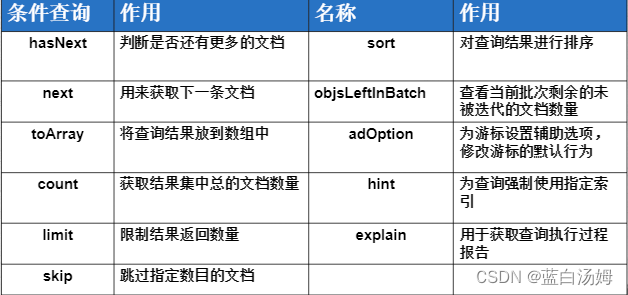
题目描述
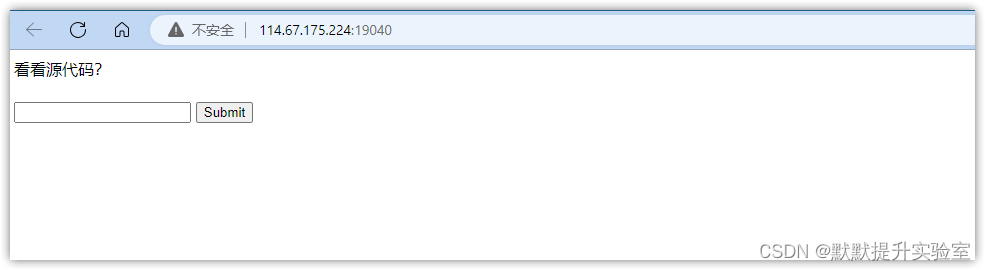
题目截图如下:

进入场景看看:
解题思路
- 你说啥就是啥:去源代码吧
相关工具
- URL解码平台:https://www.iamwawa.cn/urldecode.html
解题步骤
- 随便输入试试
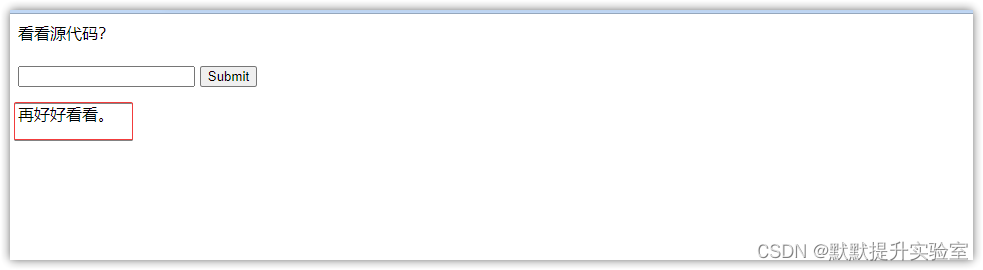
2. 看看源码

存在script:
<script>
var p1 = '%66%75%6e%63%74%69%6f%6e%20%63%68%65%63%6b%53%75%62%6d%69%74%28%29%7b%76%61%72%20%61%3d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%70%61%73%73%77%6f%72%64%22%29%3b%69%66%28%22%75%6e%64%65%66%69%6e%65%64%22%21%3d%74%79%70%65%6f%66%20%61%29%7b%69%66%28%22%36%37%64%37%30%39%62%32%62';
var p2 = '%61%61%36%34%38%63%66%36%65%38%37%61%37%31%31%34%66%31%22%3d%3d%61%2e%76%61%6c%75%65%29%72%65%74%75%72%6e%21%30%3b%61%6c%65%72%74%28%22%45%72%72%6f%72%22%29%3b%61%2e%66%6f%63%75%73%28%29%3b%72%65%74%75%72%6e%21%31%7d%7d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%6c%65%76%65%6c%51%75%65%73%74%22%29%2e%6f%6e%73%75%62%6d%69%74%3d%63%68%65%63%6b%53%75%62%6d%69%74%3b';
eval(unescape(p1) + unescape('%35%34%61%61%32' + p2));
</script>
这是要我解码分析的意思?看这个样子是URL编码,解码试试:
p1:
function checkSubmit(){var a=document.getElementById("password");if("undefined"!=typeof a){if("67d709b2b
p2:
aa648cf6e87a7114f1"==a.value)return!0;alert("Error");a.focus();return!1}}document.getElementById("levelQuest").onsubmit=checkSubmit;
unescape:
54aa2
eval(unescape(p1) + unescape(‘54aa2’ + p2));的意思是?
eval 是运算函数,也就是将p1和54aa2以及p2拼接起来。
- unescape 这是一个解密函数,对应的就是escape加密函数
得到拼接后的代码如下,js格式化:
function checkSubmit() {var a = document.getElementById("password");if ("undefined" != typeof a) {if ("67d709b2b54aa2aa648cf6e87a7114f1" == a.value) return !0;alert("Error");a.focus();return !1}
}
document.getElementById("levelQuest").onsubmit = checkSubmit;
解释如下:
在函数中,首先通过 document.getElementById() 方法获取 id 为 “password” 的元素,并将其赋值给变量 a。然后判断变量 a 是否被定义,如果是未定义,则执行以下操作:
- 弹出一个警告框,显示 “Error”。
- 将焦点设置到变量 a 所指向的元素。
- 返回 false,表示验证失败。
如果变量 a 被定义,进一步判断变量 a 的值是否等于 “67d709b2b54aa2aa648cf6e87a7114f1”,如果是,则表示验证通过,返回 true,表示可以提交表单。
最后,通过 document.getElementById() 方法获取 id 为 “levelQuest” 的元素,并将函数 checkSubmit() 赋值给其 onsubmit 事件,这样当表单被提交时,会调用函数 checkSubmit() 进行验证。
我们也可以直接使用在线js平台:https://www.wetools.com/js-run
var p1 = '%66%75%6e%63%74%69%6f%6e%20%63%68%65%63%6b%53%75%62%6d%69%74%28%29%7b%76%61%72%20%61%3d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%70%61%73%73%77%6f%72%64%22%29%3b%69%66%28%22%75%6e%64%65%66%69%6e%65%64%22%21%3d%74%79%70%65%6f%66%20%61%29%7b%69%66%28%22%36%37%64%37%30%39%62%32%62';
var p2 = '%61%61%36%34%38%63%66%36%65%38%37%61%37%31%31%34%66%31%22%3d%3d%61%2e%76%61%6c%75%65%29%72%65%74%75%72%6e%21%30%3b%61%6c%65%72%74%28%22%45%72%72%6f%72%22%29%3b%61%2e%66%6f%63%75%73%28%29%3b%72%65%74%75%72%6e%21%31%7d%7d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%6c%65%76%65%6c%51%75%65%73%74%22%29%2e%6f%6e%73%75%62%6d%69%74%3d%63%68%65%63%6b%53%75%62%6d%69%74%3b';
var p3 = unescape(p1) + unescape('%35%34%61%61%32' + p2);
console.log(p3)
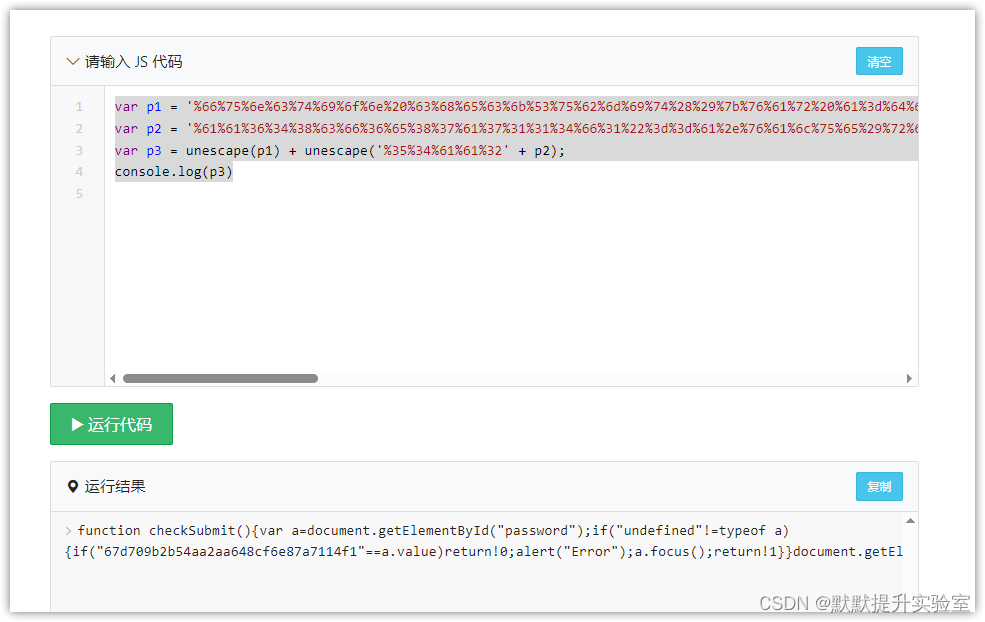
看这里:
if("67d709b2b54aa2aa648cf6e87a7114f1"==a.value)return!0;
那不就直接复制输入67d709b2b54aa2aa648cf6e87a7114f1
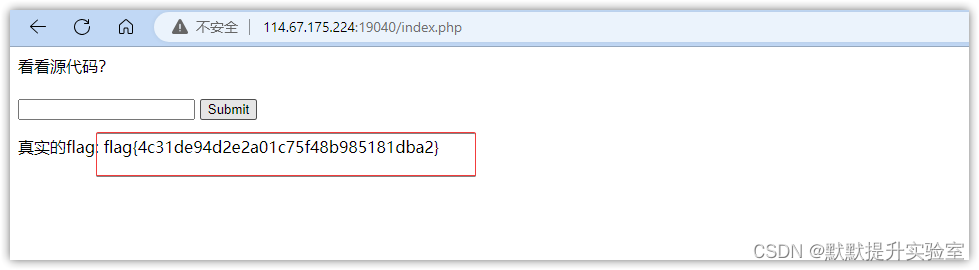
得到Flag
flag{4c31de94d2e2a01c75f48b985181dba2}
新知识点
有用的话,请
点赞收藏评论,帮助更多的同学哦