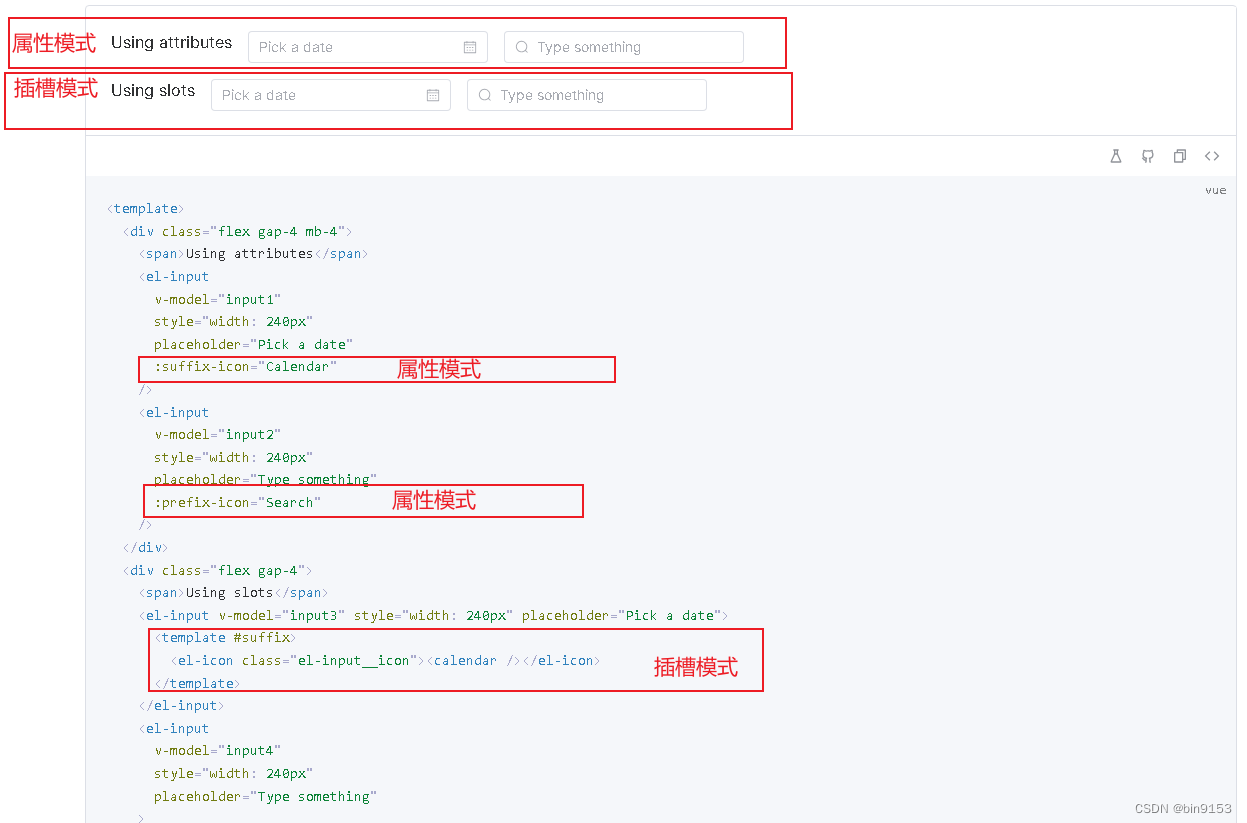
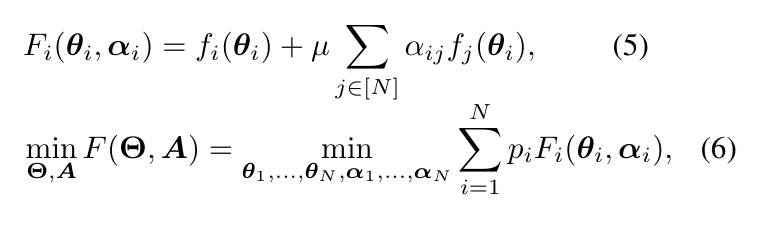运行解密响应数据程序:
D:\Python\Python311\python.exe E:\baichuan\youdaos.py
{"code":0,"dictResult":{"ce":{"word":{"trs"D:\Python\Python311\python.exe E:\baichuan\youdaospdm.pyD:\Python\Python311\python.exe E:\baichuan\youdaospdm.py:[{"voice":"hello&type=2","#text":"hello","#tran":"喂,你好(用于问候或打招呼);喂,你好(打电话时的招呼语);喂,你好(引起别人注意的招呼语);<非正式>喂,嘿 (认为别人说了蠢话或分心);<英,旧>嘿(表示惊讶);招呼,问候;(Hello)(法、印、美、俄)埃洛(人名);说(或大声说)“喂”;打招呼;"},{"voice":"hi&type=2","#text":"hi","#tran":"嗨!(表示问候或用以唤起注意);(Hi)人名;(柬)希;"},{"voice":"how+do+you+do&type=2","#text":"how do you do","#tran":"你好;"}],"phone":"nǐ hǎo","return-phrase":"你好"}}},"translateResult":[[{"tgt":"hello","src":"你好","srcPronounce":"nĭhăo"}]],"type":"zh-CHS2en"}

Process finished with exit code 0
可以看到在末尾多了14个乱码字符,添加了这行代码问题解决了:
a = unpad(a, 16)
原来有道在响应数据中添加了pad,在aes解密后去除pad就好了
import base64
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad, unpad
import hashlibdef decode_data(text):decodeiv = "ydsecret://query/iv/C@lZe2YzHtZ2CYgaXKSVfsb7Y4QWHjITPPZ0nQp87fBeJ!Iv6v^6fvi2WN@bYpJ4"decodekey = "ydsecret://query/key/B*RGygVywfNBwpmBaZg*WT7SIOUP2T0C9WHMZN39j^DAdaZhAnxvGcCY6VYFwnHl"key = hashlib.md5(decodekey.encode(encoding='utf-8')).digest()iv = hashlib.md5(decodeiv.encode(encoding='utf-8')).digest()# 构造一个AES对象aes_en = AES.new(key, AES.MODE_CBC, iv)# text是b64编码的数据,将其解码data_new = base64.urlsafe_b64decode(text)# AES解密数据a = aes_en.decrypt(data_new)# 去除pada = unpad(a, 16)# 解码成str格式a = a.decode(encoding='utf-8')return aif __name__ == '__main__':s = 'Z21kD9ZK1ke6ugku2ccWu4n6eLnvoDT0YgGi0y3g-v0B9sYqg8L9D6UERNozYOHqnYdl2efZNyM6Trc_xS-zKtfTK4hb6JP8XwCzNh0avc8qItQUiIU_4wKKXJlIpvMvfKvJaaZzaX6VEtpkr2FdkfoT_Jgbm2GRSVj3r40autIdlImENG8hC0ZH4ww7utwuTt3Oo_ZpXg0BSq9wePSAB75-ChkiGKF9HTIPeCl2bl84SBD1XDfFCZpkKQhecYSs0JLoXOqP2ltavxRrg58Hp1q5uIgZZ_Oo2-Jmd-t1r4es40drcAq5bjmS62M2VJF8D6ojtOh9JTfNwgzD3CxYn-Pd7-TgHMyNEJEkFXTAyxzpjlFqtrCYDE3SZUYlENkqsL8Wrra1hM-1n TfiB-BLcWAdRBynNpP5_54aq_-GBsq8bB_9yEX5ovzDB4_Ry_spVVuUnb39iplMHCdCnjOD3ngiIDbl9SUz-9n pjBX05ZYRdPmFPAl424qdoaxeVqnVoH8jQFPZVqaHMzu4mJg0SICDWFH7GP1zqGRbXd3ESjT_iBInl3gICt2XVuhh_nubcELkTEC6xbqEDRQkPUNMpzXJHjcvsLHtcmSW0S9F0445ho9kT2qZYdMBC3Fs0OaHpUtFu77gZpQn7sGiqh8VliXIcUtfvvop-1 c-Vu5QjfUbLn2-s5POR9fGYG6rt6ioe_PGmwWj-Cc00zUM7FybfarKTr4D3Rk57R72qpXN4Ja86ZsCAMmDG-m5z31RQh_V7echJ8Kna3Go3yWKCK4vtSwOWrFhiS5RTz6EkrGc3SkFKbb5vp8Wop_84myBtgnBmj4CczhTq2HcOxrJf4def6yDt2uBxyv4bTVGx9Yx3uB4Gx0iK5kYvfma6B_LnkRWk331wjuXKQtBGYIuWkR8J5QtvBmIRVaa7AA19Z4xMIEAqbcuQ5p4I9FCElthBrJd9YOcouHK4U27xxYWJJXcJoTvzG7zWtiV76fHDeQLgAWvJJ7ww4NFgjhqc6AKA_2afxa4c_lAvVZgFuKL3XSCL7PfKxp6GhjcGKeSRr80PT1gfFw2xi8X4ejjNm_prsUZ'res = decode_data(s)print(res)