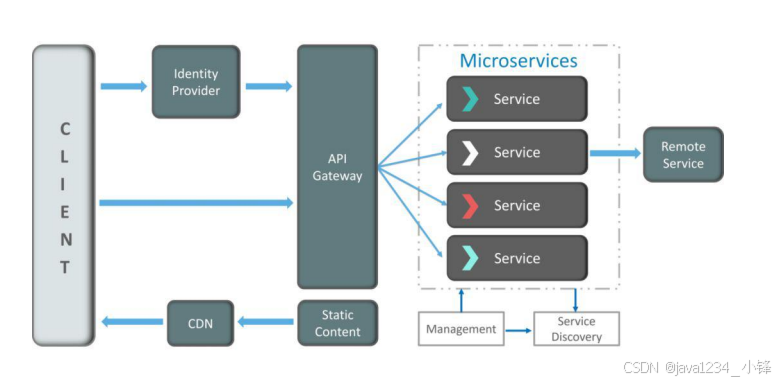
随着DeepSeek的热度,各行各业接入AI智能,当然作为一个深受3D爱好者喜爱的软件——Blender,也接入了AI智能,通过Blender-MCP,开启一场Blender的智能化模型创建的世界之旅。
目录
- 1.准备工作
- 2.环境配置
- 2.1 Mac安装
- 2.2 Windows安装
- 3.安装与配置
- 3.1 Blender安装插件
- 3.2 Cursor配置
- 4.测试
- 4.1 Blender插件启动
- 4.2 命令行启动
- 4.3 Blender文字模型生成
- 4.4 Blender图片模型生成
1.准备工作
Python环境:
国内高速下载
版本要求Python3.10以上,建议选择Python3.12版本。
Blender下载:
Blender下载官网地址:点击下载

Blender LTS版本:点击下载

Cursor下载
Cursor官网:点击下载

Blender-MCP插件
安装Git,下载插件文件
git clone https://github.com/ahujasid/blender-mcp.git
2.环境配置
2.1 Mac安装
配置HomeBrew,打开termial终端输入。
/bin/zsh -c "$(curl -fsSL https://gitee.com/cunkai/HomebrewCN/raw/master/Homebrew.sh)"```

brew安装uv (注意,一定要安装)
brew install uv
2.2 Windows安装
前提Python3.10以上版本已安装
python安装uv
pip install uv
3.安装与配置
3.1 Blender安装插件


3.2 Cursor配置
安装中文语言,Ctrl+Shift+X,安装Chinese。

Cursor配置JSON文件


mcp.json文件,添加配置参数代码。
{"mcpServers":{"blender":{"command":"uvx","args":["blender-mcp"]}}
}4.测试
4.1 Blender插件启动

4.2 命令行启动
uvx blender-mcp
 Cursor打开
Cursor打开

4.3 Blender文字模型生成

4.4 Blender图片模型生成