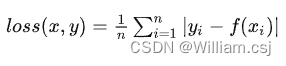前言:
jd m端使用最新的h5st 4.2签名算法,与h5st 4.1版本有很大的不同。在这儿分析一下,供大家参考。
一、目标地址(Base64解码)
aHR0cHM6Ly9zby5tLmpkLmNvbS93YXJlL3NlYXJjaC5hY3Rpb24/a2V5d29yZD0lRTklOTklQTQlRTYlQjklQkYlRTYlOUMlQkEmc2VhcmNoRnJvbT1ob21lJnNmPTE1JmFzPTA=逆向发现,是h5st 4.2版本的签名算法,比之前h5st 4.1版本的逆向难度大大提高,算法里面混淆了window,JD等环境变量,难于分离。
二、body参数的加密逆向(Base64解码):
1、评论接口(Base64解码):
aHR0cHM6Ly9hcGkubS5qZC5jb20vd2FyZS9jb21tZW50L2dldENvbW1lbnRMaXN0P2xvZ2luVHlwZT0yJmFwcGlkPW1fY29yZSZ1dWlkPTQ4NzA4MTI3NTkxNzY2NzAxJmZ1bmN0aW9uSWQ9Y29tbWVudF9nZXRDb21tZW50TGlzdCZ4LWFwaS1laWQtdG9rZW49amRkMDNYS05CM0M1NENJMlk2SEJUM0VPWUE1SllZM05HU1lCQzRBQ1FSRVE0WjNPVEdFU09XSFVPSk5JMkRBTUFNQk1HNk42WllBQkZPQUVTT0FaR042Qk9aQkROVElBQUFBTU1DUzVWQzdJQUFBQUFEWVg3REVYUFkzN1ZaTVgmanNvbnA9c2t1SkRFdmFsJmg1c3Q9MjAyMzExMjgxNTE3NTc5NDYlM0JpdzMzdDMzYWdwOW16dDMxJTNCZTQyNTYlM0J0azAyd2FhYzMxYjc3NDFsTXlzemVETXJNak16NGVnREU4SDlwVWN4M2daRi14THdyMm9PRUNYNGNkOE80cnFIX0gxdjFFNTVKc3JiRmtoVFIxcjlJMzFEMmtmXyUzQjZhMWU2YzIwZWRiYWFlOTExMTcxMDUzYjM1MTA1YTA4MDBlYTE0MjViODAyYzY4ZDA2ZGYyNjZhMDE4Y2NlNGMlM0I0LjIlM0IxNzAxMTU1ODc3OTQ2JTNCMGFlZWZhZjUyYzVhN2ZhMzFhMWFkNWUwNmM4NTUxZmRhODVhZDVmNDUzNmU3ZTRhYTYzOWMyN2M3NDJjYjAzNWJjNDA0ZTA0MmRhNzFhNmZhYTg1MzY4Mjk0MTIxYzk5ODBkNTVhZWMyZjY5ZDcxMjJjMDcxZDljMDdmYTAyNzc4ZGE3MzY3NDZiNTRlNTQ1Y2I5NzE1NGYwNzk2NjA0ZDZjOGRjYTY3NThhOTYwMmM0MzkyMThhNDYyNTM0NTllNzYzYjJhY2MyZjlkZWUyZmNkYTQ5YzhmYTg0NTBhNTUzMmMwMDhkYjE2YTY0OGRkOTE2ZmNjMDkyMjc1MTFjYmU0NjM2ZDU0MTZlY2NlZGJmOTVmYzFkOGZkZGE3MDRkMmI5OGFmNjg5YmQ1MjYwOTJiN2E2MTM3NDU1NzZjYzc4YTcyZTI5MDc2Mzg3Mzk1OThjMGJlNDE2NWI3YTFiYjM1ZDg4YzlhZmNlYzUyZWU0ZTc0NTRmZGQ2MDE4YTEwMGJiOTU0ZmJmZDAyMmE4NDFmZDViZTZmZDNhMzcwMDJmMjViZmVjNmRkMGJmZDMwNzc5YmY2YTk0YzAwYjkyNDhhMmU0Zjk1ODY2MmNlYTQ2MGMxNmQyNWVhNDFlNGE0NTIxMGJmNzg2Mjk1MTY2MTk5NjIzMjY5ZjEyODgyNjc4NGU4MTI3NTlkMDg3ZDQ4ZmMxYjhjYjk4NDFhY2U5MSZib2R5PXslMjJleHRlcm5hbExvZ2luVHlwZSUyMjoxLCUyMmNhbGxiYWNrJTIyOiUyMnNrdUpERXZhbCUyMiwlMjJ2ZXJzaW9uJTIyOiUyMnYyJTIyLCUyMnBhZ2VzaXplJTIyOiUyMjEwJTIyLCUyMnNjZW5ldmFsJTIyOiUyMjIlMjIsJTIyc2NvcmUlMjI6JTIyMCUyMiwlMjJza3UlMjI6JTIyMTI4MjI3MiUyMiwlMjJzb3J0dHlwZSUyMjolMjI1JTIyLCUyMnBhZ2UlMjI6JTIyMSUyMiwlMjJ0JTIyOiUyMjAuNDU4MzEyNDczMTM0NDQzNDUlMjJ9JmFwcENvZGU9bXMwY2E5NTExNAo=2、参数h5st:
h5st=20231128151757946%3Biw33t33agp9mzt31%3Be4256%3Btk02waac31b7741lMyszeDMrMjMz4egDE8H9pUcx3gZF-xLwr2oOECX4cd8O4rqH_H1v1E55JsrbFkhTR1r9I31D2kf_%3B6a1e6c20edbaae911171053b35105a0800ea1425b802c68d06df266a018cce4c%3B4.2%3B1701155877946%3B0aeefaf52c5a7fa31a1ad5e06c8551fda85ad5f4536e7e4aa639c27c742cb035bc404e042da71a6faa85368294121c9980d55aec2f69d7122c071d9c07fa02778da736746b54e545cb97154f0796604d6c8dca6758a9602c439218a46253459e763b2acc2f9dee2fcda49c8fa8450a5532c008db16a648dd916fcc09227511cbe4636d5416eccedbf95fc1d8fdda704d2b98af689bd526092b7a613745576cc78a72e2907638739598c0be4165b7a1bb35d88c9afcec52ee4e7454fdd6018a100bb954fbfd022a841fd5be6fd3a37002f25bfec6dd0bfd30779bf6a94c00b9248a2e4f958662cea460c16d25ea41e4a45210bf786295166199623269f128826784e812759d087d48fc1b8cb9841ace91
可以看到版本号为:4.2
3、body参数:
body参数解码为:
{"externalLoginType":1,"callback":"skuJDEval","version":"v2","pagesize":"10","sceneval":"2","score":"0","sku":"1282272","sorttype":"5","page":"1","t":"0.45831247313444345"}
4、body参数的加密位置与h5st 4.1版本基本相同,加密代码如下:
function sha256_digest(e) {var t = 8, r = 0;function n(e, t) {var r = (65535 & e) + (65535 & t);return (e >> 16) + (t >> 16) + (r >> 16) << 16 | 65535 & r}function o(e, t) {return e >>> t | e << 32 - t}function i(e, t) {return e >>> t}function a(e, t, r) {return e & t ^ ~e & r}function s(e, t, r) {return e & t ^ e & r ^ t & r}function c(e) {return o(e, 2) ^ o(e, 13) ^ o(e, 22)}function l(e) {return o(e, 6) ^ o(e, 11) ^ o(e, 25)}function u(e) {return o(e, 7) ^ o(e, 18) ^ i(e, 3)}function d(e) {return o(e, 17) ^ o(e, 19) ^ i(e, 10)}return function(e) {for (var t = r ? "0123456789ABCDEF" : "0123456789abcdef", n = "", o = 0; o < 4 * e.length; o++)n += t.charAt(e[o >> 2] >> 8 * (3 - o % 4) + 4 & 15) + t.charAt(e[o >> 2] >> 8 * (3 - o % 4) & 15);return n}(function(e, t) {var r, o, i, f, p, h, v, m, g, y, _ = new Array(1116352408,1899447441,3049323471,3921009573,961987163,1508970993,2453635748,2870763221,3624381080,310598401,607225278,1426881987,1925078388,2162078206,2614888103,3248222580,3835390401,4022224774,264347078,604807628,770255983,1249150122,1555081692,1996064986,2554220882,2821834349,2952996808,3210313671,3336571891,3584528711,113926993,338241895,666307205,773529912,1294757372,1396182291,1695183700,1986661051,2177026350,2456956037,2730485921,2820302411,3259730800,3345764771,3516065817,3600352804,4094571909,275423344,430227734,506948616,659060556,883997877,958139571,1322822218,1537002063,1747873779,1955562222,2024104815,2227730452,2361852424,2428436474,2756734187,3204031479,3329325298), w = new Array(1779033703,3144134277,1013904242,2773480762,1359893119,2600822924,528734635,1541459225), b = new Array(64);e[t >> 5] |= 128 << 24 - t % 32,e[15 + (t + 64 >> 9 << 4)] = t;for (var x = 0; x < e.length; x += 16) {r = w[0],o = w[1],i = w[2],f = w[3],p = w[4],h = w[5],v = w[6],m = w[7];for (var k = 0; k < 64; k++)b[k] = k < 16 ? e[k + x] : n(n(n(d(b[k - 2]), b[k - 7]), u(b[k - 15])), b[k - 16]),g = n(n(n(n(m, l(p)), a(p, h, v)), _[k]), b[k]),y = n(c(r), s(r, o, i)),m = v,v = h,h = p,p = n(f, g),f = i,i = o,o = r,r = n(g, y);w[0] = n(r, w[0]),w[1] = n(o, w[1]),w[2] = n(i, w[2]),w[3] = n(f, w[3]),w[4] = n(p, w[4]),w[5] = n(h, w[5]),w[6] = n(v, w[6]),w[7] = n(m, w[7])}return w}(function(e) {for (var r = Array(), n = (1 << t) - 1, o = 0; o < e.length * t; o += t)r[o >> 5] |= (e.charCodeAt(o / t) & n) << 24 - o % 32;return r}(e = function(e) {e = e.replace(/\r\n/g, "\n");for (var t = "", r = 0; r < e.length; r++) {var n = e.charCodeAt(r);n < 128 ? t += String.fromCharCode(n) : n > 127 && n < 2048 ? (t += String.fromCharCode(n >> 6 | 192),t += String.fromCharCode(63 & n | 128)) : (t += String.fromCharCode(n >> 12 | 224),t += String.fromCharCode(n >> 6 & 63 | 128),t += String.fromCharCode(63 & n | 128))}return t}(e)), e.length * t))}function O(e) {var n = {};var o = void 0;try {o = sha256_digest(e.body).toString()} catch (e) {console.log(e)}return n.body = o,n}
经验证,与浏览器返回的结果一致。
三、h5st 4.2逆向
1、全局搜索h5st字符串,找到h5st位置如下:

(图1 h5st位置)
2、经过一番单步调试跟踪,最终逆向出h5st 4.2源码,部分代码如下:
var o='95cb3'
var r={"functionId": "te_m_searchWareComment","appid": "jd-cphdeveloper-m","body": "4663b8a26f440c134fbb4445ebddb2df4c981a5ad56443a3014e73f09070f33d"
}
var t=
{"functionId": "te_m_searchWareComment","appid": "jd-cphdeveloper-m","body": "4663b8a26f440c134fbb4445ebddb2df4c981a5ad56443a3014e73f09070f33d","_stk": "appid,body,functionId","_ste": 1,"h5st": "20231107170525941;p93wttizgm993334;95cb3;tk03wa21f1c2218nAJHZh2GrX7JgxkMuU3khCJOUxXTX2l-JXupACRTvMdoPH3OuVXgocCHLarlNL64g2oHmopf-UrZ2;39cc132f90bdd6e98e6e69c08ab3d0654290564292a985812bf95a42efd9bf20;4.2;1699347925941;0aeefaf52c5a7fa31a1ad5e06c8551fda85ad5f4536e7e4aa639c27c742cb035bc404e042da71a6faa85368294121c9980d55aec2f69d7122c071d9c07fa02778da736746b54e545cb97154f0796604d6c8dca6758a9602c439218a46253459e763b2acc2f9dee2fcda49c8fa8450a5532c008db16a648dd916fcc09227511cbe4636d5416eccedbf95fc1d8fdda704d2b98af689bd526092b7a613745576cc79acb2f870cb9875b4228766f18671197b784ca2933493b06da50f28ff6d591e785cc4d4dd084c226f2d26e157fdff20bc011a5a81400ab87eae7ec2ca90e47ba9db6f8e9236e768d07c6b30fb81590e5b195e026dd7fe9610dce0d317a67fcce"
}var a= new h.default(function(e, t) {var r = O(s);D[o].sign(r).then(function(t) {return s.h5st = encodeURI(t.h5st || ""),e(s)})}
//技术支持:v+:byc6352
//.....................................................篇幅太长,难于显示...................................return function(e) {var t = {_0x5d064b: 229,_0x9dfbcc: 216};return o[function(e, n, o, i) {return r(t._0x5d064b, n - -876, i)}(0, 521, 0, 619)](this, arguments)}
//.....................................................篇幅太长,难于显示...................................3、nodejs中调试成功请求到数据:

(h5st 4.2 nodejs中调试成功请求到数据)
四、h5st4.2在cmd命令行成功请求到接口数据
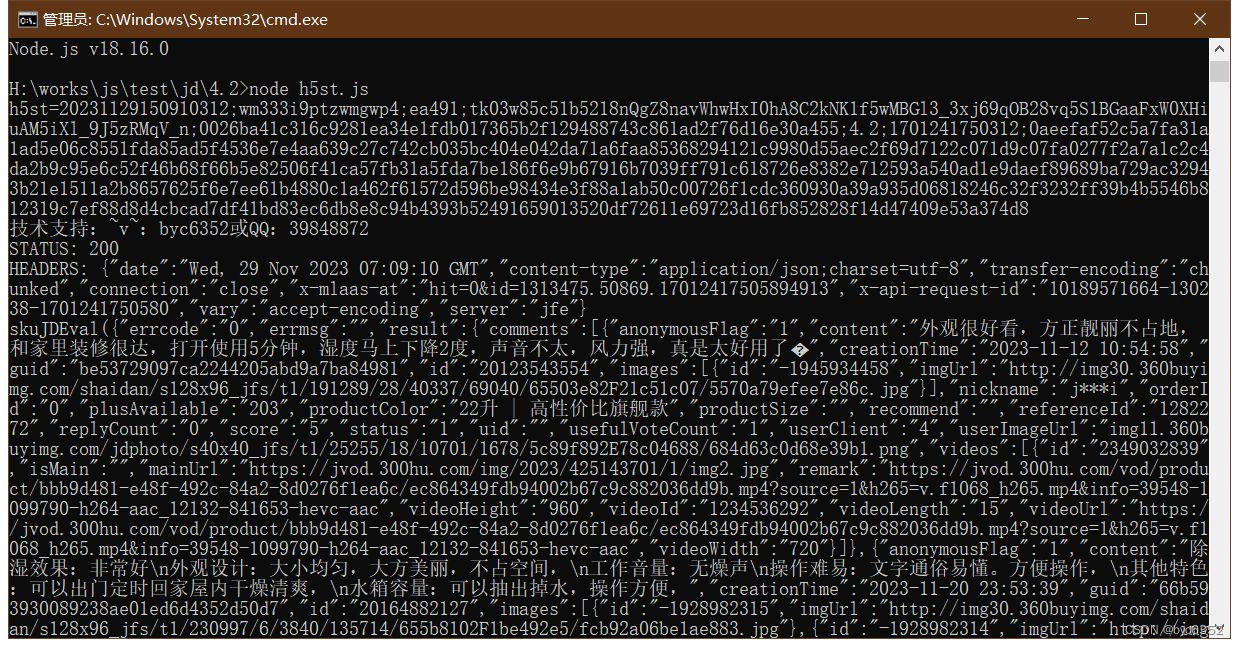
(图3 h5st 4.2 在cmd命令行成功请求到接口数据)
大功告成!!!