官网地址:
Vault | HashiCorp Developer
使用原因:
facebook审计需要将用的accesstoken等秘钥使用vault秘钥管理工具进行管理
简介:
使用 UI、CLI 或 HTTP API 保护、存储和严格控制对令牌、密码、证书、用于保护机密的加密密钥和其他敏感数据的访问。
安装(系统:ubuntu16):
官网参考地址:Install Vault | Vault | HashiCorp Developer
1.根据系统版本下载vault压缩包,下载地址:https://developer.hashicorp.com/vault/downloads
2.解压vault_1.12.2_linux_amd64.zip到任意目录(eg:/app/vault)
3.将vault添加到环境变量中 export PATH=$PATH:/root/app/vault
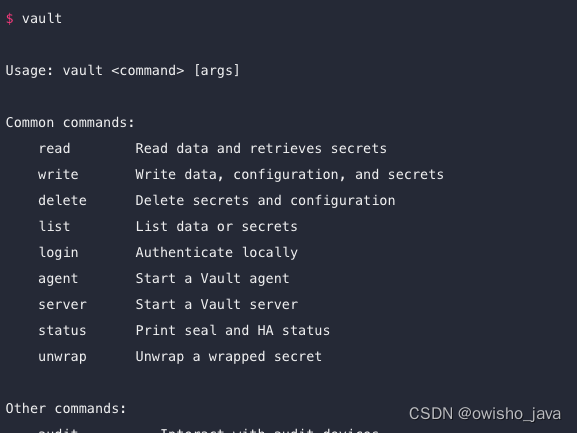
4.验证是否安装成功,命令行中执行> vault 会看到如下截图内容
正式环境部署:
官网参考地址:Deploy Vault | Vault | HashiCorp Developer
主要步骤:
1.配置hcl配置文件,内容如下
storage "raft" {path = "./vault/data"node_id = "node1"
}listener "tcp" {address = "127.0.0.1:8200"tls_disable = "true"
}api_addr = "http://127.0.0.1:8200"
cluster_addr = "https://127.0.0.1:8201"
ui = true
2.根据hcl配置中storage内容,创建数据存储目录 ./vault/data
3.依次执行一下命令
#命令1:启动vault服务
vault server -config=config.hcl#命令2:个人理解vault cli 与vault通信需要使用VAULT_ADDR环境变量的值
export VAULT_ADDR='http://127.0.0.1:8200'#命令3:生成root token和unseal key的操作
vault operator init
#会看到类似如下的输出内容:
Unseal Key 1: 4jYbl2CBIv6SpkKj6Hos9iD32k5RfGkLzlosrrq/JgOm
Unseal Key 2: B05G1DRtfYckFV5BbdBvXq0wkK5HFqB9g2jcDmNfTQiS
Unseal Key 3: Arig0N9rN9ezkTRo7qTB7gsIZDaonOcc53EHo83F5chA
Unseal Key 4: 0cZE0C/gEk3YHaKjIWxhyyfs8REhqkRW/CSXTnmTilv+
Unseal Key 5: fYhZOseRgzxmJCmIqUdxEm9C3jB5Q27AowER9w4FC2CkInitial Root Token: s.KkNJYWF5g0pomcCLEmDdOVCWVault initialized with 5 key shares and a key threshold of 3. Please securely
distribute the key shares printed above. When the Vault is re-sealed,
restarted, or stopped, you must supply at least 3 of these keys to unseal it
before it can start servicing requests.Vault does not store the generated root key (previously known as master key).
Without at least 3 key to reconstruct the root key, Vault will remain
permanently sealed!It is possible to generate new unseal keys, provided you have a quorum of
existing unseal keys shares. See "vault operator rekey" for more information.#命令4:让vault解锁变可用的操作,此步骤可以在cli中执行,也可以在ui界面等其他终端中执行
#多次执行该命令并输入对应的Unseal Key(官网示例中为5选3,可以修改相关配置)
vault operator unseal #命令5:登录,个人学习中使用了root token登录,可以配置policy生成新的token并使用相应的token进行登录;也可以修改登录方式为LDAP等(需要修改相关配置)
vault login#命令6:清理,杀死进程,并删除数据文件
pgrep -f vault | xargs kill
rm -r ./vault/data策略配置policies:
官网参考地址:Policies | Vault | HashiCorp Developer
认证相关(token生成等):
官网参考地址:Authentication | Vault | HashiCorp Developer
APP集成相关参考地址:
Java Application Demo | Vault | HashiCorp Developer
Spring Cloud Vault
HTTP API: Libraries | Vault | HashiCorp Developer
GitHub - hashicorp/vault-examples: A collection of example code snippets demonstrating the various ways to use the HashiCorp Vault client libraries.
其他请参考官网内容
Web UI、Dynamic Secrets、Secrets Engines等