背景
最近在写Android abl阶段fastboot工具,需要我在Android代码中实现一些鉴权加解密相关的fastboot命令,里面用到了OpenSSL。我们先来实践一下OpenSSL在Linux系统中的指令。
OpenSSL官方网站:OpenSSL 中文手册 | OpenSSL 中文网
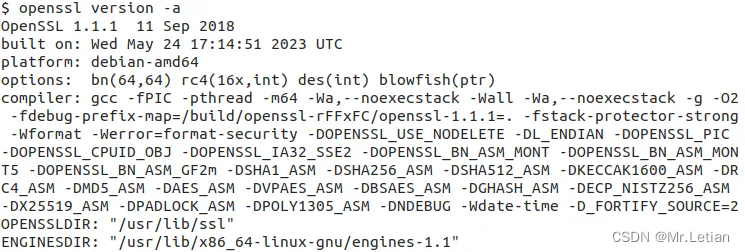
1. 查看openssl版本
openssl version
# 完整版本信息
openssl version -a
2. 命令rsa
2.1 生成双钥
2.1.1 生成key1
openssl genrsa -out priv.key
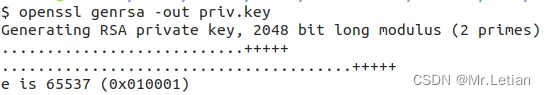
2.1.2 提取key2
openssl rsa [-inform PEM|NET|DER] [-outform PEM|NET|DER]
[-in filename] [-passin arg] [-out filename] [-passout arg]
[-sgckey] [-des] [-des3] [-idea] [-text] [-noout] [-modulus] [-check]
[-pubin] [-pubout] [-engine id]
常用选项:
- -in filename:输入文件
- -out filename:输出文件
- -pubout:根据私钥提取出公钥
openssl rsa -in priv.key -out pub.key -pubout
2.2 查看key内容
openssl rsa -in priv.key -text -noout
openssl rsa -in pub.key -text -noout -pubin
- -text:打印出私有密钥的各个组成部分
- -noout:key对应的ASCII码版本 不打印
2.2.1 key1
openssl rsa -in priv.key -text -noout
RSA Private-Key: (2048 bit, 2 primes)
modulus:00:cd:0d:ba:2b:56:57:68:10:7a:9d:31:47:51:f7:41:0d:ab:de:f1:c7:70:9f:a0:a2:18:49:6f:74:15:85:b5:68:bc:00:d3:46:f6:26:3d:16:a4:23:25:09:65:4f:f9:8e:2f:70:35:54:fe:b4:31:29:a8:70:f8:bf:b0:31:4a:85:79:31:99:da:7c:72:3a:21:f1:77:ec:d9:50:2a:8e:75:ab:34:c8:bf:82:0b:08:de:74:56:48:ba:56:17:30:1a:22:09:a1:f4:b3:cd:d3:6f:84:12:dc:a3:0e:33:95:91:27:4a:ee:f6:4e:2a:d0:85:9c:04:cc:52:c9:f8:5a:f3:78:e5:de:3e:28:5b:21:d0:ff:4a:54:79:4c:d8:81:a1:4e:3f:52:b5:71:d2:6f:5e:13:c0:33:48:53:5c:7f:7e:34:4f:e9:3b:53:7f:00:a0:80:60:69:e5:94:b0:00:1e:33:08:ec:c9:9a:31:de:40:8e:6b:0a:da:67:30:98:16:be:7f:da:11:c0:e0:64:77:09:6b:a6:26:e8:bb:45:17:88:88:f1:d4:e8:cc:d5:e9:70:ca:c2:1b:72:3d:00:e4:2f:6c:e4:68:ab:7e:03:e3:43:fc:eb:66:b2:7a:0d:c7:27:bc:40:a3:37:bf:76:eb:55:ed:a7:13:54:b7:e2:c5
publicExponent: 65537 (0x10001)
privateExponent:3f:4e:32:a0:b8:8a:49:a5:74:c5:5c:f6:60:d6:cd:ed:b3:97:23:db:e7:e8:50:46:5a:eb:29:0e:94:aa:70:04:42:ae:9a:8b:b8:e8:bb:49:67:29:36:80:fd:17:40:bb:65:e7:e5:7f:35:17:5a:6a:3b:07:8d:b4:58:68:0f:52:bf:c4:d1:74:03:a1:9c:52:e8:62:96:eb:cc:75:27:00:2a:f8:23:d6:04:06:f6:18:ff:9f:b7:da:57:43:d7:64:ea:07:41:49:f3:cc:e2:ae:f5:fe:80:c1:92:5b:d8:9c:34:9e:4c:c2:1c:05:d9:d4:b6:03:41:35:7a:07:43:c4:83:57:3e:e3:41:45:5a:c5:c9:f2:6f:2f:80:59:61:08:19:7d:54:4d:3d:09:be:38:5a:e6:ac:74:0f:80:7e:e7:37:9d:f6:f1:0b:5e:27:c4:a0:58:70:0c:9b:b0:af:25:1c:df:53:83:1a:ad:5d:ab:73:5b:c8:30:5b:9b:cf:e4:9d:e0:0d:5a:f6:60:8b:86:9d:44:37:6b:7c:64:54:c6:c1:3f:fc:74:23:5f:59:5b:cc:af:41:40:c8:79:24:29:13:c6:ff:eb:4b:28:aa:3e:9f:bd:9b:9a:fd:79:58:72:20:7d:cc:8b:0b:96:ca:cc:47:b8:2b:5a:75:5f:3b:6d
prime1:00:f4:40:4b:fc:dc:53:e7:b2:74:03:cd:83:dc:36:e8:97:34:01:37:29:0e:67:40:a2:3b:f3:8d:0c:41:21:16:17:d5:e1:f0:25:61:12:38:5e:db:f1:58:fb:b8:92:63:4d:3a:57:a3:25:b5:0b:9a:21:58:c7:60:2b:b7:16:7b:9f:9c:a3:4a:39:9a:23:c8:b1:2c:68:53:32:f1:a4:7c:6c:92:f4:ed:48:30:a2:d7:ed:9f:a4:d8:f9:dc:69:9f:34:39:3a:bf:1a:14:1e:97:48:81:7b:6a:b4:82:5c:70:6f:5f:4b:32:2b:8f:b2:30:0e:09:f3:a8:72:94:c1:30:5b
prime2:00:d6:ea:c0:b8:c2:c3:e0:6f:96:64:f1:3d:cb:1c:89:cc:b7:d9:bf:f6:32:9e:2b:54:37:77:20:3f:3c:24:a1:c5:55:2a:63:6e:42:18:86:e2:19:e3:19:19:62:e3:2f:59:3d:5d:82:8b:d0:98:80:83:dc:4f:1d:7a:45:4f:da:63:58:b6:fb:13:2d:d7:51:c0:d1:4c:7f:7b:32:d3:00:73:b7:bc:4e:b1:3c:ab:23:fd:7c:90:95:e3:a7:7d:5c:78:c2:5b:72:99:16:bb:fc:4b:e2:39:16:68:1b:22:28:6d:4b:0e:29:d3:04:e9:4c:f3:0d:7e:09:46:02:47:a3:5f
exponent1:00:cf:be:f8:62:c4:0b:e1:a0:59:28:fa:de:52:a9:a9:3f:22:0e:7e:9a:3f:13:f7:57:85:e2:6b:6f:a6:dd:bb:6a:de:92:63:ad:87:58:f5:f5:48:e1:88:ab:e1:9b:31:36:f8:8e:9d:c7:6e:ab:c5:96:e3:6a:01:14:6d:8f:83:ea:88:52:22:c9:c7:9e:f4:0e:2e:15:35:de:b8:c5:0c:c7:54:5f:5a:8a:f2:43:2f:a1:7f:0d:b9:37:1c:10:02:47:6a:fd:da:99:15:cf:c7:20:f6:70:c0:9b:73:dd:a8:0c:32:63:44:f2:e4:2f:cc:cb:c4:0f:28:90:fc:91:2c:cd
exponent2:0d:da:13:91:d4:fb:ca:fb:66:36:1b:56:60:40:f6:a0:bb:38:cd:a6:90:9c:a1:2e:4c:64:e1:2f:32:31:2a:3c:0d:c1:2d:a7:6d:9b:27:16:6b:94:b7:89:6b:56:39:37:07:3d:7f:ac:83:45:51:03:2e:af:ea:b6:76:c1:2e:d2:38:65:92:c9:29:ab:37:19:b6:63:b7:d3:b8:f2:e0:94:94:c3:0e:4f:5e:19:a9:b8:2c:cf:24:da:07:71:8d:04:3b:82:a9:60:34:96:e9:2b:fa:e8:b3:09:02:b6:b0:e4:5a:72:0f:40:0a:90:fe:e4:ab:79:f4:1f:0f:06:8f:01
coefficient:45:b8:5d:e3:ec:af:16:00:60:7a:a1:b8:ce:74:50:74:54:58:12:ab:ac:aa:bc:c4:c0:18:ee:75:50:75:18:3d:0f:99:ed:70:7a:b7:0b:4b:46:e6:ba:28:69:d8:c9:f6:a5:5a:f1:98:8d:f8:a2:91:06:16:89:34:3d:54:f3:a3:3b:0b:dd:f5:0a:ad:5c:99:03:f6:d1:fe:f8:d6:e4:61:46:e9:bf:2f:18:f0:1f:24:25:e0:ad:83:c3:63:4e:d0:ec:75:14:3e:d7:d4:76:e1:b7:c2:dd:0d:fd:14:2a:14:d6:10:e9:c9:73:ef:ac:aa:c8:0a:9c:62:52:ea:4e:53
2.2.3 key2
openssl rsa -pubin -in pub.key -text -noout
RSA Public-Key: (2048 bit)
Modulus:00:cd:0d:ba:2b:56:57:68:10:7a:9d:31:47:51:f7:41:0d:ab:de:f1:c7:70:9f:a0:a2:18:49:6f:74:15:85:b5:68:bc:00:d3:46:f6:26:3d:16:a4:23:25:09:65:4f:f9:8e:2f:70:35:54:fe:b4:31:29:a8:70:f8:bf:b0:31:4a:85:79:31:99:da:7c:72:3a:21:f1:77:ec:d9:50:2a:8e:75:ab:34:c8:bf:82:0b:08:de:74:56:48:ba:56:17:30:1a:22:09:a1:f4:b3:cd:d3:6f:84:12:dc:a3:0e:33:95:91:27:4a:ee:f6:4e:2a:d0:85:9c:04:cc:52:c9:f8:5a:f3:78:e5:de:3e:28:5b:21:d0:ff:4a:54:79:4c:d8:81:a1:4e:3f:52:b5:71:d2:6f:5e:13:c0:33:48:53:5c:7f:7e:34:4f:e9:3b:53:7f:00:a0:80:60:69:e5:94:b0:00:1e:33:08:ec:c9:9a:31:de:40:8e:6b:0a:da:67:30:98:16:be:7f:da:11:c0:e0:64:77:09:6b:a6:26:e8:bb:45:17:88:88:f1:d4:e8:cc:d5:e9:70:ca:c2:1b:72:3d:00:e4:2f:6c:e4:68:ab:7e:03:e3:43:fc:eb:66:b2:7a:0d:c7:27:bc:40:a3:37:bf:76:eb:55:ed:a7:13:54:b7:e2:c5
Exponent: 65537 (0x10001)
2.2.3 内容比较
- Modules:模组,双钥都包含这个数,且内容是一样的
- publicExponent:公钥指数,一般是固定值65537
- privateExponent:私钥指数
- prime1:素数1
- prime2:素数2
- exponent1:指数1
- exponent2:指数2
- coefficient:系数
3. 命令rsautl
3.1 加密-encrypt
openssl rsautl -encrypt -inkey pub.key -pubin -in text.txt -out sec_text.enc
3.2 解密-decrypt
openssl rsautl -decrypt -inkey priv.key -in sec_text.enc -out source.txt && cat source.txt
由于我将cat命令与解密命令进行了拼接,我们能收到命令的返回值:

此时说明我们成功使用私钥进行了对 使用公钥加密后的文件 成功解密的处理。
3.3 签名-sign
openssl rsautl -sign -inkey priv.key -in text.txt -out sec_text_sign.enc
3.4 验签-verify
openssl rsautl -verify -inkey pub.key -pubin -in sec_text_sign.enc -out source_sign.txt
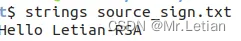
3.5 实践发现
理论上,使用公钥加密,私钥可以解密;同时用私钥加密,公钥也能解密。
但在OpenSSL工具上,后者并不可以,加密命令可以执行,但解密命令会发生报错:
- 私钥加密:

- 公钥解密:
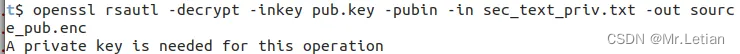
但是使用签名和验签指令实现了该功能。此处的签名和验签其实并不是理论上的签名和验签
4. 命令dgst
# verify by RSA2048 with SHA-256
# Output a base64 string after signing
openssl dgst -sha256 -sign <private key> <file path> | openssl base64 -A# Decode base64 string
$ openssl base64 -d -A -in <base64 encoded file> -out <base64 decoded file>
# Verify the signature
$ openssl dgst -sha256 -verify <public key> -signature <decoded file> <file path>