关于Subdominator
Subdominator是一款针对漏洞奖励计划的子域名安全枚举工具,可用于在漏洞搜寻和侦察过程中进行被动子域名枚举。它旨在通过高效枚举子域名和各种免费被动资源来帮助研究人员和网络安全专业人员发现潜在的安全漏洞。

Subdominator 与各种免费和付费 API 被动源集成,以收集有价值的子域信息。
功能介绍
1、能够快速、强大地子域名枚举能力;
2、45+ 被动结果枚举子域;
3、可配置 API 密钥设置;
4、综合通知系统;
工具要求
aiofiles>=23.2.1
aiohttp>=3.9.4
appdirs>=1.4.4
art>=6.1
beautifulsoup4>=4.11.1
colorama>=0.4.6
fake_useragent>=1.5.0
PyYAML>=6.0.1
Requests>=2.31.0
rich>=13.7.1
urllib3>=1.26.18
工具安装
由于该工具基于Python 3开发,因此我们首先需要在本地设备上安装并配置好最新版本的Python 3环境。
接下来,广大研究人员可以直接使用下列命令将该项目源码克隆至本地:
git clone https://github.com/RevoltSecurities/Subdominator.git
然后切换到项目目录中,使用pip命令和项目提供的requirements.txt安装该工具所需的其他依赖组件:
cd Subdominatorpip install -r requirements.txt
或直接使用pip命令行工具安装最新版本的Subdominator:
pip install git+https://github.com/RevoltSecurities/Subdominator
Subdominator安装成功后即可使用,但如果想以最高级别高效地使用 subdominator,则某些源需要 API 密钥来设置,用户可以使用此命令:
subdominator -ls__ __ _ __ _____ __ __ / /_ ____/ / ____ ____ ___ (_) ____ ____ _ / /_ ____ _____/ ___/ / / / / / __ \ / __ / / __ \ / __ `__ \ / / / __ \ / __ `/ / __/ / __ \ / ___/(__ ) / /_/ / / /_/ // /_/ / / /_/ / / / / / / / / / / / / // /_/ / / /_ / /_/ / / / /____/ \__,_/ /_.___/ \__,_/ \____/ /_/ /_/ /_/ /_/ /_/ /_/ \__,_/ \__/ \____/ /_/ @RevoltSecurities[Version]: Subdominator current version v1.0.8 (latest)[INFO]: Current Available free passive resources: [45][INFO]: Sources marked with an * needs API key(s) or token(s) configuration to works[INFO]: Hey sanjai you can config your api keys or token here /home/sanjai/.config/Subdominator/provider-config.yaml to workabuseipDB alienvault anubis bevigil* binaryedge* bufferover* c99* censys* certspotter* chaos* columbusapi crtsh digitorus dnsdumpster* dnsrepo fofa* facebook* fullhunt* google* hackertarget huntermap* intelx* leakix* myssl netlas* quake* racent rapidapi* rapiddns redhuntlabs* rsecloud* securitytrails* shodan* shodanx shrewdeye sitedossier subdomaincenter urlscan virustotal* waybackarchive whoisxml* zoomeyeapi* rapidfinder*: Rapidfinder requires rapidapi api key but before it required to subscribe for free and please see here: https://rapidapi.com/Glavier/api/subdomain-finder3/pricing rapidscan*: Rapidscan requires rapidapi api key but before it required to subscribe for free and please see here: https://rapidapi.com/sedrakpc/api/subdomain-scan1/pricing coderog*: Coderog source required to subscribe for free and please see here: https://rapidapi.com/coderog-coderog-default/api/subdomain-finder5/pricing
工具使用
subdominator -h__ __ _ __ _____ __ __ / /_ ____/ / ____ ____ ___ (_) ____ ____ _ / /_ ____ _____/ ___/ / / / / / __ \ / __ / / __ \ / __ `__ \ / / / __ \ / __ `/ / __/ / __ \ / ___/(__ ) / /_/ / / /_/ // /_/ / / /_/ / / / / / / / / / / / / // /_/ / / /_ / /_/ / / / /____/ \__,_/ /_.___/ \__,_/ \____/ /_/ /_/ /_/ /_/ /_/ /_/ \__,_/ \__/ \____/ /_/ @RevoltSecurities[DESCRIPTION]: Subdominator a passive subdomain enumeration that discovers subdomains for your targets using with passive and open source resources[USAGE]:subdominator [flags][FLAGS]:[INPUT]:-d,--domain:枚举子域的域名;-dL,--domain-list:包含用于枚举子域的域的文件名;stdout:子域支持 stdout 以将其输出通过管道传输;[OUTPUT]:-o,--output:用于保存输出的文件名;-oD,--output-directory:用于保存输出的目录名(使用 -dL 标志时使用它);[OPTIMIZATION]:-t,--timeout:每个源请求的超时值。 [Update]:-up,--update:更新子域以获取最新版本,但 yaml 源更新需要手动操作,以免影响您的 api 密钥配置;-duc, --disable-update-check :禁用 subdominator 的自动更新检查;-sup, --show-updates :显示 subdominator 的最新版本更新;[CONFIG]:-nt, --notify :使用源 Slack、Pushbullet、Telegram、Discord 发送发现子域的通知;-p, --proxy :与 subdominator 一起使用的 http 代理(用于调试 subdominator 的性能);-cp, --config-path :subdominator 读取 api 密钥的配置文件的自定义路径(默认路径:/home/sanjai/.config/Subdominator/provider-config.yaml); [DEBUG]:-h, --help :显示此帮助消息并退出;-v, --version :显示 subdominator 的当前版本和最新版本(如果可用)并退出;-ske, --show-key-error :显示特定来源的信用不足和未提供密钥的密钥错误;-sre, --show-timeout-error :显示连接超时的来源的超时错误;-nc, --no-color :禁用 subdominator 的彩色输出;-ls, --list-source :显示 subdominator 用于子域枚举和退出的来源;
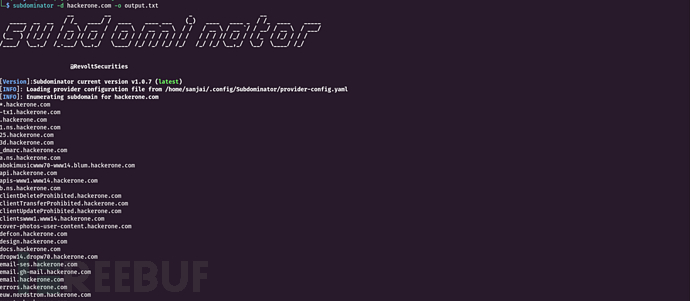
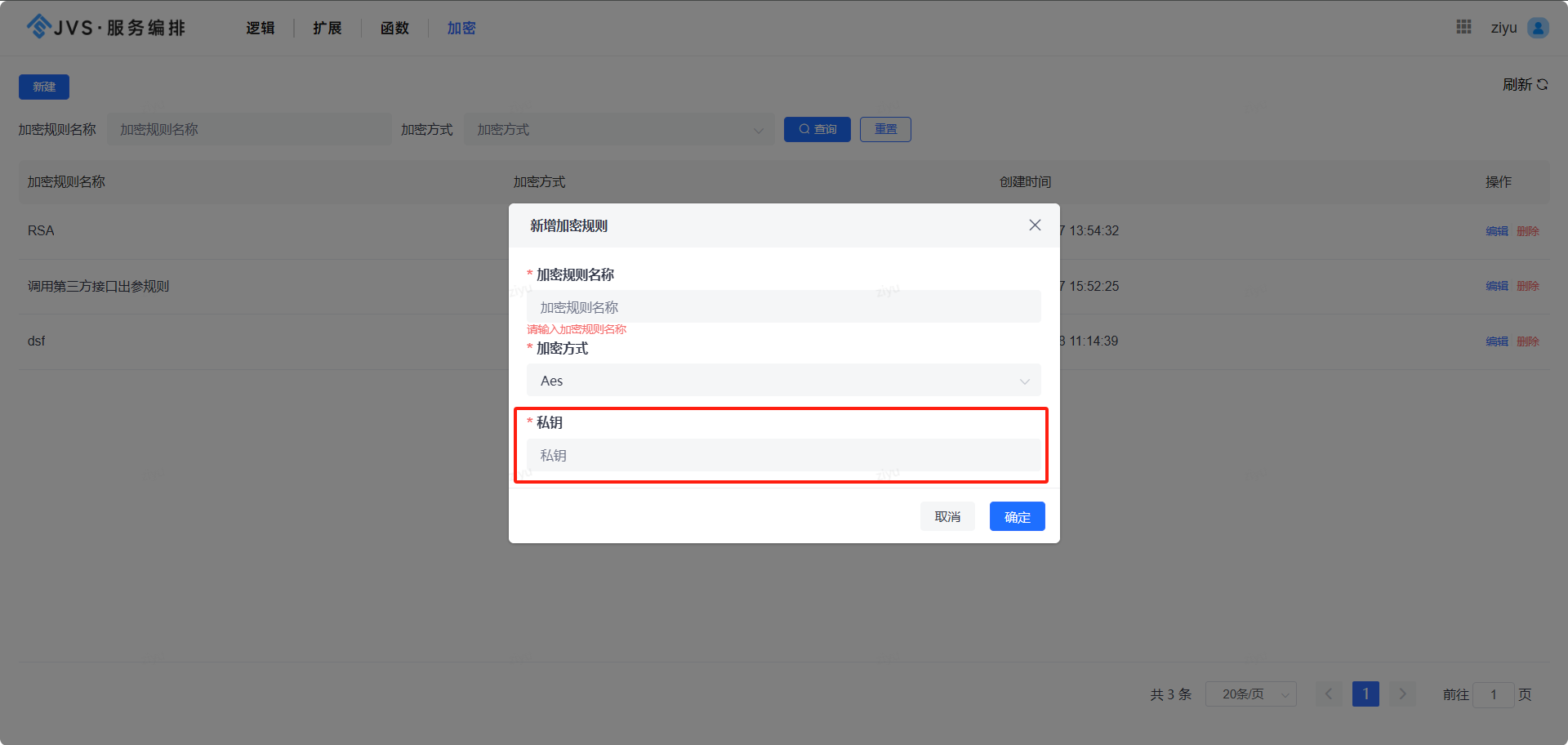
工具运行截图
许可证协议
本项目的开发与发布遵循MIT开源许可协议。
项目地址
Subdominator:【GitHub传送门】
参考资料
Installing Subfinder - ProjectDiscovery Documentation
DNSDumpster.com - dns recon and research, find and lookup dns records
https://programmablesearchengine.google.com/controlpanel/create
https://developers.google.com/custom-search/v1/introduction







![[论文精读]TorWard: Discovery, Blocking, and Traceback of Malicious Traffic Over Tor](https://i-blog.csdnimg.cn/direct/932159c051504260b188b43e1cc5e897.png)