备考ICA----Istio实验13—使用Istio Ingress TLS暴露应用
1. 环境部署
清理之前实验遗留,并重新部署httpbin服务进行测试
# 清理之前的环境
kubectl delete vs httpbin
kubectl delete gw mygateway
# 部署httpbin
kubectl apply -f istio/samples/httpbin/httpbin.yaml
确认应用被正确创建
kubectl get deployments,svc httpbin

2. 为httpbin创建ingress
创建一个ingress指向httpbin服务,测试服务本身是否正常
kubectl create ingress httpbin-ingress \--rule 'httpbin.example.com/status*=httpbin:8000' \--annotation kubernetes.io/ingress.class=istio
确认ingress被正确创建
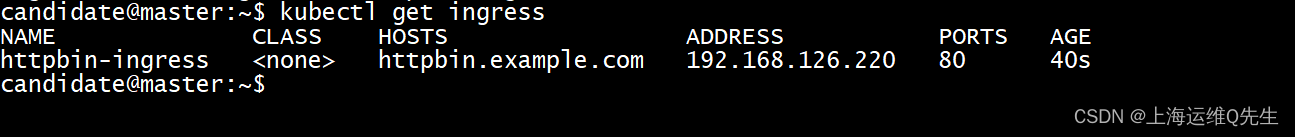
kubectl get ingress
访问测试
curl -s -I -HHost:httpbin.example.com "http://192.168.126.220/status/200"
3. 为httpbin创建ingress TLS
通过IngressClass连接istio.io/ingresss-controller将流量转给httpbin服务
3.1 创建 Istio ingressclass
ingress/IngressClass.yaml
apiVersion: networking.k8s.io/v1
kind: IngressClass
metadata:name: istio
spec:controller: istio.io/ingress-controller
部署istio ingressclass
kubectl apply -f ingress/IngressClass.yaml
3.2 调用Istio Ingressclass
重建httpbin的ingress
kubectl delete ingress httpbin-ingress
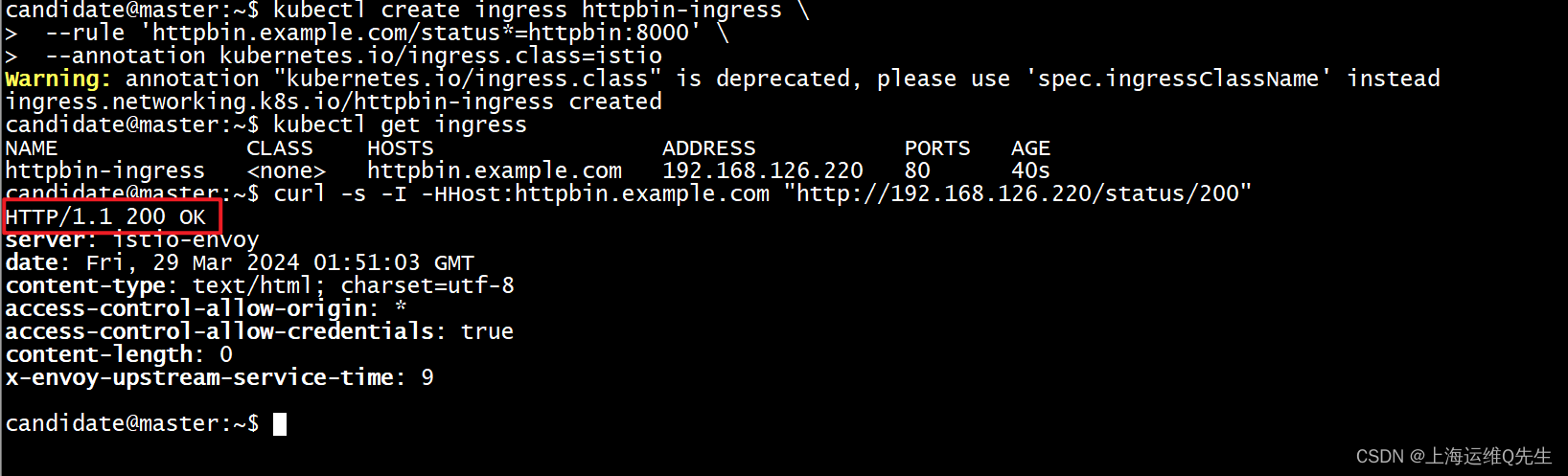
kubectl create ingress httpbin-ingress \--rule 'httpbin.example.com/status*=httpbin:8000' \--class istio
kubectl get ingress
访问测试
curl -s -I -HHost:httpbin.example.com "http://192.168.126.220/status/200"
3.3 使用 TLS ingress
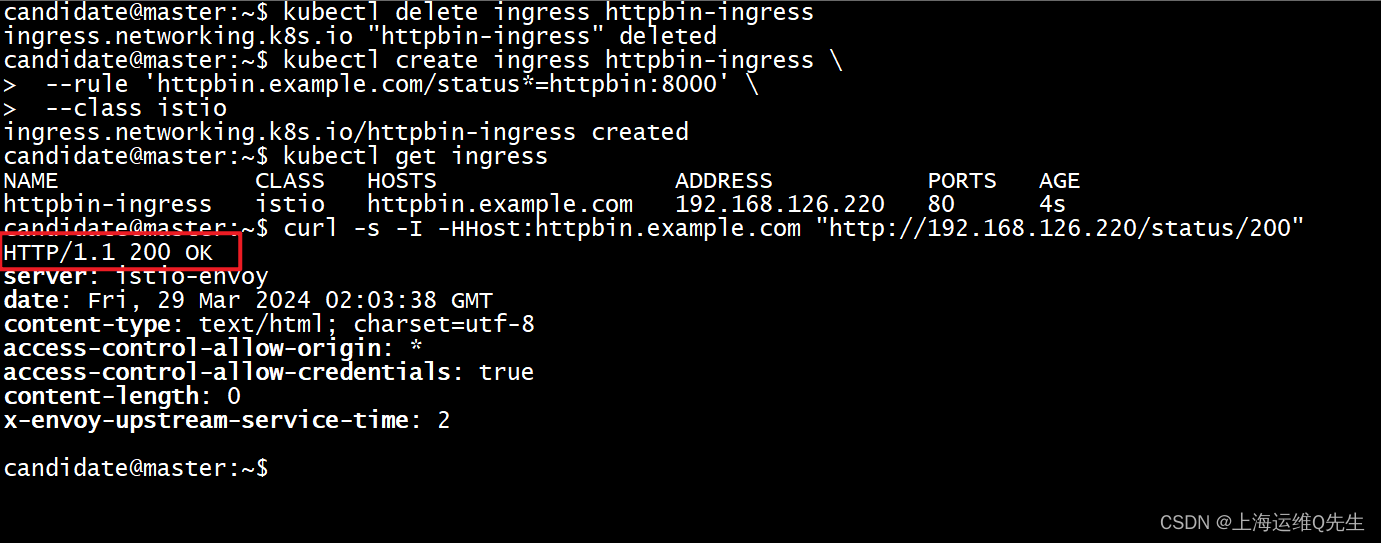
kubectl delete ingress httpbin-ingress
kubectl create secret tls httpbin-credential \
--key=example_certs_httpbin/httpbin.example.com.key \
--cert=example_certs_httpbin/httpbin.example.com.crt
kubectl create ingress httpbin-ingress \--rule 'httpbin.example.com/status*=httpbin:8000,tls=httpbin-credential' \--class istio
确认hosts中存在httpbin.example.com的解析,访问测试
curl -k -vvv https://httpbin.example.com
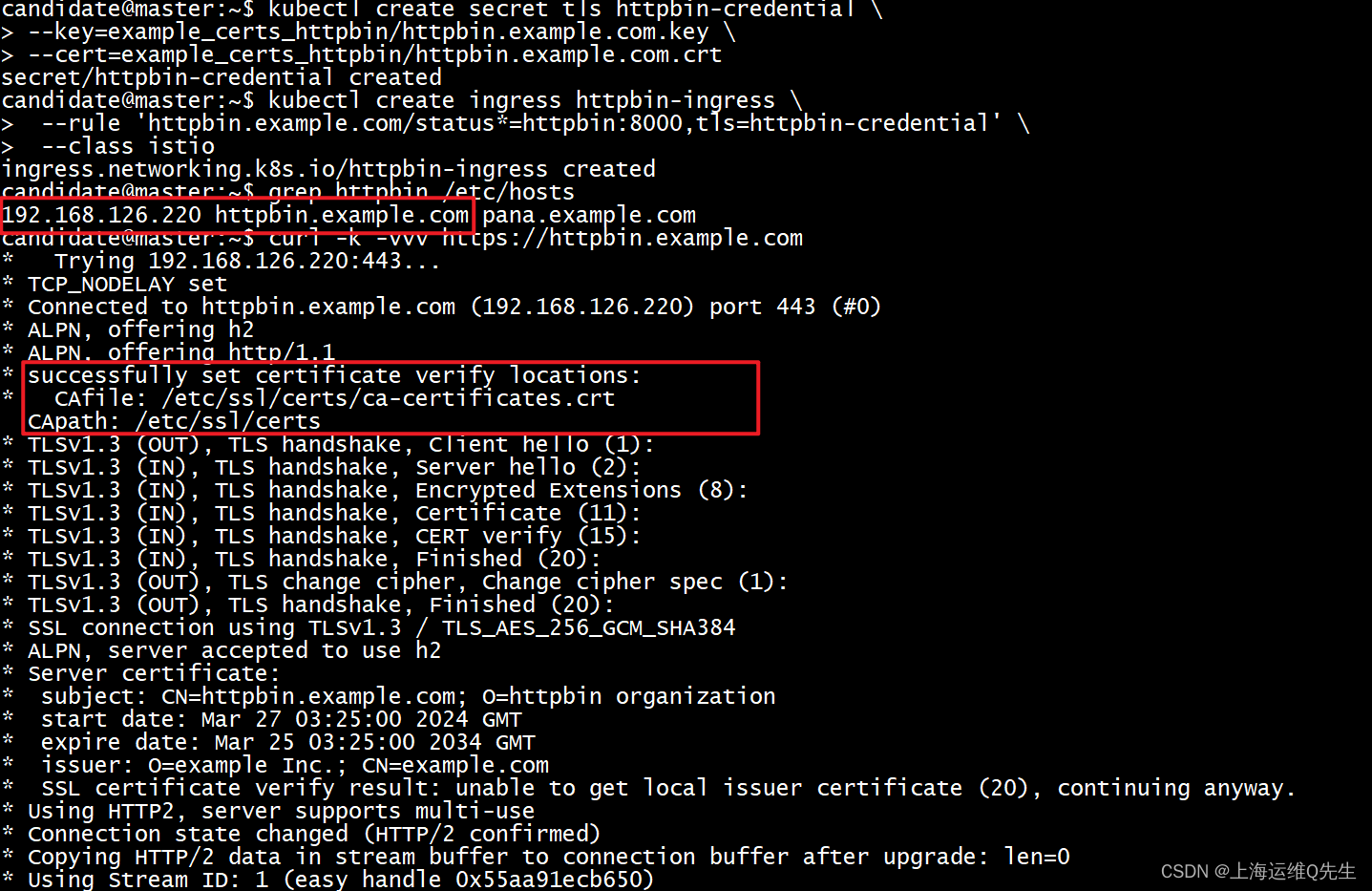
可以看到证书已经被加载
到浏览器中查看证书详情,也是和我们之前生成并绑定的证书相符
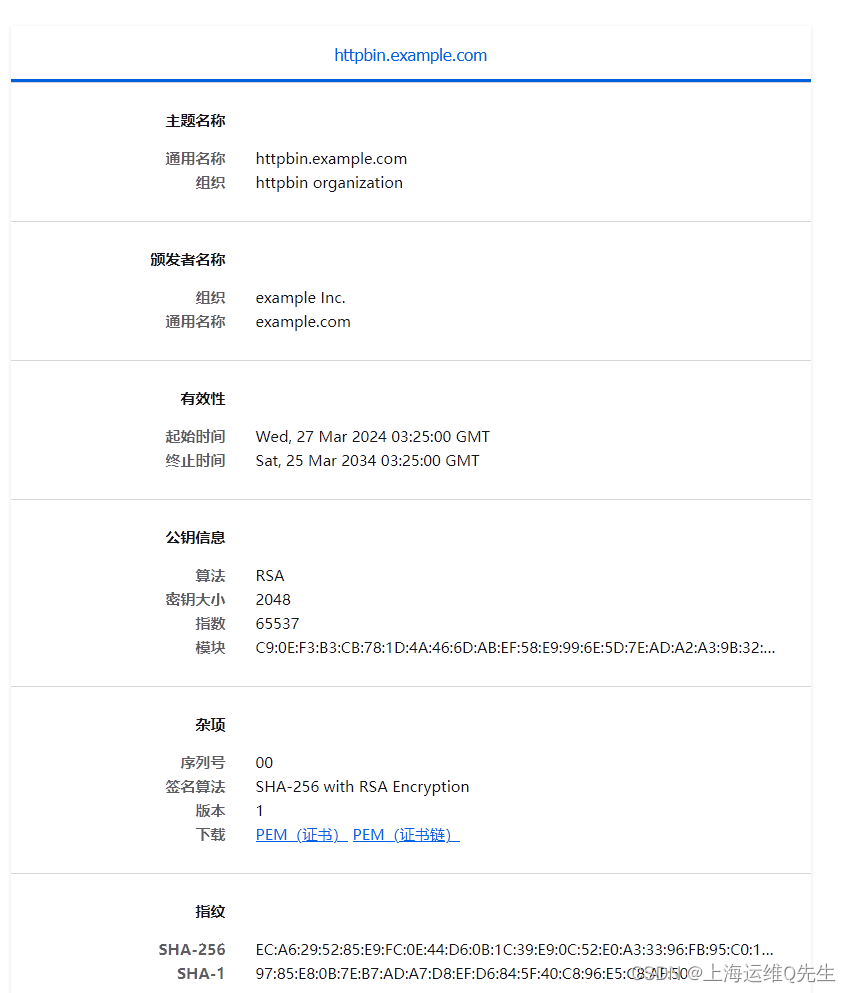
至此备考ICA----Istio实验13—使用 Istio Ingress 暴露应用实验完成