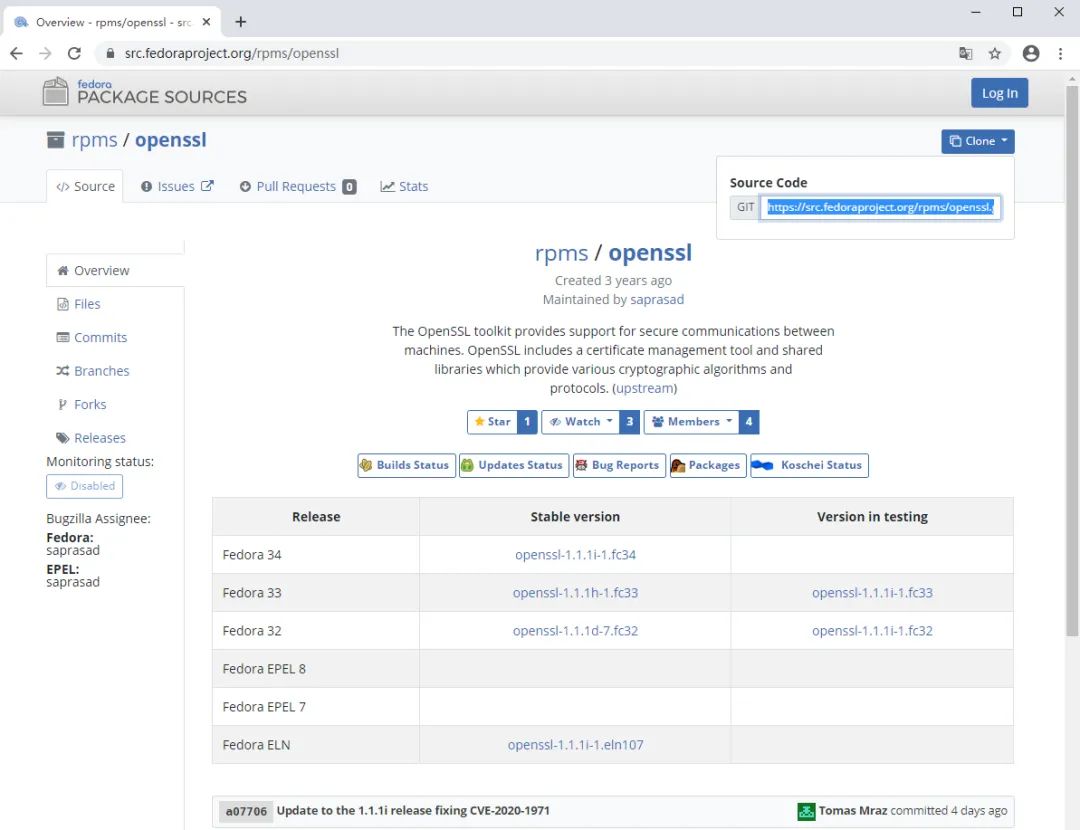
OpenSSL最新漏洞
OpenSSL官方发布了拒绝服务漏洞风险通告,漏洞编号为CVE-2020-1971
漏洞详情
OpenSSL是一个开放源代码的软件库包,应用程序可以使用这个包来进行安全通信,避免窃听,同时确认另一端连接者的身份。这个包广泛被应用在互联网的网页服务器上。
OpenSSL在处理EDIPartyName(X.509 GeneralName类型标识)的时候,存在一处空指针解引用,并引起程序崩溃导致拒绝服务。攻击者可通过构造特制的证书验证过程触发该漏洞,并导致服务端拒绝服务。
风险等级
高
漏洞风险
漏洞被利用可能导致拒绝服务
影响版本
OpenSSL : 1.0.2-1.0.2w
OpenSSL : 1.1.1-1.1.1h
安全版本
OpenSSL : 1.1.1i
OpenSSL : 1.0.2x
修复建议
将OpenSSL升级到1.1.1i、 1.0.2x或最新版本
【备注】:建议您在升级前做好数据备份工作,避免出现意外
漏洞参考
https://www.openssl.org/news/vulnerabilities-1.1.1.html#CVE-2020-1971
https://www.openssl.org/news/vulnerabilities-1.0.2.html#CVE-2020-1971
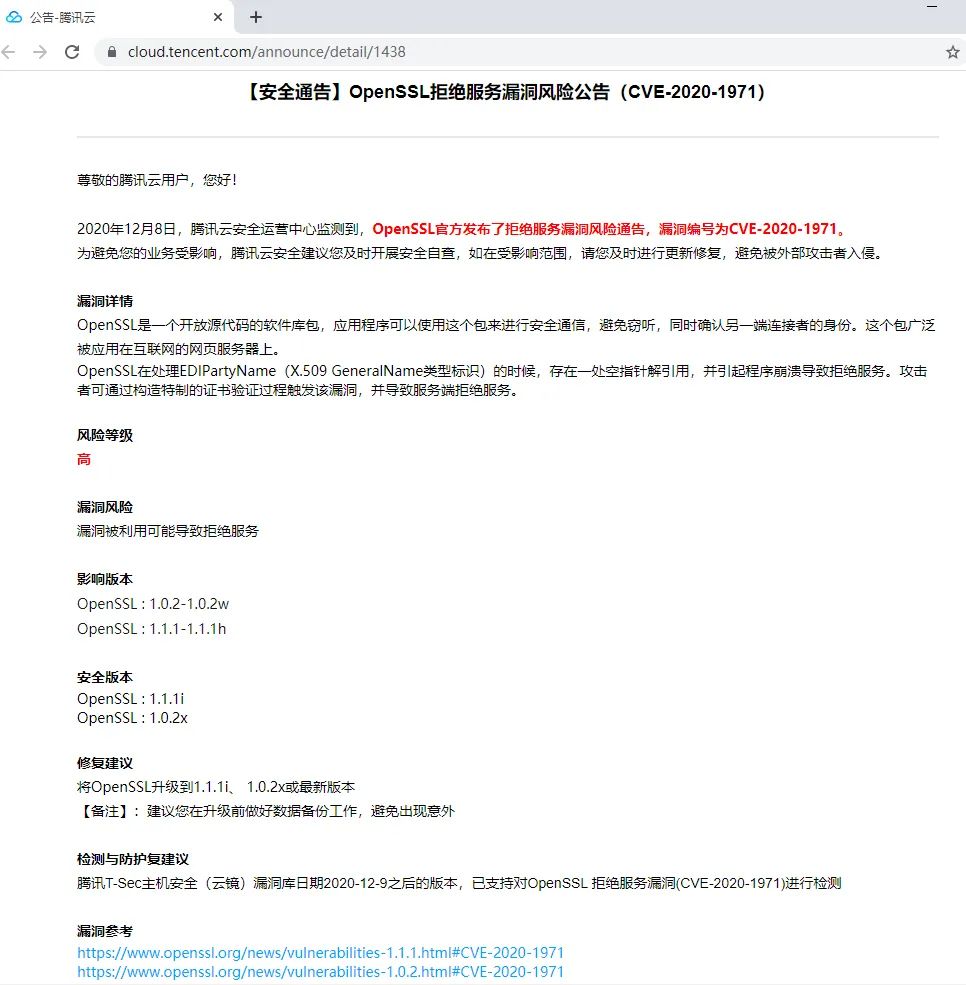
openssl版本自查
针对该漏洞,在CentOS7当前的机器上进行自查
[root@centos ~]# cat /etc/redhat-release
CentOS Linux release 7.9.2009 (Core)
[root@centos ~]#
[root@centos ~]# rpm -aq openssl
openssl-1.0.2k-19.el7.x86_64
[root@centos ~]#
[root@centos ~]# rpm -aq | grep openssl
xmlsec1-openssl-1.2.20-7.el7_4.x86_64
openssl-1.0.2k-19.el7.x86_64
openssl098e-0.9.8e-29.el7.centos.3.x86_64
openssl-libs-1.0.2k-19.el7.x86_64
[root@centos ~]#
[root@centos ~]# openssl version
OpenSSL 1.0.2k-fips 26 Jan 2017
[root@centos ~]#
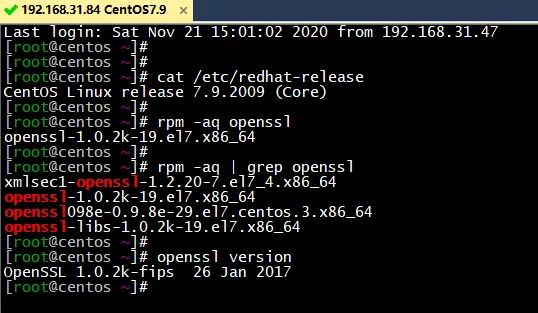
制作OpenSSL1.1.1i rpm包
在GitHub上找到制作openssl 1.1.1i版本rpm包的脚本
本地修改后,进行打包修改后的脚本如下install-openssl_1.1.1i.sh
#!/bin/bash
set -e
set -v
mkdir ~/openssl && cd ~/openssl
yum -y install \curl \which \make \gcc \perl \perl-WWW-Curl \rpm-build
# Get openssl tarball
cp /root/openssl-1.1.1i.tar.gz ./# SPEC file
cat << 'EOF' > ~/openssl/openssl.spec
Summary: OpenSSL 1.1.1i for Centos
Name: openssl
Version: %{?version}%{!?version:1.1.1i}
Release: 1%{?dist}
Obsoletes: %{name} <= %{version}
Provides: %{name} = %{version}
URL: https://www.openssl.org/
License: GPLv2+Source: https://www.openssl.org/source/%{name}-%{version}.tar.gzBuildRequires: make gcc perl perl-WWW-Curl
BuildRoot: %{_tmppath}/%{name}-%{version}-%{release}-root
%global openssldir /usr/openssl%description
OpenSSL RPM for version 1.1.1i on Centos%package devel
Summary: Development files for programs which will use the openssl library
Group: Development/Libraries
Requires: %{name} = %{version}-%{release}%description devel
OpenSSL RPM for version 1.1.1i on Centos (development package)%prep
%setup -q%build
./config --prefix=%{openssldir} --openssldir=%{openssldir}
make%install
[ "%{buildroot}" != "/" ] && %{__rm} -rf %{buildroot}
%make_installmkdir -p %{buildroot}%{_bindir}
mkdir -p %{buildroot}%{_libdir}
ln -sf %{openssldir}/lib/libssl.so.1.1 %{buildroot}%{_libdir}
ln -sf %{openssldir}/lib/libcrypto.so.1.1 %{buildroot}%{_libdir}
ln -sf %{openssldir}/bin/openssl %{buildroot}%{_bindir}%clean
[ "%{buildroot}" != "/" ] && %{__rm} -rf %{buildroot}%files
%{openssldir}
%defattr(-,root,root)
/usr/bin/openssl
/usr/lib64/libcrypto.so.1.1
/usr/lib64/libssl.so.1.1%files devel
%{openssldir}/include/*
%defattr(-,root,root)%post -p /sbin/ldconfig%postun -p /sbin/ldconfig
EOFmkdir -p /root/rpmbuild/{BUILD,RPMS,SOURCES,SPECS,SRPMS}
cp ~/openssl/openssl.spec /root/rpmbuild/SPECS/openssl.specmv openssl-1.1.1i.tar.gz /root/rpmbuild/SOURCES
cd /root/rpmbuild/SPECS && \rpmbuild \-D "version 1.1.1i" \-ba openssl.spec# Before Uninstall Openssl : rpm -qa openssl
# Uninstall Current Openssl Vesion : yum -y remove openssl
# For install: rpm -ivvh /root/rpmbuild/RPMS/x86_64/openssl-1.1.1i-1.el7.x86_64.rpm --nodeps
# Verify install: rpm -qa openssl
# openssl version下载openssl1.1.1i版本源码包,并上传到/root
https://www.openssl.org/source/openssl-1.1.1i.tar.gz
./install-openssl_1.1.1i.sh进行编译打包
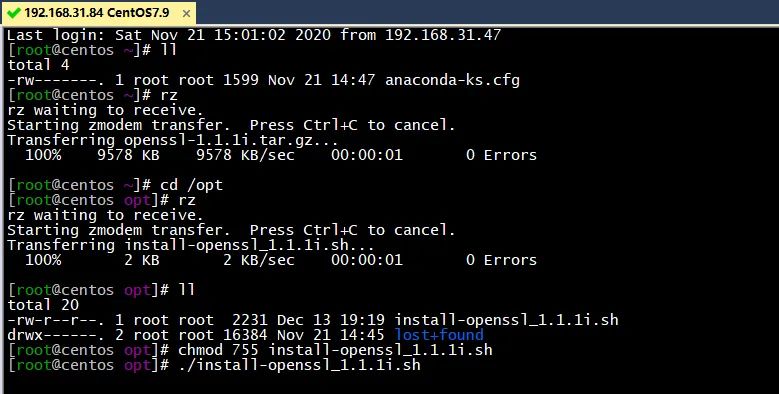
打完包后截图如下
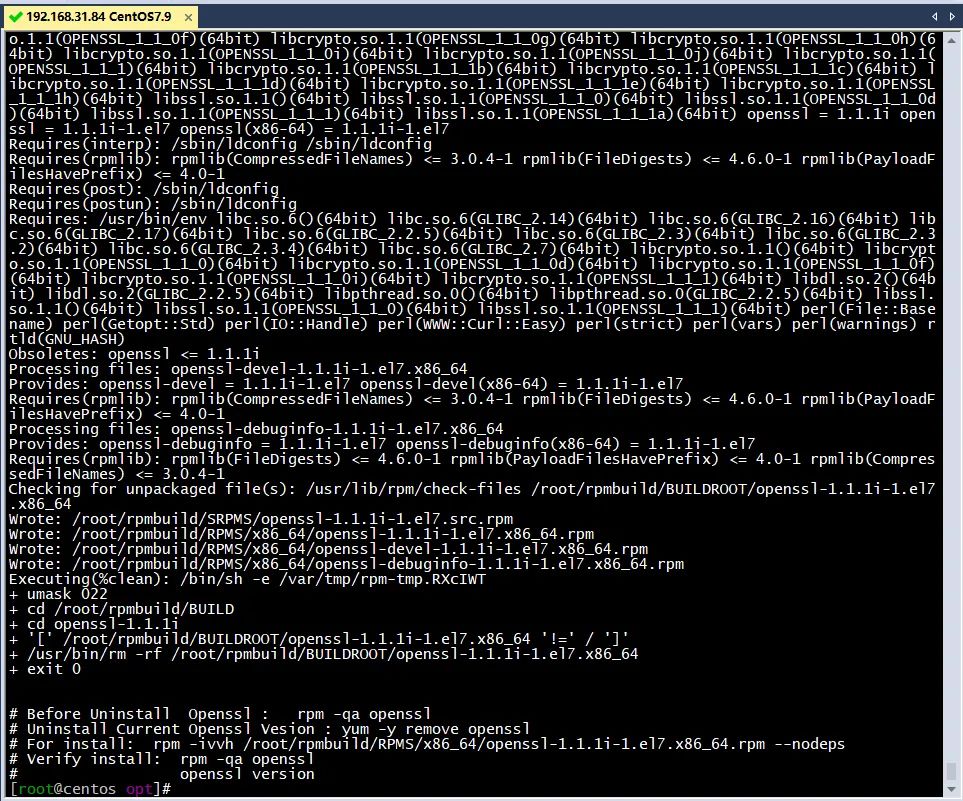
(图片可放大查看)
rpm升级到openssl1.1.1i
rpm -aq openssl
yum -y remove openssl
rpm -ivh /root/rpmbuild/RPMS/x86_64/openssl-1.1.1i-1.el7.x86_64.rpm --nodeps
openssl version

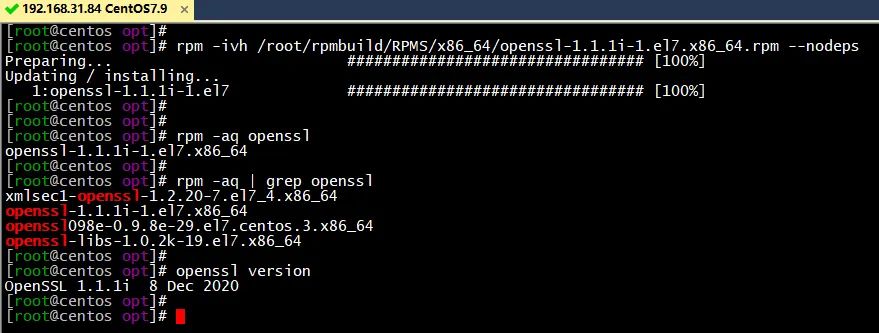
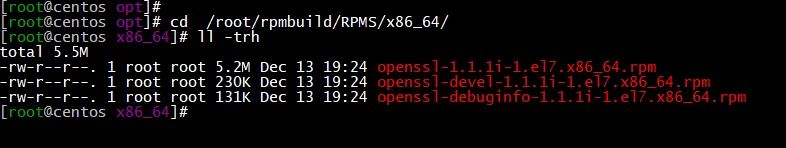
以上就是CentOS7下制作openssl1.1.1i RPM包并升级的步骤
尝试过git clone https://src.fedoraproject.org/rpms/openssl.git,利用openssl.spec进行rpmbuild -ba openssl.spec进行打包,未成功,后续有机会再研究