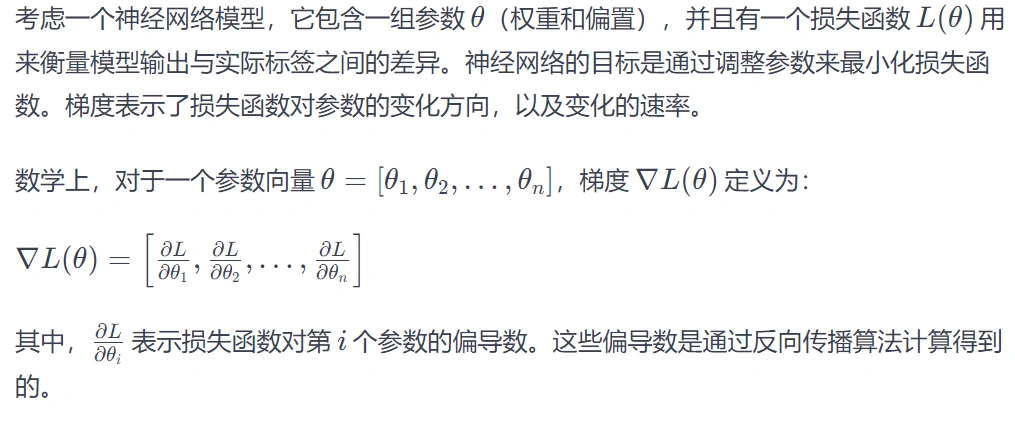
网络设备配置
将 syslog-ip 替换成服务器的IP地址。
Huawei
info-center loghost source interface
info-center loghost syslog-ip local-time facility local6
H3C
info-center loghost source interface
info-center loghost syslog-ip facility local5
Aruba
logging arm subcat all level warnings
logging network subcat all level warnings
logging security subcat all level warnings
logging security subcat ids level warnings
logging security subcat ids-ap level warnings
logging system subcat all level warnings
logging user subcat all level warnings
logging wireless subcat all level warnings
logging 10.10.4.86 severity warnings facility local3
CISCO
logging on
logging syslog-ip
logging facility local4
logging source-interface e0本次以华为交换机为例,首先登录交换机,设置日志收集服务器地址:
1、设置日志服务器IP地址
<S5735-EsxiMGT-SW1>system-view
Enter system view, return user view with Ctrl+Z.
[S5735-EsxiMGT-SW1]display current-configuration | in info
info-center loghost source Vlanif100
snmp-agent sys-info version v2c
undo snmp-agent sys-info version v3
[S5735-EsxiMGT-SW1]info-center loghost 10.10.200.35
[S5735-EsxiMGT-SW1]display current-configuration | in info
info-center loghost source Vlanif100
info-center loghost 10.10.200.35
snmp-agent sys-info version v2c
undo snmp-agent sys-info version v3
之后登录logstash服务器,配置conf
[root@node3 ~]# cd /etc/logstash/conf.d/
[root@node3 conf.d]# vim switch.conf
input{tcp { port => 5002type => "Cisco"}udp { port => 514type => "HUAWEI"}udp { port => 5002type => "Cisco"}udp { port => 5003type => "H3C"}
}
filter {if [type] == "Cisco" {grok {match => { "message" => "<%{BASE10NUM:syslog_pri}>%{NUMBER:log_sequence}: .%{SYSLOGTIMESTAMP:timestamp}: %%{DATA:facility}-%{POSINT:severity}-%{CISCO_REASON:mnemonic}: %{GREEDYDATA:message}" }match => { "message" => "<%{BASE10NUM:syslog_pri}>%{NUMBER:log_sequence}: %{SYSLOGTIMESTAMP:timestamp}: %%{DATA:facility}-%{POSINT:severity}-%{CISCO_REASON:mnemonic}: %{GREEDYDATA:message}" }add_field => {"severity_code" => "%{severity}"}overwrite => ["message"]}
}elseif [type] == "H3C" {grok {match => { "message" => "<%{BASE10NUM:syslog_pri}>%{SYSLOGTIMESTAMP:timestamp} %{YEAR:year} %{DATA:hostname} %%%{DATA:vvmodule}/%{POSINT:severity}/%{DATA:digest}: %{GREEDYDATA:message}" }remove_field => [ "year" ]add_field => {"severity_code" => "%{severity}"}overwrite => ["message"]}
}elseif [type] == "HUAWEI" {grok {match => { "message" => "<%{BASE10NUM:syslog_pri}>%{SYSLOGTIMESTAMP:timestamp} %{DATA:hostname} %%%{DATA:ddModuleName}/%{POSINT:severity}/%{DATA:Brief}:%{GREEDYDATA:message}"}match => { "message" => "<%{BASE10NUM:syslog_pri}>%{SYSLOGTIMESTAMP:timestamp} %{DATA:hostname} %{DATA:ddModuleName}/%{POSINT:severity}/%{DATA:Brief}:%{GREEDYDATA:message}"}remove_field => [ "timestamp" ]add_field => {"severity_code" => "%{severity}"}overwrite => ["message"]}
}
#mutate {
# gsub => [
# "severity", "0", "Emergency",
# "severity", "1", "Alert",
# "severity", "2", "Critical",
# "severity", "3", "Error",
# "severity", "4", "Warning",
# "severity", "5", "Notice",
# "severity", "6", "Informational",
# "severity", "7", "Debug"
# ]
# }
}
output{elasticsearch {index =>"syslog-%{+YYYY.MM.dd}"hosts => ["10.10.200.33:9200","10.10.200.34:9200","10.10.200.35:9200"]}
}
修改后,重启Logstash
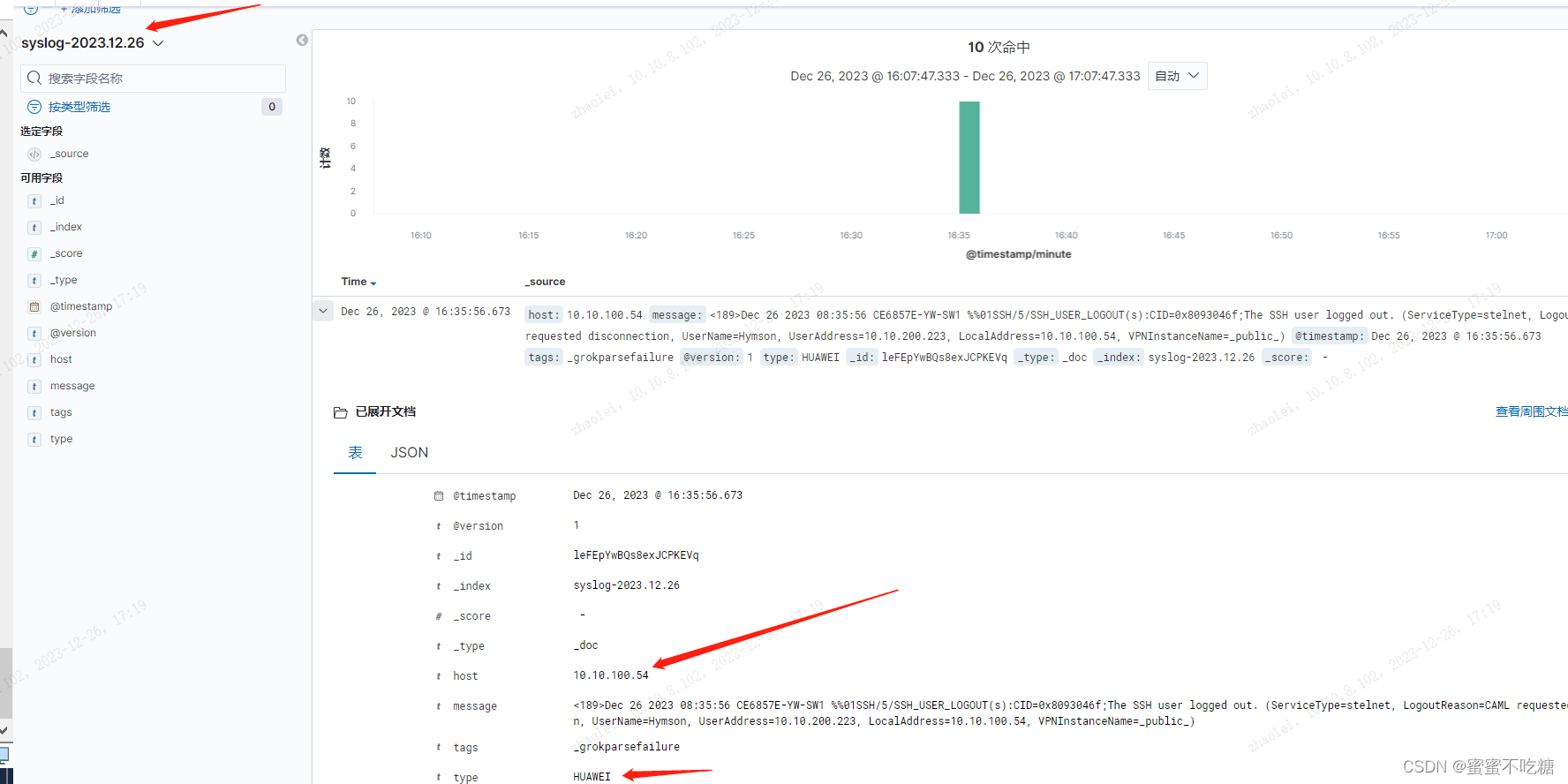
登录ELK,检查数据