分析
题目:ez_chal
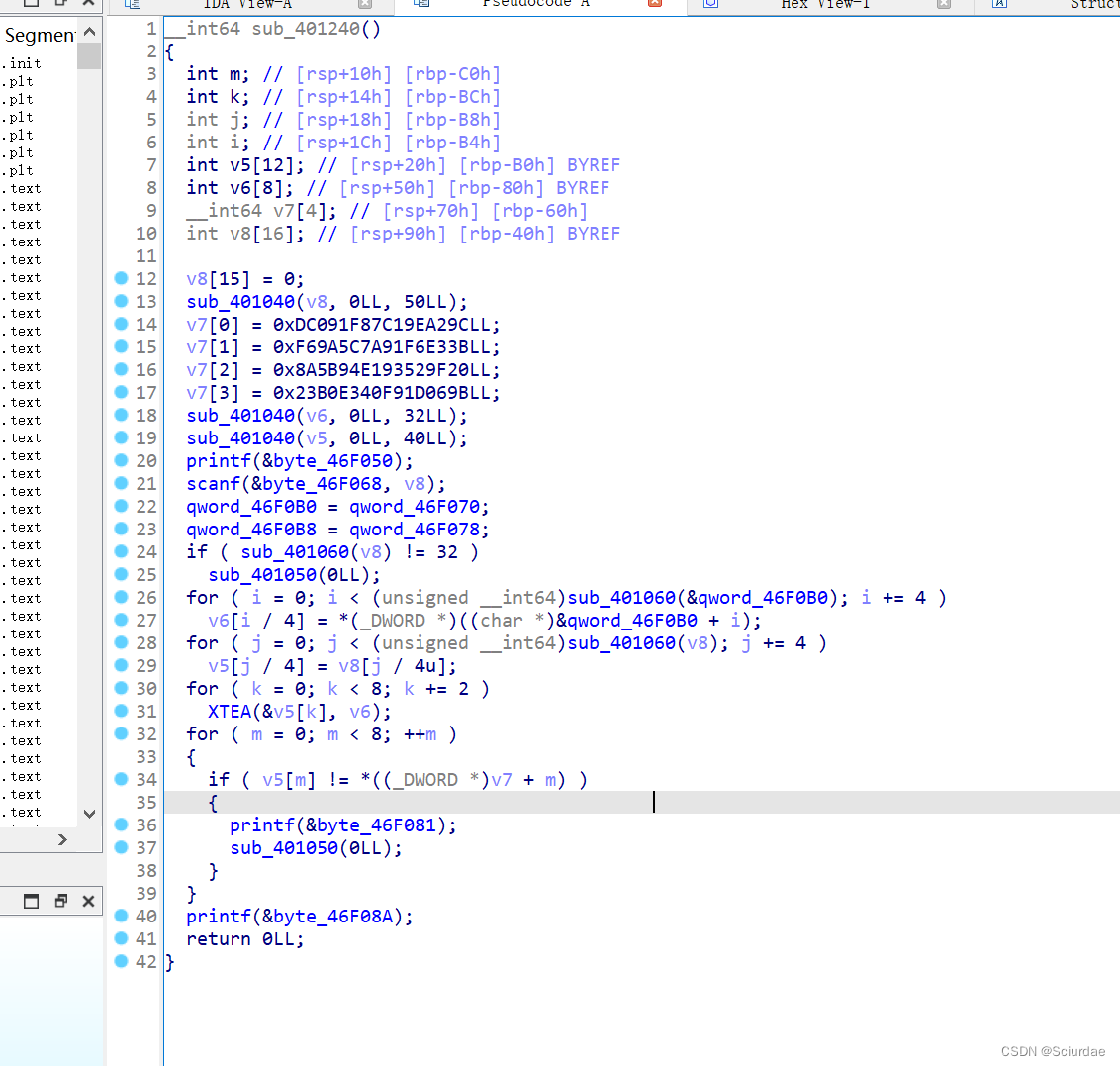
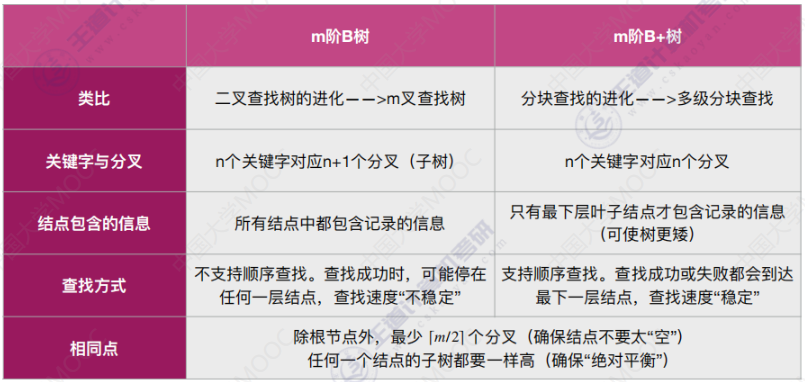
一个XTEA加密,
V6是key,v5是输入,然后v7就是密文。
看了v6,要用动调。
ELF文件用ida的远程调试。
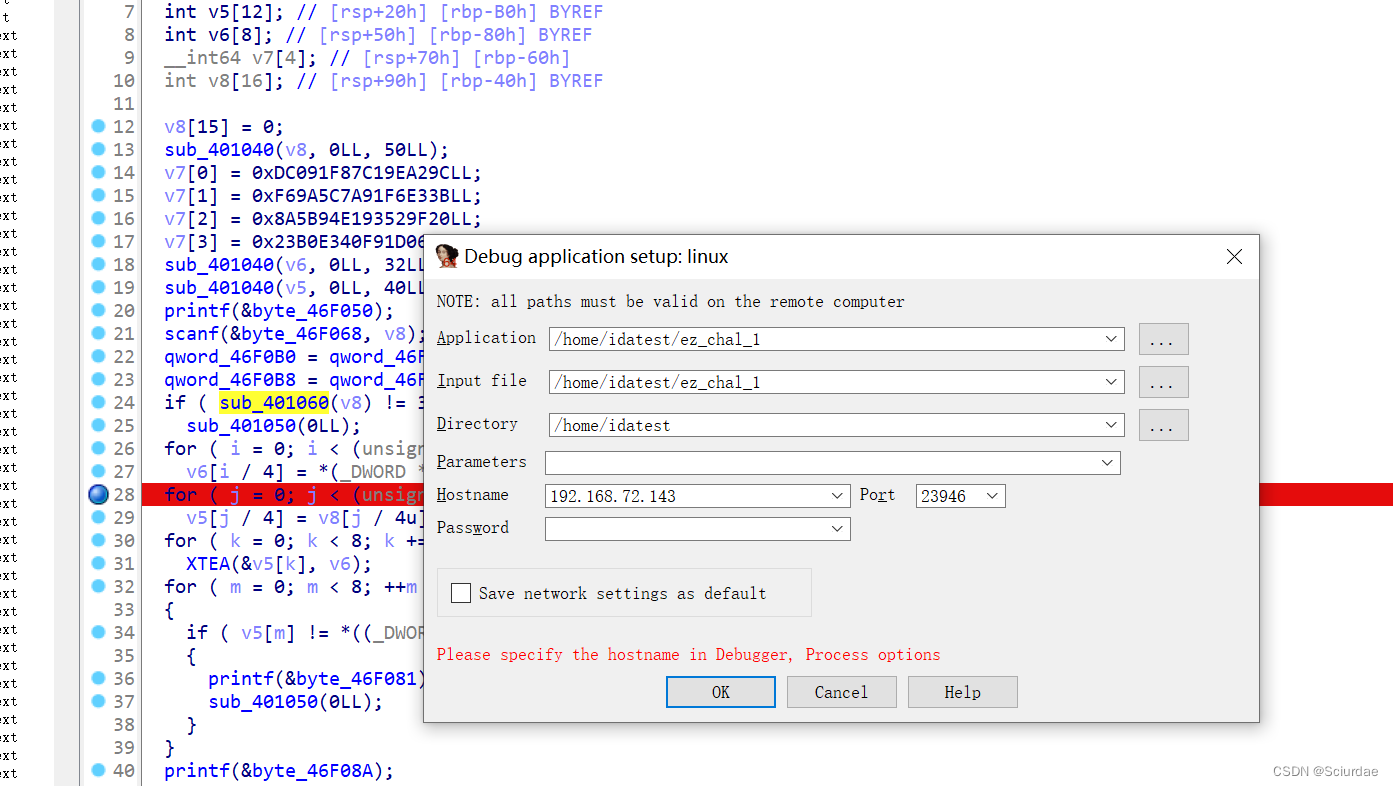
然后在kali上输入长度为32的flag
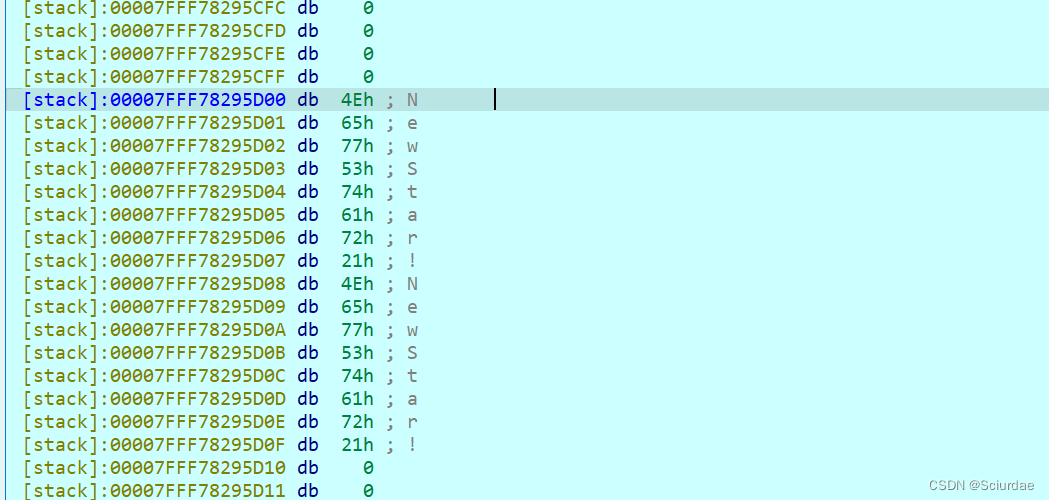
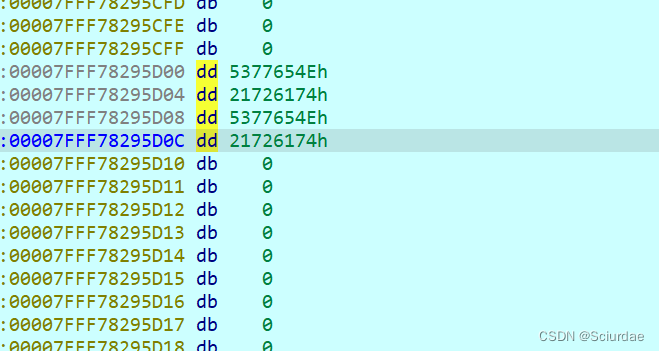
全部转换成dd
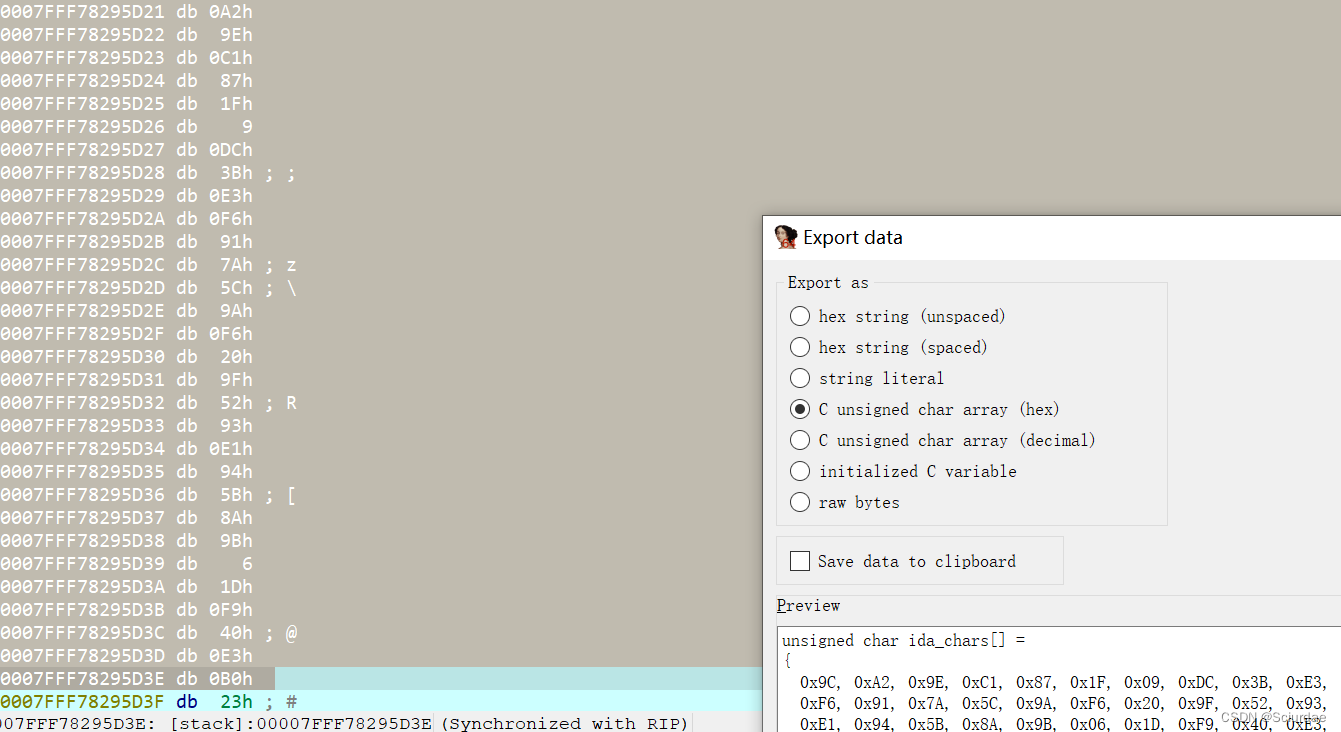
再提取密文。
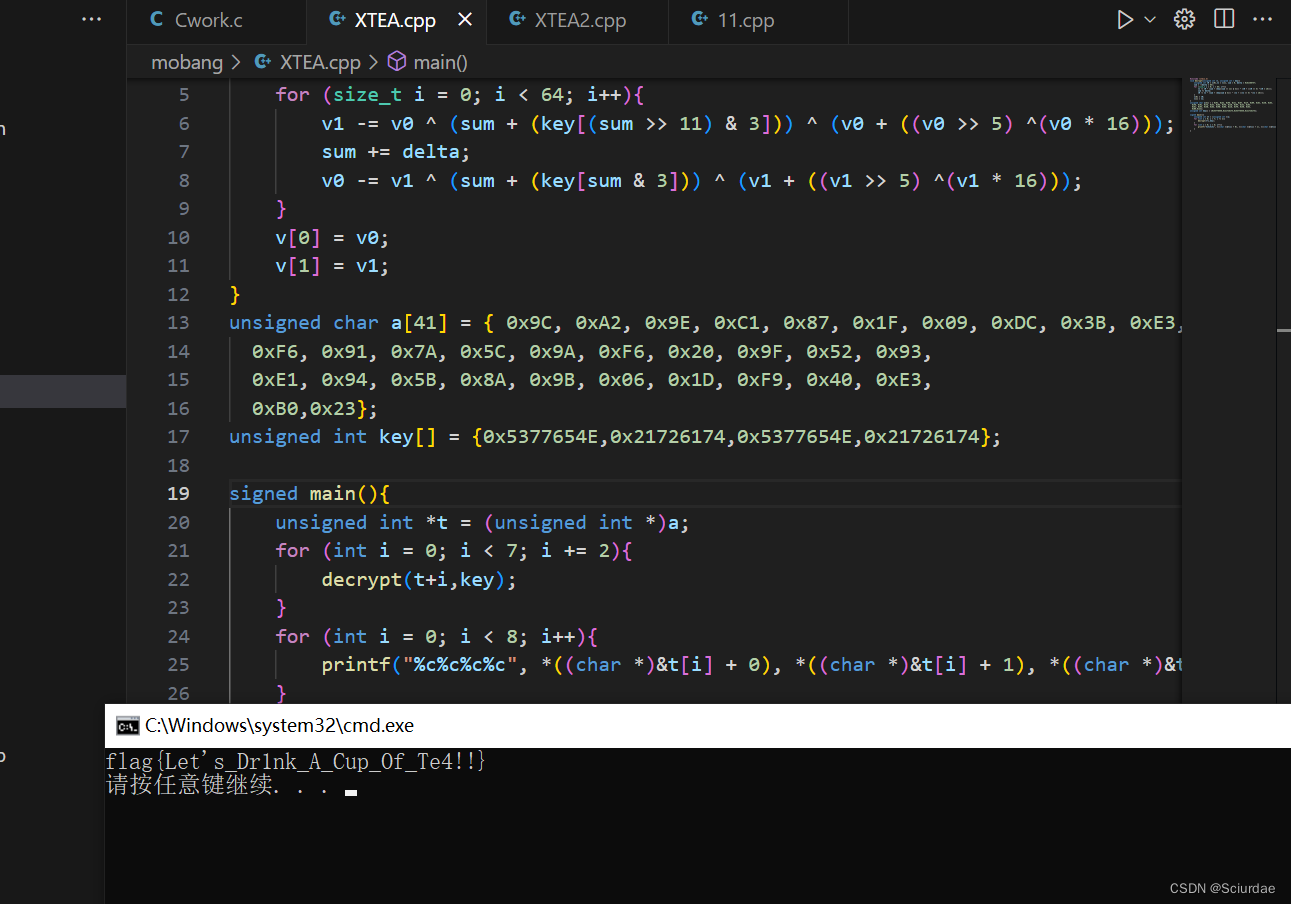
EXP
#include <stdio.h>
void decrypt(unsigned int *v, unsigned int * key){unsigned int v0 = v[0],v1 = v[1], sum = 0, delta = 0x61C88747;sum = -(delta * 64);for (size_t i = 0; i < 64; i++){v1 -= v0 ^ (sum + (key[(sum >> 11) & 3])) ^ (v0 + ((v0 >> 5) ^(v0 * 16)));sum += delta;v0 -= v1 ^ (sum + (key[sum & 3])) ^ (v1 + ((v1 >> 5) ^(v1 * 16)));}v[0] = v0;v[1] = v1;
}
unsigned char a[41] = { 0x9C, 0xA2, 0x9E, 0xC1, 0x87, 0x1F, 0x09, 0xDC, 0x3B, 0xE3, 0xF6, 0x91, 0x7A, 0x5C, 0x9A, 0xF6, 0x20, 0x9F, 0x52, 0x93, 0xE1, 0x94, 0x5B, 0x8A, 0x9B, 0x06, 0x1D, 0xF9, 0x40, 0xE3, 0xB0,0x23};
unsigned int key[] = {0x5377654E,0x21726174,0x5377654E,0x21726174};signed main(){unsigned int *t = (unsigned int *)a;for (int i = 0; i < 7; i += 2){decrypt(t+i,key);}for (int i = 0; i < 8; i++){printf("%c%c%c%c", *((char *)&t[i] + 0), *((char *)&t[i] + 1), *((char *)&t[i] + 2), *((char *)&t[i] + 3));}
}