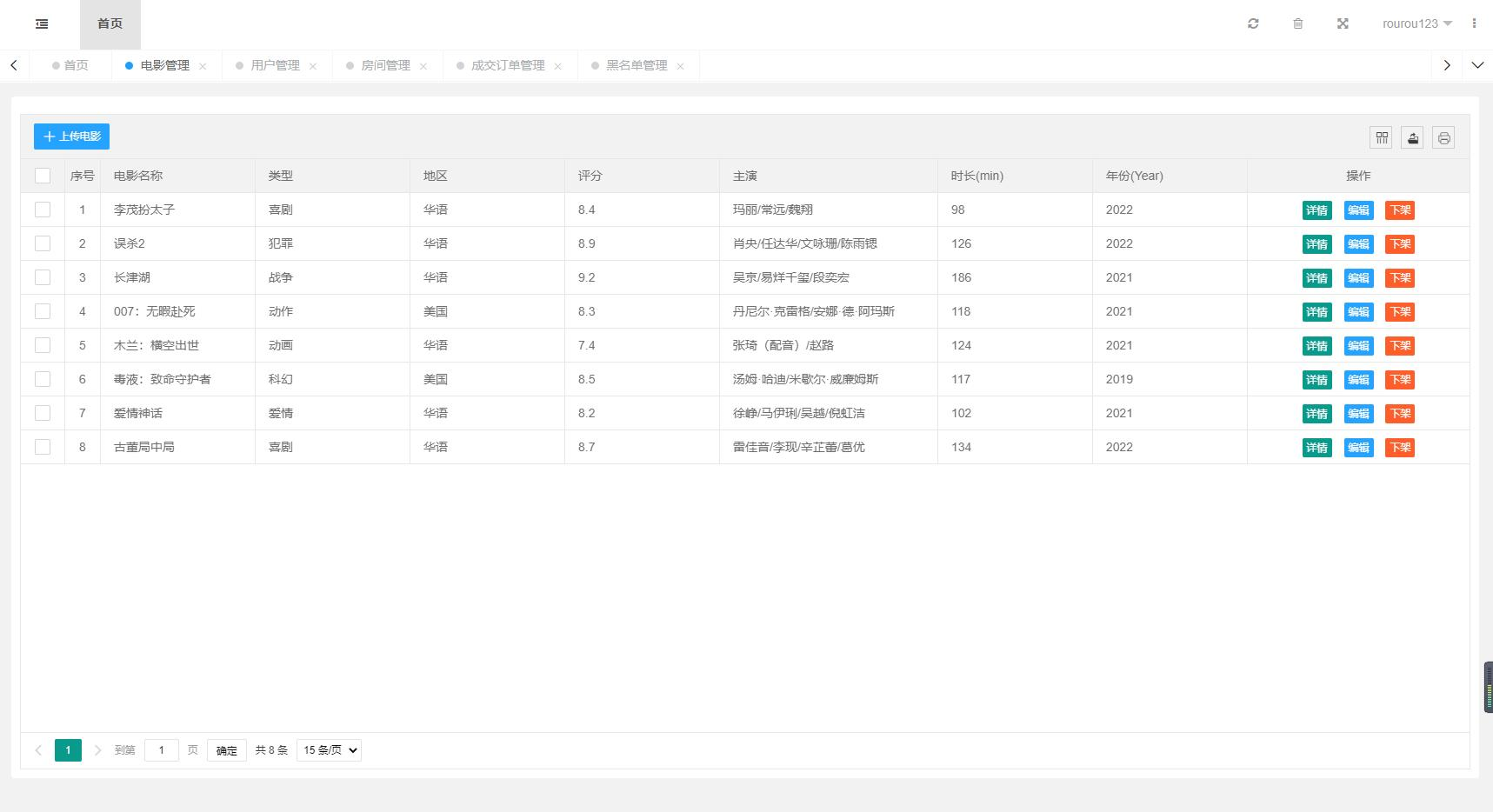
1.先连接X-shell
主服务器:192.168.32.168(server)
从服务器:192.168.32.169(node)

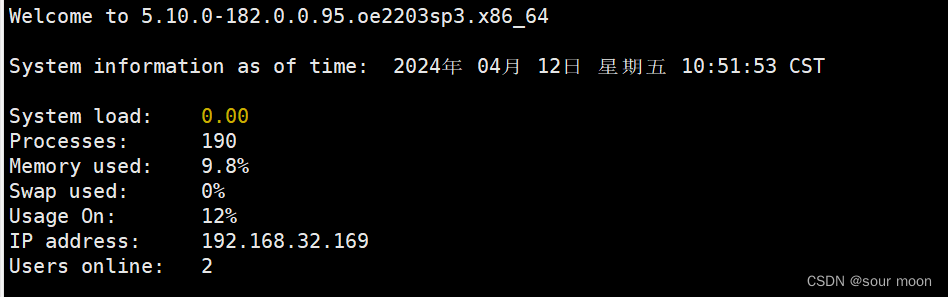
2.给主从服务器做准备工作
[root@server ~]# setenforce 0
setenforce: SELinux is disabled
[root@server ~]# systemctl stop firewalld
[root@server ~]# yum install bind -y
[root@node ~]# setenforce 0
setenforce: SELinux is disabled
[root@node ~]# systemctl stop filewalld
Failed to stop filewalld.service: Unit filewalld.service not loaded.
[root@node ~]# yum install bind -y
3.主服务器IP地址信息
[root@server ~]# nmcli c modify ens33 ipv4.method manual ipv4.addresses '192.168.32.168/24' ipv4.gateway '192.168.32.2' ipv4.dns '192.168.32.168'
[root@server ~]# nmcli c reload
[root@server ~]# nmcli c up ens33
连接已成功激活(D-Bus 活动路径:/org/freedesktop/NetworkManager/ActiveConnection/2)
4.从服务器IP地址信息
[root@node ~]# nmcli c modify ens33 ipv4.method manual ipv4.addresses '192.168.32.169/24' ipv4.gateway '192.168.32.2' ipv4.dns '192.168.32.169'
[root@node ~]# nmcli c reload
[root@node ~]# nmcli c up ens33
连接已成功激活(D-Bus 活动路径:/org/freedesktop/NetworkManager/ActiveConnection/3)
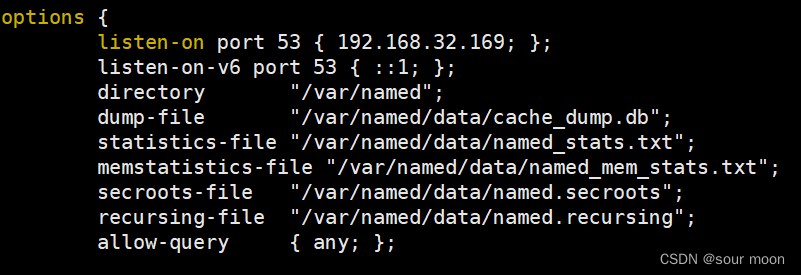
5.主服务端操作,编辑主配置文件设置监听IP
[root@server ~]# vim /etc/named.conf
6.主服务端操作打开区域配置文件,添加如下内容,重点为:允许从服务器的同步请求,即修改为 allow-transfer {允许同步区域信息的主机IP;};参数
[root@server ~]# vim /etc/named.rfc1912.zones

7.主服务端操作,设置正反向解析数据配置文件,内容如下:
正向解析
[root@server ~]# cd /var/named
[root@server named]# ls
data dynamic named.ca named.empty named.localhost named.loopback slaves
[root@server named]# cp -a named.localhost openlab.com.zone

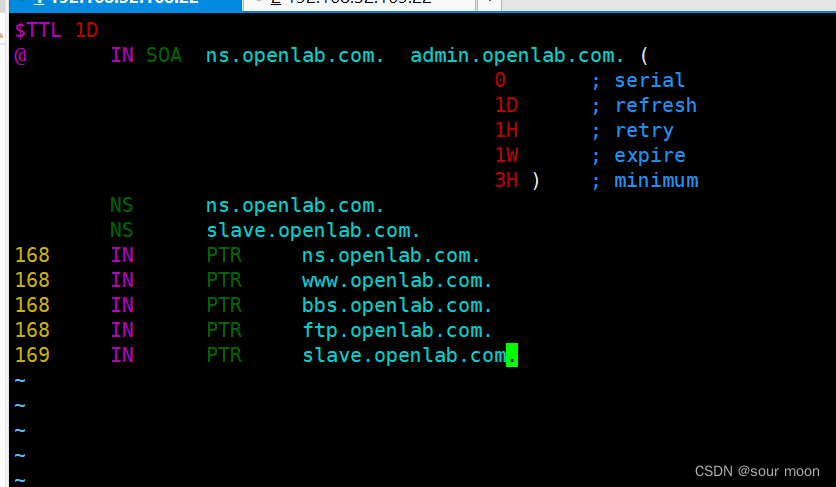
反向解析
[root@server named]# vim openlab.com.zone
[root@server named]# cp -a named.loopback 192.168.32.arpa
[root@server named]# vim /var/named/192.168.32.arpa
 8.主服务端操作,重启服务
8.主服务端操作,重启服务
[root@server named]# systemctl restart named
9.从服务端操作,修改主配置文件
10.从服务端操作,修改区域配置文件,填写主服务器的 IP 地址与要抓取的区域信息,注意此时的服务类型应该是 slave(从)
[root@node ~]# vim /etc/named.rfc1912.zones
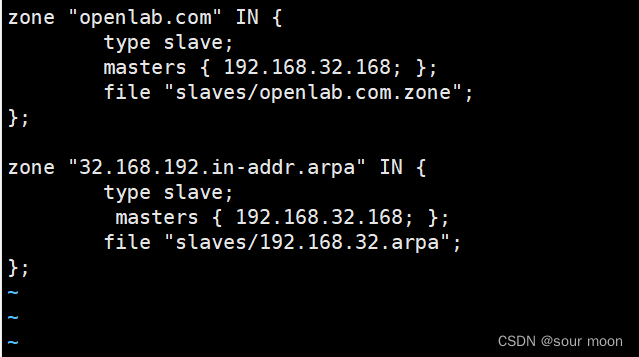
11.从服务端操作,重启服务,注意:当从服务器的 DNS 服务程序在重启后,就自动从主服务器上同步了数据配置文件,且该文件默认会放置在区域配置文件中所定义的目录位置中
[root@node ~]# cd /var/named/slaves
[root@node slaves]# ls
[root@node slaves]# systemctl start named
[root@node slaves]# ls
192.168.32.arpa openlab.com.zone
12.从服务端操作,确认从服务端的网卡DNS地址修改为自己的IP,使从服务器自身也能提供的 DNS 域名解析服务,在进行测试
[root@node slaves]# nslookup www.openlab.com
Server: 192.168.32.169
Address: 192.168.32.169#53Name: www.openlab.com
Address: 192.168.32.168[root@node slaves]# nslookup 192.168.32.168
168.32.168.192.in-addr.arpa name = ns.openlab.com.
168.32.168.192.in-addr.arpa name = ftp.openlab.com.
168.32.168.192.in-addr.arpa name = bbs.openlab.com.
168.32.168.192.in-addr.arpa name = www.openlab.com.[root@node slaves]# dig @192.168.32.168 www.openlab.com; <<>> DiG 9.16.23 <<>> @192.168.32.168 www.openlab.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 27107
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; COOKIE: 46406ed4d2e88dbf010000006618c6cd725007f625add712 (good)
;; QUESTION SECTION:
;www.openlab.com. IN A;; ANSWER SECTION:
www.openlab.com. 86400 IN A 192.168.32.168;; Query time: 2 msec
;; SERVER: 192.168.32.168#53(192.168.32.168)
;; WHEN: Sat Mar 09 14:34:48 CST 2024