]# sbin/nginx
nginx: [emerg] getpwnam("nginx") failed 启动失败的原因是,编译时指定以nginx用户启动,服务器没有nginx用户,所以失败
[root@localhost nginx]# useradd nginx #创建个nginx用户
[root@localhost nginx]# sbin/nginx
[root@localhost nginx]# netstat -ntupl |grep 80
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 4615/nginx: master nginx认证
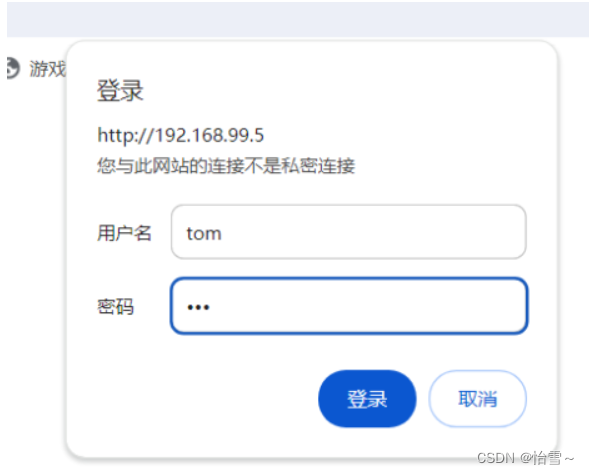
访问nginx网站时,需要输入正确的用户名和密码才能访问
配置如下:
[root@localhost nginx]# pwd
/usr/local/nginx
[root@localhost nginx]# vim conf/nginx.conf
server {listen 80;server_name localhost;auth_basic "password";auth_basic_user_file "/usr/local/nginx/pass"; 认证文件
[root@localhost nginx]# sbin/nginx -s reload
htpasswd用于为指定用户生成基于网页用户身份认证的密码,由httpd-tools软件包提供。支持3种加密算法:MD5、SHA和系统上的crypt()函数,不指定算法时,默认为md5。
[root@localhost ~]# yum -y install httpd-tools
[root@localhost ~]# htpasswd -c pass tom
New password:
Re-type new password:
Adding password for user tom
[root@localhost nginx]# ls
client_body_temp fastcgi_temp logs proxy_temp scgi_temp
conf html pass sbin uwsgi_temp
[root@localhost nginx]# cat pass
tom:$apr1$KVns/c9N$K3YF4Lnb3lM2nMcH/WF1r/
添加第二个用户认证以上,不需要加 -c
[root@localhost nginx]# htpasswd pass jerry
New password:
Re-type new password:
Adding password for user jerry
[root@localhost nginx]# cat pass
tom:$apr1$KVns/c9N$K3YF4Lnb3lM2nMcH/WF1r/
jerry:$apr1$e/pzkrYu$90EooPydjHbG.fzc8Na6c1浏览器访问ip地址
虚拟主机
可以将网络上的每一台计算机分成多个虚拟主机,每个虚拟主机可以独立对外提供www服务,这样就可以实现一台主机对外提供多个web服务,每个虚拟主机之间是独立的,互不影响。
配置如下:
基于域名的虚拟主机
[root@localhost nginx]# vim conf/nginx.conf
server {listen 80;server_name www.b.com;root html_b;index index.html;}
server {listen 80;server_name www.a.com;#charset koi8-r;
#access_log logs/host.access.log main;location / {root html_a;index index.html index.html;
[root@localhost nginx]# mkdir html_b && echo "test-b~~~" > html_b/index.html
[root@localhost nginx]# mkdir html_a && echo "test_a" > html_a/index.html
[root@localhost nginx]# sbin/nginx -s reload
这里没有搭建DNS服务器,就用主机映射文件暂时替用
[root@localhost nginx]# vim /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.99.5 www.a.com
192.168.99.5 www.b.com
[root@localhost nginx]# curl www.b.com
test-b~~~
[root@localhost nginx]# curl www.a.com
test_a基于ip的虚拟主机
[root@localhost nginx]# ifconfig eth0 | sed -n "/inet/p" | awk '{print $2}' |grep ^1
192.168.88.5
[root@localhost nginx]# ifconfig eth1 | sed -n "/inet/p" | awk '{print $2}' |grep ^1
192.168.99.5
[root@localhost nginx]# vim conf/nginx.conf
server {listen 80;server_name 192.168.99.5;root html_b;index index.html;}
server {listen 80;server_name 192.168.88.5;#charset koi8-r;
#access_log logs/host.access.log main;location / {root html_a;index index.html index.htm;}
[root@localhost nginx]# sbin/nginx -s reload
[root@localhost nginx]# curl 192.168.88.5
test_a
[root@localhost nginx]# curl 192.168.99.5
test-b~~~基于端口的虚拟主机
[root@localhost nginx]# vim conf/nginx.conf
server {listen 88;server_name www.a.com;root html_b;index index.html;}
server {listen 80;server_name www.a.com;#charset koi8-r;
#access_log logs/host.access.log main;location / {root html_a;index index.html index.htm;}
[root@localhost nginx]# sbin/nginx -s reload
[root@localhost nginx]# curl www.a.com:88
test-b~~~
[root@localhost nginx]# curl www.a.com:80
test_a
nginx加密网站
https协议原理 首先,客户端与服务器建立连接,各自生成私钥和公钥,是不同的。服务器返给客户端一个公钥,然后客户端拿着这个公钥把要搜索的东西加密,称之为密文,并连并自己的公钥一起返回给服务器,服务器拿着自己的私钥解密密文,然后把响应到的数据用客户端的公钥加密,返回给客户端,客户端拿着自己的私钥解密密文,把数据呈现出来
配置如下:
[root@localhost nginx]# vim conf/nginx.conf
输入法切换英文,按esc,冒号:,输入以下情况
:101,118s/#/ /
把以下配置的#号取消注释
server {listen 443 ssl;server_name localhost;
ssl_certificate cert.pem;ssl_certificate_key cert.key;
ssl_session_cache shared:SSL:1m;ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;ssl_prefer_server_ciphers on;
location / {root https;index index.html index.htm;}}
[root@localhost nginx]# openssl genrsa > conf/cert.key
Generating RSA private key, 2048 bit long modulus
...+++
.+++
e is 65537 (0x10001)openssl genrsa 命令是会用来生成 RSA 私有秘钥,不会生成公钥,因为公钥提取自私钥。生成时是可以指定私钥长度和密码保护。
[root@localhost nginx]# openssl req -x509 -key conf/cert.key > conf/cert.pem
-key:指定已有的秘钥文件生成秘钥请求
req命令主要的功能有,生成证书请求文件, 查看验证证书请求文件,还有就是生成自签名证书
-x509: 说明生成自签名证书,自签名证书又称为根证书,是自己颁发给自己的证书,即证书中的颁发者和主体名相同。
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:dc
State or Province Name (full name) []:dc
Locality Name (eg, city) [Default City]:dc
Organization Name (eg, company) [Default Company Ltd]:dc
Organizational Unit Name (eg, section) []:dc
Common Name (eg, your name or your server's hostname) []:dc
Email Address []:dc
[root@localhost nginx]# mkdir https && echo "https-test~~" > https/index.html
[root@localhost nginx]# sbin/nginx -s reload
[root@localhost nginx]# curl -k https://192.168.99.5
https-test~~